Justifying the return on cybersecurity investments can be hard. Some things are relatively easy, especially with the help of tools like compliance automation platforms. You have to comply with legal requirements and customer demands to see your SOC 2 report, but what about security that goes beyond regulatory requirements?
In a business full of competing interests, managers asking for new hires, and the marketing team wanting to spend additional money, security often falls by the wayside – but it shouldn’t.
That’s one of the reasons at Rhymetec we love checking out Verizon’s annual Data Breach Investigation Report (DBIR). Verizon’s DBIR shows exactly why companies need to move beyond compliance and implement proactive controls.
Regulators are often years behind the latest trends in the industry – companies that just focus on compliance often fail to implement safeguards and controls that could save their business millions of dollars in lost business, fines, and legal fees.
So, what are the big takeaways from this year’s DBIR? Well, there are quite a few:
Generative AI, Compliance, and Accidental Leaks
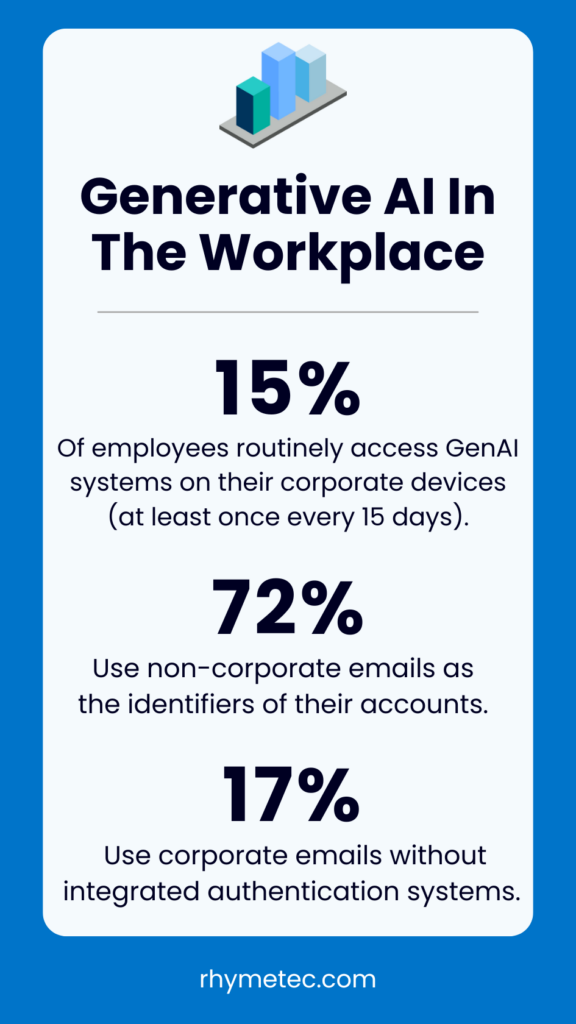
You almost certainly have employees at your company feeding data into AI models that you don’t know about. One of the findings that should be the most alarming to information security leaders is that, according to the DBIR:
“15% of employees were routinely accessing GenAI systems on their corporate devices (at least once every 15 days). Even more concerning, a large number of those were either using non-corporate emails as the identifiers of their accounts (72%) or were using their corporate emails without integrated authentication systems in place (17%), most likely suggesting use outside of corporate policy.”
Many organizations pick one or two AI vendors and work with those, and accept a certain degree of risk. However, employees signing up directly for generative AI applications can pose severe risks, particularly to organizations that deal with highly sensitive intellectual property, regulated data such as health records, or even national security and classified data.
For example, imagine an employee at a defense contractor decides to use DeepSeek to analyze CUI (controlled unclassified information) that a contractor sends them. They likely unknowingly just sent that data directly to China.
Getting a handle on “shadow SaaS”, and particularly which AI applications employees may be sending sensitive data, is likely to be one of the most important issues vexing information security teams in the next five years.
Third-Party Risk Remains Highly Relevant in The 2025 Verizon Data Breach Report
Another key finding in the 2025 DBIR that security professionals should be paying close attention to is the dramatic increase in third-party involvement in breaches. According to Verizon’s analysis, third-party involvement in breaches doubled from 15% to 30% in just one year. This isn’t merely a statistical blip – it represents a fundamental shift in how attackers are approaching your organization’s security perimeter.
As in all things in life, there are tradeoffs. As organizations increasingly adopt convenient SaaS solutions to solve various business challenges, in many cases, they unwittingly dramatically expand their attack surface (sometimes even the business doesn’t know what their attack surface is, such as with shadow generative AI use).
