What is SOC 2?
SOC 2 is an auditing procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of its clients. For security-conscious businesses, SOC 2 compliance is a minimal requirement when considering a SaaS provider.
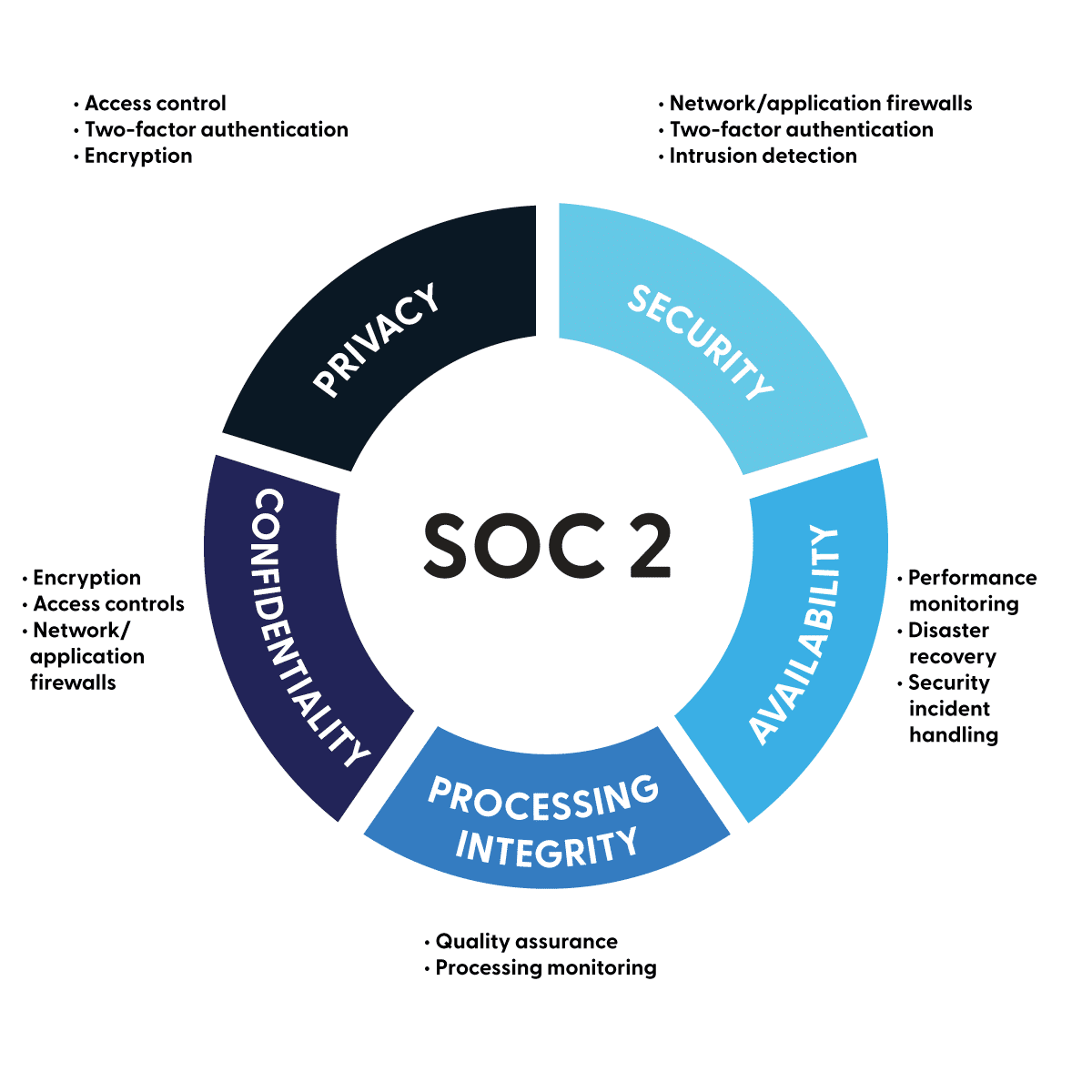
SOC 2 defines criteria for managing customer data based on five trust service principles:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
SOC 2 reports are unique to each organization because of specific business practices they may use. Each organization designs its own controls to comply with one or more of the trust principles. These internal reports provide you with important information about how your service provider manages data.
There are two types of SOC reports:
- SOC 2 Type I report is an attestation of controls at a service organization at a specific point in time.
- SOC 2 Type II report is an attestation of controls at a service organization over a minimum six-month period.
Why SOC 2 compliance is a good idea
Without SOC services, cyber-criminal attacks can remain hidden for a long time with companies that do not have the skills to detect and respond to threats in a timely manner. SOC 2 allows companies to have improved visibility on their security posture and stronger data protection processes through more cyber-aware skills, creating improved threat management for today—and the future.

At Rhymetec we take security seriously. SOC 2 demonstrates compliance, and an important aspect for our clients is that they can trust that we have taken all necessary measures to protect the information processed through our services. In addition to our ISO 27001 certification, the SOC 2 Type II report provides additional verification and detailed descriptions of the applied security controls in place at Rhymetec.
How do we do it?
We make audits more efficient—and less of a hassle—by implementing technologies and controls to meet each SOC 2 criteria. We also provide compliance reports and automatic threat updates.
At Rhymetec we implement multiple systems to get you SOC 2 compliant, these include but are not limited to:
1. Bringing in credible auditors
2. Auditing the 5 criteria for SOC 2 compliance:
- Security: We make sure that your system is protected against unauthorized access for both physical and logical.
- Availability: We ensure that your system is available for operation and use as you’ve agree to with your customers.
- Processing Integrity: We use data roadmaps and management software to make sure that your system is processing data accurately, timely, and with authority
- Confidentiality: We systematically organize information at Rhymetec as to ensure the protection of confidential information as agreed to with your customer.
- Privacy: We ensure that your organization will stay in compliance as privacy is secured.
3. Building a roadmap to SOC 2 Compliance
4. A formal Audit
5. Certification and Recertification
-
- It is imperative to maintain certification. This will require you to undergo regular annual audits to ensure that your security measures and documentation scale with your organization.
Deliverables from Rhymetec
Our team is dedicated to delivering premium-tier service to ensure SOC 2 compliance, from comprehensive data management plans, to fully itemized reports that provide information regarding methodology, findings, potential mitigations, and our recommendations.
Rhymetec specializes in enabling meaningful, real world solutions to the most pressing challenges of the modern enterprise security environment. Assessment and reporting is contextualized to your business sector, and custom-tailored to your specific environment.
Our process is engineered to provide all the data and insights needed for you to make informed security decisions and take definitive action against unforseene cyber threats.


