
Our security professionals are at your service with years of experience working with the most complex compliance regulations.
Get Started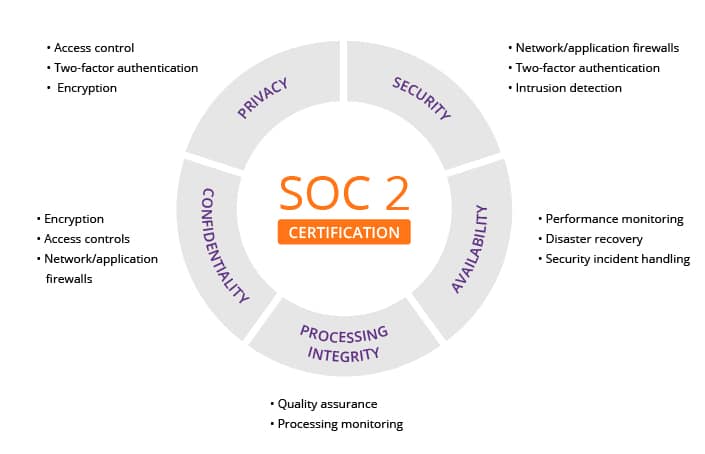
No Sweat SOC2 Certification
What we do – We manage all the hard work so you can sail through your SOC (Service Organization Controls) 2 audit.
How we do it – Implement and monitor the security controls needed to satisfy each of the common criteria of the SOC 2 certification, including asset discovery and inventory, vulnerability assessment, file integrity monitoring, and lots more.
Why it’s a good idea – More efficient (and less of a hassle) than implementing separate technologies to meet each SOC 2 criteria. Plus, we’ll give you compliance reports and automatic threat updates so that you’re always in the loop.
LEARN MORE
Check Off GDPR Compliance
What we do – Identify, classify, secure, and protect data that is relevant to GDPR (General Data Protection Regulation) standards.
How we do it – Create a custom data classification and management plan to help your business meet GDPR compliance regulations. Establish compliance policies and procedures and a Data Protection Officer (DPO) to keep your data safe and secure. And, prepare you to act in the event of a security incident (which we’ll help you avoid).
Why it’s a good idea – Protect your company from data breach and non-compliance fines.
LEARN MORE
Get Airtight With HIPAA
What we do – Develop a HIPAA-secure cyber security program just for you, that aligns to your business goals and optimizes your operations.
How we do it – Conduct risk analysis and gap analysis. Review and assess your policies and controls. Provide 1-on-1 IT support from a HIPPA compliance specialist. Research, recommend, and implement the right technologies to help your business run smoothly and safely.
Why it’s a good idea – HIPAA compliance is non-negotiable, and yet the requirements and specifics are ever-changing. We’ll stay on top of them, so you don’t have to.
LEARN MORE