The report specifically highlights how several high-profile breaches in services like Change Healthcare, CDK Global, and Blue Yonder exposed sensitive data and created substantial business interruption events across entire industries:
Healthcare providers couldn’t process claims, auto dealerships lost access to their systems, and retailers and food services companies found themselves unable to manage inventory. When your critical business functions rely on third-party SaaS providers, their security posture becomes your operational vulnerability.
While compliance frameworks like SOC 2 have recognized third-party risk for years, the real-world impact is growing faster than many organizations’ vendor management programs can adapt.
This data should serve as a wake-up call: Today’s interconnected business ecosystem requires a much more proactive approach to vendor security assessment, continuous monitoring, and contingency planning. Organizations that fail to evolve beyond “check the box” vendor management will increasingly find themselves dealing with the consequences of their partners’ security failures.
Malware Is Fueling Identity-Based Attacks
On page 54 of the report is perhaps one of the most interesting insights of the 2025 DBIR. In a section titled “Infostealers Galore”, Verizon discusses one of the most prominent threats to organizations today – infostealer malware.
Infostealers are a type of malware that infects a victim’s computer and siphons all of the passwords and session cookies the victim has saved on their browser, sessions for applications such as Discord, crypto wallet keys, autofill data, and basically any other sensitive or valuable lightweight data from the device. This data is then sent back to the threat actor’s infrastructure, where individual victims’ information is sold as an “infostealer log” containing one victim’s data.
As you can imagine, there is a trove of high value information for threat actors to leverage within this data to include session cookies which can be used to hijack active sessions to facilitiate account takeover attacks for major web applications and e-commerce companies, crypto wallet keys which can allow the threat actor to steal currency, and even credit card data from autofills which can facilitate fraud.
However, this malware can also grab corporate emails and passwords for SaaS applications, VPN’s, corporate bank accounts, and other critical information. Verizon estimates that 30% of the tens of millions of logs out there come from devices that are corporate-owned, an absolutely astounding figure.
A discerning observer might ask an obvious question: Does the prevalence of corporate credentials, session cookies, and information available in the stealer log ecosystem enable ransomware groups and other similar threat actors?
Well, Verizon has the answer there, too.
“By examining some of the victims posted to the ransomware extortion sites, we found that 54% of the victims had their domains show up in at least one infostealer log or in marketplace postings, and 40% of those logs contained corporate email addresses.” – Verizon Data Breach Report 2025, page 57.
This type of analysis is critical, as threat actors are continuously evolving their tactics, techniques, and procedures in response to improvements in organizational cybersecurity. Oftentimes, threat actors will use whatever is easiest, and active sets of corporate credentials and session cookies floating around in the criminal ether is indeed a pretty easy way to get access to some high-value systems.
Ransomware Is On the Rise, Sort Of
Speaking of ransomware, many organizations make the mistake of believing that they are too small for ransomware groups and threat actors to target.
However, this belief couldn’t be further from the truth. One of the most interesting and relevant findings from the DBIR was the data around ransomware attacks in 2024. While attacks continue to rise, victim behavior and attacker strategies are evolving in notable ways.
Ransomware incidents jumped dramatically, showing a 37% increase from last year. These attacks now represent 44% of all data breaches analyzed – up from 32% in the previous report. Nobody expected ransomware to go away, but this data shows that even the notable law enforcement takedowns of Lockbit, Black Cat, and other high-profile ransomware groups has at best dented this highly financially lucrative criminal operation.
However, it’s worth digging in a bit on the ransomware piece of the report because the increase in ransomware as a proportion of all attacks doesn’t tell the whole story. The reports section on ransom payments shows a potential silver lining:
Both the frequency and size of ransom payments are decreasing. The median ransom payment dropped to $115,000 in 2024, down from $150,000 in 2023. More significantly, 64% of victims now refuse to pay ransoms altogether – a substantial increase from 50% just two years ago.
While the report doesn’t directly make the connection, organizations improving backup and recovery combined with defensive measures may be fueling another trend – the increased targeting of small and midsize businesses by ransomware operators.
