You might be wondering – Why would a threat actor bother targeting a startup? Don’t they focus on larger companies?
In 2024, cybersecurity for startups is just as critical as it is for the world’s largest organizations. You may be surprised to learn that small businesses nowadays are actually more frequent targets of cyberattacks than larger companies.
According to Verizon’s 2023 Data Breach Investigations Report, there’s a very clear reason for this:
Regardless of organizational size, companies are increasingly adopting similar services and infrastructure. This means that the attack surface of small organizations – all of the points from which a threat actor can access a system – looks more similar than ever to that of large companies.
When it comes to the attack surface of small versus large businesses, “…by now there is so little difference based on organizational size that we were hard-pressed to make any distinctions whatsoever.” (Verizon, 2023).
While it’s great that many business-accelerating tools are now equally accessible to small organizations, this democratization of technology has a dark side:
Organizations, from startups to Fortune 500, have increasingly similar risk profiles but do not have the same resources to prevent and respond to attacks.
From a threat actor’s perspective, this makes smaller organizations ripe targets. In light of this, what can you do as a startup to improve your security, especially without breaking the bank?
This guide will discuss:
- Why is Cybersecurity for Startups Important?
- 5 Practical Things You Can Do Right Away
- Measures to Further Improve Your Security
- Balancing Security With Budget
- Frequently Asked Questions in 2024
- Accelerating Cybersecurity for Startups in 2024
Rhymetec was specifically founded with the mission to make cutting-edge security available to startups. We’ve worked with hundreds of companies to provide practical solutions that enable them to be as secure as possible while also balancing security with budget.
This guide will provide actionable solutions for cybersecurity for startups based on:
- Our experience working with hundreds of startups.
- Current trends in the industry in 2024.
Why is Cybersecurity for Startups Important?
Large companies have the resources to continuously sharpen their security measures and keep up with increasingly stringent compliance requirements. Meanwhile, smaller businesses without the same resources to devote to security are left behind.
Threat actors know this, and that’s why an employee at a company with less than 100 employees receives 350% more social engineering attacks in their email than an employee at a large company.
And the smaller the business, the harder the attack hits: For over half of small companies, all it takes is one data breach to go out of business within 6 months.
What does this mean?
Startups need to invest in cybersecurity as much as large companies do, ideally from the onset. Fortunately, nowadays, there are affordable solutions for startups to access cybersecurity services and expertise historically reserved for large companies:
Instead of building out expensive in-house security teams, many startups turn to Virtual CISO Services as an alternative. Additionally, there are measures any startup can take right away to improve security, which we’ll discuss in the section “5 Practical Things To Do Right Away”.
But first, let’s talk about the most common threats faced by startups in 2024. We’ll keep these in mind when suggesting security measures you should consider.
Common Threats Faced by Startups in 2024
According to Verizon, 92% of tactics threat actors use against small businesses are either:
- Social engineering tactics, such as phishing emails.
- Basic web application attacks.
User credentials (like passwords) are the most frequently compromised type of data. This is because threat actors know this type of data is particularly vulnerable when hosted and processed by small organizations without strong security.
Even if you aren’t at the stage where you want to explore building out a comprehensive security program, there are a few things you can do in the short term.
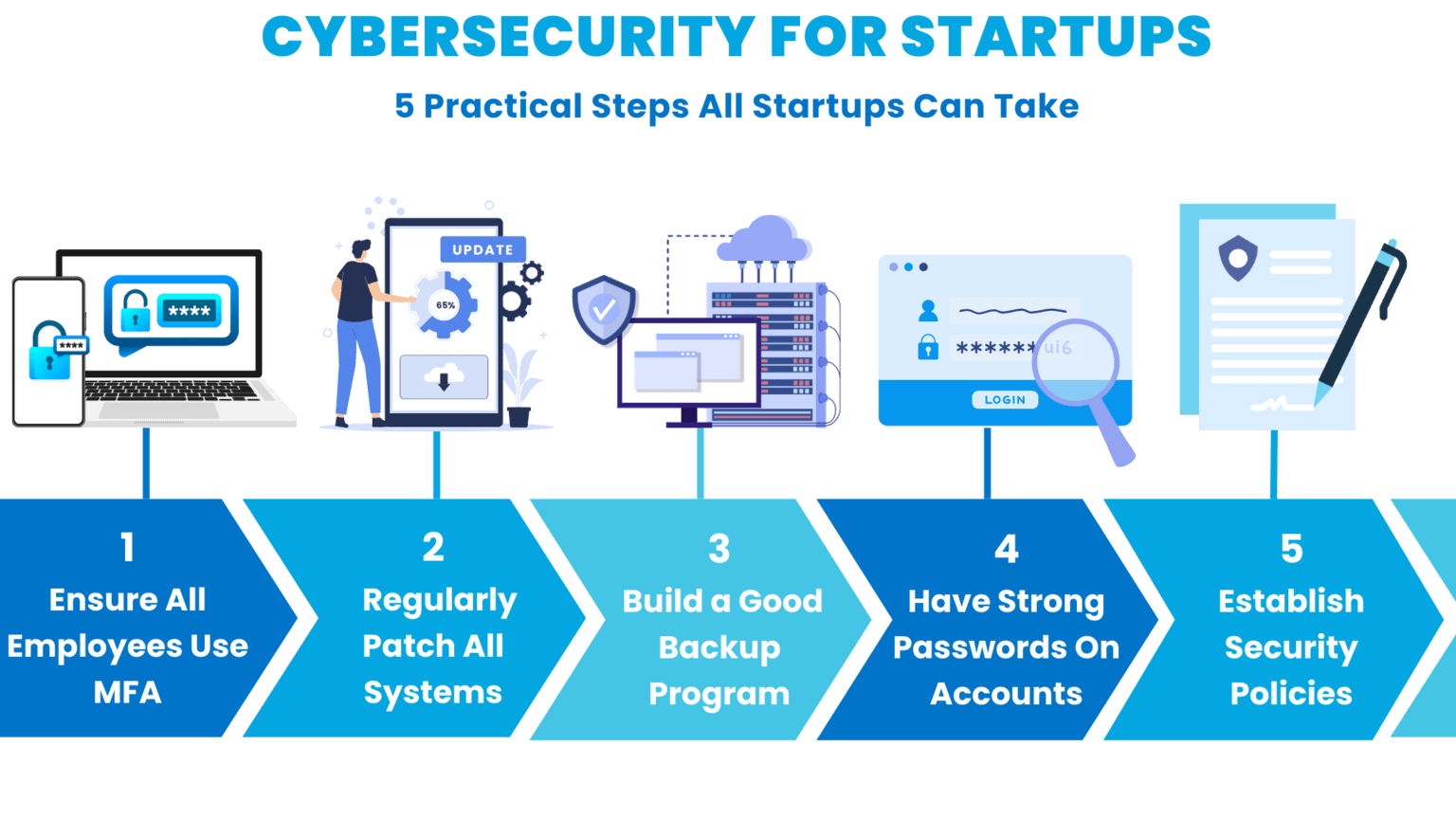
With the most common threats faced by startups in mind, here are 5 solutions that will mitigate a huge amount of risk right off the bat:
Cybersecurity for Startups: 5 Practical Things To Do Right Away
We get how much running a startup involves on a daily basis.
Even if you’re crunched for time and resources, fortunately, there are a few ‘quick win’ measures you can take to improve your security immediately!
Some of these may seem basic. But you would be stunned how many people, even in high-level positions, are using passwords like “032564Oreo (user’s birthday + their cat’s name), or “newpassword2024!” (self-explanatory).
It’s best to play it safe and operate from the assumption that most people simply don’t practice good security hygiene. It’s on company leadership to provide guidance and policies.
With this in mind, here are 5 measures you can take right away:
1. Ensure All Employees Use MFA At Your Startup
Multi-factor authentication (MFA) is critical to an effective security program.
Implementing MFA across all accounts, including cloud access, network access, and even SaaS access accounts, is the number one thing you can do to reduce the risk of a major incident or breach.
Without MFA, all a major breach takes is a single employee setting a weak password, which a threat actor then identifies through password spraying or traditional leaks.
Beyond simply setting up and requiring MFA, there are additional steps you should take in light of the current threat landscape in 2024. Unfortunately, threat actors have inventive ways around MFA nowadays.
To mitigate this risk, here are some important tips when setting up MFA controls:
- Understand where your customer data lives. Individual teams and employees may purchase new SaaS applications on their own authority and begin storing customer and other data in these systems. Without adequate controls and visibility, employees may be storing customer data in SaaS solutions without MFA that your IT and security teams are unaware of.
- Set short time-to-live (TLL) on session cookies where possible. Session cookies allow a user to reauthenticate without having to reenter a code for a set duration of time. If session cookies are stolen in the meantime, they can be used in a session replay attack to bypass codes. Setting time-to-live for cookies as shortly as possible does inconvenience users, but reduces the risk that if a threat actor steals cookies, they can be effectively used.
- When implementing MFA, it is strongly recommended to use authenticator applications rather than SMS-based authentication when possible. SMS-based authentication is susceptible through a practice known as “SIM Swapping,” in which threat actors either social engineer or steal the means to swap SIM devices at the carrier level, allowing them to hijack a user’s cellphone traffic.
2. Make Sure All Systems Are Patched
Many cyberattacks happen as a result of organizations not building a successful vulnerability management practice. Threat actors continuously scan for publicly facing IT assets with known vulnerabilities to identify potential targets to exploit.
A great example of this is the WannaCry ransomware attack in 2017. The exploit used by threat actors had actually been patched in Windows two months prior to the attack. Devices up-to-date on the latest security updates were not impacted by the attack. Meanwhile, devices that hadn’t kept up with the latest patches were left vulnerable.
Vulnerability prioritization can be a pain. It isn’t always clear when a vulnerability is critical versus when it can be delayed somewhat. Additionally, patches can be extremely disruptive to existing IT infrastructure. All of this makes effectively patching systems quite difficult. Here are a few tips:
- Prioritize vulnerabilities on publicly facing systems first: Threat actors regularly scan the internet looking for known exploitable vulnerabilities on publicly facing systems. An instance of this in 2024 includes the ConnectWise ScreenConnect vulnerability. Another recent example includes the MOVEit vulnerability.
- Prioritize actively exploited vulnerabilities: Not all vulnerabilities are equally high-risk. Vulnerabilities that are theoretical or haven’t been known to be “actively exploited in the wild” are likely lower risk and can be deprioritized compared to those that threat actors are utilizing.
- Use a vulnerability management service like Shodan: Shodan can help identify publicly facing IT assets along with services running on them. This can dramatically expedite mapping your organization’s attack surface and identifying services that may have exploitable vulnerabilities.
3. Build A Cybersecurity Program With an Extensive Backup and Recovery Program
It’s no secret that ransomware groups often encrypt sensitive data belonging to organizations. But ransomware isn’t the only reason you should have a strong backup and recovery program.
Natural disasters, unexpected outages, and threat actors can all compromise the confidentiality, integrity, and availability of data. This creates enormous risk.
Create not just a backup system for your startup, but a backup and recovery program that includes technology (either localized or cloud backups), processes (policies and procedures), and people responsible for ensuring it all works together.
Once you have a system that works, test it!
Tabletop exercises can be invaluable in testing real-world examples to make sure that your system works, everyone knows their role, and you can effectively respond to a crisis.
Bonus Tip: Be sure to back up your “less” critical systems.
Don’t underestimate the dependencies between data and software applications. Even if your organization has multiple systems, don’t isolate backup and recovery to “only” the most critical. It is often easy to overlook data dependencies between systems where one system going down can render another entirely nonfunctional.
4. Ensure All Employees Have A Strong Password
Many organizations make the mistake of believing that if they have strong two-factor authentication, they are adequately protected and don’t need to worry too much about weak passwords. This couldn’t be further from the truth.
If you have a weak, easily guessable password and two-factor authentication, you only really have single-factor authentication!
IBM’s recent X-Force Report showed that identity-based attacks that involve leveraging valid user accounts are now the predominant way threat actors compromise environments. Compromising a single valid user account with administrative privileges can quickly escalate into a full-blown breach.
Multi-factor authentication means your organization has strong passwords and monitors password reuse. Here are a few tips to ensure employees are using good passwords:
- Create strong passwords with a length requirement, special characters, numbers, and letters.
- Use a credential monitoring service like haveibeenpwned to identify if a user’s credentials have been compromised in a data breach. Rotate credentials immediately if this has happened.
- Talk extensively about password hygiene during regular security trainings. Emphasize not to reuse passwords across services. Walk users through how reusing passwords can result in the organization being compromised.
Bonus Tip: Use a password manager like 1Password.
Tools like 1Password automatically create strong passwords, which are then encrypted and stored so that only authorized users can access them.
This allows members of your team to share passwords without showing the actual password. Additionally, employees can access business-critical accounts across multiple devices without having to remember complex passwords.
If your startup has a remote workforce and employees are logging into their work accounts on multiple devices, a password manager is a must-have.
5. Establish A Written Security Policy
Establishing a written security policy is one of the most critical things you can do to create a strong cybersecurity baseline for your startup.
Rhymetec’s Senior Cybersecurity Analyst, Kyle Jones, recently spoke about how to draft and communicate strong security policies. Here are a few tips he suggested:
- Know your audience. If the people who need to understand and adhere to your security policies aren’t security knowledgeable, keep that in mind. Don’t use overly technical language in your policies. Instead, tailor your language to your audience.
- Emphasize your policies continuously, and connect policies with the reasons behind them. People will be more likely to follow policies if the reason behind them is explained. Find opportunities, such as when an employee has an IT-related question, to reference the policies and see what they say.
- Make sure your policies reflect current trends. Your risk profile changes depending on what’s going on in the world! For instance, the launching of large language models (LLMs) like Google’s Gemini should make you rethink your policies.
Here are several critical questions about AI:
- Do you know if your employees are sharing data with any LLMs they may be using for work?
- Do you have an established policy around the use of this technology at your startup?
- What about updates to regulatory language around AI? Do your policies take that into account?
A great example of why these questions need to be visited can be seen in Samsung’s 2023 data leak with Chat GPT – the company has since banned the internal use of generative AI tools.
Bonus Tip: Create a culture that prioritizes security and transparency.
Share resources and talk to your team regularly about the importance of security.
Don’t fearmonger – you never want your employees to feel like they can’t come to you if something happens. Make it clear that your door is open, and you want to know if they receive a suspicious email or if they notice unfamiliar software on their work device.
Cybersecurity for Startups: Measures To Further Improve
So, you’ve made sure your employees are using MFA and that nobody’s password is their cat’s name. You regularly update all of your systems, back up your data, and already have security policies in place.
Here are the next steps you should take:
1. Build A Formal Process to Assess The Security of Third-Party Vendors and Suppliers
Third-party risk management continues to grow in importance for organizations of all sizes.
We recommend building a full inventory of all third-party suppliers your organization uses and implementing a standard risk screening. Fortunately, modern standards make it easy to quickly screen to see if a potential third party takes information security seriously.
We recommend asking questions like:
- Does your organization have a SOC 2 Type 2 Report, or other third-party attestation on your information security program?
- Are you compliant with the HIPAA Security Rule, New York Department of Financial Services Cybersecurity Rule, or other formal legal requirements?
- Does your organization have documented security policies?
- Do you share customer data with third parties? If so, which ones?
2. Conduct Routine Pen Testing Engagements
Engage a third party (such as Rhymetec) to regularly put your security controls to the test.
Regular pen testing identifies gaps that potential attackers could exploit. Pen tests should be scoped to the specific risks that your organization faces. For example, Rhymetec can help with:
- Web application pen testing to identify vulnerabilities and misconfigurations in web apps.
- Mobile application penetration testing to identify vulnerabilities or exploits in mobile apps that could be exploited.
- Network penetration testing to identify ways that your organization’s network could be exposed.
Pen testing is critical to meeting numerous security requirements. It also enables you to better answer questionnaires about your organization’s security provided by potential customers.
3. Conduct Simulated Spear-Phishing Tests
Simulated phishing exercises represent another very significant opportunity to improve your security.
Running realistic simulated phishing tests can help condition employees to be wary of even realistic-looking emails purporting to offer them gift cards and sensitive information. Make sure emails look realistic and are targeted. Sending generic emails generated by a platform can come across as too obvious and fail to adequately test users.
Take an attacker’s perspective – what might an attacker write without inside knowledge of users to get users to click links?
Bonus Tip: Have An Incident Response Plan In Place.
An incident response plan is a set of documented procedures to act on in the event of a security incident. For instance, do you know what steps to take in the event your startup experiences a ransomware attack?
To recall an earlier example, during the WannaCry ransomware attack in 2017, many victims paid the ransom to try to get their data back. Security professionals generally do not advise paying ransoms. The threat actors behind the WannaCry attack did not restore people’s data even after they’d paid the ransom.
Having a documented incident response plan equips you with important know-how in the event you are to experience an attack or a data breach. This saves time, money, and headaches if an incident were to occur.
Balancing Security With Budget
Building good organizational security is critical. However the cost of protecting an asset shouldn’t have to exceed the value of the asset.
Cybersecurity for startups needs to be balanced against ease of access, business processes, and the risks associated with the service, data, or application being secured.
At Rhymetec, we work with a lot of SaaS startups who need to build a security program typically because their customers require it and it’s difficult to compete in the marketplace without one. These startups are working off a limited budget.
A good place to start to figure out how to balance security with budget is to think about the answers to the following two questions:
- What does your risk profile look like? Narrowing down the specific risks facing your organization helps prioritize where you need to spend your security dollars. For example, if you are located somewhere that’s prone to earthquakes and your servers are stored there, that’s a high risk. You would want to prioritize taking steps to remediate this.
- What’s your risk appetite? Understand what your own risk tolerance is – If you have a low-risk appetite, you will want to commit to remediating any medium or high risks. Or, at the very least, look at how to reduce your risk from high to low in the areas of highest risk.
At Rhymetec, after we assess your risk profile and answer these questions, we get creative on the best way to proceed with building your information security program while keeping in mind budget constraints.
Frequently Asked Questions (FAQ) for Cybersecurity for Startups in 2024
Here are 5 questions we see frequently from startups in 2024. Knowing the answers to these questions – and implementing corresponding policies – is essential for robust cybersecurity for startups.
1. What are some commonly required or requested compliance frameworks for startups in 2024?
- SOC 2 is a voluntary standard often requested by customers to show you take security seriously and that their data will be in good hands if they share it with you.
- ISO 27001 is the leading international standard for information security.
- PCI DISS is necessary if your startup processes credit card payments.
- GDPR is required in 2024 if you handle the personal data of EU citizens.
- HIPAA privacy regulations require organizations dealing with healthcare data to follow procedures around the confidentiality and security of PHI (Protected Health Information).
2. How does the increasing shift to remote work impact cybersecurity for startups in 2024?
Cloud security is critical in the age of remote work.
Without proper controls, even daily activities like file sharing can result in sensitive information being shared with unauthorized users. Following best practices for cloud storage is essential in 2024, including:
- Make sure your employees have a strong separation between work and personal documents and devices.
- Invest in backing up your data to prevent the loss of important information and documents.
3. What should startups do from a security standpoint with all the AI hype?
AI amplifies existing threats, especially social engineering attacks. For example, AI can be used by threat actors to generate a larger number of personalized phishing emails.
This simply means that the best way to protect your business from AI-assisted threats is to strengthen your core security program. Staff awareness training to protect against social engineering attacks is especially important.
4. What are some best-of-breed tools startups can easily utilize in 2024?
As discussed earlier, the attack surface of small organizations is starting to increasingly resemble that of large organizations. What if you could monitor this, even down to the individual employee level?
Services like Picnic enable you to minimize the human attack surface of your startup and protect executives, contractors, and employees from social engineering attacks.
Nowadays, fortunately, there are tools that make security more accessible. Even if you have zero technical background, you can seamlessly integrate tools like Zip Security that provide enterprise-grade security and endpoint threat detection.
5. When is the right time to start looking into cybersecurity for startups?
The straightforward answer here is that if you’re reading this, the right time is now.
Don’t wait for the perfect time. The reality is that early-stage startups are unfortunately particularly vulnerable to cyberattacks, precisely because threat actors know they often lack even basic security practices.
Plus, it’s always better to start building your security program early on so it can grow in alignment with your needs as your startup scales. Implementing a robust information security program after growth involves even more time, money, and resources to catch up.
How MSSPs Can Accelerate Cybersecurity for Startups in 2024
Hiring an external security team can substantially help organizations, especially in the early stages.
Virtual CISOs at organizations like Rhymetec have extensive experience balancing budgetary needs, usability, and security for start-up cybersecurity programs. It’s not an easy balance, but leveraging an experienced partner can deliver huge amounts of specialized talent without the need to spend millions of dollars on an in-house security team.
Managed Security Services Providers like Rhymetec have dozens of professionals across security disciplines like cloud security, compliance, web application security, penetration testing, and others. They have the experience putting these skills to work for startups in a way that drives real security outcomes as you scale while also keeping your budget in mind.
To learn more about how our team can accelerate your security while keeping your budget in mind, contact us for more information.
About The Author: Metin Kortak, CISO
Metin Kortak is the Chief Information Security Officer at Rhymetec. Metin began his career working in IT security and gained extensive knowledge of compliance and data privacy frameworks such as SOC, ISO 27001, PCI, FedRAMP, NIST 800-53, GDPR, CCPA, HITRUST and HIPAA. He joined Rhymetec to build data privacy and compliance as a service offering. Under Metin’s leadership, these offerings have grown to more than 200 customers, positioning the company as a leading SaaS security service provider in the industry.