What are the most critical cybersecurity measures for small and medium-sized businesses (SMBs)?
We analyzed over 300 responses from security professionals to find out.
We identified the top 10 most important cybersecurity measures for SMBs, as well as the 5 most common obstacles SMBs face when building out or improving their security program. Using the information from our findings, SMBs can be better prepared to tailor their security program to expert-approved measures and stay ahead of the most common obstacles.
This research brief discusses the importance of cybersecurity for small and medium-sized businesses, our research methodology, results, and evidence-based recommendations. The findings address the following research questions:
- According to security professionals, what are the most critical cybersecurity measures and services for SMBs?
- Which obstacles do SMBs most frequently encounter when building out or improving upon their security program?
We answer these questions (and more), discuss practical implications, and provide 6 ways to balance security with obstacles like budgetary constraints that SMBs often face.
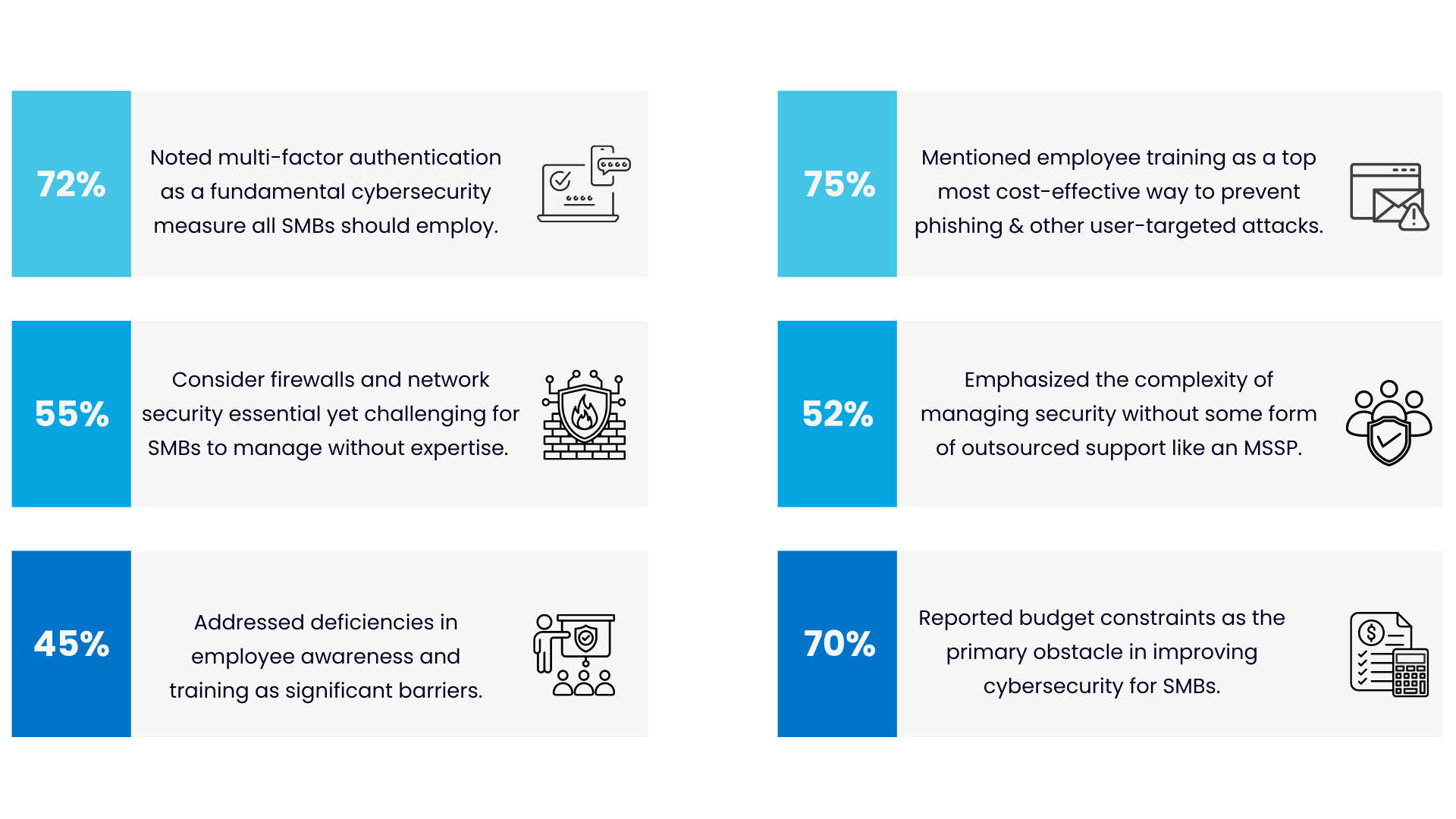
Before jumping in, here are a few of the most interesting findings to highlight:
SMB Cybersecurity Statistics
Data were collected through a systematic search of online cybersecurity forums. Using real-world discussions from online forums in research has several key advantages: The discussions provide a rich source of practical insights based on people’s firsthand experiences that are directly applicable to SMBs facing similar issues. Solutions and advice shared in forums are often scrutinized, debated, and validated by the community.
Data analysis leveraged both quantitative and qualitative methodologies to understand the significance of SMB cybersecurity measures and challenges discussed across threads (For more details on data collection and analysis, see the method section).
A thematic analysis identified recurring topics across the discussions, which were categorized into themes to reflect the main ideas and insights. A descriptive statistical analysis quantified the frequency and prevalence of certain terms, concepts, and themes within the dataset.
Results: SMB Cybersecurity Statistics From Over 300 Expert Responses
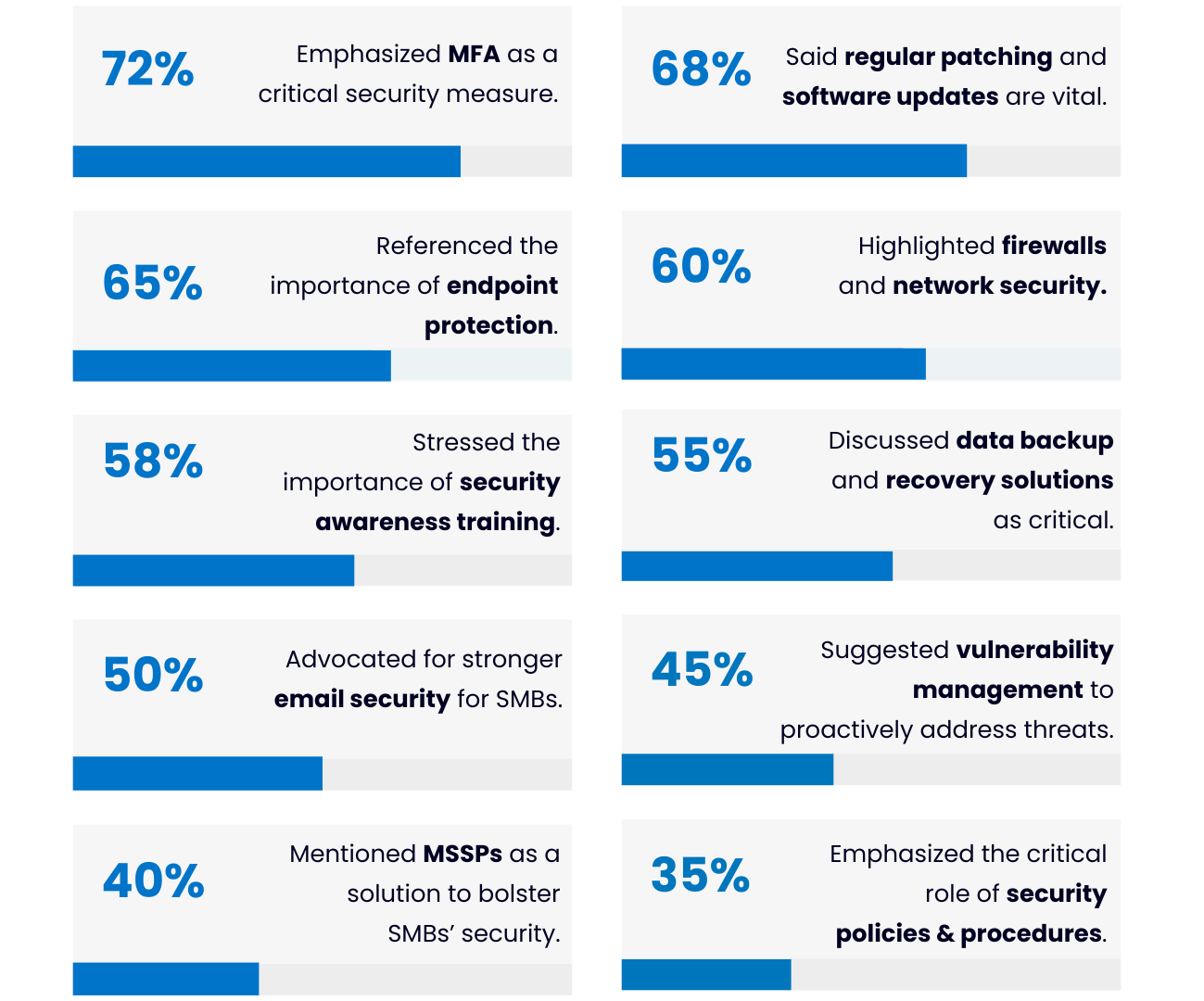
Here are the top 10 expert-approved cybersecurity measures for SMBs based on our analysis. The following cybersecurity measures emerged as the most frequently mentioned suggestions for small and medium businesses to improve their cybersecurity:
Cybersecurity Measure: % of answers mentioning it as critical for SMBs
- Multi-Factor Authentication (MFA): 72%
- Regular Patching and Software Updates: 68%
- Endpoint Protection (Antivirus, EDR): 65%
- Firewalls and Network Security: 60%
- Security Awareness Training: 58%
- Data Backup and Recovery Solutions: 55%
- Email Security: 50%
- Vulnerability Management: 45%
- Managed Security Services (MSSP, MDR): 40%
- Security Policies and Procedures: 35%
Practical implications and advice for SMBs based on these findings are discussed in the conclusion section.
Top 10 SMB Cybersecurity Measures
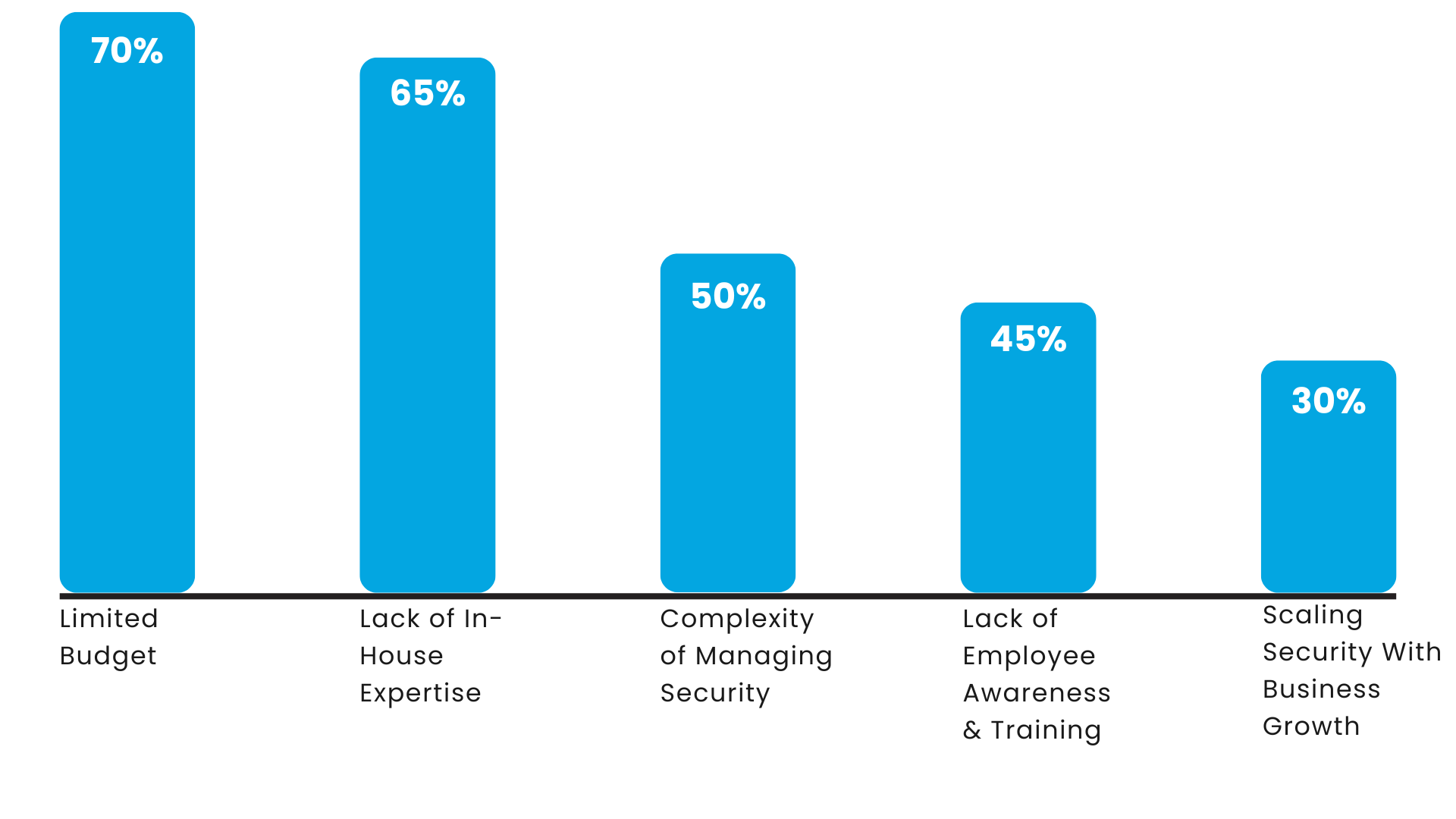
Common Obstacles With SMB Cybersecurity
Many security experts work with a variety of organizations and obtain insights into the specific problems they face based on factors like organization size. The following obstacles that SMBs encounter most frequently when trying to improve security should be kept in mind when implementing and improving security:
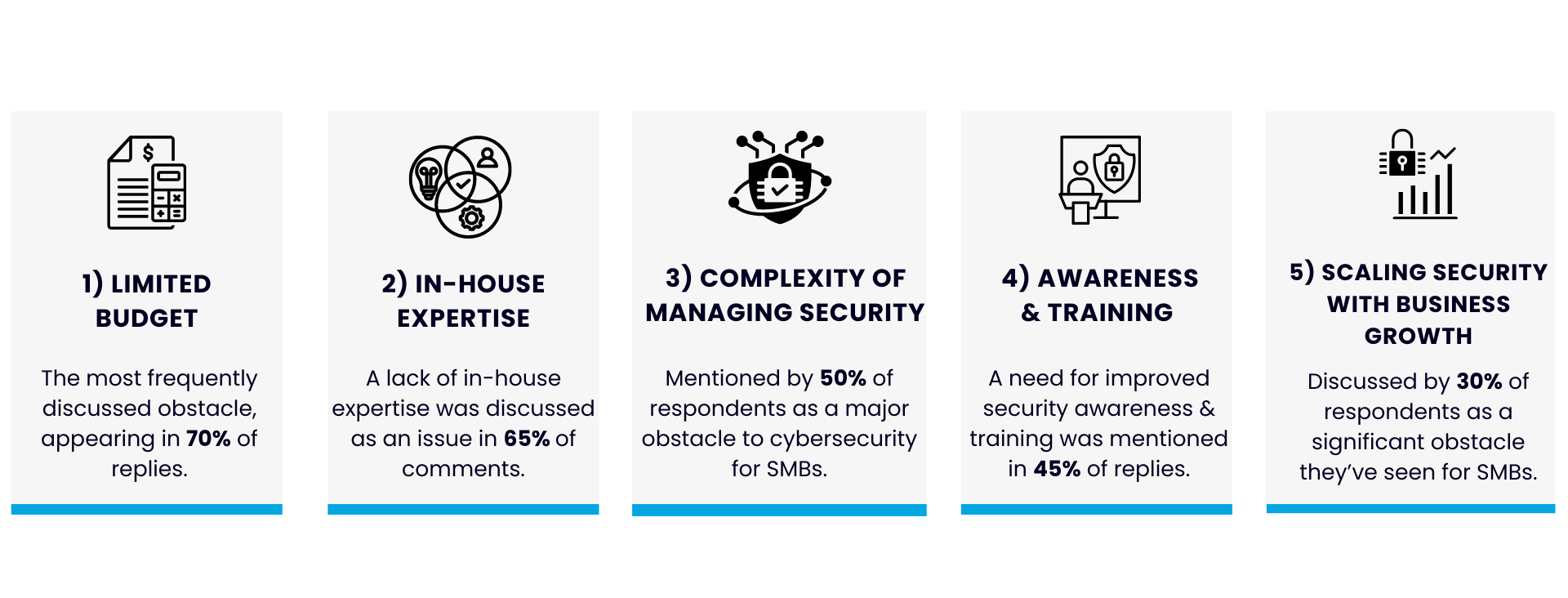
Obstacle Faced by SMBs: % of responses mentioning it
- Limited Budget: 70%
- Lack of In-House IT Expertise: 65%
- Complexity of Managing Security Solutions: 50%
- Awareness and Training Deficiencies: 45%
- Scaling Security with Business Growth: 30%
When building out your security program, it’s critical to keep these considerations in mind. For example, when drafting security policies for small businesses, there’s often a balancing act between security and budget that requires security measures to be tailored to the organization’s capacities. Unsurprisingly, budget was the most frequently discussed obstacle:
Top 5 Obstacles For SMBs With Cybersecurity
Thematic Analysis: Categorizing Obstacles & Practical Implications
Thematic analysis is used to find common themes and ideas by analyzing how people are discussing a particular topic. The analysis groups similar themes and patterns together to understand what people think and to provide a clear picture of the main points.
The thematic analysis for our research revealed several consistent patterns and recurring topics of discussion across the forum:
Resource Constraints
Limited financial and human resources hinder many SMBs. This impacts their ability to employ security measures, especially more advanced measures that companies handling specific types of data may need.
Rhymetec’s Take: There are a range of security measures SMBs can adopt that are both low-cost and effective. For example, enforcing strong password policies for all employees and using MFA are great ways to enhance security without breaking the bank.
Dependence on External Support
The analysis revealed a substantial reliance on external vendors (such as MSSPs) due to gaps in in-house capacity. Outsourcing security was often discussed as a necessary strategy to make up for limited internal resources, especially for more complex security measures.
Rhymetec’s Take: Given that many SMBs choose to outsource their security, they should be sure to have a rigorous process for carefully evaluating vendors according to their specific needs. Not all MSSPs are created equally. Many provide surface-level security measures or serve in a purely advisory capacity.
Depending on the type of data organizations handle, as well as security regulations in their industry, more support may or may not be needed. MSSPs that offer solutions like a vCISO service are equipped to provide substantially more hands-on support.
Awareness and Education
There was a continuous emphasis on the importance of security training to help mitigate human error and increase awareness of security risks. The importance of measures like phishing training for employees emerged as a recurring theme.
Rhymetec’s Take: Security awareness training plays a critical role for small and medium businesses in preventing phishing and social engineering attacks. Training programs should include simulated phishing attacks, educating staff on the latest and most relevant security threats, and teaching safe online practices.
Regulatory Compliance
Many SMBs are driven by compliance requirements to improve their security. This fact emerged as a common theme throughout analyzed forums. Compliance with industry regulations such as GDPR, HIPAA, or PCI DSS was mentioned many times as the motivating factor to implement security measures. The language and controls under their selected framework(s), therefore, end up guiding their security policies.
Rhymetec’s Take: It is clear from the analysis that for many SMBs, the need to meet compliance ends up driving security instead of the other way around. This is understandable, as SMBs often lack the same in-house resources as larger companies.
Traditionally, compliance is thought of as a “pass or fail” measurement of controls against a standard, whereas security is the management of risk through implementing controls and is measured through control maturity and effective risk mitigation. However, depending on how you choose to approach compliance (for example, the criteria you select under SOC 2), it can lean more toward security.
Needing to achieve compliance can serve as a gateway to truly robust security for many organizations. At the very least, it provides a solid baseline of security to build on.
It’s also important to note that implementing even baseline security measures under many regulations (such as MFA, backups, and asset monitoring) vastly improves security if these measures were not previously implemented!
Practical and Cost-Effective Solutions
Discussions often revolved around seeking practical, easy-to-implement solutions that offer substantial security benefits without overly excessive costs. There was a focus on basic yet effective measures such as MFA, firewalls, regular patching, and data backups.
Rhymetec’s Take: Resoundingly, MFA was the most frequently mentioned critical cybersecurity measure for SMBs. This aligns with prior security research from Verizon emphasizing the role of the human element in cybersecurity: MFA is the number one way organizations can protect themselves from cyber-attacks. If an organization does not enforce clear MFA policies for all employees, all it takes for a breach to occur is one employee having a weak password that gets identified through password spraying or traditional leaks.
Overall, these results highlight the importance of strategic investments in security measures that are effective and feasible within the constraints that smaller businesses often have.
SMB cybersecurity programs should prioritize foundational solutions that offer the highest ROI, scale with business growth, and strike a balance between effective security and realistic constraints.
Method: Analysis of Online Forums In Cybersecurity
Data were collected through a systematic search of online cybersecurity forums, using search terms including: “cybersecurity for SMBs” and “small business cybersecurity”. The following selection criteria were used to choose discussions for analysis:
- Posted in the last 5 years
- Contain at least 3 comments
- Relevant to the research questions
We identified 20 discussions in alignment with the selection criteria, totaling 327 data points (the posts and replies). Discussions included posts asking the following questions to obtain advice from cybersecurity professionals: “Cybersecurity for small-medium businesses?”, “Advice for a small business looking to tighten security?” and “Improving security posture as a small business.” Each post had an average of 15 comments responding to the question.
Thematic Analysis & Descriptive Statistics
A thematic analysis was conducted following a structured coding process to extract and interpret the data systematically. The raw data were organized into meaningful categories to enable identification of themes and patterns. Initial codes were generated by assigning codes to sections of threads that summarize what was being discussed in the body of the post and subsequent comments.
Codes were refined and merged to better match emerging themes. For example, codes such as “budget constraints” and “financial limitations” were merged into a single code based on their similarity. The textual data were broken down into meaningful parts, each tagged with a code encapsulating the key idea of that part of the text. For example:
- “Phishing risks”: Assigned to mentions of phishing as a significant threat and discussions on measures to counter it.
- “Dependence on MSSPs”: Tagged when reliance on managed security service providers for the cybersecurity needs of SMBs was expressed.
- “Compliance driven”: Used for discussions where regulatory compliance (like GDPR or HIPAA) was a primary motivator for adopting cybersecurity measures.
Next, a descriptive statistical analysis was conducted to quantify the frequency and prevalence of certain terms, concepts, and themes within the dataset.
In Conclusion: Balancing Cost, Complexity, and Effectiveness of SMB Cybersecurity
SMB cybersecurity needs to be manageable and sustainable. It’s important to craft a strategy from the beginning that balances realistic constraints with the need for security.
Again, here are the most common obstacles small and midsized businesses encounter with cybersecurity, as revealed by our research:
The 6 pieces of advice below strike a balance between these realistic constraints while prioritizing security measures that are effective and yield the highest ROI.
The major takeaways from this research include the following advice for SMBs:
1. Prioritize Cost-Effective Security Measures
Focus on controls such as MFA, enabling backups, and regular patching that are relatively low-cost and high-reward in terms of security benefits.
2. If Possible, Get The Basics Right From The Beginning
Have a subject matter expert draft your security policies. It’s important to bake security in from the very beginning (or as soon as possible) so your security program can grow seamlessly with your business.
It’s much harder to go back later and expand upon your security program and policies when your business has grown substantially and has more assets.
3. Conduct A Cost-Benefit Analysis
Evaluate the financial implications of cybersecurity investments against the potential costs of data breaches, considering both direct and indirect costs like reputational damage and legal fees.
4. Invest In Employee Training And Awareness
Foster a culture where security is everyone’s responsibility. Encourage employees to report suspicious activities without fear of repercussions and conduct ongoing security awareness training.
5. Plan For Compliance And Regular Audits
Understand your regulatory requirements and stay informed about any regulations that may impact your industry (such as GDPR and HIPAA). The legal and regulatory compliance requirements relevant to your organization change.
Managed compliance services can help you stay ahead of this and continuously ensure you are meeting all relevant requirements. Conducting regular security assessments can also help identify gaps in security and improve weak areas before they can be exploited.
6. Embed Cybersecurity Into Business Strategy
This last piece of advice is critical for company leadership.
Leadership should ensure that cybersecurity is a top priority from the highest levels of the organization. Additionally, it’s good practice to align business goals with cybersecurity. If security considerations are baked into overall business goals and strategies, it helps foster an environment that continuously seeks to prioritize and improve security as risks to your organization change.
Hopefully, this research report helped provide evidence-based recommendations that are both practical and effective for SMBs. In summary, here are the 6 expert-approved ways for SMBs to balance effective security with budgetary and personnel constraints:
6 Evidence-Based Tips For Effective SMB Cybersecurity
How Rhymetec Provides Effective & Practical SMB Cybersecurity Solutions
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget.
We enable our clients to outsource the complexity of security and focus on what really matters – their business. If you are interested in our services or if you have questions about security, contact our team for more information.
Interested in reading more? Check out additional content on our blog.