In our recent CMMC webinar, we joined forces with Vanta and A-LIGN to discuss the updated CMMC 2.0 and what organizations should be doing now to meet the requirements. Morgan Kaplan, Director of USG Strategy & Affairs at Vanta, moderated a lively discussion between Metin Kortak, Rhymetec CISO, and Matt Bruggeman, Director of Federal Sales at A-LIGN.
This Rhymetec CMMC Compliance Checklist for CMMC Level 2 is directly based on their discussion and pulls in expert insights from the webinar. Check out the recording of the full webinar here.
First, What Is CMMC?
CMMC, or the Cybersecurity Maturity Model Certification, is the Department of Defense's approach to standardizing cybersecurity requirements across its supply chain. It protects Controlled Unclassified Information (CUI) by requiring contractors (and many subcontractors as well) to meet security practices based on the type of work and data they handle.
As Rhymetec CISO Metin Kortak explained in our webinar:
"CMMC is a framework that's been developed by the US Department of Defense, and it really applies to anyone who's working with the Department of Defense and also processes, transmits, or stores controlled unclassified information. If you're processing that information and you're also working on direct contracts with the Department of Defense, or if you're one of their subcontractors, that means CMMC might apply to you." - Metin Kortak, CISO at Rhymetec
That scope includes contractors, manufacturers, software vendors, and cloud service providers that deal with DoD contracts even indirectly. This Rhymetec CMMC Compliance Checklist breaks down what's required and how to build a roadmap that aligns with contract timelines for CMMC Level 2. (If you need CMMC Level 1, check out our CMMC Level 1 Checklist).
You can also contact our team today and we'd be happy to walk you through everything you need to know.
Contact
How Does The Updated CMMC Version 2.0 Differ From The Original Version 1.0?
CMMC 2.0 simplifies the framework while reinforcing its core goal to protect sensitive data within the Defense Industrial Base (DIB). The shift from Version 1.0 to 2.0 reflects feedback from industry stakeholders who found the original model extremely onerous to implement:
"CMMC 1.0 was quite strict and required organizations to go through many additional requirements outside of NIST 800-171. This made the process extremely difficult, especially for organizations that need to comply with other government compliance frameworks such as FedRAMP. Based on the feedback received, 2.0 is a less strict version of CMMC, while still maintaining the core security requirements.” - Metin Kortak, CISO at Rhymetec
CMMC 1.0 introduced five maturity levels and included additional practices and documentation beyond NIST 800-171. This generated a lot of confusion for subcontractors and SaaS providers, especially those also working toward FedRAMP.
CMMC 2.0 successfully restructured the model around three levels and removed the unique CMMC-only requirements. The new version falls under basic safeguarding practices and are derived from the Federal Acquisition Regulation (FAR) 52.204-21, which directly references and relates to NIST SP 800-171 as part of its requirements.
This change reduces redundancy and increases compatibility with other federal frameworks. With the updated version, CMMC consultants have seen renewed customer interest:
"In the past, in terms of the requirements themselves, it's been more around NIST 800-171, plus a couple of other CMMC requirements. Recently, there have been updates to the CMMC framework. They've updated from Version 1.0 to 2.0. We've seen a lot of interest from our customers about this new version of CMMC." - Metin Kortak, CISO at Rhymetec
This renewed interest is likely since the assessment requirements have evolved. The new version maintains some elements of the previous requirements, but refines the role of C3PAOs (Certified Third Party Assessor Organizations):
"C3PAOs come in and assess you against the requirements, depending on the level that you're at. Our goal is to validate that the sensitive data is actually being protected, because looking historically at just relying on self-attestations to 800-171 for anybody within the supply chain has not been sufficient." - Matt Bruggeman, A-LIGN
In short, CMMC 2.0 is:
- Better aligned with existing industry standards.
- Highly adaptable to real-world constraints.
- More accessible for businesses supporting DoD missions.
Getting Started: Determining Which Level You Need and A Gap Assessment
Before you get started on working through your CMMC compliance checklist (for whichever level you need), it’s important to understand what type of data your organization handles.
This will determine which certification level of CMMC applies to your business:
"The first thing is understanding what type of data you process. If you don't know that, working with a partner to help you determine that can be helpful, because that's going to help you figure out which level of compliance you're going to need to do for CMMC." - Metin Kortak, CISO at Rhymetec
Determining Which Type of Organization Your Organization Handles
Two main types of information matter when it comes to CMMC:
- Federal Contract Information (FCI): Any information provided by or generated for the government under a contract that’s not intended for public release. Include project timelines, internal communications, and organizational charts related to a DoD contract.
- Controlled Unclassified Information (CUI): More sensitive than FCI. This is information that the government has decided needs to be protected, but doesn’t meet classification levels such as “Secret” or “Top Secret”:
“CUI is sensitive information that does not meet the criteria for classification but must still be protected. It is Government-created or owned UNCLASSIFIED information that allows for, or requires, safeguarding and dissemination controls in accordance with laws, regulations, or Government-wide policies.” - Department of Defense
Examples of CUI include software code related to defense programs, incident response reports, training content, documentation for DoD systems, and API guides that define how systems interoperate with DoD environments.
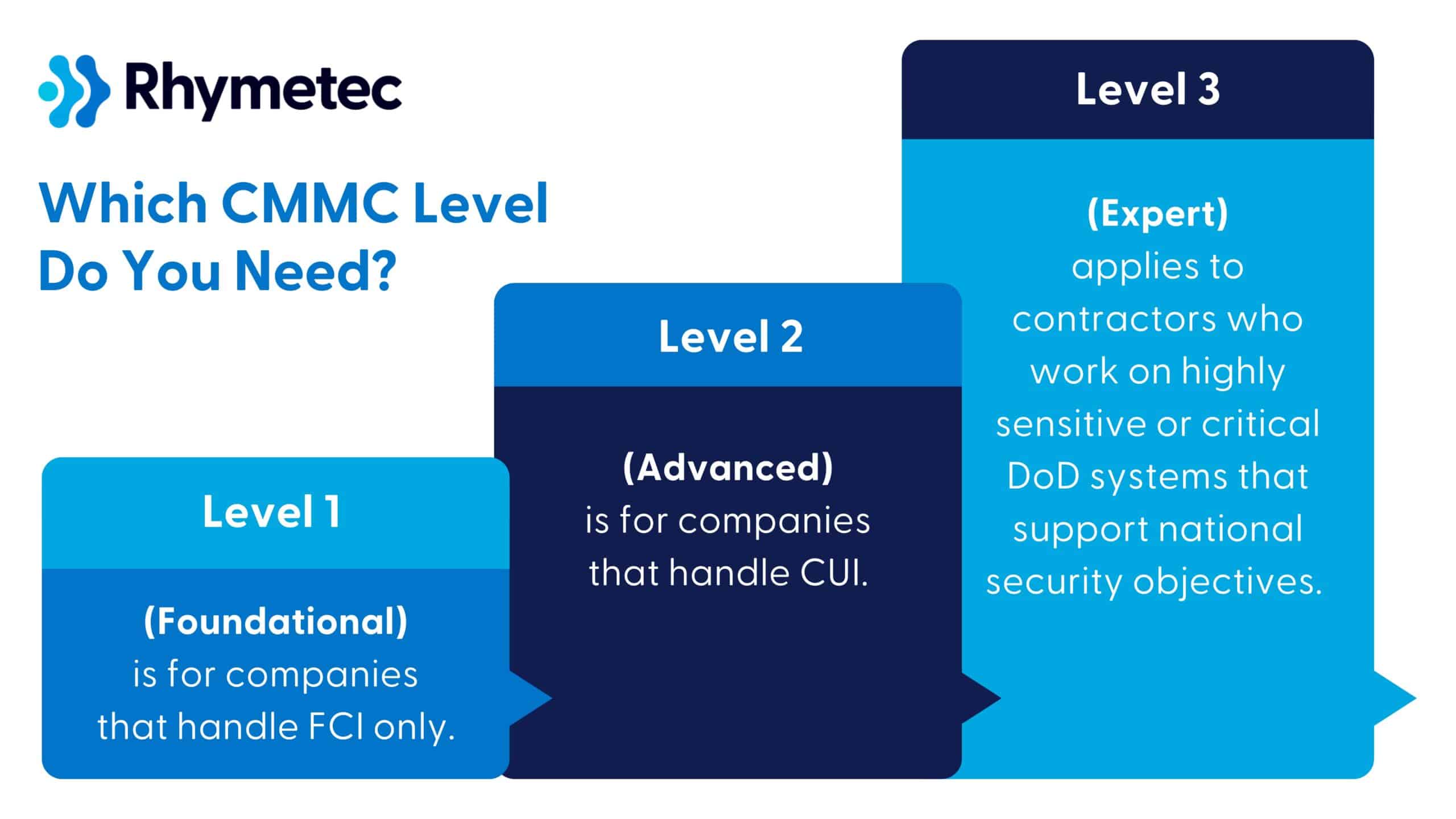
So, which CMMC Level Do You Need?
