Find weaknesses before hackers
A Rhymetec pen test entails an intentional launching of simulated cyberattacks by our own penetration testers to access or exploit computer systems, networks, websites and applications. Our pen testers will identify exploitable issues so that effective security controls can be implemented, or will test the robustness of your current infosec program.
Get StartedAbout Rhymetec Pen Tests
We offer a range of penetration tests customized to your requirements and environment.
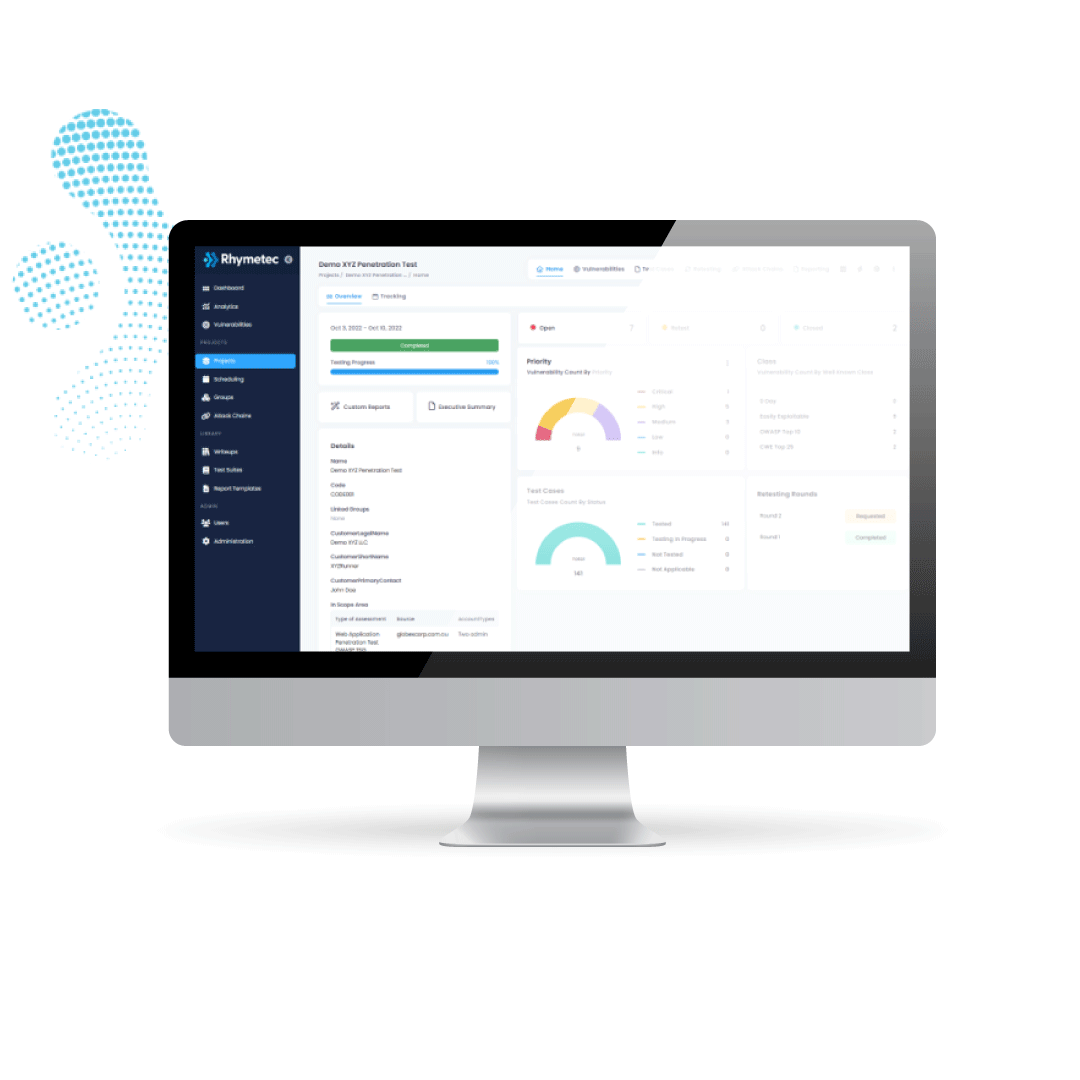
Increasing the speed and quality of your experience
Rhymetec’s new Penetration Testing platform provides improved testing workflow management and productivity to provide your team with actionable, and easy-to-understand results:
- Save time with high-level reporting, on-demand, and accessible when you need it.
- Improve team collaboration by utilizing a centralized location to address vulnerabilities.
- Have increased visibility into your businesses with a clearer view of your organization’s vulnerable areas.
Get Started
API Penetration Test
API penetration testing is an ethical hacking process to assess the security of the API design. Our goal is to find gaps before an internal or external hacker does, and report them to strengthen the API and prevent unauthorized access or data breaches across your systems and applications.
Learn More

External Network Penetration Test
An external network penetration test simulates a real-world attack on your external network infrastructure, including networks, systems, hosts and network devices. Our experts will assess your organization’s network and prepare a report detailing your areas of risk, and providing a roadmap detailing opportunities for improvement.
Learn More

Mobile Application Penetration Test
A Mobile Application Penetration Test will provide a comprehensive analysis of the security features of the application and backend components. This analysis will identify key areas within the application where security can be improved.
Learn More

Web Application Penetration Test
Web Application Penetration Testing allows organizations to test the security state of their applications, whether developed in-house or by third parties. The assessment can help organizations identify and correct vulnerabilities to protect from harmful attacks, and should be used as part of an ongoing strategy to support the organization’s software development lifecycle.
Learn More
Certifications our Penetration Testers Hold
Have A Question?
We Can Help You
Although there is little automation in our Rhymetec Penetration Test, we rely heavily on manual testing to provide the most accurate and impactful results that are unique to your business. Plus, we provide custom reports—to communicate any of our findings—that are easy to understand and present to your executive teams.
Rhymetec offers API Penetration Tests, External Network Penetration Tests, Mobile App Penetration Tests and Web Application Penetration Tests. Plus, we are newly offering phishing and PCI scans. Contact our team to learn more.
Due to the high-demand of a Rhymetec Penetration Test, and the necessary preparation and assessment needed to properly execute on our services, we typically ask our clients to schedule their Penetration Test within 2-6 weeks at a minimum. However, we understand that some client needs are immediate and would still accept consultations to confirm any last-minute openings and availability.
Penetration testing costs can vary significantly depending on multiple variables like network IP addresses, API endpoints, number of applications, complexity of applications and more. Accounting for these variables, our team works diligently to match the scope details with the security needs of your organization. Our pricing is extremely competitive compared to other Pen Test service providers in the market, and we would be happy to provide a custom quote.
Testimonials
What Our Clients Are Saying About Us