Over 80% of breaches involve weak or misused credentials, according to Verizon’s Data Breach Investigations Report. This is a clear example of just one risk that represents both a security and a compliance risk for organizations, as it impacts everything from the efficacy of your cybersecurity program to compliance audits, contracts, and revenue.
For federal contractors handling Federal Contract Information (FCI), CMMC Level 1 directly addresses this risk and other pressing ones. Level 1 is designed to encourage basic cyber hygiene, and outlines 15 controls that help safeguard sensitive data and maintain eligibility for federal contracts.
In this blog post, we will go over a CMMC Level 1 checklist and requirements, starting with which types of organizations Level 1 applies to:
Government contractors, subcontractors, and suppliers in the federal supply chain that handle FCI (Federal Contract Information) likely fall into CMMC Level 1. This tier is designed for contractors and subcontractors working with the Department of Defense who don’t store or process sensitive technical data but still have access to basic contract details, for example.
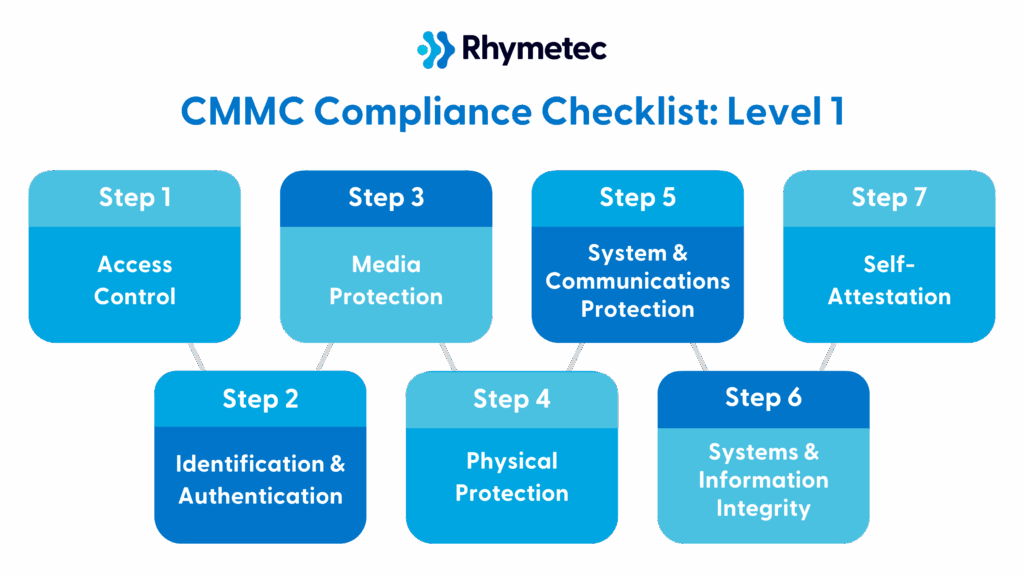
CMMC Level 1 has 15 requirements. Your organization must meet these 15 requirements and self-attest against them each year. The requirements fall under basic safeguarding practices and are derived from the Federal Acquisition Regulation (FAR) 52.204-21.
Below is our CMMC Level 1 Checklist, starting with the gap assessment process and then walking you through the 15 requirements that need to be addressed:
Getting Started – CMMC Level 1 Checklist: Gap Assessment
“At Rhymetec, we always start with a gap assessment. A gap assessment against the NIST 800-171 controls is a must-have…It helps you determine if you have any missing controls or if you have any gaps in your compliance, so you can start putting together a roadmap for completing the remaining controls.” – Metin Kortak, Rhymetec
The aim is to compare your current environment against the required controls. This process tells you what needs to be done before you’re ready to self-attest or move into the certification phase.
CMMC 2.0 also allows you to use a Plan of Action and Milestones (POA&M) to formally track missing controls and your plan for implementing them:
“In 2.0, CMMC came out with a final action and milestones plan. This document essentially allows you to create implementation plans for controls that are missing in your gap assessment, so that you can remediate these controls within a certain amount of time. This is also something you can work with third parties on or conduct your own self-assessment.” – Metin Kortak, Rhymetec
Next, we’ll break down what you need to do to meet the requirements of CMMC Level 1.
CMMC Level 1 Checklist
If your organization handles only FCI and not CUI, then CMMC Level 1 likely applies to you.
“If you’re only handling FCI and not CUI, you fall into Level 1. Level 1 is an order of magnitude less involved than Level 2. It actually only has 15 requirements that are heavily aligned with a subset of the NIST 800-171 framework. You must meet these 15 requirements, and then you just need to self-attest against them each year.” – Matt Bruggeman, A-LIGN
This tier is designed for contractors and subcontractors working with the Department of Defense who don’t store or process sensitive technical data but still have access to basic contract details, for example. The 15 requirements fall under basic safeguarding practices and map to NIST 800-171, Rev. 2, specifically from Federal Acquisition Regulation (FAR) 52.204-21.
Below are the 15 action items you need to address for CMMC Level 1, divided into clear sections based on our expert advice.
*For a full list of these items with a greater level of technical detail, see the official FAR 52.204-21 documentation.
Access Control
1. Limit system access to authorized users.
To reduce the risk of unauthorized exposure of data, only users with a business need should be able to log in to systems that store or process FCI.
In practice, what you’ll need to do is action items such as setting up role-based access controls, implementing IAM (identity and access management) tools, and regularly auditing user access to remove accounts if they are no longer needed.
These types of security measures entail broader business benefits, as they reduce the risk of insider threats and limit the extent of potential damage in case of compromised credentials.
2. Limit system access to authorized devices.
Even if a user is not authorized, their device might be without the proper controls.
All laptops and mobile devices connected to your systems should be managed to prevent untrusted endpoints from introducing threats. Implementing Mobile Device Management or endpoint detection and response solutions are industry-standard methods to accomplish this and prevent threats from entering through untrusted endpoints.
3. Control access to system functions (e.g., user roles).
Users should only be able to perform actions appropriate for their job (such as admin tasks being restricted to IT staff). It is critical to define roles and assign permissions accordingly, and restrict admin rights to select personnel.
These measures vastly minimize the risk of unauthorized changes or even accidental misconfigurations being made.
4. Verify control connections to external systems.
Any systems that link with a third party (such as a cloud storage provider or file-sharing services) can become gateways for data leaks. As such, they must be reviewed and approved to prevent unauthorized data transfers.
Organizations can accomplish this by maintaining an inventory of all third-party connections, reviewing and approving integrations before use, and monitoring data flow between internal systems and external services. This serves to protect against data loss via insecure APIs or file-sharing platforms.
Identification and Authentication
5. Require user identification before granting system access.
Every action should be traceable to an individual.
Action items to accomplish this objective include assigning unique user IDs to all personnel, eliminating any shared accounts, and enabling logging to tie activity back to specific users.
The business value of this step is crucial, as it creates accountability and aids in forensic investigation in case of incidents.
Media Protection
6. Sanitize or destroy media containing FCI before disposal.
Leaving data on discarded devices is a common but extremely preventable risk.
Simply establishing a process to wipe drives using certified tools, physically destroy storage devices when decommissioned, and document sanitization or destruction (for audit purposes) accomplishes this and prevents data leakage from improperly discarded hardware.
7. Protect FCI stored on removable media and external drives.
Portable storage can create unique risks when used off-site, and it’s critical to protect data in the event devices are lost or stolen.
Avoiding the use of removable media altogether is the best way to circumvent this risk entirely, but if your organization has to use removable media, you should be encrypting USB drives and external hard drives and locking physical storage devices when not in use.
Physical Protection
8. Limit physical access to systems storing or processing FCI.
Unauthorized individuals shouldn’t be able to walk up to a server or terminal.
Acceptable measures to fulfill this requirement under CMMC Level 1 include using keycards, biometric access, or badge systems, monitoring entry points with surveillance, and keeping visitor logs. All of these measures greatly reduce the risk of physical tampering and/or data theft.
System and Communications Protection
9. Monitor and control communications at system boundaries.
Network traffic needs to be inspected and controlled to catch threats early.
Firewalls and intrusion detection tools are used to monitor traffic entering or leaving your network and block suspicious activity, and setting up logging and alerting for traffic anomalies cues you into threats early on.
10. Implement boundary protections such as firewalls and filters.
Network segmentation can both contain threats and reduce their impact.
Actions such as applying email filters and web proxies, enforcing traffic rule zones between zones, and creating VLANs to isolate sensitive systems will limit the radius of a breach and keep attackers from causing further harm.
11. Use cryptographic methods when transmitting FCI.
Sensitive data in transit needs to be protected from being intercepted. The recommended controls around this are enforcing TLS for all network communications, using secure transfer protocols, and encryption.
Systems and Information Integrity
12. Identify system flaws (e.g., patches) and manage them.
Outdated systems are prime targets for attackers. This is why it is crucially important to keep systems up to date by applying security patches regularly.
For CMMC Level 1, organizations need to be accomplishing this by prioritizing critical updates, applying patches on a schedule with a documented process, and regularly checking for software updates.
13. Take steps to protect against malicious code, such as antivirus.
Malware can compromise systems and exfiltrate data. To combat this risk, deploying anti-malware tools to block viruses and other threats that could compromise FCI are industry standard steps.
14. Monitor system activity for security events.
Without visibility, threats can go undetected for months. It’s crucial to set up a way to track system logs in order to detect unusual behavior that could indicate a breach or misuse. To accomplish this, organizations often implement a SIEM platform, or other tools to monitor for suspicious behavior.
15. Perform periodic system scans and take corrective action.
Running regular vulnerability scans to detect weaknesses and applying fixes or updates as needed to keep systems secure is something every organization should be doing. The business value of this last control is keeping your security posture strong and supporting audit readiness.
CMMC Level 1 Checklist: Self-Attestation For CMMC Level 1
Unlike Level 2 and Level 3, Level 1 does not require a third-party assessment.
Instead, your organization must annually self-attest to meet all 15 practices. That attestation must come from a senior company official and be submitted through the Supplier Performance Risk System (SPRS).
Most organizations will need to document the following for Level 1:
- How are these 15 controls above are implemented
- Which systems process or store FCI
- Who is responsible for each requirement
- Dates of the last review and updates
Although Level 1 is a massive degree less resource-intensive than Level 2 or 3, that doesn’t mean that accountability is any less important! Contractors who don’t meet these requirements can face contract risks.
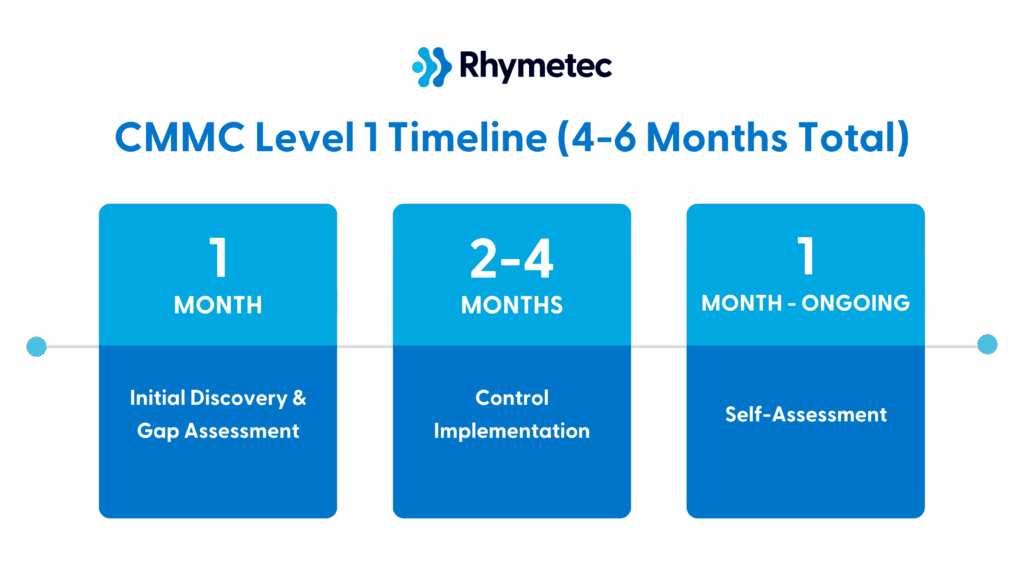
Here is how long you can anticipate CMMC Level 1 to take:
Partner For Success: Work With An Accredited C3PAO
Meeting CMMC requirements is a complex process, even for Level 1.
The good news is that you don’t have to do it alone. Our partnership with industry leader A-LIGN, an accredited C3PAO, gives you access to both the security legwork needed to meet requirements as well as certified assessment services. Working with trusted partners speeds up the timeline for CMMC.
Together, we help organizations prepare for CMMC with confidence. Whether you are just getting started or finalizing your readiness for an assessment, we’re here to support your compliance journey with security expertise and a trusted C3PAO partner.
C3PAOs are the only organizations authorized by the CyberAB to perform official CMMC assessments, if you need to go beyond self-assessments. Their involvement is essentially a must-have for any contractor aiming for certification. Meanwhile, as a Registered Provider Organization (RPO), Rhymetec works hand-in-hand with A-LIGN to help you prepare for that assessment.
RPOs are approved to offer consulting and readiness support, and help you implement required controls, remediate gaps, and make sure your security practices and documentation align with CMMC standards.
Together with A-LIGN, we are proud to offer this streamlined option for our clients. Contact us today to get started.