How are resource-savvy businesses fast-tracking and maintaining cybersecurity compliance in 2024?
Many companies are now using an innovative and complete solution that combines automation with hands-on, expert security services. Compliance automation platforms provide an invaluable tool that works in sync with manual tasks to achieve compliance in the fastest timeframe possible, helping you effectively prepare for your audit.
Our team of security experts at Rhymetec is extremely experienced with this process. We have helped hundreds of companies build strong infosec programs and meet compliance requirements while reaping the full benefits of an automation tool. For more information on how we can help with all of your security and compliance automation needs, contact our team today:
The Benefits of Compliance Automation
Compliance automation is an innovative tool companies use to establish and scale their information security (infosec) programs. The platform serves as a single source of truth for everything related to compliance, allowing companies to have sharp visibility into these areas and pinpoint exactly what they need to do.
Many companies elect to use an automation tool because they are astutely thinking ahead about their audits and what they can do to make the process easier. After all, what makes life easier for your auditor will ultimately make your life easier as well.
No auditor likes receiving headache-inducing 50-page Excel spreadsheets that they have to figure out how to navigate for every new engagement. Instead, auditors appreciate having a single place where companies can easily collect all relevant documentation laid out in a clear format. Compliance automation platforms provide exactly this.
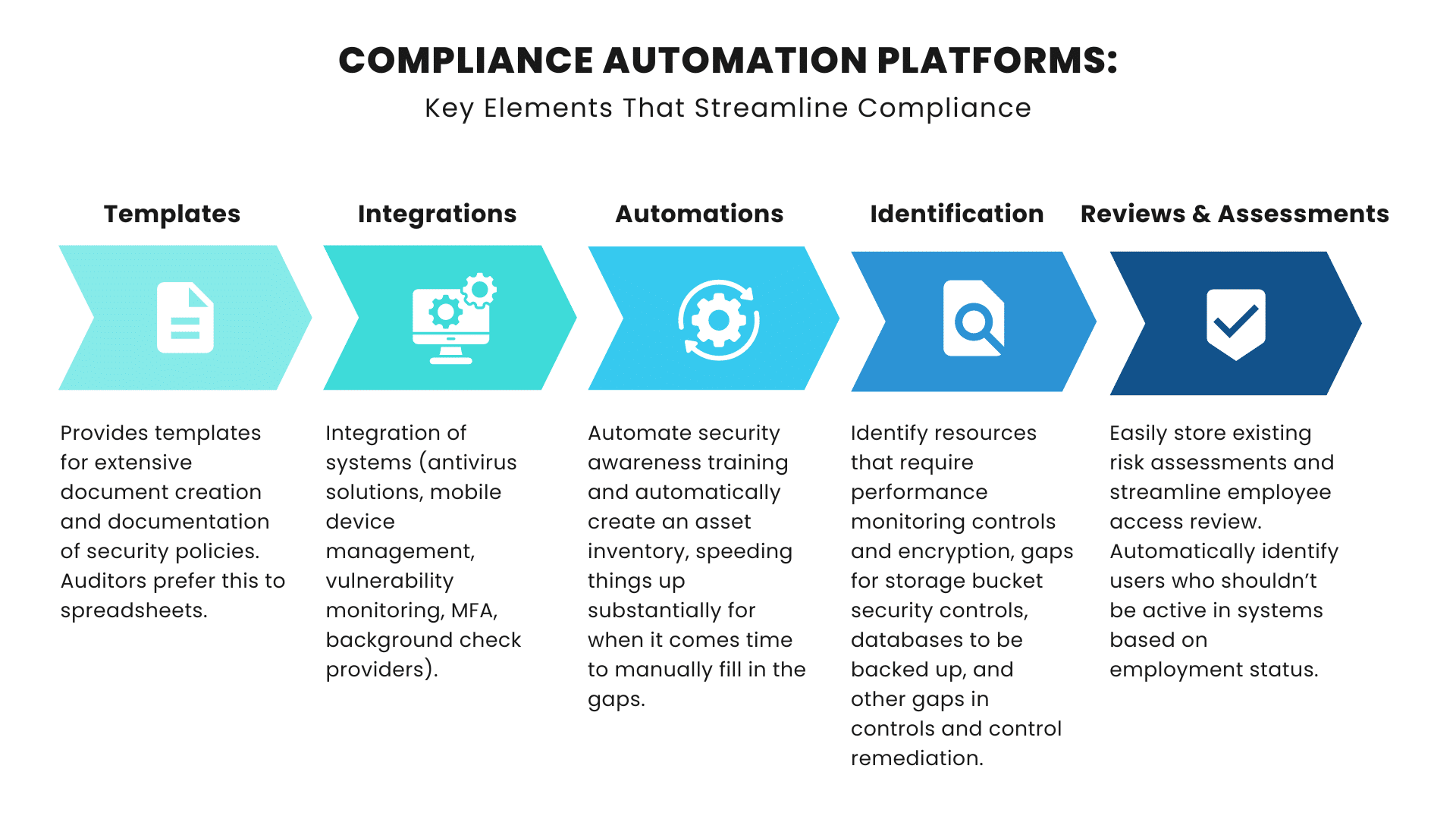
They streamline the process in many areas, accomplishing the following tasks:
Policy Templates:
Compliance automation platforms provide robust templates for extensive document creation and documentation of security policies.