Based on the type of data your organization handles, there are three levels of CMMC:
- Level 1 (Foundational) applies to companies that handle FCI only and do not store or process any CUI. This could be an IT helpdesk vendor managing onboarding for non-sensitive systems, construction companies that work on DoD facilities, or a staffing agency that places civilian contractors on DoD projects, just to give a few examples. The new version of Level 1 falls under basic safeguarding practices and is derived from the Federal Acquisition Regulation (FAR) 52.204-21, which directly references and relates to NIST SP 800-171 as part of its requirements.
- Level 2 (Advanced) is for companies that handle CUI. Examples include a SaaS provider offering workflow tools to a DoD agency that handles technical mission data, manufacturing companies that produce parts for defense blueprints, and subcontractors who write embedded software for military systems. Requirements entail full implementation of NIST SP 800-171 (110 controls). Some contractors allow self-attestation, but many require a C3PAO to perform an audit and issue your certification.
- Level 3 (Expert) applies to contractors who work on highly sensitive or critical DoD systems that support national security objectives. Defense contractors managing secure communications infrastructure, and aerospace or defense firms involved in weapons systems development, are examples of organizations that will need Level 3. Requirements include more advanced security controls based on NIST SP 800-172, and a government-led assessment must be conducted.
Getting Started: Conducting A Gap Assessment
Once you’ve identified which level applies to your organization, the next step is a gap assessment.
"For the next step, at Rhymetec, we always start with a gap assessment. A gap assessment against the NIST 800-171 controls is a must-have…It helps you determine if you have any missing controls or if you have any gaps in your compliance, so you can start putting together a roadmap for completing the remaining controls." - Metin Kortak, CISO at Rhymetec
The aim is to compare your current environment against the required controls. This process tells you what needs to be done before you’re ready to self-attest or move into the certification phase.
CMMC 2.0 also allows you to use a Plan of Action and Milestones (POA&M) to formally track missing controls and your plan for implementing them:
“In 2.0, CMMC came out with a final action and milestones plan. This document essentially allows you to create implementation plans for controls that are missing in your gap assessment, so that you can remediate these controls within a certain amount of time. This is also something you can work with third parties on or conduct your own self-assessment.” - Metin Kortak, CISO at Rhymetec
Next, we'll break down what you need to do for each level of CMMC:
CMMC Compliance Checklist: What Are The Level 2 Requirements?
CMMC Level 2 applies to organizations that process, store, or transmit CUI as part of their work with the Department of Defense. This includes software vendors, MSPs, and subcontractors that handle technical data, system specifications, or any other sensitive project-related information:
"If you process CUI as part of your work in the supply chain of the DoD, that's where the Level 2 requirements come in. A majority of organizations that handle CUI will require a third-party audit and CMMC certification." - Matt Bruggeman, A-LIGN
Level 2 is based on the controls in NIST SP 800-171.
These controls are grouped into areas to include access control, configuration management, incident response, and audit and accountability. For a more comprehensive list of the 110 controls (with more technical detail), see the NIST SP 800-171 official documentation here.
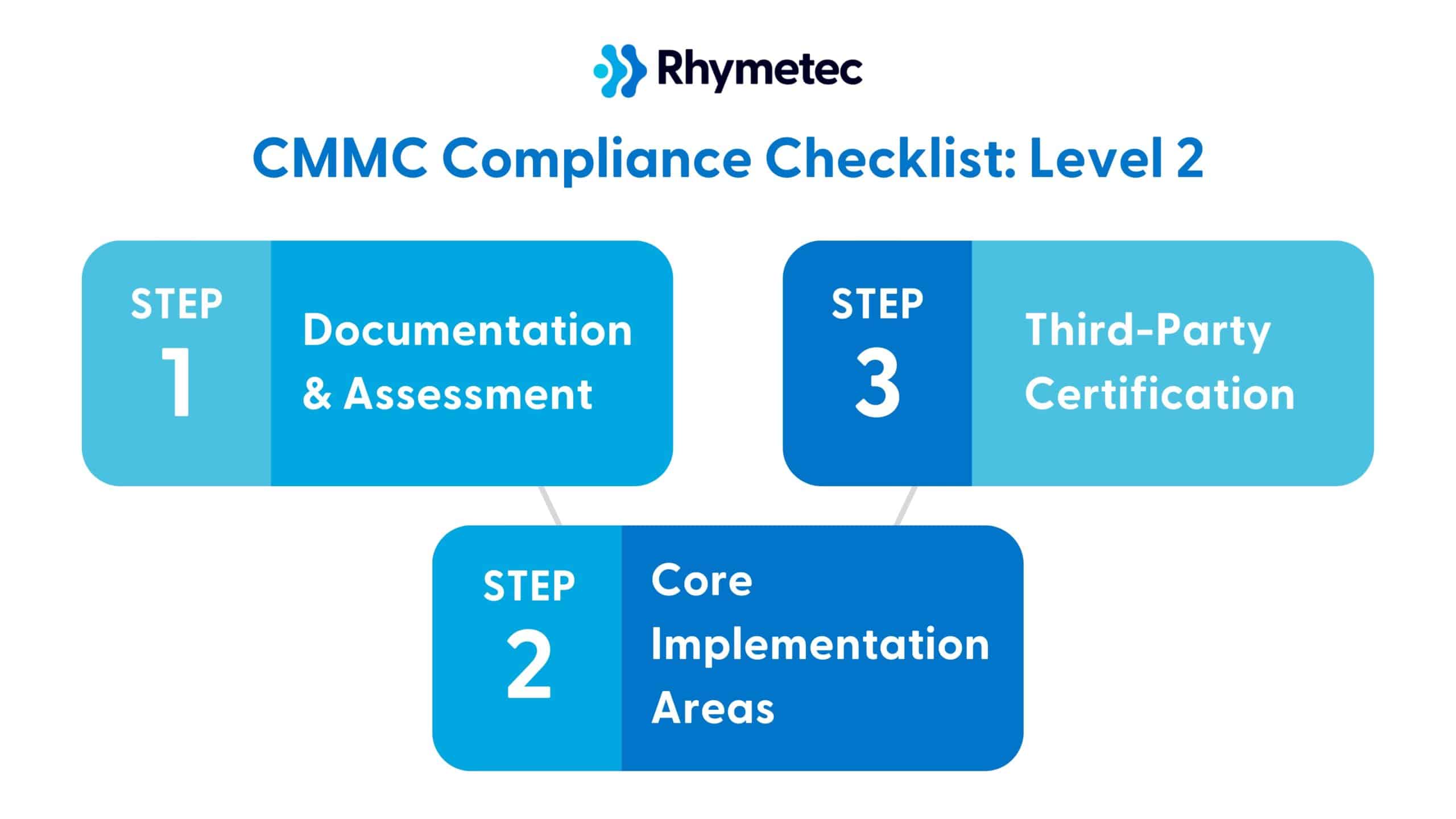
Below is a checklist with the main items broken down into three categories to give you an idea of what to expect:
1. Documentation and Assessment
Complete a full NIST 800- 171A self-assessment (or third-party assessment).
This will show which controls your organization is missing or needs to improve, and form the foundation for remediation work needed for CMMC.
Develop a System Security Plan (SSP).
The SSP documents how your organization has implemented each NIST control and serves as the core evidence package when it comes time for your external assessment by a C3PAO.
Create a Plan of Action and Milestones (POA&M) for any discovered gaps.
The purpose of a POA&M is to outline the timelines and resources needed to remediate security control deficiencies you discovered during the self-assessment.
Submit or update your SPRS score.
The Supplier Performance Risk System (SPRS) score is an indication of how many of the 110 controls you've implemented, and is required by DoD contracting officers when evaluating vendor eligibility.
Document CUI data flows.
Mapping how CUI moves through your systems (and your vendors) is a core part of scoping your security boundary and making sure this is documented in your compliance program.
2. Core Implementation Areas
Access Control.
Enforce measures to include least privilege and MFA, and manage privileged accounts.
Asset Management.
Inventory CUI systems, segment networks, and label systems appropriately.
Audit and Accountability.
Retain records and review logs for anomalies.
Configuration Management.
Establish secure baseline configurations and change control procedures.
Identification and Authentication.
Make sure your organization is using strong authentication mechanisms and unique IDs for users.
Incident Response.
Create an incident response plan if your organization doesn't already have one, and test it.
Maintenance.
Track system maintenance activities.
Media Protection.
Create policies to limit and monitor removable media and sanitize storage before reuse.
Personnel Security.
Screen employees, terminate access promptly, and deliver regular security training.
Physical Protection.
Restrict physical access to systems and facilities handling CUI.
Risk Assessments.
Perform risk assessments and remediate vulnerabilities.
Security Assessment.
Conduct internal control testing and prepare for external audits.
System and Communications Protection.
Implement boundary defenses and encryption for CUI in transit.
System and Information Integrity.
Deploy measures to include endpoint protection, monitoring for malware, and regular patching.
3. Third-Party Certification
Most organizations at Level 2 will be required to undergo an audit by a CMMC Third Party Assessment Organization (C3PAO).
Some contractors (specifically, those working on lower-risk programs) might be permitted to self-attest for Level 2, but this is an exception.
C3PAOs validate the implementation of the 110 controls. Generally, you can expect them to conduct technical testing, interview your staff, and verify documentation.
Preparing for Level 2 requires an enormous amount of coordinated effort across technical and operational domains. Working with a CMMC Consultant can vastly streamline the process for you.
CMMC Compliance Checklist: Level 2 Timelines
The time required to meet CMMC Level 2 requirements varies depending on your organization’s size, industry, and whether or not you already comply with NIST 800-171 or a similar framework.
Below are timelines to show what an average organization can expect for CMMC Level 2.
**The following timeline assumes that the organization will start with a gap assessment and follow a typical implementation plan. Organizations that are already aligned with NIST 800-171 can proceed faster.
CMMC Level 2 Timeline (6-8 Months)
Gap Assessment and Planning (1-2 Months)
- Determine the type of CUI your organization handles
- Map data flows for CUI and list out the systems involved in processing it
- Conduct a gap assessment against the 110 controls
- Draft your POA&M and create an implementation roadmap
Control Implementation (3-4 Months)
- Implementation of 110 controls, including access control, endpoint protection, backup and disaster recovery, incident response, and change management policies.
Documentation and Internal Validation Prior to Audit (1 Month)
- Internal testing of controls
- Vulnerability scan and patching
- Finalize documentation of evidence
C3PAO Audit (1 Month)
- Pre-assessment (optional, but strongly recommended)
- Official audit with interviews, control verification, and documentation review
- Validation of compliance (ongoing)
**Note: A vCISO can streamline the process and fast-track you to audit readiness. Rhymetec works closely with trusted auditing partners and can connect you with them for your assessment.
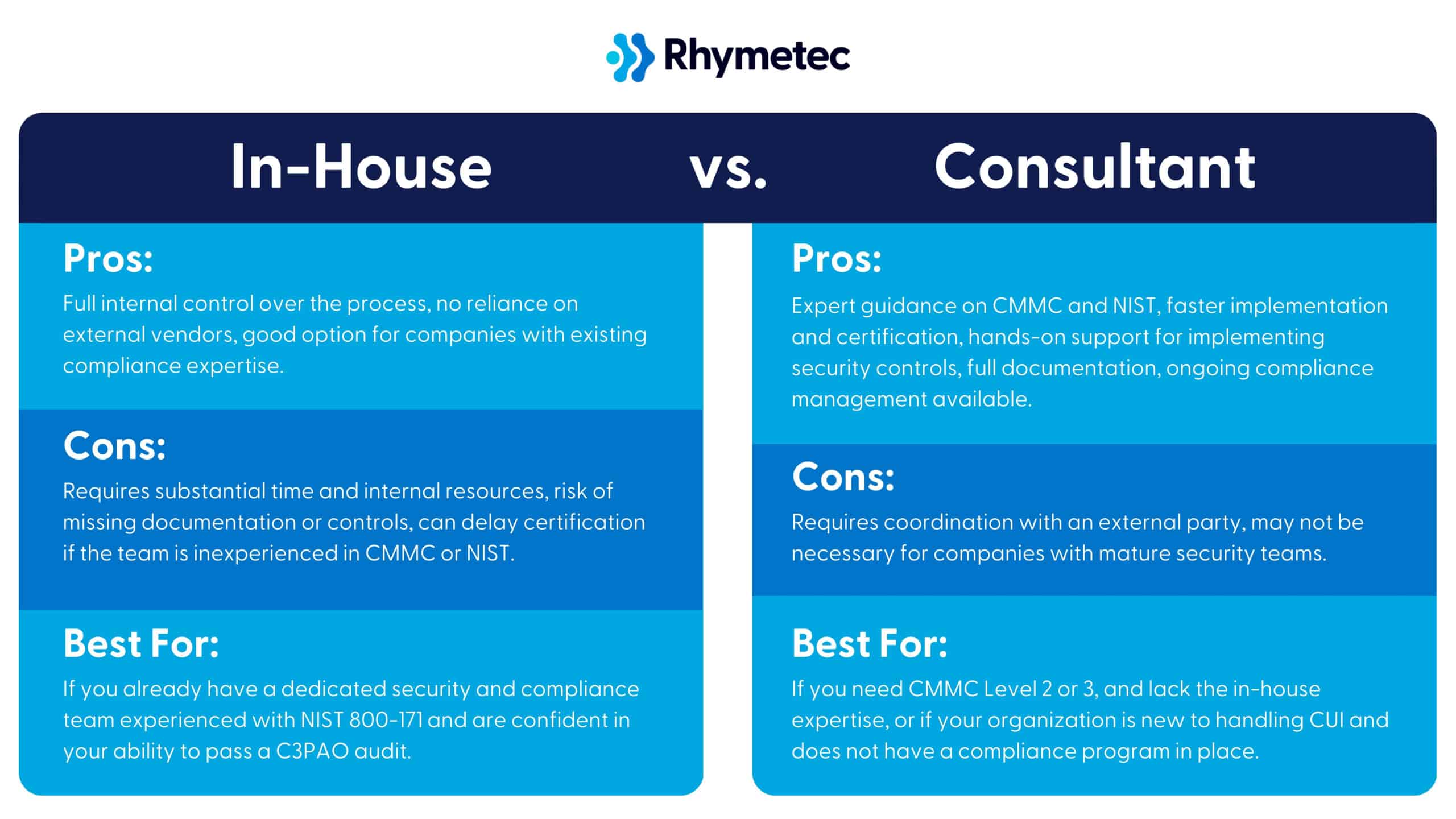
Advantages of Engaging A CMMC Consultant (The Earlier, The Better!)
The higher levels of CMMC are complex.
If you aren’t already compliant with the relevant NIST frameworks, compliance for Level 2 will require implementing a massive amount of technical controls and corresponding documentation. For many companies, it simply doesn’t make sense to try to manage all of this internally.
This is where a virtual CISO (vCISO) comes in.
A vCISO works closely with your team to understand your environment and translates CMMC requirements into what you actually need to accomplish.
Our vCISOs at Rhymetec support you throughout the entire CMMC preparation process. We conduct your gap assessment, carry out control implementation for the controls you need, finalize documentation, and serve as the main contact point for auditors on your behalf.
**For information on our vCISO pricing options, check out our blog on vCISO pricing.
Outsourcing the bulk of the work required for CMMC is helpful at any point in the compliance process, but is especially transformative during the initial stages. In our experience, especially partnering with startups to meet their compliance goals, working with a vCISO from the beginning allows you to turn an onerous process into a business enabler.
An experienced vCISO will build a security program for your organization that not only meets CMMC and requirements but scales as your business grows. They understand exactly how to structure your compliance program to enable you to more easily meet additional or future requirements in your industry, and can connect you to the best auditing partners in your space.
Partner For Success: Work With Rhymetec + An Accredited C3PAO
Meeting CMMC requirements is a complex process.
The good news is that you don’t have to do it alone. Our partnership with industry leader A-LIGN, an accredited C3PAO, gives you access to both the security legwork needed to meet requirements as well as certified assessment services.
Together, we help organizations prepare for CMMC with confidence. Whether you are just getting started or finalizing your readiness for an assessment, we’re here to support your compliance journey with security expertise and a trusted C3PAO partner.
C3PAOs are the only organizations authorized by the CyberAB to perform official CMMC assessments. Their involvement is essentially a must-have for any contractor aiming for certification. Meanwhile, as a Registered Provider Organization (RPO), Rhymetec works hand-in-hand with A-LIGN to help you prepare for that assessment.
RPOs are approved to offer consulting and readiness support, and help you implement required controls, remediate gaps, and make sure your security practices and documentation align with CMMC standards. Together with A-LIGN, we are proud to offer this streamlined option for our clients. Contact us todayto learn more.