Companies often find that SOC 2 compliance acts as a business enabler, unblocking sales and allowing them to break into new marketplaces.
However, obstacles like resource constraints and a lack of in-house expertise make crossing the finish line with compliance a challenge, especially for small and mid-sized businesses.
Achieving compliance with standards like SOC 2 can seem like a daunting task. In our latest webinar, Rhymetec CISO Metin Kortak spoke to Craig Saldanha from Insight Assurance about how to simplify SOC 2 compliance and navigate the 5 SOC 2 Trust Services Criteria:
Check out the recording to watch their discussion. A bit about the speakers:
Metin Kortak started his career in IT security and then joined Rhymetec to build data privacy and managed compliance as a service offerings. Rhymetec started as a penetration testing firm in 2015, and under Metin's leadership, we've expanded to do all things security and compliance, with a focus on working with startups.
Craig Saldanha from Insight Assurance has nearly 10 years of audit experience. He's an expert in GRC and third-party/vendor risk management. In his current role at Insight Assurance, he leads and manages SOC 2, PCI, & vCISO service lines.
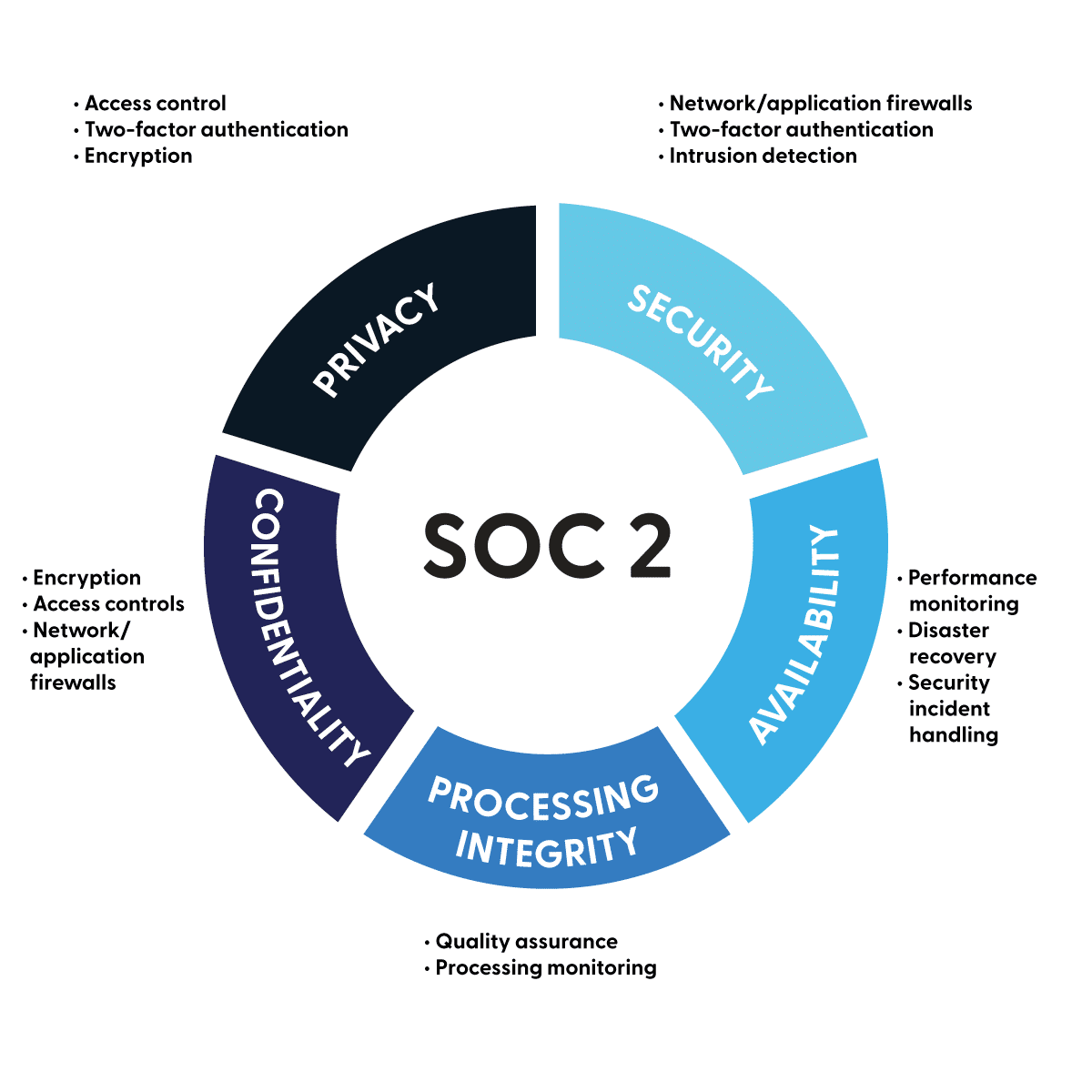
What Are The 5 Trust Services Criteria for SOC 2?
The SOC 2 Trust Services Criteria are used to evaluate an organization's controls related to data management. The 5 criteria are:
- Security (the protection of data against unauthorized access).
- Availability (the system's operational uptime and accessibility).
- Processing Integrity (ensuring that system processing is complete, valid, and accurate).
- Confidentiality (protection of sensitive information from unauthorized disclosure).
- Privacy (focuses on the collection, use, and retention of personal information).
"Security is the most common one that we see at Rhymetec," Metin noted.
The entire SOC 2 set of controls is over 150 controls. About 70% of that is likely going to be controls related to the security Trust Services Criteria. When customers are pursuing a SOC 2 assessment, security Trust Services Criteria are usually selected by default and included in every report.
The remaining 4 have fewer available controls to select. Some of them are more challenging to implement, which is one reason some companies just select the security criteria.
When it comes to which criteria to select, there are two main things to consider:
- What your requirements from your client base are
- What you value in your information security program
At Rhymetec, "We usually look at what our customers need, what is most important to them, and what their customer requirements are. A lot of organizations pursue SOC 2 because their clients are requiring them to have it, or they would like to pursue a larger client that has stricter requirements to start working with them," said Metin.
It also depends on what you value as a company. If you really value the availability of customer data and are concerned about privacy, you'd also want to select those criteria. Lastly, it also depends on factors like the type of data you handle and requirements specific to your industry.
At Rhymetec, we sometimes see customers pursuing all 5 Trust Services Criteria:
What Is SOC 2 and Why Are The SOC 2 Trust Services Criteria Important?
SOC 2 is a security and compliance standard created by the AICPA.
The primary purpose of SOC 2 is to ensure that third-party companies, SaaS providers, and other organizations protect their client information in a secure manner. SOC 2 compliance demonstrates your commitment to security and builds trust with your clients and stakeholders.
"Type 1 is a point-in-time audit and takes a much shorter time to complete with our customers at Rhymetec," Metin explained in our webinar. "We can usually get them compliant within about three months, and in some cases even less if they have already implemented some security controls."
For SOC 2 Type 2 (the more commonly sought type), companies are audited over a period of time.
Observation windows start at a minimum of three to six months, with some auditors requiring a 12-month period. Metin noted that, "...it makes the audit definitely more challenging, as companies are audited over the course of the observation window. If you missed an SLA (service-level agreement), or if an employee was onboarded incorrectly, that may cause some issues with your audit reports."
Getting expert input from the beginning of your SOC 2 journey can avoid these pitfalls, and enable you to choose the right criteria for your business.
From an MSSP (Managed Security Services Provider) perspective, Metin typically finds that there is a lack of understanding about the SOC 2 Trust Services Criteria in particular:
"When customers start working with us, we usually need to explain to them what the 5 Trust Services Criteria are and which ones they should select for their business. It's a very critical decision-making process."
So, let's jump right into what the Trust Services Criteria are, how to select the right ones for your business, and more:
Industry-Specific Examples for Each SOC 2 Trust Services Criteria
Let's take a closer look at each individual Trust Services Criteria:
1. Security
Regardless of your industry or what type of company you are, the security Trust Services Criteria is a mandatory component of the SOC 2 Report. It's required for all SOC 2 engagements and forms the baseline on which other criteria are then built.
For the next 4 criteria, we will provide examples of the types of companies that may opt to select each one:
2. Availability
Criteria around the availability of data apply to companies like online realtors and e-commerce platforms that rely on continuous uptime to support their customer transactions.
Telecom companies that provide communication services and need to maintain uninterrupted network availability would also want to explore availability criteria under SOC 2. Lastly, utilities and other critical infrastructure providers that need to ensure constant availability for operational purposes may opt for this set of criteria.
3. Processing Integrity
This applies to investment firms, accounting firms, and financial service providers that manage financial transactions and require accurate processing of data. Manufacturers that rely on automated processes for production and distribution would also want to consider the integrity selection criteria.
4. Confidentiality
"Law firms and legal service providers that handle sensitive client information would want to consider confidentiality," said Craig. So would consulting firms that deal with proprietary business strategies and government organizations that handle classified or sensitive information.
5. Privacy
Last but not least, privacy is often selected by schools, universities, and online education platforms to protect the personal data of students and staff. Likewise, online retailers that collect customer information for marketing purposes and healthcare organizations often opt for privacy criteria.
It's important to note that companies must roll out SOC 2 compliance across all locations and business units. Some adjusting may be needed if you operate across multiple regions to reflect nuances like local regulations and cultural differences. But in general, controls under the selected Trust Services Criteria should be consistently implemented.
Who And What Should Be In Scope?
The scope refers to the specific boundaries and focus areas that an audit will cover concerning the SOC 2 Trust Services Criteria.
By paying close attention to scope from the beginning, you can help reduce the scope and get through your audit easier. Here is what auditors will look for of who will be in scope, according to Craig:
"Any users that are critical to the delivery or the service that we are auditing should be in scope. In addition to anyone with access to sensitive data, customer data, or production data."
This could include your core team members across IT security, compliance, HR, finance, and operations, as well as consultants or contractors.
As for systems in scope (the what), it depends on 1) which systems impact your customers, and 2) which systems contain customer information.
"When we go through a SOC 2 Type 2 audit with a client, the auditors are looking into the production systems, production networks, and other production devices that actually impact customers. Staging environments or test environments that do not impact customer systems are not monitored or even audited," Metin explained.
If you have a SaaS product or other technical systems in place, you should think about what is actually in production and what impacts your customers. This also applies to any third-party vendors you work with.
If a vendor does not impact your customers in any way and does not process sensitive information, it will likely be assigned as low-risk and won't be subject to the same scrutiny as high-risk vendors (like your hosting provider or your email provider).
What Tools and Advice Should Companies Consider To Help Streamline Compliance?
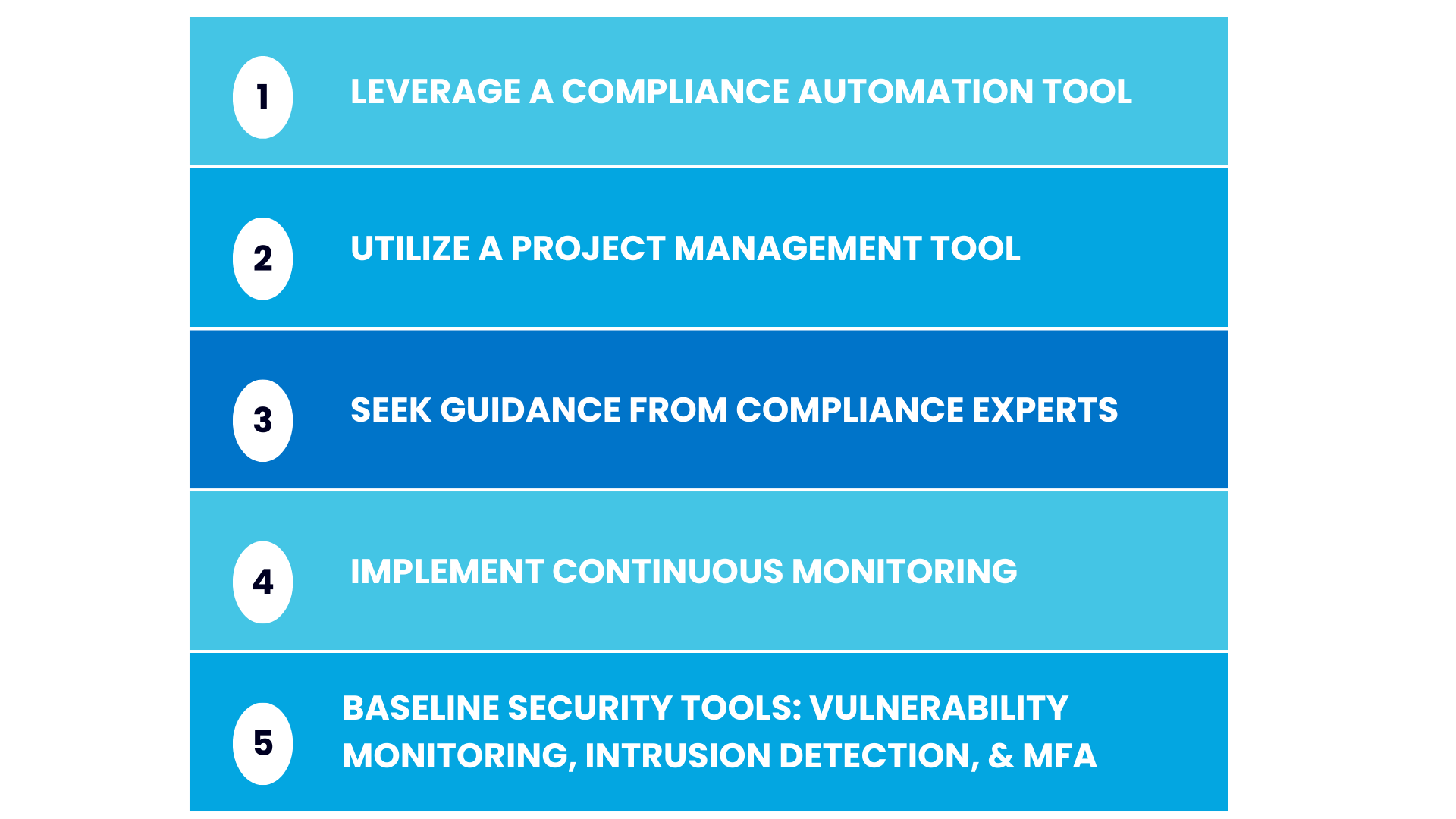
"First off, consider using compliance automation tools," suggested Craig. "We see clients save time to focus on their business by leveraging compliance automation tools in the market."
Spreadsheets don't cut it anymore. Compliance automation tools speed things up for everyone and are favored by auditors.
Having a solid project management tool is also very important.
There is a lot of work involved in SOC 2 compliance and there are typically 10 - 15 stakeholders who need to follow these controls and track them to completion. With a project management tool, you can add certain tasks (such as your penetration tests, access reviews, and risk assessments), assign them to the right personnel, and track them to completion.
Craig also suggested seeking guidance from compliance experts. Choosing the right vCISO and the right auditing partner for your business is critical, as is investing in internal training to ensure everyone understands their roles in your compliance journey.
Next, implementing continuous monitoring for compliance maintenance is extremely important. Any instances of non-compliance should be quickly rectified. Be sure to keep thorough documentation for your audit for any areas that fall out of compliance and how you addressed them.
There are some additional baseline security tools you will need to have, depending on which controls you select. These include vulnerability monitoring tools, intrusion detection systems, and a system to enable multifactor authentication.
5 Ways To Streamline Compliance
Concluding Thoughts: How Rhymetec Aligns SOC 2 Trust Services Criteria With Businesses' Operations & Goals
At Rhymetec, we enable businesses to align SOC 2 controls with their operations and goals to protect data, build customer trust, and meet regulatory requirements in their industry.
SOC 2 compliance shows that you take security seriously and mitigates risks. As demonstrated in our case studies with businesses like Kizen and Modicum, companies also find that having their SOC 2 report unblocks sales and opens up new market opportunities.
At Rhymetec, we see compliance and security as business enablers. We've helped over 600 companies establish scalable security solutions and get compliant in record time. Our custom solutions are specifically tailored to each organization we work with so their cybersecurity grows with their business and goals.
Explore our transparent pricingand schedule a time to chat with our team to learn more.
Interested in reading more? Check out additional content on our blog.