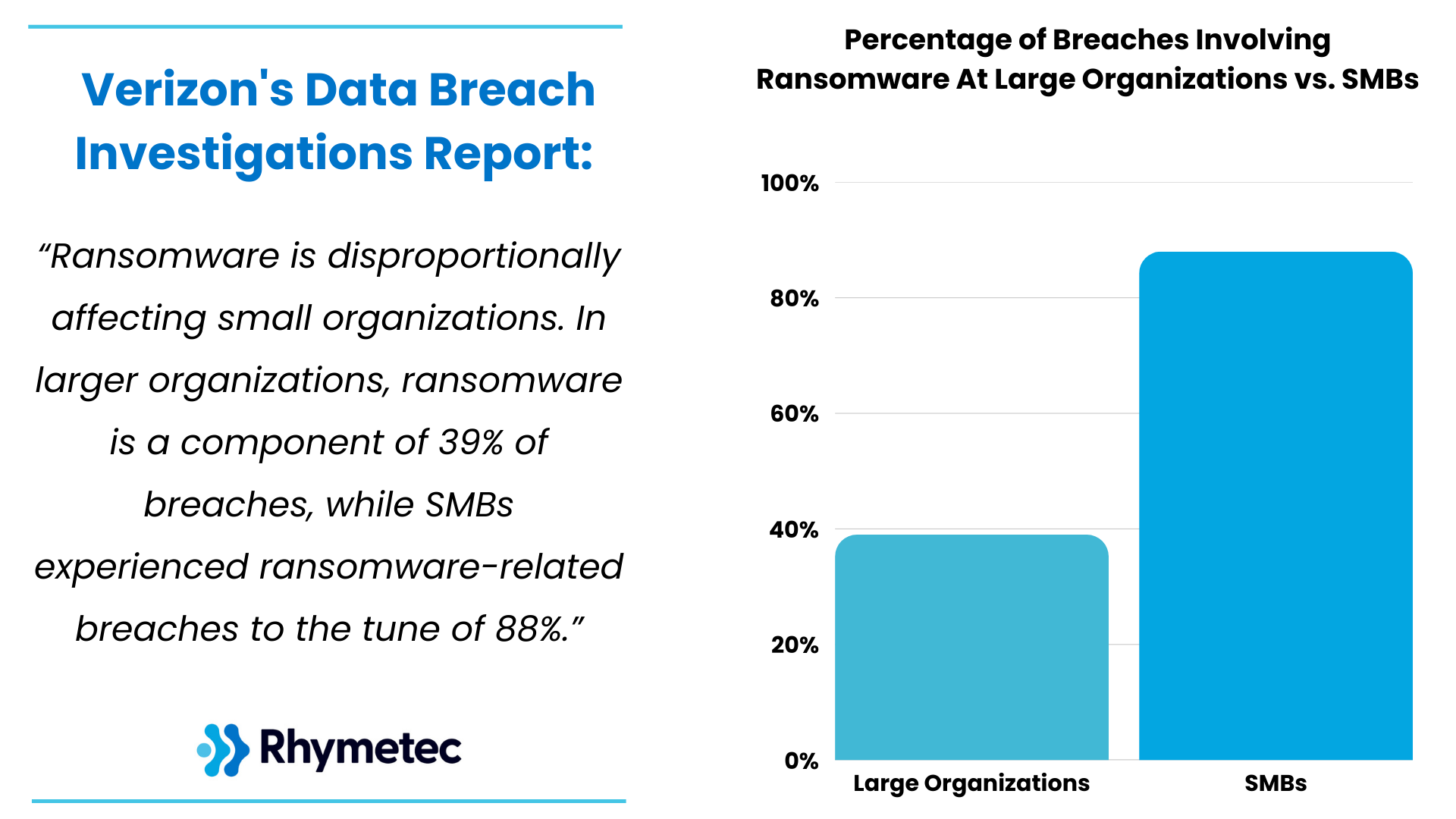
Perhaps the most alarming finding is how severely ransomware affects smaller organizations. While ransomware appears in 39% of breaches at large enterprises, it’s present at a staggering 88% of breaches at SMBs.
This disparity likely reflects the resource gap in cybersecurity preparedness. Smaller organizations typically have less robust backup solutions, fewer security controls, and limited incident response capabilities, making them both easier targets and more likely to suffer catastrophic impacts.
Concluding Thoughts: The Verizon Data Breach Report 2025
The 2025 Verizon Data Breach Report paints a clear picture of an evolving threat landscape that demands more than just a checkbox approach to security. Compliance frameworks like SOC 2 and ISO 27001 provide a valuable foundation, but going beyond them is essential for organizations to protect themselves from sophisticated ransomware groups and other threat actors.
The data tells a compelling story: Third-party risks have doubled, credential theft via infostealers is directly fueling ransomware attacks, and shadow AI usage presents entirely new vectors for data loss. These threats are often moving faster than regulatory and best practice frameworks can adapt.
At Rhymetec, we recommend that organizations build their compliance foundation with targeted security investments that address these emerging threats:
- Implement continuous monitoring for external threats.
- Develop comprehensive controls for third-party risk management that go beyond questionnaires.
- Establish clear policies and technical controls for AI platform usage.
- Prioritize edge device security given their increased targeting by threat actors.
- Develop security strategies that account for the human element, which remains involved in 60% of breaches.
The most successful organizations will be those that view compliance as the starting point, not the destination, of their security journey. And most importantly, those who stay educated on how the threat landscape is shifting over time.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.