Preparing for your PCI audit isn’t a matter of simply “checking the boxes” to meet compliance requirements. Ongoing compliance with PCI DSS builds trust with customers and stakeholders, protects your customers’ data, and helps with long-term reputation management.
With recent updates in PCI DSS 4.0, there’s been an increased focus on compliance maintenance. This article will help you understand the core principles of PCI DSS, how to apply them to your organization, and how to stay compliant over time.
What Is A PCI Audit and How Does It Work At A High Level?
A PCI audit is an assessment of an organization’s compliance with the Payment Card Industry Data Security Standard (PCI DSS), a set of security requirements that protect cardholder data. The auditor reviews your organization’s security measures, policies, and technical infrastructure to verify that you meet requirements.
In our recent webinar on Compliance to Confidence: Simplifying PCI Security Standards, Rhymetec CISO Metin Kortak discussed frequently asked questions and concerns around PCI DSS Version 4.0 with Kevin Whalen, Head of PCI at Prescient Security.
“The Version 4 standard has a number of new requirements, but I don’t think any of the changes are overly difficult. There are a few that are, but a lot of what the update did was simplify and consolidate some of the requirement language. But there are some new enhancements to it to be aware of,” noted Kevin Whalen during our webinar.
One such enhancement is the new focus on ensuring organizations maintain compliance over time. As we have seen with other recent updates to cybersecurity and compliance frameworks like NIST CSF Version 2.0, there is a stronger focus in the updated PCI DSS 4.0 on continuous compliance. This means businesses need to show they maintain compliance on an ongoing basis rather than just at the time of the audit.
The PCI compliance readiness process starts with a gap analysis to identify areas that need remediation. Once gaps are addressed, the formal audit is conducted by a Qualified Security Assessor (QSA). This individual reviews documentation, interviews staff, and tests controls to validate compliance. Following your audit, they will provide a report on the findings and note any corrective actions you need to take.
Core Principles and Requirements Under PCI DSS
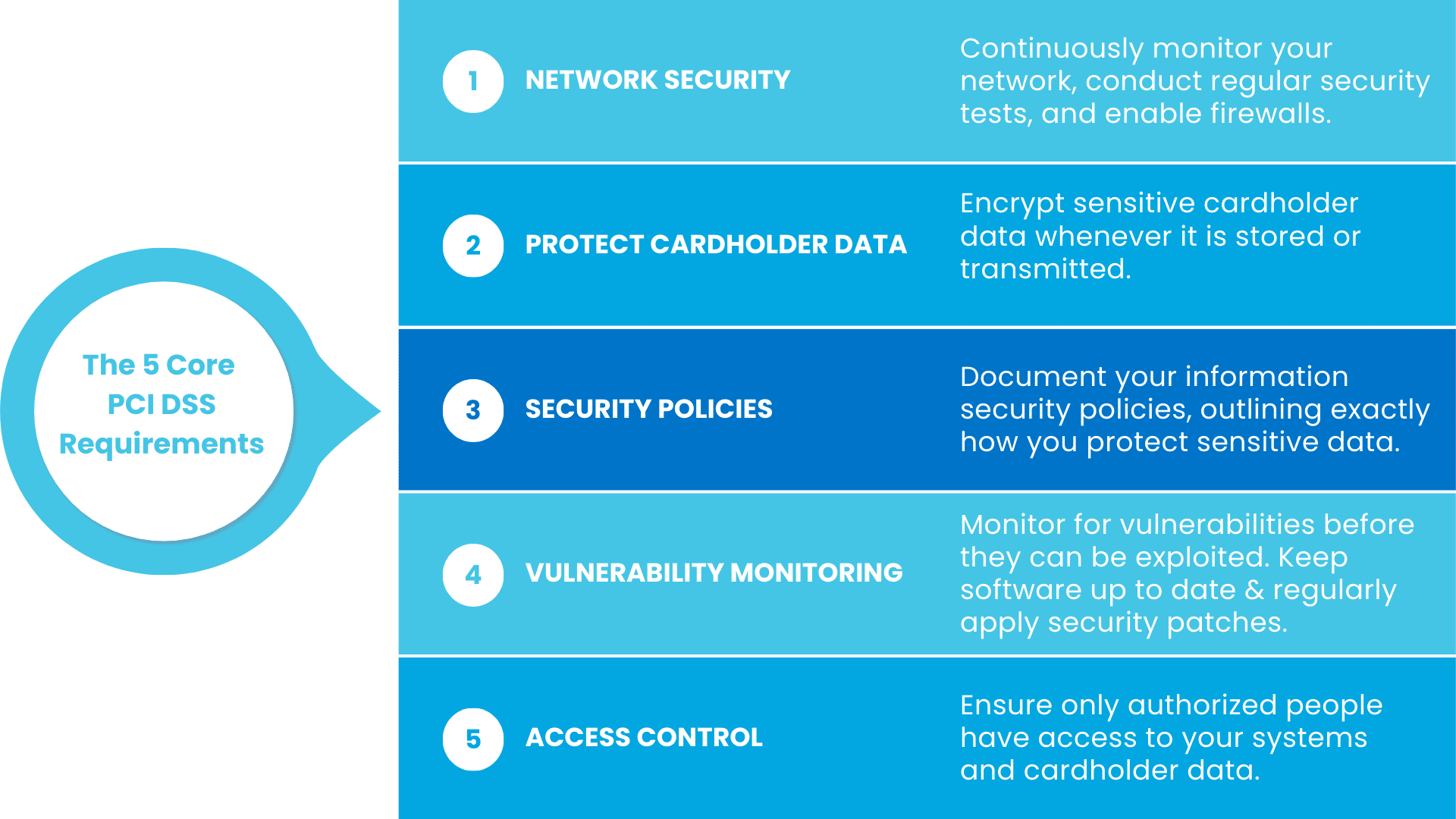
There are five core principles under PCI DSS. Each of the following requirements is important from a compliance perspective and will also vastly improve your security if you did not have them in place previously.
Let’s go over each principle in more detail, and explain how they help prevent breaches and keep your customers’ data safe:
1. Securing and Monitoring Your Network
PCI DSS requires that you set your network up with security top-of-mind.
This includes measures like firewalls to block unauthorized traffic and making sure your systems are configured securely. You also should set up ways to constantly monitor your network for suspicious activity and conduct regular security tests.
Let’s say you run a SaaS platform offering payment processing for small retailers:
If your network isn’t secured properly, it’s easier for hackers to intercept cardholder data during transactions. By setting up proper firewall measures, you can block unwanted traffic and limit access to only those who really need it.
Regular network monitoring, meanwhile, will alert you to unusual activity, such as an unexpected increase in traffic to your payment systems. Lastly, ASV scans for PCI, vulnerability scans, and penetration tests can help identify weak points and enable you to fix them before they can be exploited.
2. Protecting Cardholder Data
Under PCI DSS, you must encrypt sensitive cardholder data whenever it’s stored or transmitted. Encryption makes the data unreadable to anyone without the decryption key, so even if it’s intercepted, it’s useless to bad actors.
As an example, if a platform offers subscription services and stores credit card information for recurring payments, under PCI DSS they must have encryption enabled to prevent hackers from being able to steal readable credit card data. This is a particularly important measure if your business deals with large volumes of recurring transactions where cardholder data may be stored for longer periods of time.
3. Updating Security Policies For Your PCI Audit
Under PCI DSS, organizations must have a set of documented information security policies. Your policies should outline precisely how you protect sensitive data, and how different members of your teams play a role in this.
For example, your policies may require that all developers at your company use secure coding practices, or that support staff avoid accessing customer payment data directly.
4. Vulnerability Monitoring
Vulnerability monitoring entails common sense security measures like keeping antivirus software up to date and regularly applying security patches to your systems. The idea is to address security vulnerabilities before they can be exploited.
If a known vulnerability exists in one of the software components your project management tool relies on to work, for example, threat actors could use that to access your customers’ data. Continuously monitoring for potential vulnerabilities and having a plan to address them is critical not only for your PCI audit but also from a baseline security perspective.
5. Access Control
Access control measures need to be implemented to ensure only the right people can get into your systems and access sensitive cardholder data. Baseline security measures that all organizations should ideally be doing, like multi-factor authentication (MFA), also help with access control.
