Penetration testing is one of the most critical and misunderstood security activities for companies. Often, buyers of security services may have difficulty differentiating between penetration tests and vulnerability scans as a result of technical jargon and a lack of clarity from vendors.
Vendors contribute to this confusion by claiming to offer “penetration testing” that, in reality, involves only spending a short time running automated tools. This article explores the differences between a penetration test and a vulnerability scan to clarify how they differ and where each fits into a modern security program.
Let’s jump right in with the main differences at a high level:
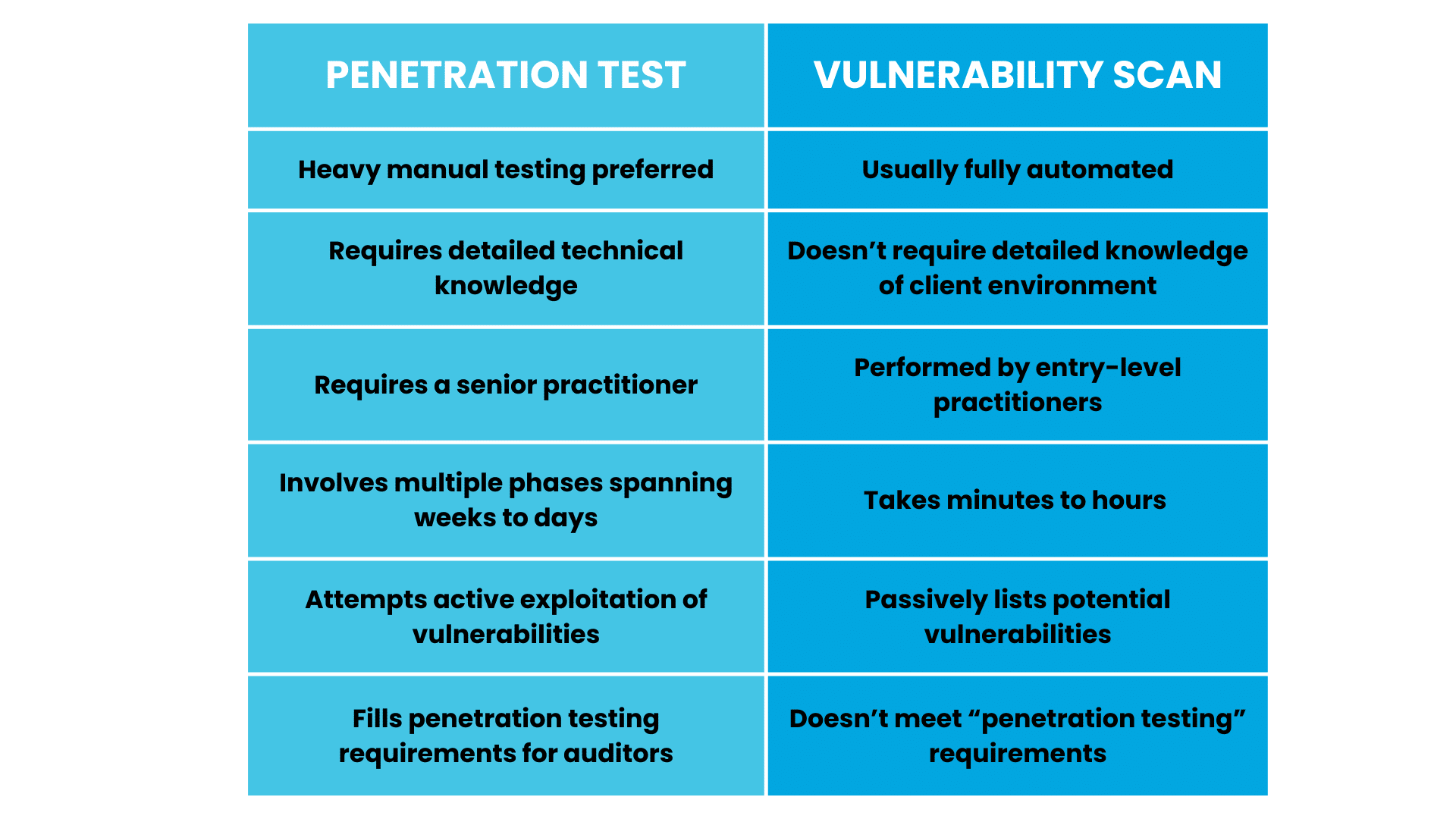
Penetration Testing Vs. Vulnerability Scanning: 6 Main Differences
Penetration testing is substantially more involved than vulnerability scanning.
While penetration testing and vulnerability scanning are both important for identifying security risks, they serve different purposes:
Penetration testing is largely manual, requires expert knowledge, and can take weeks. A senior-level practitioner aims to exploit vulnerabilities (just like a real threat actor would do) in order to identify weak points. Vulnerability scanning is mostly automated and needs minimal expertise, but is useful for passively identifying risks on an ongoing basis.
When assessing pen testing vendors, it’s critical to know the differences. Some vendors claim to offer “penetration testing” when, in reality, what they are really doing is vulnerability scanning.
Next, let’s go over penetration testing vs. vulnerability scanning in more detail to equip you with the information to decide if you need one or the other (or both) for your organization.
What Is A Vulnerability Scan?
Almost all modern software applications have vulnerabilities or weaknesses in the code that can allow an attacker to gain information or privileged access that the software doesn’t intend. Major software companies such as Microsoft and Apple routinely deploy patches to both personal computers and to servers to fix identified vulnerabilities.
In their simplest form, vulnerability scans involve using tools like Nessus and Shodan to proactively scan for known vulnerabilities against an IP range to identify unpatched systems and prioritize the highest-risk vulnerabilities.
Vulnerability scans are meant to be run regularly after even minor changes to an organization’s IT infrastructure. It’s worth noting that threat actors use the same tools as security teams to continuously scan the internet, looking for internet-facing devices with exploitable software vulnerabilities.
Vulnerabilities in Context: Vulnerabilities on externally facing assets (such as hosts and servers exposed to the internet) tend to be more critical than vulnerabilities on computers that are not accessible to the internet. Additionally, not all vulnerabilities are equally risky. Some are “theoretical” in that nobody has actively exploited them before. This type of vulnerability tends to be a lower priority than a vulnerability that is known to be actively exploited by threat actors.
Generally speaking, vulnerability scans can be performed automatically by entry-level team members as the software will automatically identify, prioritize, and report on vulnerabilities. Vulnerability scans do not attempt to exploit the vulnerabilities. They only identify their presence by looking at details such as the source code and software version.
Think of a vulnerability scan like a security guard checking to ensure all of the doors are locked in an office building. Meanwhile, a penetration test is like a skilled lockpicker trying to unlock a door.
What Is A Penetration Test?
The goal of a penetration test is to take the attacker’s perspective and actively attempt to gain access to privileged IT systems. The tester will aim to exploit vulnerabilities and leverage exposed servers in order to identify weak points and report on how they did it.
Following up on our security guard analogy, a penetration test involves hiring someone to act as a criminal and try to pick the locks on the building (and the windows, too!). Penetration testing is far more involved, scoped to the individual business, and requires the vendor to have deep expertise.
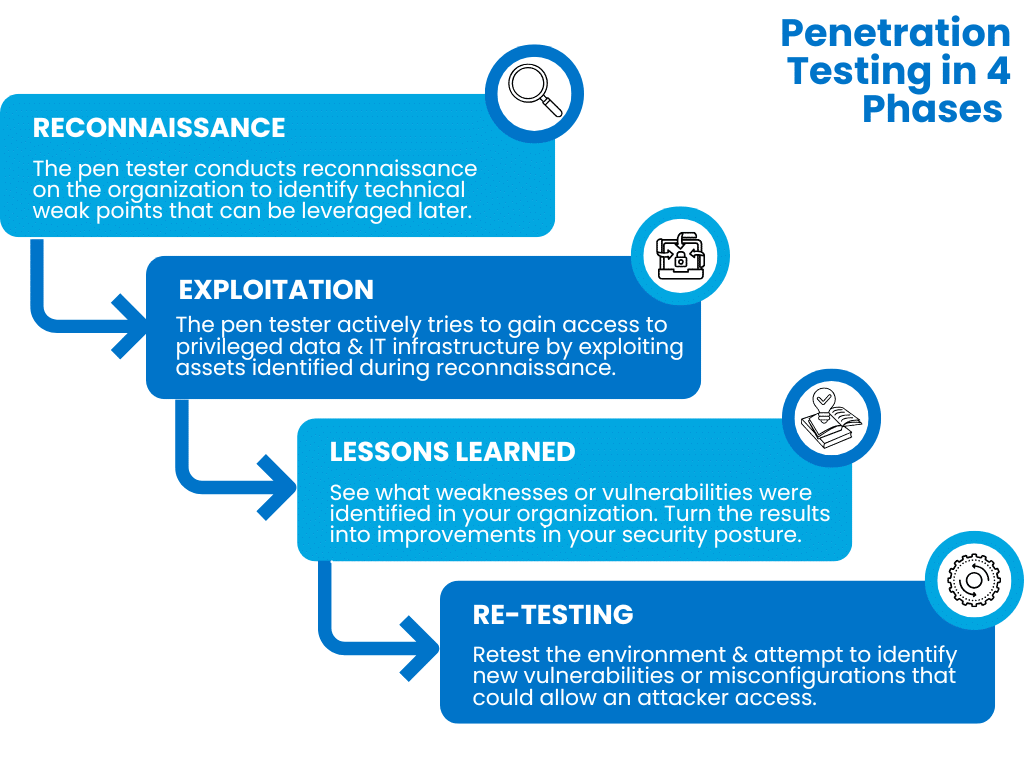
A reputable penetration testing company will work with the client prior to the test, set rules of engagement, and take a multi-phased approach to include:
Reconnaissance: During this phase, the pen tester conducts reconnaissance on the organization to identify technical weak points that can be leveraged later. The pen tester may leverage various proprietary and open-source tools to conduct scanning, identify exposed services, and catalog information to prepare for the exploitation phase.
Exploitation: During the exploitation phase, the penetration testing company will actively try to gain access to privileged data and IT infrastructure by exploiting assets identified during the reconnaissance phase. When successful, a pentester may attempt to move laterally through the network to identify additional resources they can access.
Lessons Learned: This is the most important phase of a penetration test. What weaknesses or vulnerabilities were identified in the target organization? The lessons learned phase is absolutely critical for turning pen testing results into improvements in your organization’s security posture.
Re-testing: After a certain period has elapsed, it can be enormously beneficial to retest the environment and attempt to identify new vulnerabilities or misconfigurations that could allow an attacker access.
Security should never be viewed as a one-time fixed event or test. At Rhymetec, we focus on building a continuous security function that proactively meets compliance requirements and identifies gaps in our client’s defenses before an attacker does.
Types of Penetration Tests
Penetration tests can be quite varied and are specific to the client’s environment.
Rhymetec offers 4 types of testing designed to identify gaps across multiple types of information technology architectures:
- Mobile Application Penetration Testing
- Web Application Penetration Testing
- External Network Penetration Testing
- API Penetration Testing
All types of penetration tests simulate a real attack. They leverage multiple vantage points to attempt to gain access, including exploiting vulnerabilities, but also potentially social engineering, phishing, and even exposed credentials in order to bypass the client’s security defenses.
Read the case study on CXO Nexus to see how our penetration testing team at Rhymetec helped them level up their security and compliance, build trust with customers, and improve product development.
Penetration Tests Versus Vulnerability Scans in Context: Compliance
Nearly all major compliance requirements require routine vulnerability scanning and patching. Conducting vulnerability scans is relatively simple and can go a long way toward reducing risk for your organization.
However, for the purposes of compliance, vulnerability scanning is not penetration testing.
Many organizations conduct pen tests solely for the purpose of improving their security posture and uncovering vulnerabilities before attackers do. In many cases, pen tests are required by regulatory compliance requirements as well. The following compliance requirements mandate a penetration test in order to be audit-ready:
- FedRAMP: Requires cloud service providers to conduct penetration tests.
- PCI DSS: Some levels of PCI DSS require a penetration test once per year for most organizations that handle credit card transactions. It can also be required biannually for service organizations that handle credit card transactions and who segment their network to protect cardholder data.
- FISMA: Requires federal agencies to conduct penetration tests and vulnerability assessments on a sampling of their information systems annually.
- NIST’s Special Publication 800-53: Requires federal organizations to perform penetration testing under control CA-8.
Companies can also use penetration testing to strengthen their compliance posture and demonstrate proactive cybersecurity to meet other requirements. Requirements that benefit from penetration testing and for which it can be used to fulfill controls (but is not outright required) include:
- HIPAA
- HITRUST
- SOC 2
- ISO 27001
- CCPA
- NIST
- GDPR
We often hear from our customers that although a penetration test is not an explicit requirement under frameworks like SOC 2, their auditors are inquiring about whether or not they’ve undergone a penetration test.
As the gold standard method of testing the strength of your security, penetration testing adds a strong layer of assurance going into your audit.
Penetration Tests and Security Questionnaires
Almost all compliance requirements and security questionnaires require routine vulnerability scanning. Proactively conducting penetration tests can be an additional high-value way to demonstrate continuous compliance to clients and show that your firm takes security seriously.
Large corporations, in particular, are increasingly requiring potential vendors to answer rigorous security questionnaires. Penetration testing, combined with meeting voluntary compliance requirements such as SOC 2 or ISO 27001, goes a long way toward demonstrating that your organization has a serious security program.
Penetration Testing vs. Vulnerability Scanning FAQ
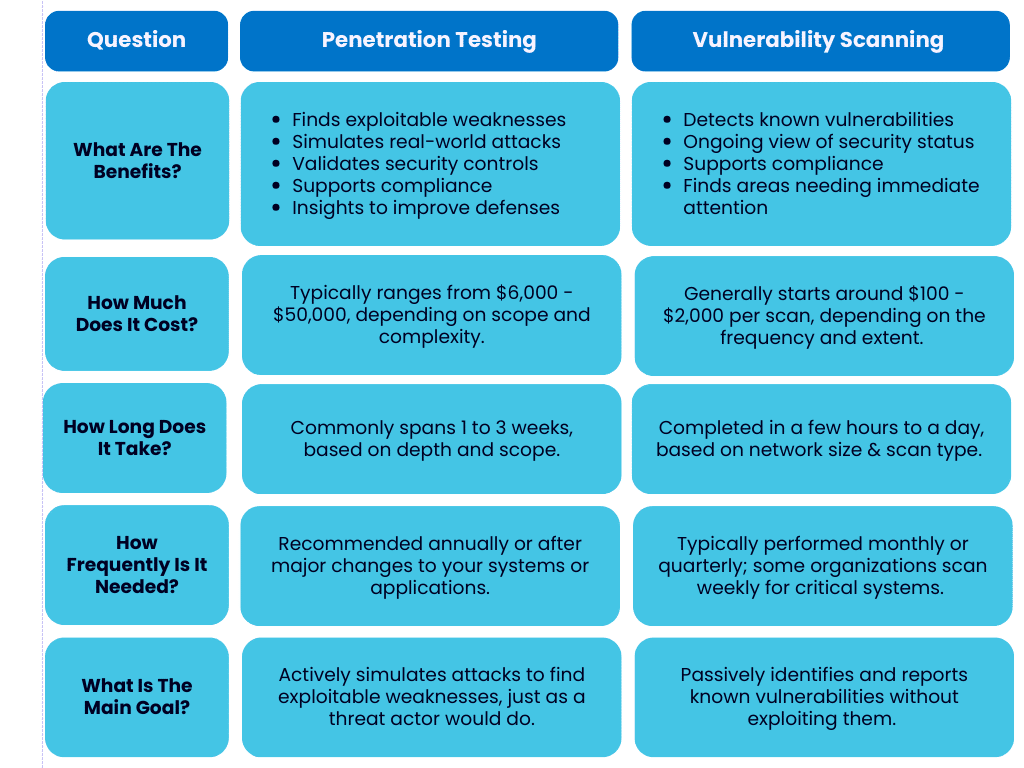
What Are The Benefits of Penetration Testing?
- Identifies exploitable weaknesses in systems.
- Simulates real-world attacks to gauge your organization’s response.
- Helps validate security controls.
- Provides practical insights for improving your security defenses.
- Supports compliance with security standards.
What Are The Benefits of Vulnerability Scanning?
- Detects known vulnerabilities.
- Offers a continuous view of your systems’ security status.
- Highlights areas needing immediate attention.
- Supports compliance with security standards.
How Much Does Penetration Testing Cost?
- Penetration testing typically ranges from $6,000 to $50,000, depending on scope and complexity.
How Much Does Vulnerability Scanning Cost?
- Vulnerability scanning generally starts around $100 – $2,000 per scan, depending on the frequency and extent.
How Long Does A Pen Test Take?
- A penetration test commonly spans 1 to 3 weeks, based on depth and scope.
How Long Does A Vulnerability Scan Take?
- A vulnerability scan is often completed in a few hours to a day, depending on network size and scan type.
How Frequently Do You Need Penetration Testing vs. Vulnerability Scanning?
- Penetration testing is recommended at a minimum annually or after major changes to your systems or applications.
- Vulnerability scanning is typically performed monthly or quarterly; some organizations scan weekly for critical systems.
What Is The Main Difference Between Penetration Testing and Vulnerability Scanning?
- Penetration testing actively simulates attacks to find exploitable weaknesses, just as a real threat actor would do, while vulnerability scanning passively identifies and reports known vulnerabilities without exploiting them.
Frequently Asked Questions
The Bottom Line: Penetration Testing vs. Vulnerability Scanning
Vulnerability scanning and penetration testing are both critical for your company’s security.
We hope at this point it’s clear that a vulnerability scan is a single fixed-in-time way to identify unpatched systems that have software vulnerabilities, while penetration testing involves simulating an attacker in a real-life attempt to gain access to your organization’s sensitive IT infrastructure.
From an audit perspective, your auditors may expect to see that you’ve undergone a penetration test. Regular penetration testing will vastly strengthen your security program’s credibility with auditors and give your prospects and clients confidence in your security.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
About The Author: Metin Kortak, CISO
Metin Kortak is the Chief Information Security Officer at Rhymetec. Metin began his career working in IT security and gained extensive knowledge of compliance and data privacy frameworks such as SOC 2, ISO 27001, PCI, FedRAMP, NIST 800-53, GDPR, CCPA, HITRUST and HIPAA. He joined Rhymetec to build data privacy and compliance as a service offering. Under Metin’s leadership, these offerings have grown to more than 200 customers, positioning the company as a leading SaaS security service provider in the industry.
Interested in reading more? Check out more content on our blog: