What is SOC 2?
The purpose of SOC 2 compliance is to obtain proof that a company is storing and processing customer data in a secure manner. Also known as Service Organization Control Type 2, SOC 2 was developed by the American Institute of Certified Public Accountants (AICPA). For security-conscious businesses, SOC 2 compliance is a minimal requirement when considering a SaaS provider.
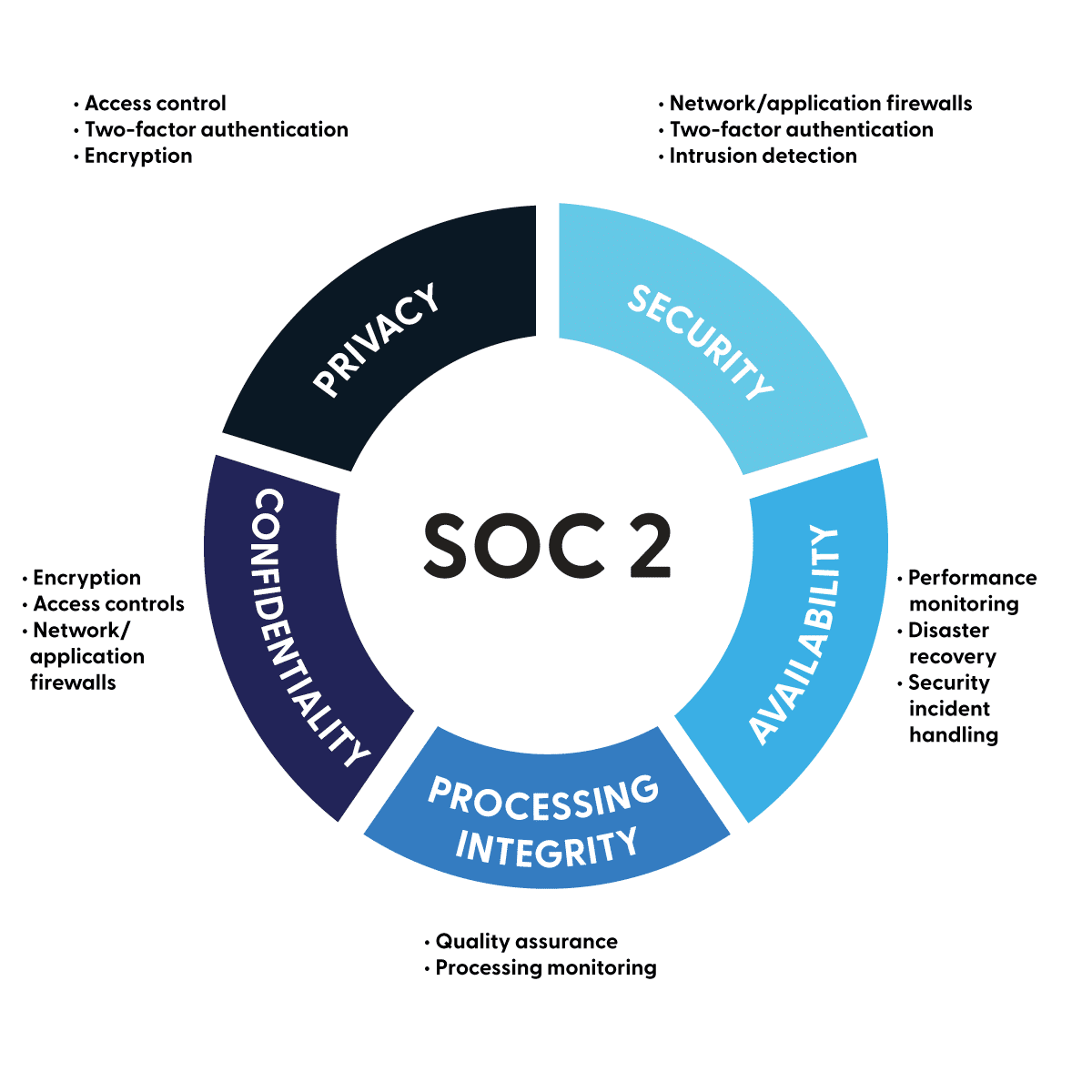
SOC 2 defines criteria for managing customer data based on five trust service principles:
- Security
- Availability
- Processing Integrity
- Confidentiality
- Privacy
SOC 2 reports are unique to each organization because of specific business practices they may use. Each organization designs its own controls to comply with one or more of the SOC 2 Trust Services Criteria. These internal reports provide you with important information about how your service provider manages data.
There are two types of SOC reports, SOC 2 Type 1 and Type 2:
- SOC 2 Type I report is an attestation of controls at a service organization at a specific point in time.
- SOC 2 Type II report is an attestation of controls at a service organization over a minimum six-month period.
Why SOC 2 compliance?
SOC 2 allows companies to have improved visibility on their security posture and stronger data protection processes through more cyber-aware skills, creating improved threat management for today—and the future. Plus, it helps build trust, gain a competitive edge, manage risks effectively, meet customer expectations, comply with legal and regulatory requirements, improve operational efficiency, and facilitate business growth.
How do we do it?
We make audits more efficient—and less of a hassle—by implementing technologies and controls to meet each SOC 2 criteria. Our team will develop and manage an internal information security program that aligns with all SOC 2 controls and industry best practices. Post-report delivery, Rhymetec will continue to manage all controls to maintain compliance.
Our security and compliance experts will guide you through each phase of the SOC 2 checklist.

Deliverables from Rhymetec
Our team is dedicated to delivering premium-tier service to ensure SOC 2 compliance. We customize and fulfill all items, from comprehensive data management plans, to fully itemized reports that provide information regarding methodology, findings, potential mitigations, and our recommendations.
Rhymetec specializes in enabling meaningful, real-world solutions to the most pressing challenges of the modern enterprise security environment. Assessment and reporting is contextualized to your business sector, and custom-tailored to your specific environment.
Our process is engineered to provide all the data and insights needed for you to make informed security decisions and take definitive action against unforeseen cyber threats.