You never want everyone internally to have full access to cardholder data. By limiting access to only the employees who absolutely need it – and by also adding MFA to verify their identity – you reduce the risk of unauthorized access enormously.
Why Is PCI DSS Compliance Important For Your Business?
Businesses that handle cardholder data are required to obtain PCI DSS compliance. Non-compliance can result in fines, legal penalties, and damage to your organization’s reputation. Breaches can lead to financial losses, erode customer trust, and cause disruptions to your business operations.
Compliance also reduces the risk of fraud and theft of payment data, which can result in financial harm to both your business and your customers. With the introduction of PCI DSS 4.0, businesses are expected to demonstrate continuous compliance and show that they are taking a proactive approach to managing security risks.
Types of PCI DSS Audits and Their Scope
The type of PCI audit your business requires depends on your merchant level and the volume of transactions you process annually. Each audit type covers all of the requirements in the PCI DSS standard, but may vary in depth based on the size of your business and the sensitivity of the cardholder data you process:
Self-Assessment Questionnaire (SAQ)
This is a self-evaluation tool used by smaller businesses that don’t handle large volumes of cardholder data. The SAQ is basically a checklist where you answer a series of questions about your security practices, and is broken down into different versions depending on how you process payments. There are specific versions for businesses that process payments online, through a physical point-of-sale system, or over the phone.
As an example, if you run a SaaS business that provides a billing platform for freelancers, and you rely on a third-party payment processor like Stripe to handle the actual transactions, you wouldn’t be storing or processing cardholder data directly. Therefore, you’d likely fall under the SAQ version that applies to businesses that outsource their payment processing, and it would serve to validate that your company never stores or has access to that data.
Report on Compliance (RoC)
For larger organizations or those processing a large volume of transactions, a PCI audit conducted by a Qualified Security Assessor (QSA) is required.
This audit is more extensive and includes on-site assessments of your security controls, and is generally required for larger businesses or those processing a significant number of transactions. If your company processes more than 6 million transactions per year, you’ll likely need an RoC.
5 Steps To Prepare For Your PCI Audit
At a high level, the following 5 steps illustrate the process leading up to your PCI DSS audit.
At any one of these steps, it can be helpful to consult an outside expert, such as a Managed Security Services Provider (MSSP), with ample prior experience helping organizations achieve PCI DSS compliance.
1. Understand your scope.
Mapping out the scope of your audit is the first step. You’ll need to determine which of your systems, networks, and processes handle cardholder data. Merchants have to request additional information from customers under certain circumstances:
“When we start our scoping process, what we usually try to understand in the beginning is how the payments are being processed…Where it gets complex is when the physical card is not present when you’re making a purchase. Because the physical card is not present, PCI has certain requirements in place so that when you make a purchase online, for example, you have to provide some additional information like your billing address,” said Rhymetec CISO Metin Kortak on this topic during our webinar.
You also need to define your Cardholder Data Environment (CDE).
“What that means is we need to understand exactly where the card information is being processed. Is it only processed by the customer’s hosting provider? Or does the card information also reside in other third-party applications or physical servers? It’s important to understand the entire scope so that when we go through an audit, we can give them the proper scope and make sure that the PCI security controls are implemented on all of those hosting providers and other vendors,” said Metin.
2. Conduct a gap analysis leading up to your official PCI audit.
Perform an internal assessment to pinpoint areas where your organization does not meet PCI DSS audit requirements. This is important to do before your formal audit, as it will give you a chance to address any deficiencies beforehand. MSSPs that are experienced in compliance and offer one-off gap assessment services can be a great resource during this step.
3. Remediate any identified gaps.
Next, address any gaps found during your internal assessment. Common security measures that may need to be addressed at this stage include updating your firewalls, strengthening encryption protocols, or further formalizing your access controls.
4. Update your documentation.
Prior to your audit, make sure all of your policies and security measures are well-documented in a format that will make it easy for your auditor to keep track of. Using a compliance automation tool can be extremely helpful with this, as they provide a single, easily accessible place to upload all of your documentation for your auditors to see.
5. Perform ongoing monitoring for your next PCI audit.
This element is one of the heaviest lifts of the current version of PCI DSS.
Compliance maintenance under PCI DSS 4.0 is expected, and ongoing monitoring will help you stay compliant throughout the year. You should be regularly monitoring security systems and processes to detect any potential misconfigurations or vulnerabilities. This includes automated monitoring of various controls, such as payment page script security:
“The most significant change of 4.0 is the payment page script security, where they’ve added some new requirements in the software development controls as well as automated security controls around monitoring for changes to the construction of your pages that contain input fields for cardholder data.” – Kevin Whalen, Prescient Security
Common Challenges and What To Do
Some common challenges businesses face when preparing for PCI DSS audits include:
Defining the Scope of Your PCI Audit
Many businesses struggle with understanding the full scope of systems that must be in compliance with requirements under PCI DSS. To address this, perform an inventory of systems handling cardholder data. As an example, you will have more strict requirements that apply to your scope if you take payments over the phone instead of in person.
“Depending on how the payments are being processed, how the credit card information is being collected by the buyers – that impacts the level of work that we’re going to do for our customer,” Metin Kortak, Rhymetec
Maintaining Compliance Over Time After Your PCI Audit
Maintaining an effective compliance maintenance program that scales with your business can be a challenge. Using automated monitoring and logging tools to track compliance in real-time can be helpful, as can working with an outside expert like a Managed Security Services Provider with specific expertise in enabling organizations to stay compliant over time.
Documentation
Many organizations lack adequate documentation of their security policies and controls.
You need this documentation not only for compliance purposes but also as a common-sense security measure: All of your employees should be aware of your security policies and procedures, such as your policy on measures like multi-factor authentication (MFA).
Bonus Tip: For your PCI DSS audit, a compliance automation platform can be incredilby helpful with documentation. Compliance automation tools provide a single location with all of your documentation clearly laid out, so that you and your auditors can easily access and keep track of it.
Third-Party Risk
Third-party risk management plays an important role in PCI compliance. If you’re using a third party to process or store credit card information, you generally need to obtain that company’s own attestation or certification document to include in your own PCI audit.
“Collecting your third parties’ PCI certifications is important, especially if the vendor is processing or transmitting credit card information. Aside from that, you still need to conduct vendor assessments on all of your vendors. And that needs to go beyond just collecting the PCI certifications. That might mean checking that those vendors have proper information security policies in place, if they have conducted their own business continuity tabletop exercises, if they conduct access reviews…Just really conducting a thorough due diligence.” – Metin Kortak, Rhymetec
In sum, you need to make sure your third-party vendors that process or store your cardholder data in any way are also PCI DSS compliant.
Post PCI Audit Action Items: How To Stay Compliant
After your audit, there are several steps to help maintain compliance:
Address audit findings.
The first step post-audit is to thoroughly review the auditor’s report and remediate any identified deficiencies as needed.
Be sure you’ve implemented continuous monitoring measures.
Set up monitoring systems to track your compliance with key PCI DSS controls discussed previously, including encryption, access management, and vulnerability scanning. As noted above, a compliance automation tool can be incredibly helpful with this.
Update your policies as needed.
It can help to schedule regular intervals to review your security policies going forward. This will enable you to change your policies as needed to reflect any changes in your organization’s operations, your risk profile, or the PCI DSS standard.
Have regular internal audits.
Schedule periodic reviews to assess your compliance posture between your annual PCI DSS audits.
Vendor management.
Lastly, remaining in compliance with PCI DSS requires ongoing monitoring of your third-party vendors to confirm their continued compliance, especially if they are involved in how you handle cardholder data.
In Conclusion
Although it may seem daunting to prepare for your PCI audit, by following the steps outlined in this article, you can feel confident that you are well prepared for your audit and that your customers’ data is protected.
PCI DSS compliance is not just a one-time effort – compliance requires ongoing attention, especially with the updates introduced in PCI DSS 4.0. After your PCI audit, be sure to continue monitoring your network, confirming third-party due diligence, and updating your policies as needed. Staying proactive will help your business stay secure, remain in compliance, and build long-term trust with your customers and stakeholders.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
Interested in reading more? Check out more content on our blog: