Why is it that cyberattacks are so hard to stop? Why do organizations need to continually invest in security? And why are measures like phishing training for employees mandated under so many cybersecurity regulations and standards?
The answer is a strange one:
Trust.
For better or for worse, humans are naturally trusting. We want to trust that the used car we bought won’t have any issues missed by the inspection, that our Grubhub order will arrive when it says it will, that House of the Dragon Season 2 will be as good as Season 1, and that the email purporting to be from our CEO giving us a $500 bonus is legitimate.
Statistically, phishing is the number one way that your organization may fall victim to a cyber attack, and it’s precisely because of our tendency to trust:
According to ReliaQuest’s 2024 Cyber-Threat Report, threat actors predominantly use methods that work by “exploiting the trust and vulnerability of unsuspecting individuals.” To any experienced security professional, it’s unsurprising to hear the report found that phishing was used in 71% of all security incidents in 2023.
There are a million terms for phishing: vishing, smishing, whaling, qrishing (yes, somebody has actually made ‘qrishing’ a word; no, you don’t need to know what it means because even Google Docs flags it as made up).
When you cut down to it, every type of phishing involves abusing people’s trust in order to gain some advantage, whether financial or informational in nature. If a threat actor or ransomware group gets privileged access to your organization, odds are it will be through phishing.
This fact has both an upside and a downside:
The upside is that it gives you an area to focus on that can help substantially reduce your company’s risk. The downside is that stopping phishing attacks is a hard problem.
Fortunately, simulated phishing is an excellent tool that allows you to prepare employees for the real thing before they get an email that could lead to a ransomware attack. This article will answer the following questions:
- How is phishing training conducted?
- Do I need phishing training for employees?
- Which cybersecurity standards and regulatory frameworks require phishing training?
- What are the top current recommendations from experts to mitigate risk from social engineering attacks?
- What is the role and importance of an incident response plan?
Let’s jump right into the steps security professionals take to simulate how threat actors carry out phishing attacks and how you can conduct phishing training for employees:
Phishing Training For Employees Phase 1: Reconnaissance
Being with the assumption that you know nothing about your business.
Your job is now to take the perspective of a threat actor. What can you find out about employees and your company through open-source intelligence (OSINT)?
First, you need to find your company’s email format, such as john.doe@madeupcompany.com.
This is exactly what a motivated attacker would do.
There are several areas you can look for this information:
- Are employee emails listed on previous press releases?
- Do employees have their work email addresses listed on their LinkedIn profiles? By default, LinkedIn reveals huge amounts of both personal and professional information.
- Are any corporate email addresses related to individuals listed on the website?
Once you have this information, try to find out about the hierarchy of the organization. Who reports to whom? Who does what? A motivated threat actor may send incredibly detailed phishing emails to employees involving key aspects of their role or job duties.
Every piece of information you leverage should be publicly available to make the phishing exercise as realistic as possible.
Phase 2: Write Phishing Emails
Many organizations conduct simulated phishing with hopelessly generic emails that don’t mimic the real thing. When building your phishing account and writing emails, take the perspective of a motivated and sophisticated threat actor who has done their homework.
Here are a few tips you can use:
- Register an email with a domain that is very similar to your organization. If your company is called “john.doe@faketestcompany.com,” you can register “john.doe@faketstcompany.com.” (Fun fact: Our brains like to fill in the gaps when letters are omitted. This is one of the many ways phishing attacks prey on human psychology so effectively).
- Don’t use ChatGPT or other LLMs. Write the emails with care and precision, and mention key elements of the person’s job if you were able to identify them during the reconnaissance phase. If you decide to send out mass emails that aren’t targeted, utilize company language or recent company events as a real attacker might.
- Make your subject line an urgent one. For example, depending on the person you are targeting, adding “EMERGENCY” to the subject line is one way to do this. This can help make people miss the key element.
- Have a call to action. Downloading a benign file is common in simulated phishing tests. Another option is to set up a web page to “capture” their corporate credentials, as an attacker might.
Phase 3: Establishing A Baseline
If you do your job well people are going to click.
If you do your job exceptionally well, people are going to click…a lot.
Once you’ve set up your domain and carefully crafted your phishing emails, it’s time to send them out to individual employees. This baseline will help identify which employees are the most susceptible to phishing.
A few tips during this phase:
- Don’t punish or shame employees for falling for it. If you punish employees, you will disincentivize them from reporting phishing attacks in the future.
- Make it clear that the purpose of the exercise is to simulate a real attacker and not to embarrass employees. Show employees why it’s important to do these exercises.
- Show employees where you found their information that enabled you to craft your emails so that they can reduce their online footprint.
During this phase it can also be worthwhile to have employees review a service such as haveibeenpwned to see if they have credentials that are being traded on the dark web as well, as this is another common vector of attack.
Services like Picnic that search the web for personal information are also helpful to show employees. Picnic provides enterprises with the capability to manage their external human attack surface and to detect, prevent, and protect against social engineering attacks.
Using both dark and clear web monitoring services enables employees to pinpoint exactly where their information is available online and stay ahead of bad actors.
Phase 4: Training Employees
Follow up immediately and personally with employees who have downloaded a file or submitted credentials to your fake web page. There are many free or paid security training courses that you could prescribe to the individual.
Work with them to go over common phishing email tactics and strategies to avoid them:
- Focus on providing customized instruction and time one-on-one. Employees should never be publicly ridiculed for clicking phishing links.
- Showcase real examples of phishing emails that the company has received (or use online resources) to provide examples.
- Emphasize that phishing can come in many forms. Any emails that aren’t expected from known entities should be carefully scrutinized.
Don’t come across with the mentality of, ‘simulated phishing exercises won’t end until the click rates get better.’ Instead, provide educational material that will help people feel comfortable reporting incidents.
Statistics like the following can be used to help illustrate the importance of coming forward: In the case of a type of phishing attack where threat actors impersonate banks, over 50% of victims are able to recover most of their money.
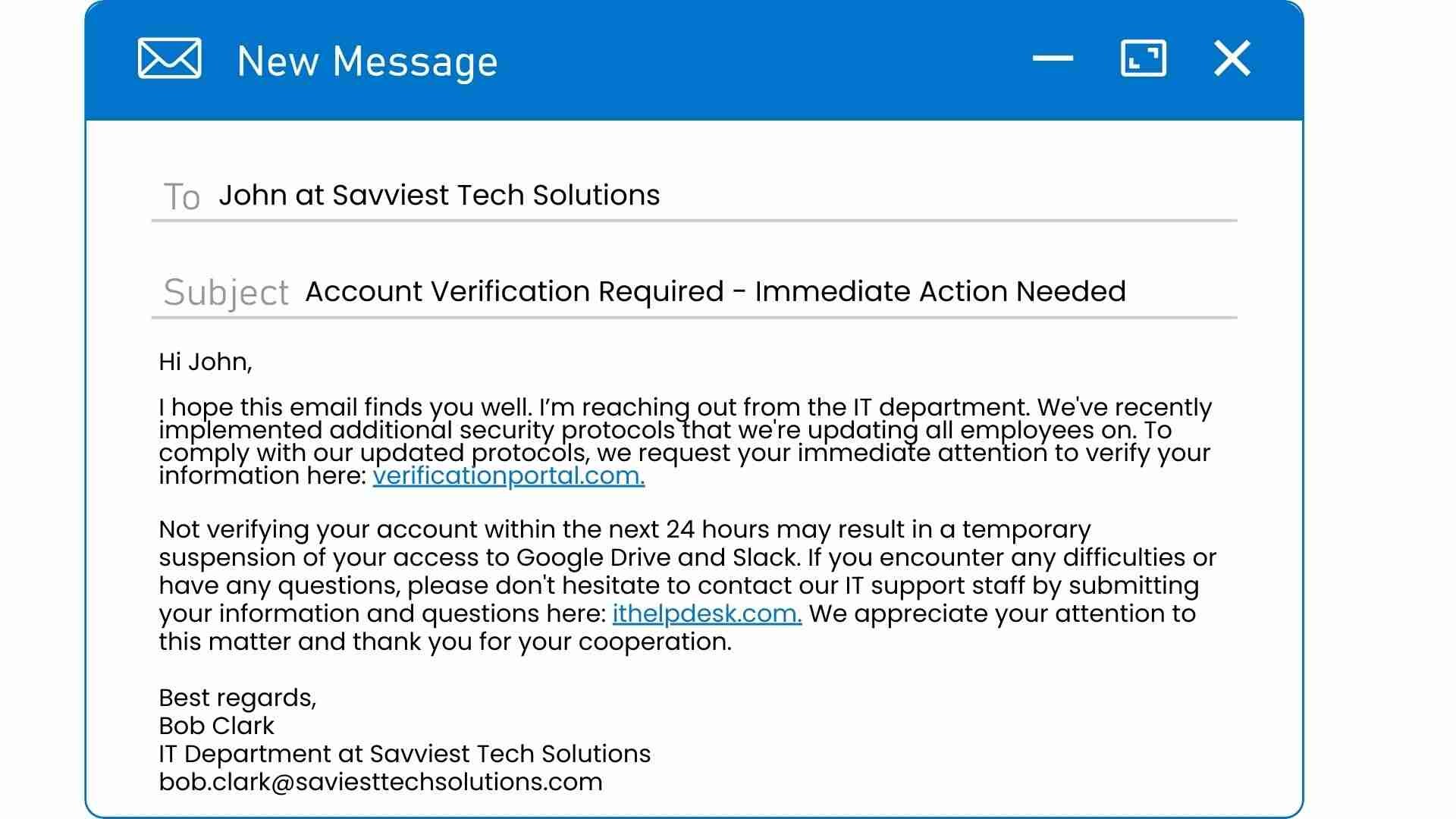
Example Of A Phishing Email
Here is an example of a more sophisticated phishing email that you might use as part of your training materials:
Can you spot what gives it away as phishing?
And, even more importantly, would every single person at your company be able to spot it as phishing if they saw it in their inbox?
The key elements here are:
- The misspelling in the sender’s email address: Note the misspelling in the sender’s email address (bob.clark@saviesttechsolutions.com). It doesn’t match the official domain name of our fake company (Savviest Tech Solutions). This is almost always a sign of phishing.
- The urgent call to action: This is common in many types of scams, not just phishing attempts. The scammer will attempt to instill a sense of urgency to create stress and try to prevent the victim from having time to think.
- The use of a fear tactic: Although not explicitly threatening, the email states that failure to comply may result in the recipient having their access to important systems suspended. This could create a fear of their performance at work being impacted.
- The link with a request for personal information: Any link asking for your credentials should always be thought twice about before clicking.
- The nature of the request itself: The recipient of this email should be extremely wary if this is the first time they’re hearing about the new “security protocols” at their company.
Phishing Training For Employees Phase 5: Reiterate and Collect Data
Within weeks to months, you should run another test.
Compare your results to the baseline data:
- Have employees substantially improved?
- Are there repeat offenders who have fallen for multiple tests?
These are excellent statistics to collect and can be powerful, as they enable you to measure your program’s effectiveness.
Do You Need Phishing Training For Employees?
If your company uses email (or if your employees have cell phones, as texting can be another vector for phishing), the answer is simple:
Yes.
As stated above, phishing is extremely common and is the number one way organizations fall victim to cyberattacks. In 2023, over 25% of U.S. employees clicked a link in an email that opened a suspicious website.
If you are a startup or a small business, the answer is just an even more emphatic yes!
Cybersecurity for startups and small businesses is critical, as they are being increasingly targeted by threat actors. When it comes to phishing, the risk appears higher for smaller companies:
Consider the fact that an employee at a company with fewer than 100 employees receives 350% more phishing emails in their inbox than an employee at a large company.
This makes security awareness training one of the most effective ways to mitigate cybersecurity risk for SMBs.
Does phishing training for employees actually work?
Yes!
Threat actors engage in phishing because it’s one of the most effective and low-effort tools they can use to gain access to usable credentials like passwords. Prevention is key when dealing with threats from phishing, and thankfully, training works:
According to Proofpoint’s 2024 State of the Phish Report, 84% of U.S. organizations reported that after their employees underwent security awareness training, the ability to spot phishing attempts improved, and click rates on phishing emails decreased.
That represents a lot of users who avoided clicking a link that would’ve delivered malware like a virus or ransomware to their computers.
Do I need phishing training to meet controls under cybersecurity standards and regulatory frameworks?
If you are trying to ensure best practices for your cybersecurity – as well as compliance with standards relevant to your industry – you absolutely need to conduct robust security training.
Security awareness training is one of the top Critical Security Controls recommended for SMBs by the Center for Internet Security (CIS):
- Control 14: Security Awareness and Skills Training. Establish and maintain a security awareness program to influence behavior among the workforce to be security conscious and properly skilled to reduce cybersecurity risks to the enterprise.
- Control 14.2: Train Workforce Members to Recognize Social Engineering Attacks.
- Control 14.6: Train Workforce Members on Recognizing and Reporting Security incidents.
The CIS is far from the only entity to include security awareness training in its guidelines.
The laws that require security awareness training include:
- The HIPAA Privacy Rule and the HIPAA Security Rule
- The Gramm-Leach-Bliley Act (GLBA)
- The Federal Information Security Management Act (FISMA)
- Massachusett’s Data Security Law
Security awareness training is also required under standards including:
- PCI DSS
- ISO 27002
- NIST Special Publication 800-53.
- GDPR
It is also a standard control organizations must fulfill as part of their SOC 2 audit.
The Bottom Line: Phishing training is one of the number one items addressed in security awareness training. A security awareness program that failed to include phishing training for employees would be viewed by auditors and regulators as insufficient.
The Top Current Recommendations To Mitigate Phishing Risk
The best-of-breed, most up-to-date practices to mitigate the risk of social engineering tactics are outlined in ReliaQuest’s 2024 Cyber-Threat Report. Here’s a summary from the report:
- Harden MFA Mechanisms: Implement a certificate-based authentication policy. Use digital certificates to verify the authenticity of users during the authentication process. Additionally, consider limiting the token lifetimes for MFA—by setting a shorter timeframe, you reduce the window of opportunity for attackers to exploit them.
- Add or use Alternative Authentication Factors: Consider implementing biometrics and adaptive authentication. Biometrics can include features like fingerprint or facial recognition, and adaptive authentication verifies users based on multiple factors, such as location, user behavior, and registered device.
- Train Employees: Develop regular training sessions and simulation exercises to teach employees how to recognize and report social engineering attempts, such as phishing emails, phone calls, and in-person scams. Teach employees to scrutinize email headers, links, and attachments and to report any suspicious activity.
- Enforce Password Security: Implement password policies requiring complex passwords (12-plus characters, uppercase, lowercase, number, and symbol), prevent password reuse, enforce password changes every 90 days, and enable MFA. Limit Access to Sensitive Information: Restrict information access to a need-to-know basis.
The Bottom Line: Phishing training for employees plays a key role in mitigating the risk of social engineering attacks and is one of the methods most commonly recommended for organizations by industry leaders in cybersecurity.
Why Do Companies Outsource Phishing Training For Employees?
Many companies choose to outsource phishing testing and training for several reasons:
Having a third party conduct your phishing testing and training is generally more robust from a security standpoint and works better from an auditing standpoint as well. The amount of work involved in phishing testing can also be a huge time suck and disruptive to daily business operations.
If your team has the security know-how and the bandwidth, you can certainly conduct phishing training for employees on your own using the 5 steps outlined above. But if you’re curious about how outsourcing phishing testing and training to the experts works, here’s Rhymetec’s methodology that we’ve implemented with hundreds of clients:
Rhymetec’s Method For Phishing Testing and Training
First, our Phishing Simulation Assessment determines the scope of the phishing campaign and which users to include. Our team has decades of experience in offensive security and is easily able to tailor the project to each organization’s needs.
We use the exact same techniques cybercriminals use: making minor changes in URLs, crafting convincing email messages, and conducting reconnaissance on employees’ online footprints.
The Phishing Simulation is scheduled to be performed at an agreed-upon time.
Once users fall for a phishing email or input their credentials into a phishing website, our team immediately provides security awareness guidance on what phishing is and how to spot phishing attempts in the future.
After the baseline assessment, Rhymetec produces a preliminary written report.
Our Phishing Platform Portal provides robust reporting to equip you with the information needed to create gradual improvements in your organization’s security. This is typically represented through a gradual decline in month-on-month phishing click rates.
Our platform provides actionable data on the number of users who viewed a phishing email, users who clicked the link in a phishing email, and users who entered credentials into a phishing website. Post-report, we send additional educational training modules to staff members who did not pass the assessment.
Rhymetec’s method is guaranteed to fulfill requirements for phishing training for employees under regulatory and voluntary standards, including SOC 2, GDPR, HIPAA, NIST, PCI DSS, and more.
In Conclusion: Two Key Recommendations For Phishing Training For Employees
We recommend conducting continuous phishing training throughout the year to keep employees mindful of phishing risks. Continuous phishing training can be an extremely powerful tool for reducing the risk that threat actors get access to your environment.
We also recommend having a solid incident response plan in place.
At the end of the day, people are only human, and mistakes happen. While measures like security awareness and phishing training for employees are essential and do work to mitigate a substantial amount of risk, nothing is foolproof when it comes to preventing human error 100% of the time. Having a documented incident response policy is vital:
We encourage companies to invest in prevention by preparing employees as best as they possibly can while also having a plan in place in case an incident were to occur.
Managed Security Services Providers like Rhymetec offer a full arsenal of prevention measures that mitigate a huge amount of risk, while also providing procedures, policies, and assistance in the event of a security incident.
To learn more about how our team can accelerate your security while keeping your budget in mind, contact us for more information.
About The Author: Metin Kortak, CISO
Metin Kortak is the Chief Information Security Officer at Rhymetec. Metin began his career working in IT security and gained extensive knowledge of compliance and data privacy frameworks such as SOC 2, ISO 27001, PCI, FedRAMP, NIST 800-53, GDPR, CCPA, HITRUST and HIPAA. He joined Rhymetec to build data privacy and compliance as a service offering. Under Metin’s leadership, these offerings have grown to more than 200 customers, positioning the company as a leading SaaS security service provider in the industry.