Integrations Provided By Compliance Automation:
A key advantage of using an automation platform is the level of integrations it provides. Platforms provide integrations in the following areas (and more) in order to streamline compliance:
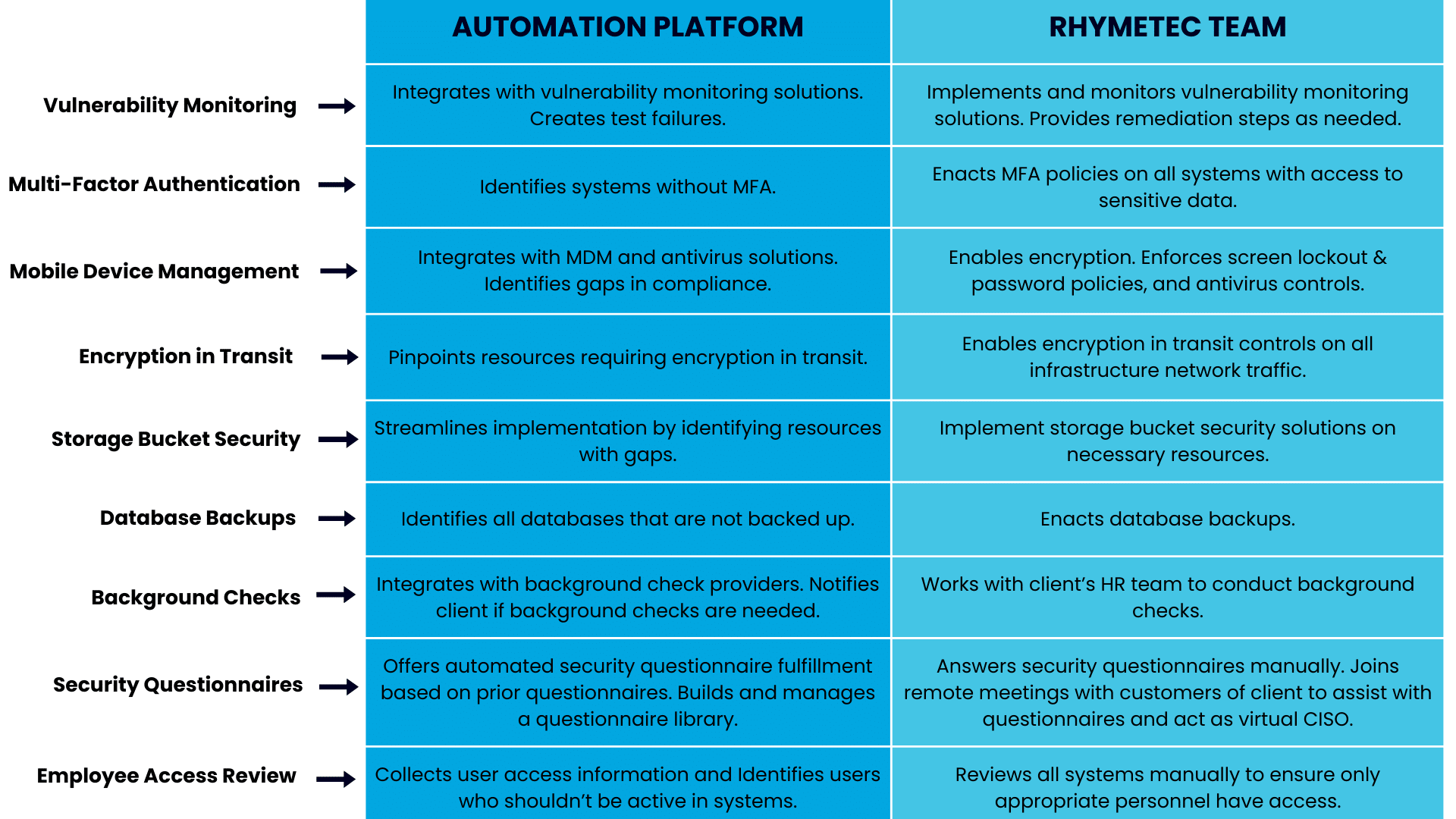
- Background check providers to notify clients if background checks are missing for any employees.
- Vulnerability monitoring solutions to create test failures based on vulnerabilities and source code tools for identification of testing failures.
- Relevant client systems to identify systems without MFA.
- Mobile Device Management and antivirus solutions to identify gaps in compliance.
Human Resource (HR) Security Solutions:
Automation platforms can automate security awareness training for organizations. This is an important advantage, as many frameworks require security awareness training. Employee access reviews can also be conducted by identifying users who shouldn't be active in systems based on their employment status. This is made possible by collecting user access information through integrations with other systems.
Frameworks like SOC 2 require periodic performance reviews for employees. These platforms provide a centralized place for evidence collection of performance reviews.
Asset Inventory:
The automatic creation of an asset inventory using available integrations is a key benefit, speeding things up substantially for when it comes time to manually fill in the gaps.
Identification Through Compliance Automation:
Compliance automation platforms automatically identify control items in the following areas:
- Resources that require performance monitoring controls.
- Resources that require encryption in transit.
- Resources with gaps for storage bucket security controls.
- Databases that are not backed up.
- Gaps in controls and control remediation.
Risk Management:
Compliance automation platforms store existing risk assessments conducted by the customer or security professional. Additionally, they provides 3rd party supplier management by storing existing risk assessments for all vendors, and their security reports.
Security Questionnaire Fulfillment:
Lastly, they offer automated security questionnaire fulfillment, removing a large amount of the burden of filling out long questionnaires.
The automation and integrations provided by compliance automation platforms speed up an array of complex processes that would otherwise take substantially longer. However, a security and compliance professional is still needed to ensure your team is doing the manual tasks of meeting your desired compliance goals; drafting policies, setting up company-specific security awareness training, conducting risk assessments, and much more.
Pinpointing The Controls You Need and That Align With Auditor Expectations
Don't have a security or compliance professional in-house? Or unsure where to start?
This is where an outsourced team of security professionals can come in to carry out a wide range of manual components necessary to get businesses across the finish line for compliance. Rhymetec's team provides the customization needed to make security and compliance efforts specific to your unique infrastructure every step of the way.
For example, one of the best parts of SOC 2 is the level of flexibility it provides for the controls, allowing companies the ability to tailor it to fit their needs. A compliance automation platform used in tandem with the customized services from an expert security team enables companies to speed things up while also ensuring they implement only the controls that make sense for their business and will align with what the auditor will expect to see.
The specialization provided by a security team allows businesses to avoid overly onerous control implementation that may not be necessary in their compliance journey.
The Manual Components of Compliance: Humans Still In The Loop
Compliance requirements and voluntary standards mandate an array of hands-on security support that only a team of qualified professionals with years of experience across different subdisciplines in cybersecurity can perform. To achieve and maintain compliance, organizations need a team of experts in GRC, penetration testing & vulnerability management, cloud security, network security, incident response, and more.
Compliance automation platforms provide a great way to manage the process and continually identify areas that need attention, speeding up the time it takes to get started and complete manual tasks. Meanwhile, the customization provided by working with Rhymetec's team ensures alignment between the controls and auditors' checklists. It enables clients to show evidence of completion of controls that cannot be automated, including penetration testing, internal audits, and tabletop exercises.
The Initial Phase: Getting Set Up
In the initial phase of the engagement, Rhymetec's security team gets the client set up in the compliance automation platform by manually accomplishing the following tasks:
- Initial Set Up In The Platform: Rhymetec manually adds the client's information to the compliance automation platform. Additionally, employees, users, and all other relevant information depending on the individual client's needs are added to the platform.
- Integration of Relevant Systems: Next, the team integrates relevant systems with the automation platform and configures settings to get items including security awareness training and onboarding setup.
- Project Planning: Rhymetec's team meets with the client to determine the infrastructure details and create a system description. The security team works closely with the client at this phase to gain a deep understanding of their individual needs and to identify the exact controls they need to adhere to under the chosen framework(s).
Compliance isn't one-size-fits-all.
Organizations can have vastly different needs depending on factors like their industry, geography, company size, the third parties they work with, the types of data they handle, and more. Without an experienced security and compliance team to examine these factors, there's a risk of not doing enough or even doing too much.
Filling In The Gaps
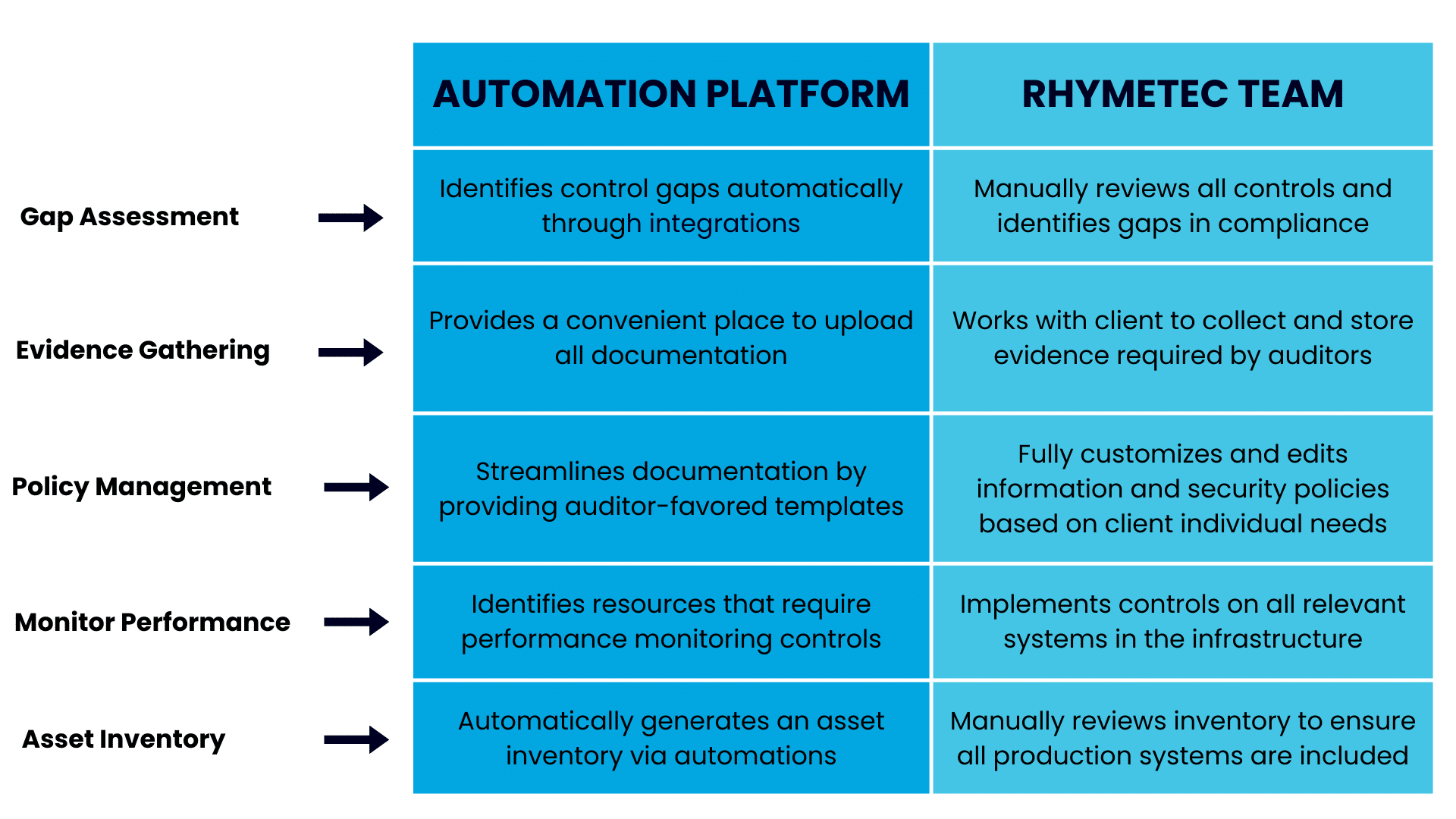
Using the information provided by the platform as a baseline, Rhymetec's team goes from there to fill in the gaps based on each client's individual needs. This stage involves:
- Gap Assessment: Rhymetec manually reviews all controls and identifies gaps in compliance for the client.
- Evidence Gathering: The security team works with the client and other stakeholders to collect and store evidence required by auditors, using the compliance automation platform as a convenient place to upload all documentation.
- Policy Management: Using templates provided by the compliance automation platform as a baseline, Rhymetec fully customizes and edits information security policies based on individual client needs.
- Performance monitoring controls: Based on the resources identified by the compliance automation platform, Rhymetec implements controls on infrastructure systems such as databases, servers, and buckets. This helps the client gain visibility into their infrastructure.
- Asset inventory: Using the asset inventory created by the automation platform, Rhymetec manually reviews the inventory and ensures all production systems are included in it.
These action items work hand-in-hand with the compliance automation platform in the following ways:
Completion of Manual Security Tasks
Thanks to the features of the compliance automation platform, many items are able to be easily identified as needed for the client on an ongoing basis. This substantially cuts down time, enabling the security team to fill in the manual pieces as soon as they are identified.
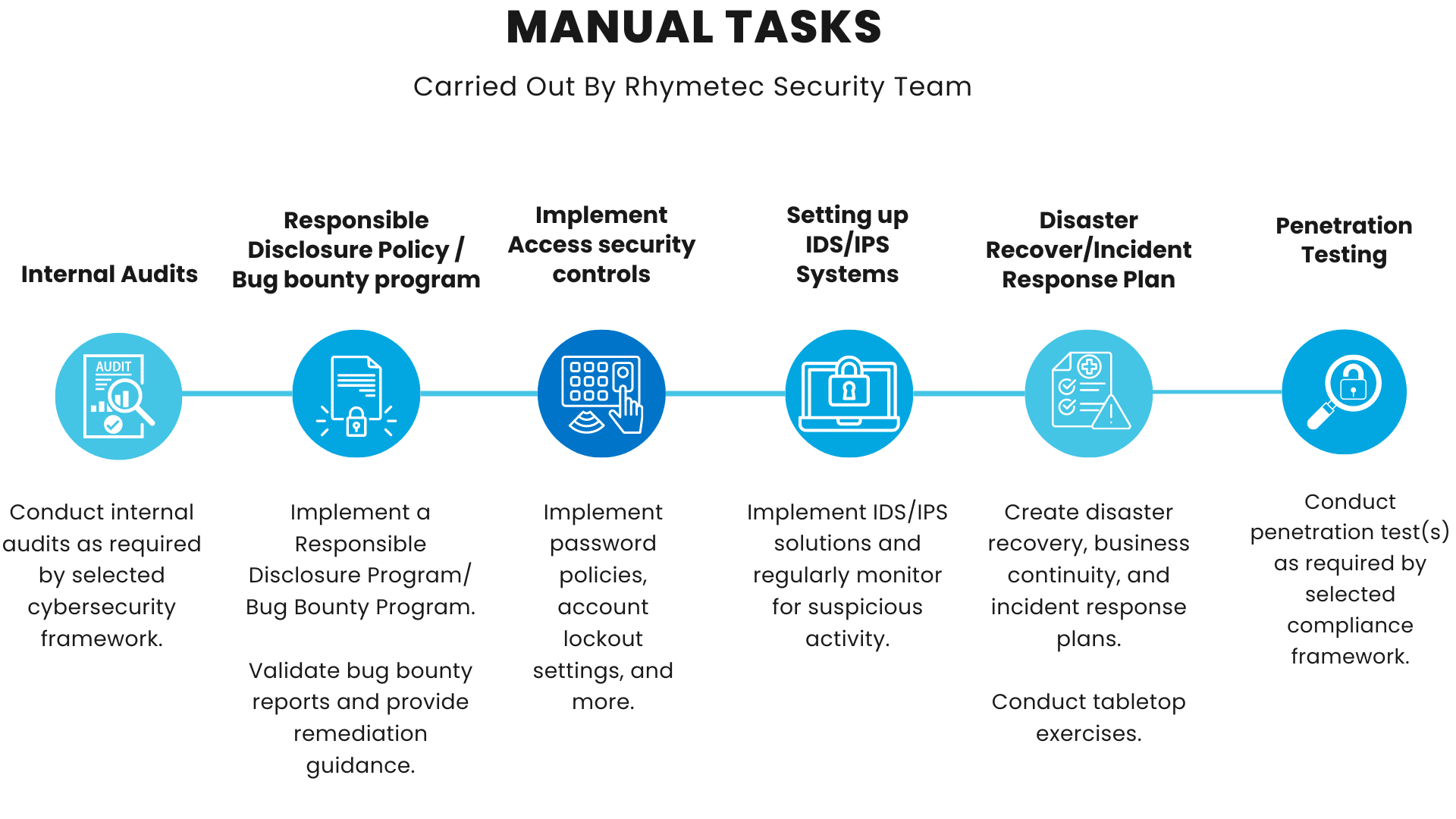
However, not every task has elements that can be automated. The fully manual tasks needed to meet controls under many cybersecurity regulations and frameworks include the following:
The above action items needed for compliance, such as penetration testing and tabletop exercises, cannot be automated. Items such as incident response plans also must be manually completed in order to be tailored to each individual company, their risk profile, and their industry.
The compliance automation platform comes back into play in the next phase, streamlining the completion of all additional security controls.
Fulfillment Of Additional Critical Security Controls: Manual Solutions Working With Compliance Automation
Rhymetec creates and implements the additional cybersecurity controls required by the compliance framework selected by the client. The compliance automation platform, meanwhile, plays a key role in this step for each control through system integrations and identification of areas for improvement.
Here's how the two solutions work in sync to streamline the implementation of critical security controls needed across many different frameworks, laws, and regulations:
The platform serves as a foundation for the tasks performed by Rhymetec's security team, enabling them to jump right in and start the hands-on work.
As an example, almost every cybersecurity standard nowadays requires organizations to implement multi-factor authentication, as it is one of the best measures companies can take to protect themselves. The compliance automation platform is able to identify systems in a client's infrastructure without MFA. The security team takes it from there to enable MFA policies on all critical systems.
Final Audit Preparation, Conducting The Audit, & After The Audit
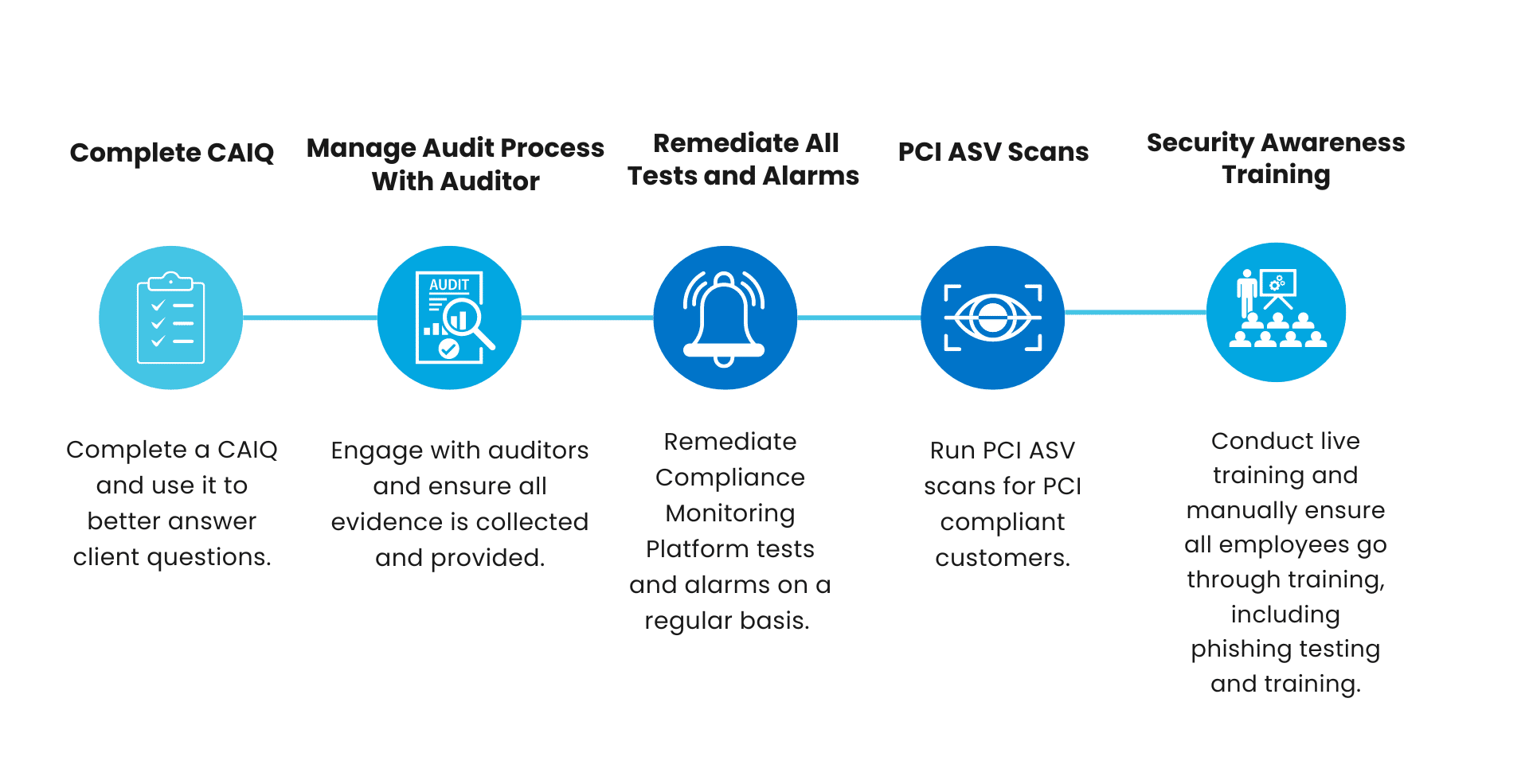
In preparation for the audit, Rhymetec ensures all necessary documentation is organized and accessible. For frameworks like ISO 27001, Rhymetec will conduct an internal audit to identify and address any non-conformities in preparation for the external audit. During the official audit, Rhymetec works closely with auditors to ensure all evidence is collected and provided.
For standards like SOC 2 that clients will be audited on annually, and to maintain a continuous strong posture of security, Rhymetec completes the following items on an ongoing basis: Annual vendor risk assessments, regularly updating risk assessments to reflect new risks, regularly reviewing firewall rules for customers to ensure they stay compliant with policies, and running continuous assessments like PCI compliance scans for PCI-compliant customers.
Don't forget, for some stakeholders compliance isn't always enough. Security questionnaires are a secondary tool that prospects use to evaluate your security against their own standards. Utilizing compliance automation can help you streamline this process. Using Rhymetec's team of experts can help you get into the weeds around more robust or complex questionnaires and even represent your business on security-related discussions.
In Conclusion: How Compliance Automation and Manual Security Services Provide A Full Portfolio Solution For The Modern Business
Compliance is not a sprint right before an audit.
It requires an ongoing solution that streamlines the process by automating the pieces that can be automated and leveraging a team of experts to fill in the gaps and carry out the manual tasks. Through a combination of automation and manual security services, organizations can maintain a posture of continuous compliance, ensuring that requirements are always being met and evidence of these standards can be accessed easily.
When used together, a compliance automation platform and the level of customization provided by an experienced security team fast-tracks compliance while avoiding a one-size-fits-all approach. Every company has its own controls that need to be implemented, as well as a unique risk profile. For effective compliance maintenance, modern businesses need an automation platform plus a team of security experts to carry out and maintain these requirements.
With Rhymetec, the manual components are accomplished by a security team with more than a century of cumulative experience across a diverse array of cybersecurity disciplines. Rhymetec leverages this experience to tailor compliance to fit organizations' individual needs and to maximize the efficiency of control implementation. Meanwhile, the compliance automation platform speeds things up every step of the way, provides a single source of truth for the client, and serves as an auditor-favored platform with all documentation presented in a clear format.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while also balancing security with budget.
We enable our clients to outsource the complexity of security and focus on what really matters – their business. If you are interested in our services, or if you simply have questions about security, you can contact our team for more information.
Interested in reading more? Check out our other blogs: