In this blog, we’ll go over frequently asked questions about conducting a cybersecurity tabletop exercise, including how it works, why it’s important for startups and SMBs, which voluntary and legal compliance requirements you need one for, and more.
What Is a Cybersecurity Tabletop Exercise?
You’re sitting in a meeting with your leadership team, the IT lead, and a couple of personnel from operations. Someone kicks things off by saying, “Alright, here’s the situation: You’ve just received an email from a threat actor claiming they’ve gained access to our production environment. They’ve encrypted customer data and are demanding a $50,000 ransom in the 48 hours. What do we do first?”.
That’s a cybersecurity tabletop exercise in action. A tabletop exercise allows your team to practice handling a cybersecurity incident without the actual crisis. Your team works through a realistic scenario step by step, discussing who’s responsible for what and how decisions will be made. During the exercise, gaps in your existing plan and questions you need to answer going forward will likely surface:
Who decides if the ransom should be paid? What happens if legal or PR resources are tied up? Is your team ready to handle questions from customers or regulators?
These are the types of issues that otherwise may not come up unless you are in the middle of a real incident, but a tabletop exercise allows you to address them before they actually happen.
These exercises enable you to see how your team will react when/if you experience a real threat, based on your specific situation: Maybe your team has a strong technical foundation but hasn’t worked out all the details for responding to an attack. Or maybe you’re growing quickly, and roles like security and IT are spread across multiple people who wear a lot of hats.
Regardless of your situation, tabletop exercises strengthen your security posture by giving you a chance to run through various scenarios, fine-tune how to respond, and stress-test your existing processes.
They also need to be conducted to meet many voluntary and legal requirements. For this reason, they’re especially critical for organizations seeking to land bigger clients or meet compliance requirements like SOC 2 or ISO 27001.
Why Do Startups and SMBs Need Tabletop Exercises?
Let’s say your startup just landed a major client. Part of the contract includes a requirement to prove you can handle a security incident without putting their data at risk (or, they simply ask to see your SOC 2 report).
You’ve got your security policies written up, but when it comes to how your team would respond to a real incident, you need to make sure everyone is on the same page and that you have documented proof of your processes.
Enter the tabletop exercise.
Startups and SMBs often operate with lean teams, where people juggle multiple responsibilities. In a crisis, this reality can often cause confusion over who does what and how to make decisions. A cybersecurity tabletop exercise allows you to clarify responsibilities and builds confidence in your ability to respond to incidents.
Besides disrupting your daily business operations and creating downtime, an incident like ransomware or a data breach can harm the trust of your customers and hurt your ability to grow. Knowing how you’ll respond greatly reduces that risk and helps minimize the fallout.
Compliance is another factor. Frameworks like SOC 2 require you to put your incident response policies and plan to the test, and tabletop exercises are an easy way to meet that requirement. Tabletop exercises are just as critical for startups and SMBs as they are for large enterprises.
For startups looking to scale, being able to demonstrate that you’ve done this makes a big difference when building trust with investors, partners, and customers.
Cybersecurity Tabletop Exercises and Compliance: SOC 2 and More
Under the SOC 2 Trust Services Criteria, tabletop exercises meet the incident response testing requirement of the security criteria (which is not amongst the optional criteria under SOC 2!). Criteria CC7.1 and CC7.2 require organizations to test out an incident response plan. Auditors will therefore ask to see evidence that you’ve actually put your plans to the test and don’t simply have them written down as policies.
ISO 27001, often seen as the baseline for global security standards, also calls for incident response testing. Annex A.16.1.5 requires the periodic testing of information security incident response plans. Tabletop exercises are the simplest, most effective, and industry-standard way to satisfy this requirement.
PCI DSS Version 4.0, which applies to organizations that handle payment card data, also includes a specific requirement for incident response testing. Noncompliance with PCI DSS can lead to fines and additional transaction fees. Requirement 12.10.2 states that companies must “test incident response procedures at least annually”. Again, tabletop exercises are the most straightforward and widely accepted way to meet this requirement.
For privacy regulations like GDPR and the California Consumer Privacy Act (CCPA), there are various stipulations around the importance of having processes in place to be ready in the event of a security incident.
For instance, GDPR’s Article 32 emphasizes the need for “…a process for regularly testing, assessing and evaluating the effectiveness of technical and organisational measures for ensuring the security of the processing.” While tabletop exercises aren’t explicitly named, CCPA has similar expectations for businesses handling sensitive consumer information.
Putting your response to a security incident into practice through a tabletop exercise allows you to prove to auditors that you can meet these requirements.
Enterprise clients in particular will want reassurance that you can handle incidents without putting their data at risk. Many enterprise contracts (which can be used as either an alternative or an add-on to compliance by some organizations) also include requirements for incident response testing. This can be especially important if your organization handles sensitive data or will be integrating with an enterprise client’s systems.
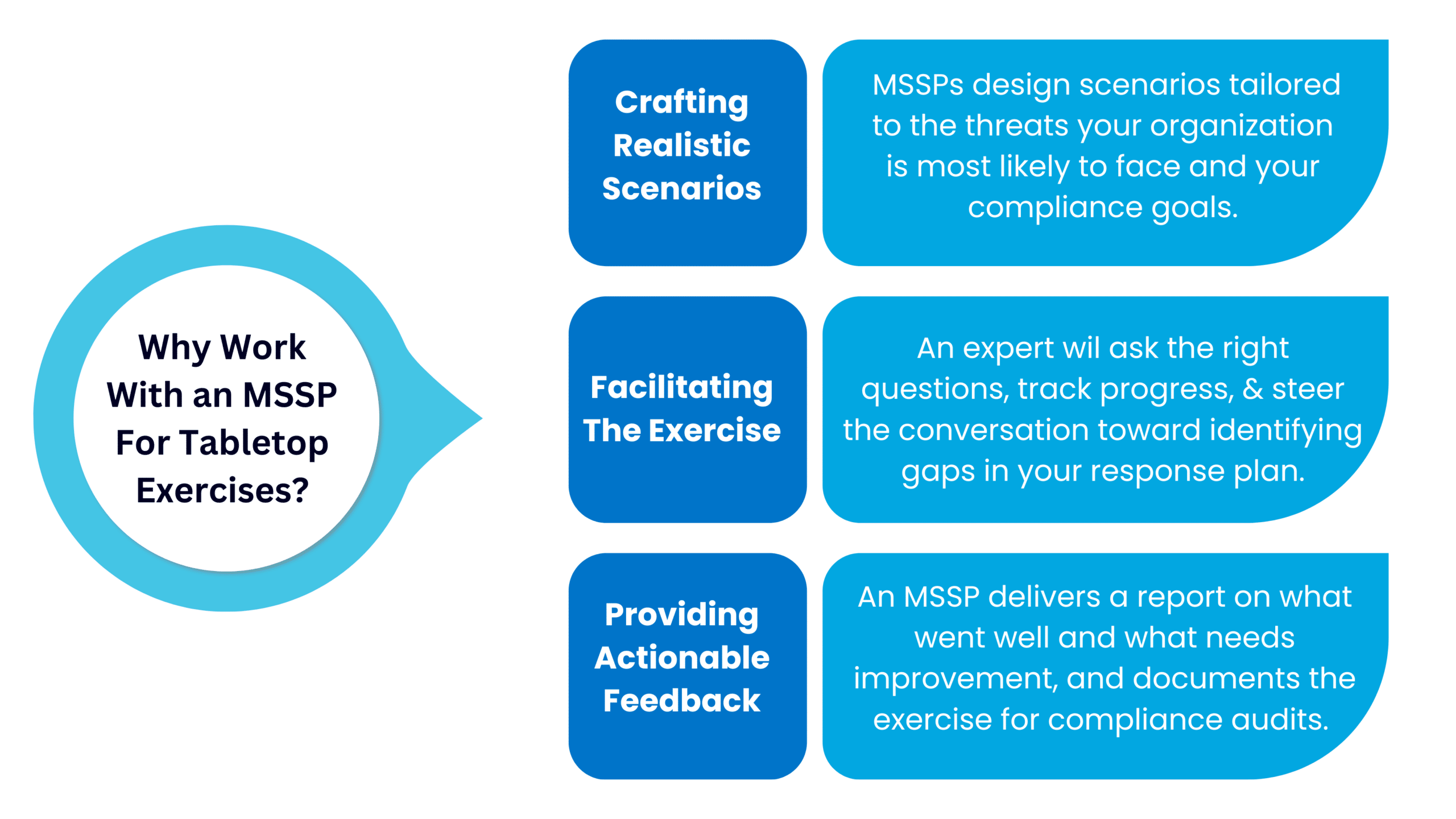
3 Ways MSSPs Support Tabletop Exercises for Organizations
Organizations often choose to work with a Managed Security Services Provider (MSSP) in order to guide them through tabletop exercises. Here are three ways MSSPs offer valuable support through this process while ensuring you meet compliance requirements:
1. Crafting Realistic Scenarios For Your Cybersecurity Tabletop Exercise
Creating a scenario that makes sense for your business is critical. MSSPs can design scenarios tailored to the threats your organization is most likely to face and your compliance goals.
For example, if your company handles customer payment data and you are trying to obtain PCI DSS compliance, the exercise may focus on a ransomware attack targeting your payment processing systems. If you’re in SaaS, it could take the form of a simulated compromise of user accounts.
2. Facilitating the Exercise
To conduct tabletop exercises, you need a neutral facilitator to guide the discussion and keep the team on track. A security expert (such as a Virtual CISO, vCISO) at an MSSP can take on this role, asking the right questions, tracking progress, and steering the conversation toward identifying gaps in your response plan.
Working with an outside expert allows your team to engage in the exercise without worrying about having to run it themselves. They bring an outsider’s point of view, which can enable you to gain insight into areas your internal team may overlook.
3. Providing Actionable Feedback
After the exercise, an MSSP delivers a report on what went well and what needs improvement. They can help you prioritize updates to your incident response plan and recommend additional security measures based on gaps uncovered during the exercise. They can also document the exercise for compliance audits.
Working with an MSSP provides access to expertise, allows you to strengthen your response capabilities without pulling your internal team away from their day-to-day work, and provides deliverables you can use to demonstrate your security posture to auditors and customers.
Getting Started: Partnering With Experts
Cybersecurity tabletop exercises can be used to meet a vast range of both legal and voluntary requirements, and having conducted them builds trust with your clients and prospects. They provide both the evidence auditors need and the confidence customers expect.
However, startups and smaller organizations may lack the resources or internal expertise needed to effectively run cybersecurity tabletop exercises. An external expert, such as a vCISO, solves this issue and provides specialized knowledge. At Rhymetec, our vCISOs have walked dozens of organizations through their tabletop exercises and provided reports that fulfill compliance requirements.
Check out details on our vCISO services to get started today if you are interested in conducting exercises for your organization.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
About the Author
Metin Kortak has been the Chief Information Security Officer at Rhymetec since 2017. He began his career working in IT security and gained extensive knowledge of compliance and data privacy frameworks such as SOC, ISO 27001, PCI, FEDRAMP, NIST 800-53, GDPR, CCPA, HITRUST and HIPAA. Metin joined Rhymetec to build data privacy and compliance as a service offering. Under his leadership, these offerings have grown to more than 700 customers, and the company is now a leading SaaS security service provider in the industry.
Interested in reading more? Check out more content on our blog.