In this penetration testing FAQ, we go over the most common questions around penetration testing and its role in a modern security program.
According to IBM’s annual report, in 2024, the average cost of a data breach reached $4.88 million globally, reflecting a 10% increase from 2023. This is the highest total ever and is projected to continue to increase.
The best way to protect yourself from financial, reputational, and other damages that can result from a data breach is to prevent attacks from happening in the first place.
This is the main goal of penetration testing. Penetration testing is one of the single most effective ways to reduce risk, as it is preventative rather than reactive. A penetration test finds weaknesses in your security before attackers do, thus taking the advantage away from bad actors.
This Rhymetec penetration testing FAQ explores key questions, including what penetration testing is, how it works, why it matters for organizations, how it compares to a vulnerability scan, and how much it can cost.
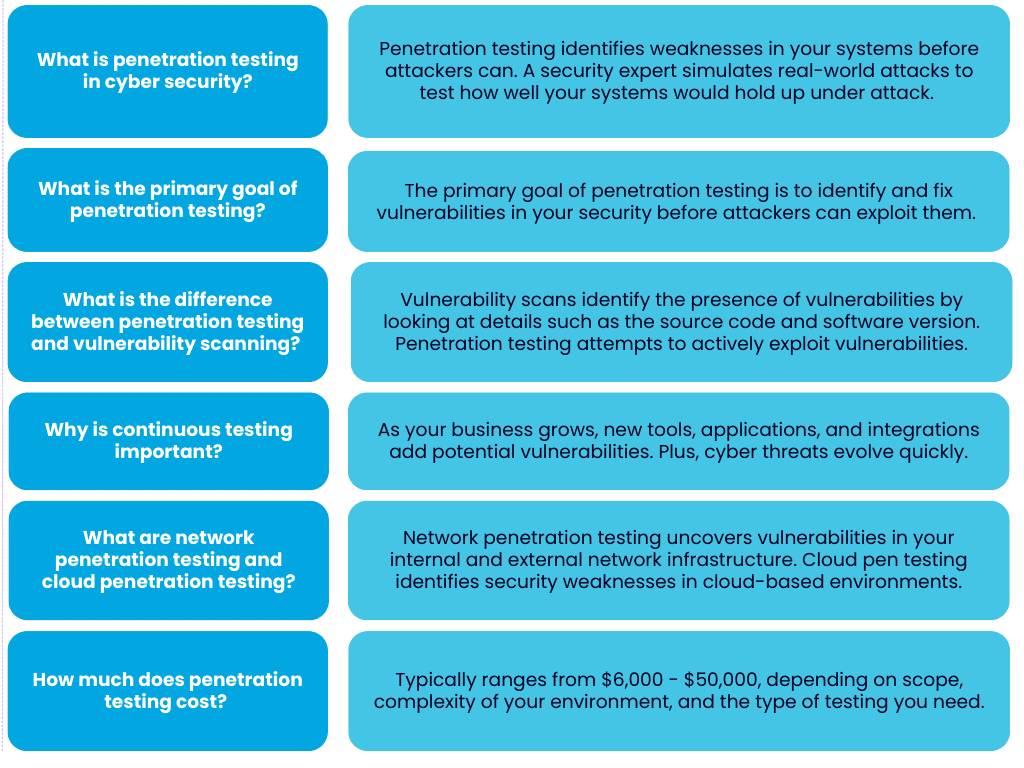
What is penetration testing in cyber security?
Penetration testing is a way to identify weaknesses in your systems before an attacker does:
During a penetration test, a security expert will simulate real-world attacks to test how well your systems would hold up if they were actually under attack. This allows them to pinpoint vulnerabilities that could allow a real attacker to gain unauthorized access and/or expose your sensitive data.
At the end of your penetration test, you’ll have a clear picture of the gaps in your defenses.
You can think of a penetration test like hiring a professional to test the locks on your building’s doors and windows, but the locks are your firewalls, applications, and networks. After uncovering your potential vulnerabilities, a good pen testing firm will also advise you on where to go from there and provide you with a roadmap to remediate gaps.
What is the primary goal of penetration testing?
The primary goal of penetration testing is to identify and fix vulnerabilities in your security before attackers can exploit them.
The process simulates how a real attacker may attempt to breach your defenses, providing you with insights to act on that are vastly more informative than results from automated scans or theoretical security risks.
After a penetration test, you’ll have a clear list of vulnerabilities that need to be addressed, as well as an understanding of the risks these issues pose to your business.
Understanding the tangible impact these risks could have enables you to prioritize which vulnerabilities need to be remediated first. Being able to effectively prioritize risks and allocate resources accordingly (and within the constraints of budgets and resources) is another goal of penetration testing.
Example of Security and Compliance Risks Addressed by Penetration Testing
Let’s take an example of a vulnerability that is frequently uncovered during a penetration test and its potential impact:
An overlooked patch could lead to financial loss, downtime, or even damage customer trust. By conducting a penetration test, you bring issues like this to light and can then prioritize actions that have the most significant impact.
In terms of risks of non-compliance, it’s important to know that penetration testing is often a compliance requirement and is an industry-standard way to fulfill a range of controls. For SOC 2 compliance, for example, penetration testing can address the risk of unauthorized access to systems that process or store customer data.
Including a penetration test in your SOC 2 readiness assessment prepares you to show auditors that you’ve covered a range of requirements.
However, compliance alone shouldn’t be the end goal! A good pen test helps you align security measures with the unique threats and challenges your business faces, creating a more resilient system overall as your business continues to grow.
Bonus Tip For Startups: Penetration testing can strengthen your position with investors. Demonstrating a commitment to cybersecurity via gold standard measures like penetration testing signals that your business is ready to handle risks that could impact revenue or reputation.
Additionally, as previously mentioned, penetration testing fulfills requirements under a vast range of both voluntary standards and legal requirements that investors may want to see, particularly if you’re targeting enterprise clients.
What is the difference between penetration testing and vulnerability scanning?
Both penetration testing and vulnerability scanning should be cornerstones in your cybersecurity strategy.
However, it’s important to understand the key differences between these two measures:
The key difference between penetration testing and vulnerability scanning is that vulnerability scans identify the presence of vulnerabilities by looking at details such as the source code and software version but do not attempt to exploit the vulnerabilities.
Penetration testing goes further. Ethical hackers attempt to exploit vulnerabilities to see if they could lead to a security incident. Penetration testing is significantly more robust than vulnerability scanning and allows you to identify the most critical real-world risks and focus your remediation efforts on them.
A vulnerability scan is a great first step for identifying surface-level issues and known vulnerabilities, while penetration testing gives you an understanding of how these issues could be exploited in practice, finds additional potential issues beyond what a vulnerability scan would uncover, and enables you to strategically prioritize remediation of your most pressing risks.
Bonus Tip: If your organization is looking for a firm to run vulnerability scans or conduct a penetration test for you, it’s extremely important to understand the differences between penetration testing and vulnerability scanning.
Buyers of security services may encounter issues differentiating between these two measures as a result of technical jargon and a lack of transparency from vendors. Unfortunately, some vendors will claim to offer “penetration testing” that is really just vulnerability scanning and may not be suited to meet your security or compliance goals.
What are the differences between a manual and automated penetration test?
The main difference between manual and automated penetration testing is how vulnerabilities are discovered. What firms may refer to as “automated penetration testing” identifies potential vulnerabilities by scanning for known issues.
Although this is an effective way to discover vulnerabilities quickly, it limits the test to what is already documented in the vulnerability database and does not provide an idea of how these vulnerabilities could be exploited in a real-world scenario by a bad actor.
Zero-Day Attacks and Automated Penetration Testing
A major limitation of automated penetration testing is it cannot detect issues that could lead to zero-day attacks, a type of attack that exploits a vulnerability that is entirely unknown to the security community. Because these vulnerabilities have not been documented, they are some of the most dangerous threats organizations face.
Automated penetration testing relies on databases of known vulnerabilities, leaving a major gap in your security assessment if you rely solely on automated methods. Manual penetration testing is much more involved and remediates this issue by leveraging human expertise and creativity.
The Stuxnet attack is a notorious example of a sophisticated zero-day attack. This malware targeted Iran’s nuclear facilities in 2010 and exploited multiple zero-day vulnerabilities in Windows systems and industrial control software. The attack was able to bypass traditional security measures because it exploited flaws that no one knew existed at the time.
While no test can accurately predict every possible zero-day vulnerability, manual penetration testing greatly reduces the risk by finding security gaps that automated tools miss.
Attackers Leverage Both Automated and Manual Tools
Attackers don’t rely solely on automated tools, so neither should your penetration testing!
While automated tools can provide a baseline of security by revealing common issues, without manual testing, you risk overlooking a range of serious issues that could lead to a breach.
Manual testing is also more specific. The tester considers your specific business context, such as the value of your data, the risk associated with your technology stack, your risk appetite, and the tactics an attacker would be most likely to use against your organization.
Red Flags Indicating An Overly Automated Penetration Test
If your penetration test feels rushed, provides generic results, or lacks detailed explanations specific to your business, it may rely on heavily automated tools.
Additionally, if the timeline seems unusually short for the scope of work, or if the report lists vulnerabilities without contexts or recommendations, your provider may be running scans without performing the deeper analysis that manual testing entails.
You should always ask your provider about their process and request a scope of work. A reputable firm will explain how they combine automated tools with manual techniques, provide examples of past testing scenarios, and describe the skills and experience of their pen testers.
Why is it important to continuously conduct penetration testing for a strong security system?
Your systems and environments are not static.
As your business grows, new tools, applications, and integrations are introduced – each adding potential vulnerabilities. Cyber threats evolve just as quickly, with attackers developing new techniques to bypass existing defenses.
Continuous penetration testing helps you keep up with these changes and minimizes the likelihood of an unknown vulnerability turning into an incident.
Compliance requirements also often call for regular penetration testing, but compliance isn’t the only reason you should be conducting pen testing. Regular penetration testing creates a process where risks are identified and addressed, rather than waiting and having to react to what could have been avoidable incidents.
For organizations like startups where change is constant, ongoing penetration testing helps you stay informed and ahead of threats as the threat landscape evolves.
Continuously conducting penetration testing protects sensitive data and reduces the overall cost of addressing vulnerabilities by catching them early while reassuring stakeholders and customers that security is a consistent priority for your business.
What is network penetration testing?
Network penetration testing uncovers vulnerabilities in your internal and external network infrastructure:
Internal networks include devices and systems within your organization, such as local file shares, servers, and employee workstations. External networks are the points where your systems interact with the internet, such as public-facing websites or VPN gateways.
A network penetration test mimics the actions of a hacker attempting to exploit weak points specifically in your network. For example, this could take the shape of testing firewalls to see if they’re properly configured, identifying open ports that could allow unauthorized access, or determining if you have any outdated protocols leaving your systems exposed.
Bonus Tip: Network penetration testing is particularly relevant as remote work and cloud adoption expand! These trends increase the complexity of network environments and expand your attack surface. Regular network testing helps you maintain visibility and control over your infrastructure and minimizes the risk of unauthorized access or disruption.
What is cloud penetration testing?
Cloud penetration testing identifies security weaknesses in cloud-based environments by testing the security of APIs, the configuration of your cloud infrastructure, how access controls are managed, and more.
An example of a common issue in cloud environments that cloud penetration testing often reveals the presence of is misconfigured storage. Sensitive data can be easily left exposed to the internet if storage is misconfigured.
Another example is overly permissive access controls that allow unauthorized users to interact with resources they should not have access to. Cloud penetration testing simulates attacks to help you find and remediate these risks, among others.
Bonus Tip: Cloud security is often a shared responsibility with your cloud provider. While providers like AWS or Azure manage the security of the underlying infrastructure, you are responsible for securing how you use their services. A penetration test helps you verify that your configurations align with both security best practices and your business needs.
How much does penetration testing cost?
The cost of a penetration test depends on the scope of the test, the size and complexity of your environment, and the type of testing you need.
For smaller organizations with a relatively straightforward network or a single application, a test may range from a few thousand to several thousand dollars. Larger organizations with more complex systems can anticipate higher costs due to the amount of time and resources required.
Specialized tests, such as those targeting cloud environments, APIs, or compliance requirements, may also carry a heavier price tag. A basic external test that focuses on your public-facing systems will generally cost less than a more comprehensive internal test that examines your entire network.
While penetration testing is an investment, it helps reduce the potential costs of a breach, which can include lost revenue, damaged reputation, and non-compliance issues. Understanding and remediating your risks early on can save your business substantially in the long run. Hopefully this penetration testing FAQ provided a solid idea of the cost-benefit analysis of investing in pen testing for your organization.
Penetration Testing FAQ:
In Conclusion: Penetration Testing FAQ
We hope this penetration testing FAQ provided helpful information and gave you a deeper understanding of penetration testing and what to look for when assessing vendors.
If you have further questions, our experts at Rhymetec are happy to help. We offer a range of penetration testing services, including:
- API Penetration Testing
- External Network Penetration Testing
- Mobile Application Penetration Testing
- Web Application Penetration Testing
Contact us today to learn more.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
Interested in reading more? Check out more content on our blog.