This Rhymetec DORA Compliance Checklist will help you understand DORA requirements, how to determine if your business falls under DORA's umbrella, the specific measures you'll need to implement, ways to leverage compliance for business growth, and a roadmap to get started.
The European Union's Digital Operational Resilience Act (DORA), which took effect in January 2025, aims to protect financial institutions from risks their dependencies on technology providers may pose to them.
The Act doesn't just cover the financial institutions. If you provide services to EU financial institutions, even if you are a small software company, DORA may apply to you. Many technology providers are classified as "critical ICT third-party service providers" (CTPs) under DORA, and need to adhere to the requirements.
Financial institutions today rely heavily on a variety of services from tech companies.
For example, your average regional bank nowadays may rely on 1) a cloud storage provider for customer data, 2) a payment processing API for transactions, and 3) a third-party authentication service for security, just to name a few.
A disruption in the services of any one of these could threaten the bank's ability to operate. Given how reliant financial institutions have become on these types of services, stricter regulatory oversight is long overdue in this sector. DORA aims to fill this need.
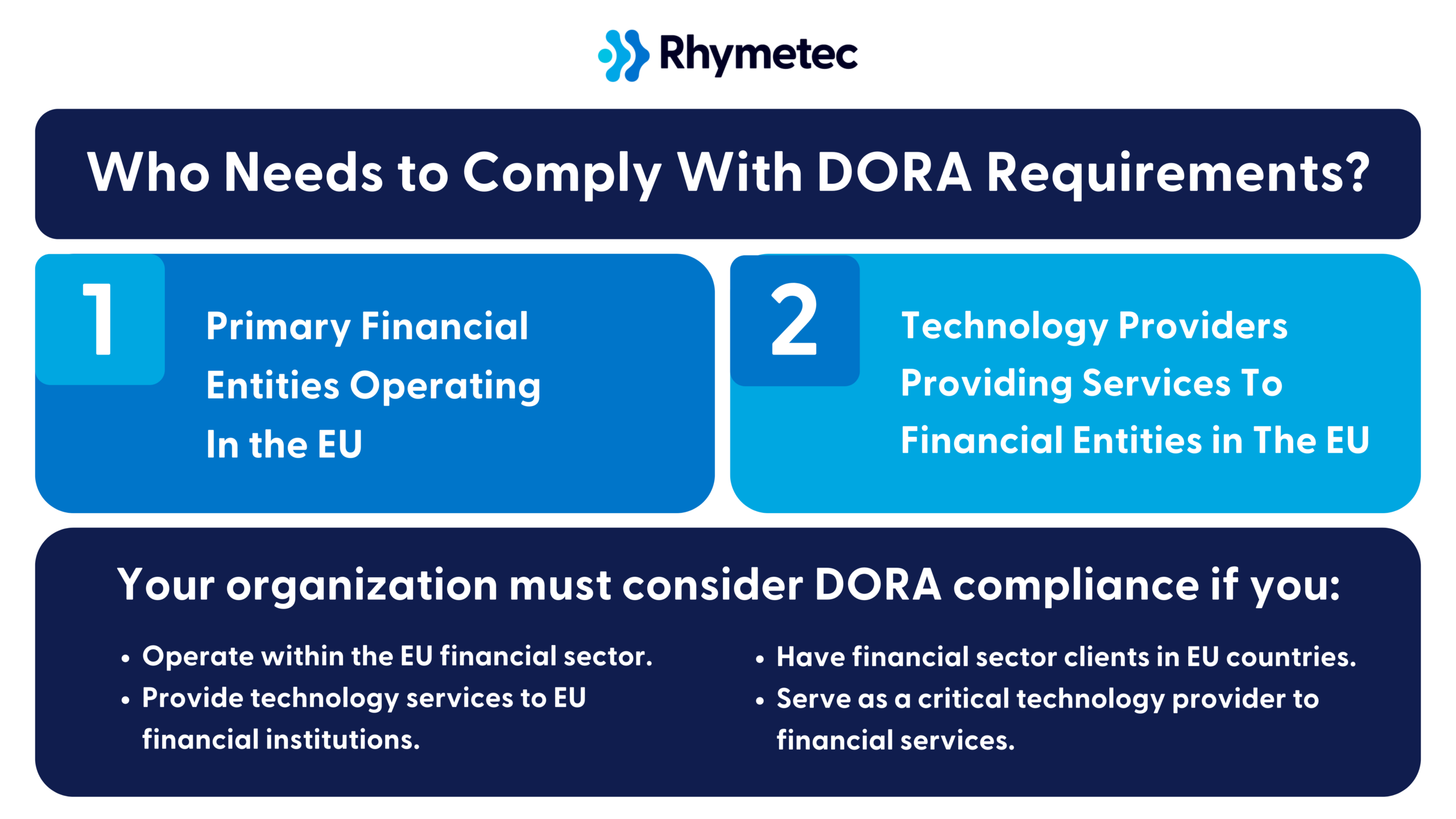
Who Needs To Comply With DORA Requirements?
DORA's compliance requirements directly apply to the following categories of organizations:
1. Primary Financial Entities Operating In the EU:
- Banks and credit institutions
- Investment firms
- Insurance and reinsurance companies
- Payment and electronic money institutions
- Cryptocurrency exchanges and providers
- Crowdfunding service providers
2. Technology Providers Providing Services To Financial Entities in The EU:
- Cloud computing services that support financial institutions
- Datacenter providers
- Network information and communication technology services
- Software and hardware providers critical to financial services
- …and more.
Your organization must consider DORA compliance if you:
- Operate within the EU financial sector.
- Provide technology services to EU financial institutions.
- Have financial sector clients in EU countries.
- Serve as a critical technology provider to financial services.
If you are unsure if your organization needs to comply with DORA, or if you need help getting started, Rhymetec's DORA Compliance Services can assist you. Our experts are happy to answer any questions you may have - we've helped over 700 organizations fast-forward their security and compliance.
DORA Compliance Checklist: Core Requirements
Let's break down what DORA actually demands from your organization.
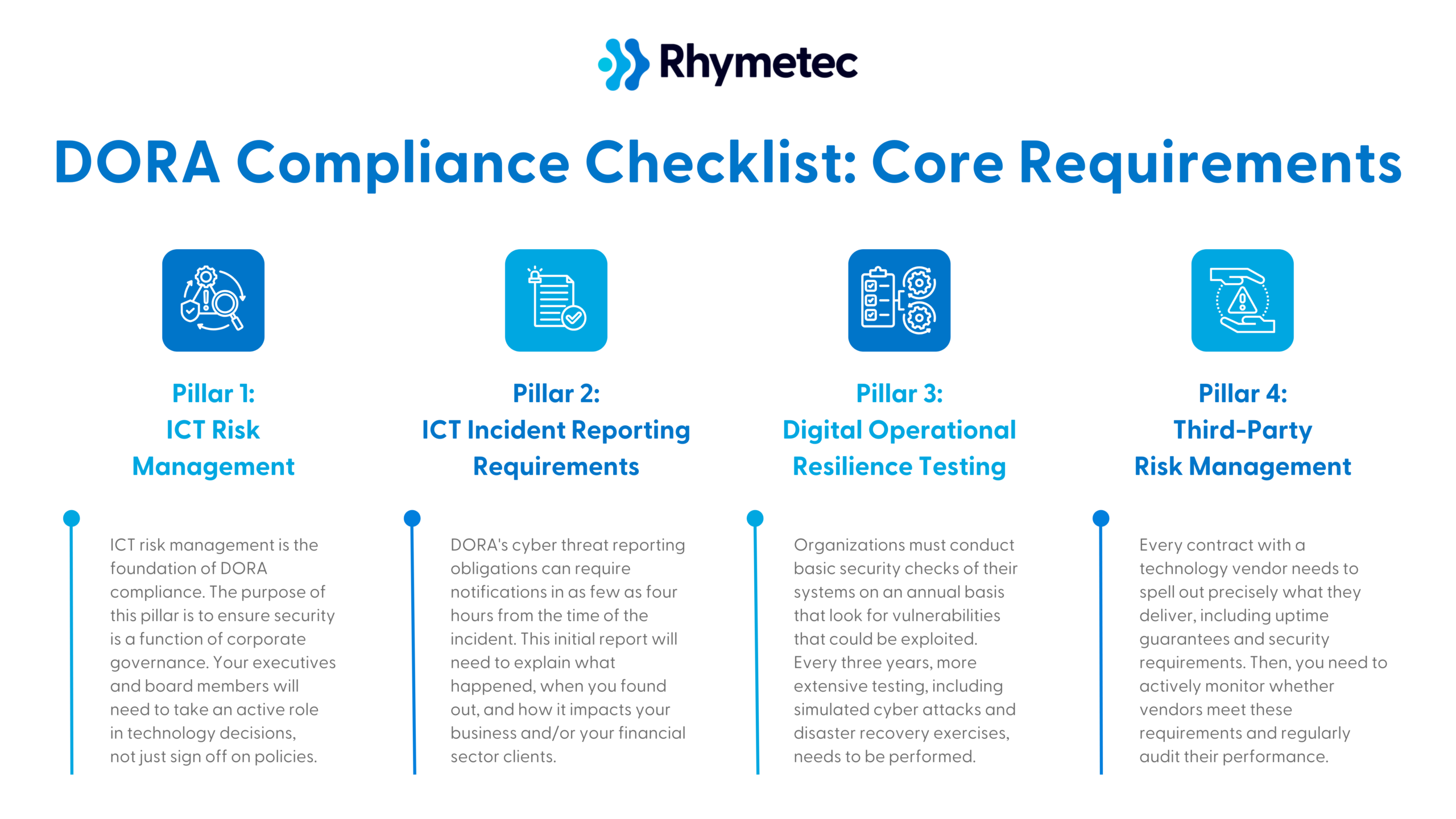
You'll need to oversee the implementation of four pillars, each of which carries specific obligations that will impact your operations differently depending on your organization's role in the financial ecosystem:
DORA Compliance Checklist Pillar 1: ICT Risk Management
Information and Communication Technology (ICT) risk management is the foundation of DORA compliance.
The purpose of this pillar is to ensure security is a function of corporate governance. Your executives and board members will need to take an active role in technology decisions, not just sign off on policies.
The following action items are requirements under this pillar:
Establish a governance framework for ICT risk management:
- Define who within your organization is responsible for ICT risk management at the executive level, and set policies to formalize accountability and integrate ICT risk into overall risk management.
- For example, you might appoint a security officer responsible for reporting ICT risks to the board.
Create policies and procedures for ICT risk identification.
- These policies should outline how you will identify threats, protect systems, detect incidents, respond to attacks, and recover.
- Tip: Align these policies with other industry standards like ISO 27001 or NIST. If you already have one of these frameworks, this can make things a lot easier!
Conduct regular risk assessments for ICT-related threats.
- DORA requires that you regularly evaluate risks to your digital systems and data. This includes assessing vulnerabilities, potential attack vectors, and business impact.
- Example: A financial services firm might decide to run quarterly assessments to identify weaknesses in its cloud storage security to meet this requirement.
Implement security measures (if you do not already have them in place).
- Security measures under DORA requirements include encryption, multi-factor authentication, and network segmentation. For a full list of these measures, reference the official DORA text.
- A backup and recovery plan for ICT disruptions is also required, as is monitoring ICT systems for anomalies and potential threats. This often takes the form of using monitoring tools and log analysis.
Lastly, employee training on security measures and ICT risk is required.
- Your staff must receive training in areas such as phishing, password security, and handling sensitive data.
DORA Compliance Checklist Pillar 2: ICT Incident Reporting Requirements
If you experience a system outage, data breach, or security incident, DORA sets strict rules about reporting the incident. DORA's cyber threat reporting obligations, for example, can require notifications in as few as four hours from the time of the incident. This initial report will need to explain what happened, when you found out, and how it impacts your business and/or your financial sector clients.
Requirements in this step include:
Develop an internal reporting mechanism for incidents, and figure out how you will identify and classify ICT-related incidents.
- ICT incidents under DORA are classified based on severity, and your response should be designed to match the severity of the incident. For example, a trading platform might classify a Distributed Denial-of-Service (DDoS) Attack as a high-severity incident requiring an immediate response.
- Establish policies for reporting major ICT-related incidents to the appropriate authorities within the required timeframe. Regulatory bodies need to be notified in the case of significant disruptions or cyberattacks.
Document and analyze incidents to improve processes and prevent recurrence.
- Every incident has to be logged, reviewed, and analyzed to improve security measures.
- After an incident, you should have policies in place to dictate how you will communicate incident impacts and remediation efforts to stakeholders.
DORA Compliance Checklist Pillar 3: Digital Operational Resilience Testing
DORA requires regularly testing your technology systems to ensure they can withstand problems and cyber attacks.
Organizations must conduct basic security checks of their systems on an annual basis that look for vulnerabilities that could be exploited. Every three years, more extensive testing, including simulated cyber attacks and disaster recovery exercises, needs to be performed.
Some organizations that fall under even more stringent DORA requirements (due to how pivotal they are to the financial sector) may need to go a step further and hire external security experts to conduct a penetration test. A penetration test is a good idea for all organizations, however, as it is the gold standard way to test your defenses in real-world situations.
In general, the requirements under this pillar are:
Conduct periodic testing of ICT systems, and perform penetration testing.
- Testing your security defenses against common threats like phishing and malware is required under DORA.
- Penetration testing is the industry-standard way to test your defenses!
Based on the results of your testing, develop remediation plans.
- For example, a company may find they need to update their firewall rules and disable unused ports after a penetration tester exposes vulnerabilities in their network.
Document testing outcomes and improvement measures.
- Under DORA requirements, organizations must maintain records of all testing activities, findings, and corrective actions.
DORA Compliance Checklist Pillar 4: Third-Party Risk Management
Lastly, your responsibility under DORA requirements extends to any vendors you rely on to serve your financial sector clients.
Every contract with a technology vendor needs to spell out precisely what they deliver, including uptime guarantees and security requirements. Then, you need to actively monitor whether vendors meet these requirements and regularly audit their performance.
DORA also requires that you plan for vendor failures, and demonstrate how you would switch to a different vendor if needed. One of the goals of this pillar is to help manage vendor concentration risk - organizations shouldn't rely too heavily on any single vendor.
Requirements include:
Create an inventory of ICT third-party providers.
- You'll need to document all of your vendors that provide ICT-related services. This can include the SaaS platforms you use, for example.
- Assign each vendor a risk level.
Carry out risk assessments for third-party ICT services.
- DORA requires you to evaluate the security posture of your vendors before and during the relationship.
- For instance, require your vendors to complete a security questionnaire or share their SOC 2 report.
Establish contractual agreements that define security and resilience expectations.
- Contracts should include cybersecurity requirements, incident response obligations, and compliance expectations relevant to your industry. For example, a payment processor might require its vendors to meet PCI DSS requirements.
Monitor third-party compliance with ICT risk requirements.
- Ongoing oversight of vendors' security practices is required. For example, you could conduct annual reviews of your cloud provider's security controls.
Develop exit strategies for critical third-party dependencies.
- Businesses must plan ahead for vendor disruptions, by having alternative providers or internal solutions ready.
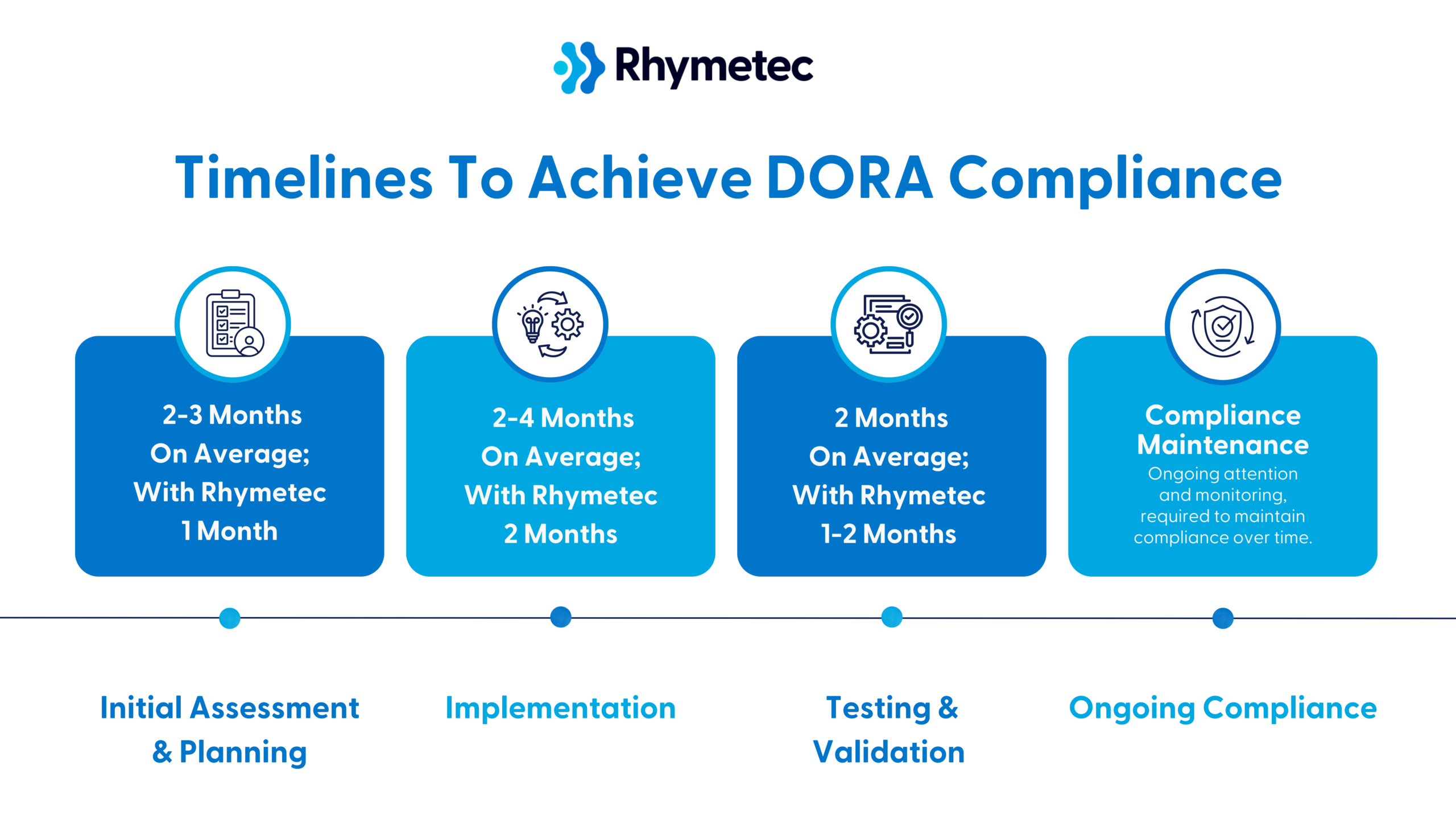
DORA Compliance Checklist Timelines: 6-9 Months Total On Average; 4-6 Months Total With Rhymetec
Below is a roadmap with timelines to give you an idea of what you can expect. Although these steps may vary depending on your organization's individual factors and needs, this should give you a general idea of what to plan for:
Initial Assessment and Planning (2-3 Months On Average; With Rhymetec 1 Month)
The first step is to understand where your organization stands in relation to DORA requirements. To do this:
- Bring in personnel from IT, security, legal, and business operations in order to understand the roles and impact across your entire organization. If you're a SaaS provider, include project managers who understand your technology stack and business leaders who manage financial sector relationships.
- Conduct a gap analysis, assessing where you currently are versus where you need to be to meet DORA requirements.
- Create an inventory of technology assets that support financial sector services (also known as mapping your ICT assets). You'll need to document every server, database, API, and third-party system you use.
After you have a clear understanding of your gaps, the next step is to develop a detailed implementation plan and allocate resources accordingly. Calculate costs for new tools, additional staff, training programs, and possible consulting help. Include both one-time costs (such as new monitoring systems) and ongoing expenses (such as additional security staff or regular testing).
Implementation (2-4 Months On Average; With Rhymetec 2 Months)
Now comes the actual work of building your compliance program:
- Update your documentation. Create or revise policies and procedures to meet DORA requirements, including incident response plans, business continuity procedures, and vendor management policies.
- Make your policies practical: Your incident response plan, for example, should include actual contact information and clear steps.
- Implement new controls. Deploy new security measures, as outlined by DORA requirements, and any monitoring tools or testing procedures you need.
- Update vendor management. You'll likely need to review and update contracts with critical service providers and add requirements for things like incident reporting and service levels.
Testing and Validation (2 Months On Average; With Rhymetec 1-2 Months)
Before finally achieving compliance, testing and validating your new controls is important. To do this:
- Conduct trial runs that allow you to practice your incident response procedures with realistic scenarios. The industry standard way to accomplish this is with a tabletop exercise, where your team works through a fictional but realistic scenario, such as what you would do in the event of a ransomware attack.
- Verify you can meet your recovery time objectives. Test scenarios where you'd need to switch between backup systems or alternative providers, document any gaps you find, and adjust your procedures accordingly based on what you find.
- Have legal and compliance experts review your documentation to make sure it will hold up under regulatory scrutiny.
Ongoing Compliance (Continuous)
Compliance requires ongoing attention and monitoring.
Organizations that are serious about maintaining compliance should schedule regular reviews of their compliance program, such as on a quarterly basis. This is important because changes in your business or technology impact your DORA obligations.
Monitor metrics about system performance, incident response times, and vendor service levels to spot potential issues before they impact your compliance.
Lastly, use lessons learned from any incidents that occur to continually improve your procedures, and stay informed about any changes in regulatory best practices and guidance.
Business Benefits of DORA Compliance
While DORA requirements may seem daunting, organizations that embrace these changes stand to gain significant competitive advantages in the European market. Complying with DORA offers substantial business advantages that extend far beyond regulatory adherence.
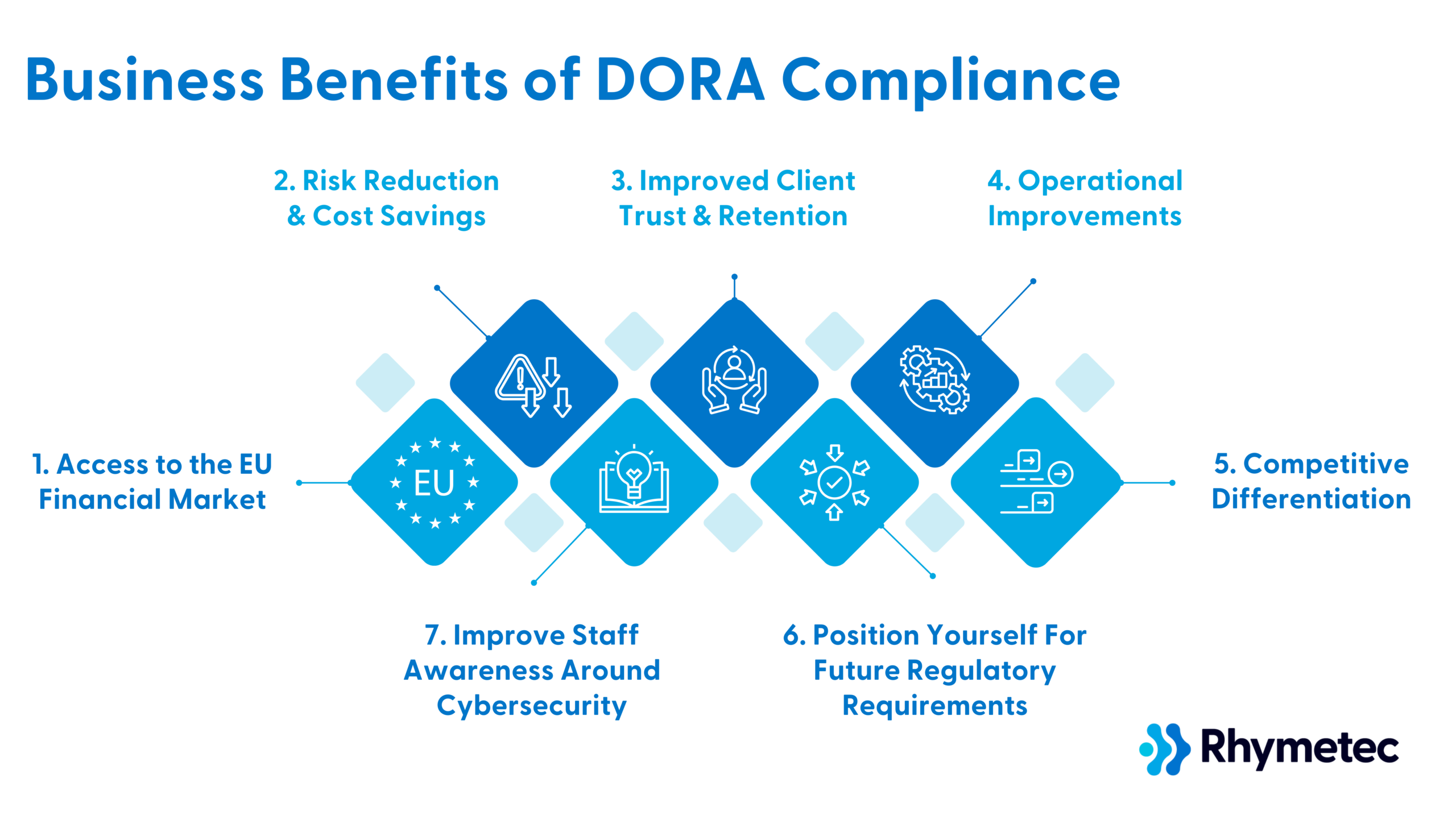
Here's how meeting DORA requirements strengthens your market position and creates new opportunities for your business:
1. Access to the EU Financial Market
By meeting DORA requirements, you gain the ability to serve financial institutions across the European Union.
Banks, insurance companies, and investment firms must work with DORA-compliant technology providers. Your non-compliant competitors get excluded from EU financial sector opportunities, while you can expand your market reach. This creates a clear competitive advantage.
For example, a small cloud storage provider that achieves DORA compliance can compete for contracts with major EU banks, opening up revenue streams that were previously inaccessible. Without compliance, they'd be limited to serving non-financial clients or risking their potential EU financial clients selecting compliant competitors.
2. Risk Reduction and Cost Savings
The approach to risk management under DORA is intended to help prevent costly incidents before they occur. While it may seem like a costly upfront investment to implement security controls, it costs far less than recovering from major technology failures or cyber-attacks.
For example, DORA-style monitoring enables companies to discover and fix potential system failure points before they can lead to massive revenue loss and reputational damage.
The time and money spent on monitoring and backup systems is an extremely wise investment compared to the potential losses and reputational damage a system failure could incur on many business's daily operations.
3. Improved Client Trust and Retention
Financial institutions face intense scrutiny over their technology providers. DORA compliance sends a strong signal to them that your company is committed to security and operational excellence, and will be less likely to cause them issues.
Compliance enables you to provide detailed evidence of your resilience measures, making it easier for financial clients to trust you with their operations.
It also serves to shorten sales cycles, as your team can readily demonstrate their security and reliability measures to prospective financial sector clients.
4. Operational Improvements
The rigorous testing that DORA requires can reveal opportunities to improve your operations.
Let's take a specific example to explain how:
A trading software provider implementing DORA's system mapping requirements could discover they're running redundant data validation checks across multiple different services.
By figuring this out, they can reduce their infrastructure costs while improving system performance. Without undergoing the compliance process, whether it be DORA or other regulations, issues like these may have never been discovered.
5. Competitive Differentiation
Achieving compliance with DORA sets you apart even in markets beyond the EU financial sector.
Take, for instance, a cloud database provider trying to compete for contracts with healthcare providers or government agencies. While DORA compliance isn't required for these sectors, the provider could leverage their DORA-compliant controls and processes to demonstrate their commitment to operational resilience, potentially helping win contracts over less rigorously controlled competitors.
Meeting DORA requirements provides an overall boost to your marketing and sales efforts as well. Your team can use compliance as a differentiator in marketing materials and sales meetings.
6. Position Yourself For Future Regulatory Requirements
Digital operational resilience only stands to become more important across all sectors. DORA-compliant organizations can get ahead of the curve and position themselves for future regulatory requirements.
Experts anticipate similar regulations to emerge in other regions and industries. DORA-compliant organizations may find themselves already 80% compliant with future regulations, saving significant time and resources compared to competitors who need to start from scratch.
By implementing DORA requirements now, you're preparing your business for future compliance needs while gaining all of the immediate security and operational benefits.
7. Improve Staff Awareness Around Cybersecurity
Implementing DORA requirements builds valuable expertise within your organization, at every level. Your team develops skills and know-how in risk management, incident response, and operational resilience that benefit all aspects of your business.
The value of DORA compliance lies not just in meeting regulatory requirements, but also in building a more resilient and competitive business. While the implementation process requires substantial effort and investment on your part, the resulting business benefits far outweigh the costs.
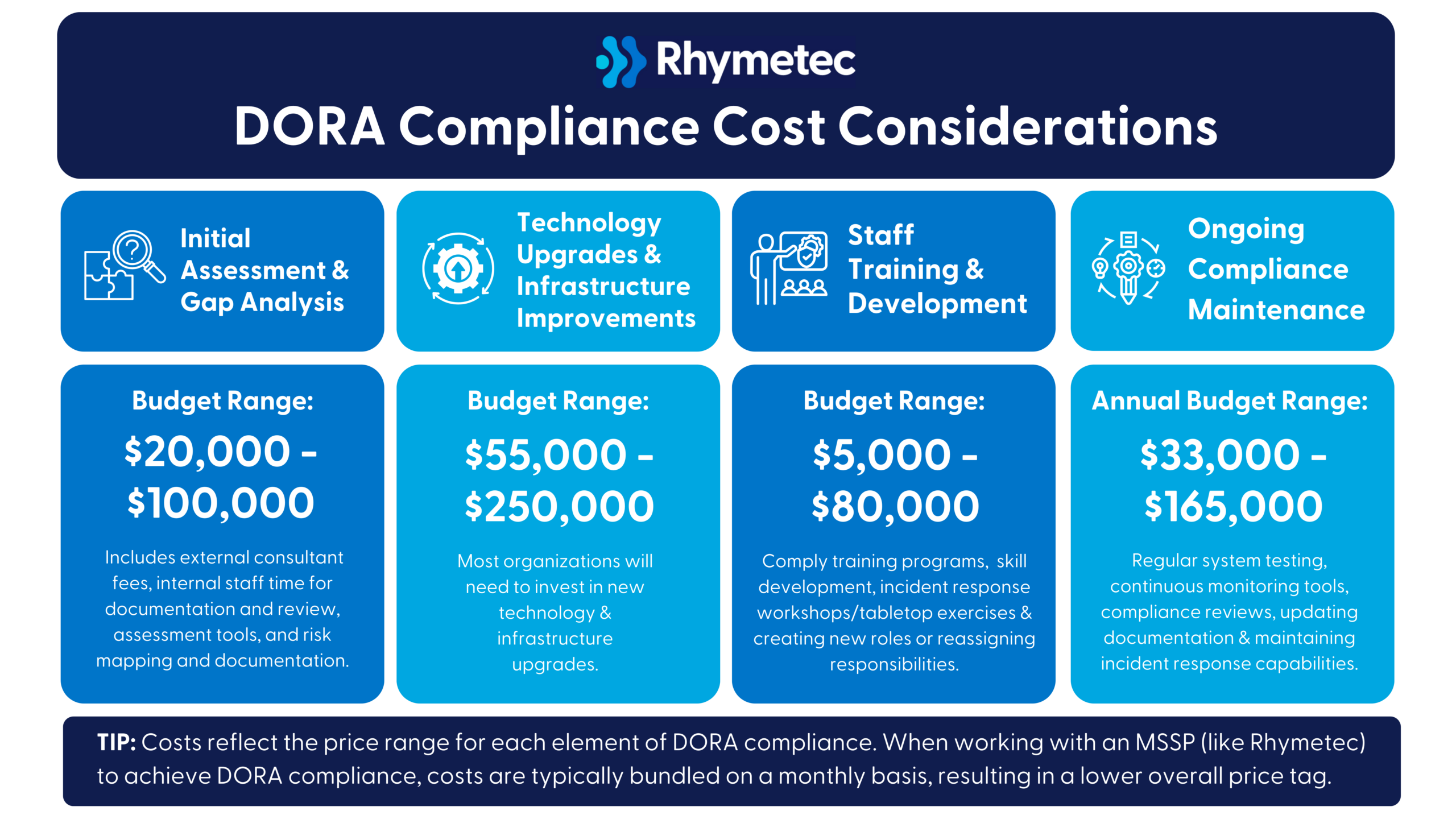
DORA Compliance Checklist: Cost Considerations
Costs to achieve DORA compliance will vary depending on your organization's size, complexity, and technology infrastructure. Here is an estimation of what you can anticipate:
Initial Assessment and Gap Analysis
Budget Range: $20,000 - $100,000
This includes external consultant fees, internal staff time for documentation and review, assessment tools, and risk mapping and documentation.
Technology Upgrades and Infrastructure Improvements
Budget Range: $55,000 - $250,000
Most organizations will need to invest in improved monitoring systems, incident response capabilities and technologies, security information and event management (SIEM) upgrades, additional backup and recovery infrastructure, and compliance tracking and reporting tools.
Staff Training and Development
Budget Range: $5,000 - $80,000
Investments include compliance training programs, cybersecurity skill development, incident response workshops/tabletop exercises, and creating new internal roles or reassigning responsibilities.
Ongoing Compliance Maintenance
Annual Budget Range: $33,000 - $165,000
Recurring annual costs include regular system testing, continuous monitoring tools, compliance reviews, updating documentation, and maintaining incident response capabilities.
Potential Hidden Costs of Fulfilling Your DORA Compliance Checklist
Potential hidden costs can include additional administrative overhead, needing to redesign existing processes, productivity loss during implementation, vendor management, and a possible temporary reduction in service delivery.
Cost Mitigation Strategies
Fortunately, there are a few things you can do it mitigate the impact of the cost associated with achieving DORA compliance:
- Start early to spread out implementation costs.
- Use a phased implementation approach and spread costs over multiple budget cycles.
- Use a compliance automation tool.
- Leverage a vCISO service to take the work off your plate entirely while receiving the highest level of service and expertise (to see costs associated with this option, check out our vCISO pricing blog).
DORA compliance is an investment in your organization's resilience and future competitiveness. While the upfront costs may seem hefty, they pale in comparison to potential losses from a major technology failure, cybersecurity incident, or regulatory non-compliance risks.
Practical Implementation Tips
Fortunately, you don't have to build everything from scratch to implement DORA requirements.
A compliance automation platform can significantly streamline the process by essentially enabling you to compile and document everything you already have. These tools enable you to automatically track your compliance progress, generate documentation, and alert you to potential gaps.
(For more information on exactly how the compliance automation process works, check out our blog post on this topic.)
Working with a virtual Chief Information Security Officer (vCISO) can also dramatically simplify your DORA compliance journey. A vCISO brings a wealth of experience in regulatory compliance and helps you avoid common pitfalls while accelerating your implementation timeline, all at a fraction of the cost of a full-time CISO.
By combining compliance automation tools with vCISO support, you can keep costs under control while meeting your DORA requirements in the fastest timeframe possible.
Additional Resources: Official EU Documentation
- Official Text of DORA - The full regulation text and requirements. This is the ultimate source of authority for any questions on specific requirements and should be referenced when there are questions about the interpretation of requirements or obligations.
- European Banking Authority (EBA) Guidelines - Technical standards and implementation guidance, as well as the latest updates on DORA implementation. The EBA's Q&A tool is an incredibly useful resource and can be used to answer common implementation questions.
- European Securities and Markets Authority (ESMA) - ESMA is one of the regulators responsible for overseeing DORA compliance. They provide updates and interpretations of DORA requirements.
In Conclusion: Get Started Today On Fulfilling Your DORA Compliance Checklist
DORA represents an opportunity to gain access to a lucrative segment of the EU marketplace, improve client trust, and strengthen your organization's operational resilience.
The most efficient way to begin your compliance journey is by engaging a virtual CISO (vCISO) who can conduct a gap assessment for you, leverage a compliance automation platform on your behalf, and guide your implementation while keeping costs manageable.
Our team at Rhymetec is happy to answer any questions you may have, and to walk you through how to tailor this DORA compliance checklist to your organization. Contact us today for more information.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We've worked with over 700 companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
Interested in reading more? Check out more content on our blog: