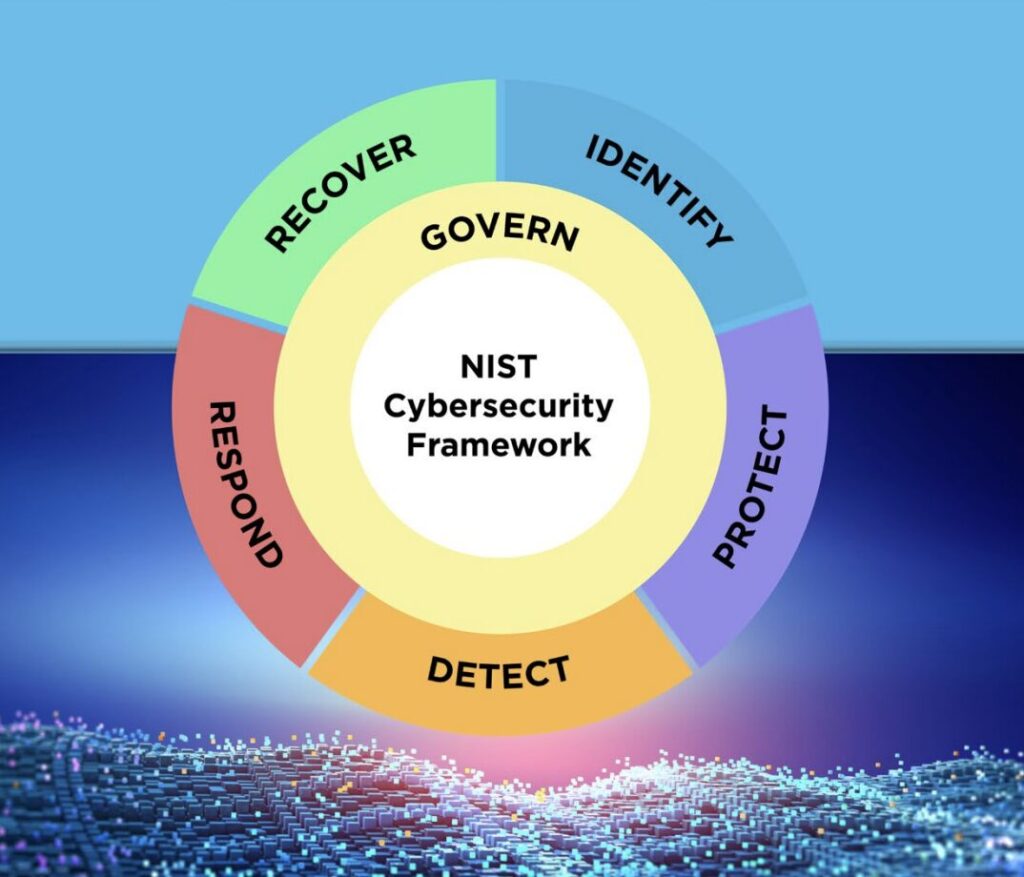
There have been many major releases in 2024. The hit new TV series FX Shogun, Dune Part 2, Taylor Swift’s Eras Tour on Disney+, and most importantly, the new NIST Cybersecurity Framework Version 2.0 with the addition of the NIST Governance Function.
Thrilled yet? Well, you should be. The National Institute of Standards and Technology regularly releases technical guidance documents and frameworks for both the public and private sectors to use as best practices guides.
The original NIST Cybersecurity Framework (NIST CSF) serves as the basis for tens of thousands of cybersecurity programs around the world and directly inspires many other compliance frameworks and requirements.
By meeting NIST, organizations automatically cover many controls in other requirements that overlap with NIST. It’s widely considered the gold standard of robust cybersecurity across many industries.
This article will explore NIST CSF V2.0, what’s changed, and what’s likely to change going forward.
What Is The NIST Cybersecurity Framework?
NIST CSF was originally intended as a cybersecurity framework for critical infrastructure companies.
Some key facts about NIST CSF V1.0:
- The original NIST CSF was released in 2014
- NIST CSF was developed in collaboration with industry and government stakeholders
- Provided a high-level framework for cybersecurity risk management
- Consisted of five core functions: Identify, Protect, Detect, Respond, and Recover
- Each core function is broken down into subcategories and controls
- NIST CSF is voluntary, but it is widely used by organizations of all sizes
- NIST CSF was updated on a regular basis to reflect changes in the cybersecurity landscape
In addition, many regulations (particularly those in the United States) directly drew on controls originally formulated in the NIST Cybersecurity Framework.
NIST CSF is split into five modules reflecting elements of the cybersecurity lifecycle, including:
Identify:
- Get visibility into the network environment, including asset categorization.
- Create continuous monitoring for new assets being brought back online or added to the network.
Protect:
- Implement robust security protocols across the organization to include IDS/IPS, firewalls, EDR systems, and anti-virus
- Create and maintain a regular patching program to reduce exploitable vulnerabilities.
- Utilize strong authentication (such as multi-factor authentication) to reduce the risk of unauthorized access.
Detect:
- Use security monitoring tools to get visibility into suspicious activity such as unauthorized access attempts.
- Set up a notifications and alerts system to inform your security team in a timely manner of potential incidents and threats.
Respond:
- Have a well-documented incident response plan that describes the procedures for responding to security incidents.
- Be able to contain security incidents to minimize their impact and mitigate further damage.
Recover:
- Ensure a comprehensive backup and recovery program is in place to protect critical assets and restore data in the event of a security incident or natural disaster.
- Test back up and recovery programs regularly and update as needed.
NIST CSF V2.0: What’s In It?
NIST CSF version two carries on many of the fundamental themes found in the original NIST CSF. However, a new element has been added: NIST Governance.
Source: NIST Drafts Major Update To Its Widely Used Cybersecurity Framework.
Note the clear emphasis of the guidance under this new function:
Governance
- Executives take on an active role in organizational risk management and collaborate on how potential cybersecurity gaps across the organization may impact broader objectives.
- Regularly hold dialogue among executives about risk management strategies, roles, and policies.
- Establish security goals tailored to the industry and organization at the executive level.
- Document and communicate security policies and expectations down the line to managers and individuals.
- Encourage collaboration at the executive level and across the organization about risk management strategies, including cybersecurity supply chain risk.
- Ensure cybersecurity risk management is explicitly rolled into overall Enterprise Risk Management (ERM).
In short, the updated CSF is intended to help executives communicate better about cybersecurity, with the goal of ensuring robust security through every level of the organization:
“The CSF helps organizations translate their terminology for cybersecurity and cybersecurity risk management into general risk management language that executives will understand.”
The features of the new version also help enforce that the CSF applies to small organizations as well as large ones, and can be easily tailored to fit their needs.
A New Addition: NIST Governance and What It Means For Businesses Going Forward
It’s important to remember, that compared to many functions of a business, cybersecurity in its current state is still extremely young.
Cybersecurity began as a sub-discipline of Information Technology.
In the 2010s, business leaders, particularly in industries with a heavy reliance on information technology, increasingly came to see cybersecurity as a standalone field – one that needed adequate resources and provisioning to succeed.
The NIST Governance section is an effort to add concreteness to cybersecurity as a board-level conversation in its own right and not just an offshoot of information technology. NIST states:
“The CSF’s governance component emphasizes that cybersecurity is a major source of enterprise risk that senior leaders should consider alongside others such as finance and reputation.”
It’s worth pausing for a moment and reflecting on what a significant statement this is.
NIST is advising companies to consider cybersecurity as significant of a risk as running out of money or having their reputation destroyed (note that bad cyber practices can cause both of these things).
The new NIST governance function includes six key aspects:
- Organizational Context (GV.OC)
- Risk Management Strategy (GV.RM)
- Roles, Responsibilities, and Authorities (GV.RR)
- Policy (GV.PO)
- Oversight (GV.OV)
- Cybersecurity Supply Chain Risk Management (GV.SC)
The introduction of Cybersecurity Supply Chain Risk Management (C-SCRM) under governance is another critical addition.
Software supply chain attacks have become increasingly common in recent years, such as the 2020 SolarWinds breach and the 2023 MOVEit vulnerability, famously exploited by the CL0P ransomware group.
Rhymetec’s Take: The business impact of investing in cybersecurity is exceptionally high. The threat landscape has continued to increase in risk, and organizations are increasingly expecting third-party suppliers to not only meet compliance but also demonstrate security that goes past it. NIST CSF’s Governance change is an excellent addition that reflects the growing importance of security for modern businesses.
The Expanded Scope: NIST Governance
NIST CSF V1.0 was focused specifically on critical infrastructure. While this did not stop organizations all over the world from using it as a basis, it did create a sense that it might be overkill for some businesses.
NIST CSF V2.0 has remedied this flaw and makes it clear that the CSF can be tailored to fit any business regardless of size or maturity.
Rhymetec’s Take: In this case NIST is catching up to where many organizations already are. NIST has long and widely been used as the basis for cybersecurity programs, but it is a positive development for them to acknowledge and expand the use case.
Additional Resources for Implementation and The NIST Governance Section
One of the most profound and significant changes has been the additional material NIST is publishing to help organizations build their security programs based on the cybersecurity framework.
NIST is publishing several appendix documents, including:
Implementation Guidance for CSF V2.0
The implementation guidance is an extremely valuable addition to the CSF.
Many organizations, particularly those that don’t yet have dedicated cybersecurity staff, may struggle to understand what the cybersecurity framework is actually asking of them. The addition of remediation guidance provides an enormous amount of additional clarity.
For example, let’s take a control found in the new governance section:
GV.SC-06: Planning and due diligence are performed to reduce risks before entering into formal supplier or other third-party relationships.
For seasoned governance risk and compliance professionals, this may seem straightforward.
But for an organization without GRC staff that is just beginning to think about third-party due diligence, how can this be implemented?
Fortunately, the Implementation Guidance provides real-life, concrete examples for businesses to better understand how to do a practical implementation of a security control. For GV.SC-06, NIST provides 4 implementation examples:
- Ex1: Perform thorough due diligence on prospective suppliers that is consistent with procurement planning and commensurate with the level of risk, criticality, and complexity of each supplier relationship.
- Ex2: Assess the suitability of the technology and cybersecurity capabilities and the risk management practices of prospective suppliers.
- Ex3: Conduct supplier risk assessments against business and applicable cybersecurity requirements, including lower-tier suppliers and the supply chain for critical suppliers.
- Ex4: Assess the authenticity, integrity, and security of critical products prior to acquisition and use.
For many organizations, implementation examples will undoubtedly be key to help clarify the request being made of them by the guidance. Note how each example has slightly different wording: compliance isn’t a one-size-fits-all project.
Many compliance requirements leave room for organizations to implement the security control in a way that will optimally benefit their organization.
Working with a vCISO can help by leveraging decades of experience in tailoring security controls to your company’s unique risk profile, maximizing your return on investment while also ensuring that your organization meets the technical and intended definition of the control.
For instance, example 4 only has the organization assessing critical suppliers, whereas example 1 has the organization tiering their suppliers and level of due diligence. If an organization is just beginning their C-SCRM program, they may not have the sophistication or resources (or need!) to fully vet every single supplier based on a tiered approach.
While the company matures, only assessing mission-critical suppliers can be an excellent addition to a security program, and it is far better than doing nothing.
Rhymetec’s Take: Implementation guidance should substantially help bridge the gap, particularly with small or immature organizations to effectively implement NIST CSF 2.0’s guidance. Note that simply claiming you are meeting a control will not pass an auditor’s scrutiny. You need to have a documented process for meeting the control, appropriate technology, and evidence that your policy is acted upon.
NIST CSF 2.0 Reference Tool
Another addition with NIST CSF 2.0 is a new reference tool that can be used to identify requirements and export data quickly.
Rather than reading a massive PDF, the new reference tool makes it simple to rapidly identify controls or subsets of controls within NIST and export that section or subset either in machine or human-readable format.
Users are able to filter based on the control family and whether the control is focused on first or third parties and then export the data into JSON or Excel. The reference tool also includes the aforementioned implementation guidance, significantly simplifying the process of understanding and complying with controls.
This makes it considerably more user friendly and allows easy exporting of data.
The reference tool could be helpful for many organizations, but particularly for large or complex organizations that may have many different individuals and functions responsible for implementing the second version of NIST CSF to include updates in alignment with the NIST Governance element.
NIST CSF 2.0 Quick Start Guides
The last major addition to NIST CSF 2.0 we will cover is quick start guides, designed to help organizations get started on implementing controls from NIST Governance and other functions based on their unique circumstances and risk posture.
Quick start guides are segmented into:
- Organizational Profiles: According to NIST, an organizational profile “…describes an organization’s current and/or target cybersecurity posture in terms of cybersecurity outcomes from the Cybersecurity Framework (CSF) Core.”
- Community Profiles: These are designed to help specific industries and sectors implement the CSF based on their unique risk profile. According to NIST, “A Community Profile can be thought of as guidance for a specific community that is organized around the common taxonomy of the CSF.”
- Small Business Resources: The small business section of the quick start guide is focused on providing actionable, easy-to-implement steps that small businesses can use to begin implementing CSF V2.0 controls.
- Cyber Supply Chain Risk Management (C-SCRM): C-SCRM is a growing concern for organizations of all sizes that continues to be highlighted by major supply chain breaches. The C-SCRM quick start guide provides specific guidance on how you can use the CSF to establish your C-SCRM program.
- Enterprise Risk Management: The Enterprise Risk Management quick start guide helps organizations better understand the implementation of NIST CSF 2.0, particularly NIST Governance, in a complex and multifaceted enterprise context.
- Tiers: NIST CSF 2.0 tiers “…can be applied to CSF Organizational Profiles to characterize the rigor of an organization’s cybersecurity risk governance and management outcomes. This can help provide context on how an organization views cybersecurity risks and the processes in place to manage those risks.”
Concluding Thoughts On NIST Governance and NIST CSF 2.0
NIST CSF 2.0 represents a huge step from the original NIST.
There has clearly been a focus on making it easier to conceptualize, understand, and implement CSF controls in a way that will reduce organizational risk for businesses.
The NIST governance section is a critical addition that helps solidify the case that cybersecurity and cyber risk management are no longer a function of the IT department, but a function that requires whole-business buy-in from the board of directors down to individual department heads.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while also balancing security with budget. We offer a full suite of security services including mobile application penetration testing services, phishing testing services, PCI compliance scanning, and more.
Our team has extensive experience helping organizations implement a variety of security frameworks and compliance requirements, including NIST CSF, SOC 2, HIPAA, GDPR, and many more.
We enable our clients to outsource the complexity of security and focus on what really matters – their business. If you are interested in our services, or if you simply have questions about security, you can contact our team for more information.
About The Author: Metin Kortak, CISO
Metin Kortak is the Chief Information Security Officer at Rhymetec. Metin began his career working in IT security and gained extensive knowledge of compliance and data privacy frameworks such as SOC 2, ISO 27001, PCI, FedRAMP, NIST 800-53, GDPR, CCPA, HITRUST and HIPAA. He joined Rhymetec to build data privacy and compliance as a service offering. Under Metin’s leadership, these offerings have grown to more than 200 customers, positioning the company as a leading SaaS security service provider in the industry.