Regular cybersecurity audits are the best way to ensure your business continuously meets security and compliance requirements while reaping the business benefits of investing in security. This post will go over the different types of audits, their benefits for your organization, how to prepare, and common findings to be aware of.
For many fast-growing startups and SMBs, cybersecurity might not feel like a top priority. But with increasingly complex data regulations, rising threats, and growing client expectations, security can no longer be an afterthought, regardless of company size or industry.
The good news is that organizations that invest in improving their security posture and undergo regular cybersecurity audits start to see a wide range of benefits, especially once they have evidence they've successfully completed their audit through a certification or a report:
Barriers are removed in their deal flows, the time spent on filling out onerous security questionnaires is eliminated, and they can get back to what really matters - moving their business forward.
Why Cybersecurity Audits Matter For Your Organization
A cybersecurity audit is a thorough review of an organization's security posture, assessing the adequacy of protections in place to defend against cyber threats and meet regulatory requirements. You can think of an audit as a health check for your security practices, allowing you to identify potential vulnerabilities before they can lead to an actual security incident.
Audit findings provide valuable insight into how secure your organization is and how well you are meeting any relevant requirements. Knowing how well your security practices measure up against industry standards allows you to pinpoint where improvements need to be made, and make only the changes you actually need.
Cybersecurity audits identify vulnerabilities and show where your security measures align with or diverge from relevant frameworks like ISO 27001, SOC 2, and HIPAA. After an audit, as you enact necessary changes to address the audit's findings, you'll reduce the risk of regulatory penalties, reputational damage, and security incidents. Decision-makers can use the results of an audit to prioritize security improvements and guide their compliance efforts.
When clients, investors, regulators, or other stakeholders expect evidence of your security controls, having third-party verification of the strength of your security posture is important. It shows that you've addressed security requirements upfront, creates confidence in your security approach, and helps meet stakeholder expectations.
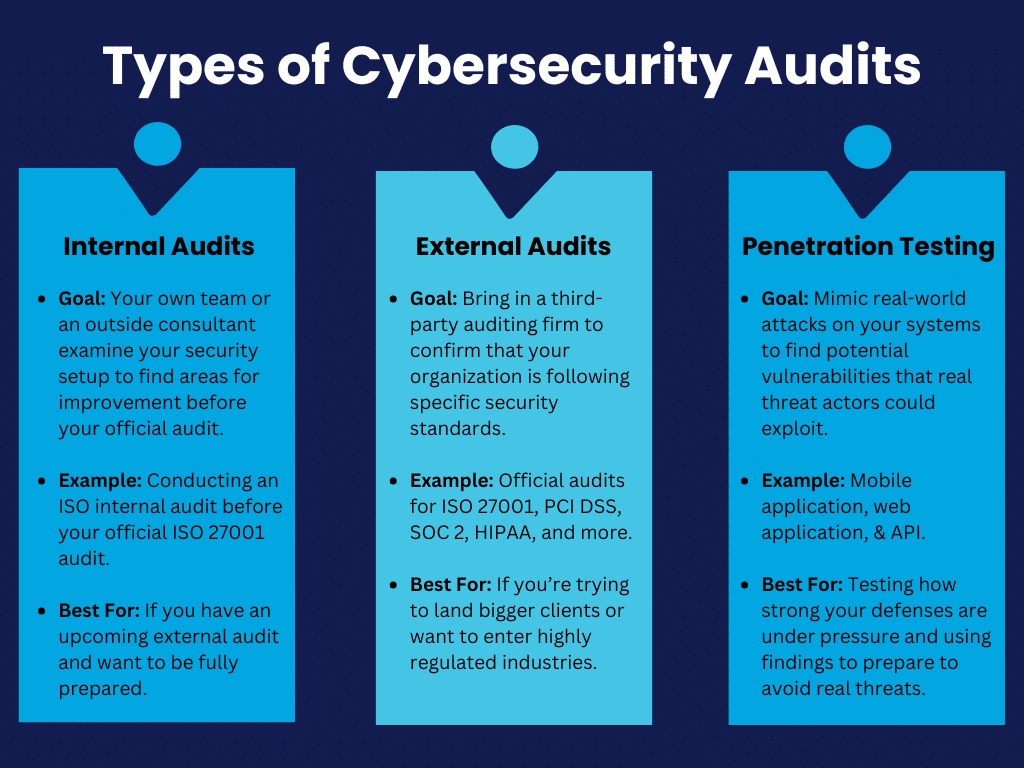
Types of Cybersecurity Audits Every Startup Should Be Aware Of
Startups should know about a few different types of cybersecurity audits:
Internal audits are when your own team or an outside consultant examines your security setup. The goal is to conduct a gap assessment and find any areas for improvement to help better prepare you for future external audits. For example, an ISO internal audit provides a way to spot weaknesses early and adjust them before your official audit for frameworks like ISO 27001 and ISO 42001.
External audits bring in a third-party auditing firm to confirm that your organization is following specific security standards such as ISO 27001, PCI DSS, SOC 2, HIPAA, and more. Passing an external audit is vital if you're trying to land bigger clients or want to enter highly regulated industries.
Penetration testing mimics real-world attacks on your systems to find potential vulnerabilities. Penetration tests give you an idea of how strong your defenses really are under pressure, and the findings help prepare you to avoid real threats:
How to Prepare For a Cybersecurity Audit
To prepare for an audit, the first step is to take a close look at your existing policies and procedures: Are they actually being followed?
It's common for companies to write policies that look great on paper but fall short in practice. You'll want to make sure everyone on your team knows their roles, especially around access controls, data handling, and your organization's incident response policies.
Don't neglect the tech side. Run vulnerability scans, review your logging and monitoring, and make sure your backups are up to date. Auditors will likely examine these areas regardless of which type of audit you undergo. Lastly, keep your documentation extremely organized. Auditors appreciate easily accessible and well-organized documentation. Having it ready can be the difference between a smooth audit and a chaotic scramble.
Bonus Tip: A compliance automation tool can come in extremely handy at this stage, as it allows a single place to upload and keep track of all of your documentation. Your auditor will appreciate being able to easily access everything in one place!
Preparing ahead of time as much as possible puts you in control of the process rather than reacting to questions or findings that may come up. Providers like Rhymetec offer internal audits and gap assessment services that are conducted before your audit, leading to fewer surprises during your official audit.
Common Findings in Cybersecurity Audits (And How To Address Them)
Cybersecurity audits often reveal a few common recurring issues that many startups and SMBs face:
One of the most common findings across a variety of different types of audits is weak access controls. Cybersecurity audits frequently find gaps in access control requirements, meaning that too many people have unnecessary access to sensitive data or systems.
The fix here is straightforward:
- Review who has access to what.
- Limit permissions to those who need it.
- Implement multi-factor authentication to add a last additional layer of security to make it harder for unauthorized users to gain access.
Another issue that often comes up is missing or outdated documentation. Auditors will expect to see things like security policies, incident response plans, and training records. If you can't provide these documents or if they're outdated, that's a red flag.
To address this issue, you should:
- Create clear, up-to-date policies that reflect what's actually happening at your organization.
- Make documentation a regular part of your operations, so you're not scrambling to pull everything together before an audit.
- Consider using compliance automation software to organize all of your documentation for auditors in one place.
Another common area where audits also tend to find vulnerabilities is in systems that haven't been patched or updated.
Leaving old software as is is like leaving your door unlocked. You should be regularly updating and patching systems to close off potential entry points for attackers. Simply setting up automated reminders or systems to handle updates can be extremely helpful.
Third-party risk management is another area that is often overlooked by organizations and comes up in audit findings. For PCI DSS audits, for example, this is one of the most common challenges our experts at Rhymetec see that organizations encounter. For many frameworks, you need to make sure your third-party vendors are also compliant.
Finally, many audits reveal a lack of proper employee training. As noted by our experts in Rhymetec's Cybersecurity Awareness Month Tips, your people are often the first line of defense. If they're not aware of basic security practices or don't follow steps to adhere to them on a daily basis, it's a problem.
Ongoing security awareness training and phishing training for employees help everyone in your company recognize and avoid common vectors of attack like phishing attempts.
If possible, address these common issues ahead of time for a smoother audit process.
Cybersecurity Audits and Penetration Testing
Penetration testing is the best way to understand how well your defenses would stand up to real-world attacks.
While not every audit requires a pen test, it's often necessary for audits tied to specific compliance frameworks like PCI DSS and certain SOC 2 reports. These audits don't just ask if you've set up your security controls - they want tangible proof that your system can actually withstand an attack.
Penetration testing is recommended when you need more than a surface-level review of your security and need to go beyond checking boxes to meet compliance requirements; experts simulate actual cyberattacks to try to break through your defenses. Think of it as having someone attempt to lockpick your door, rather than just checking if your door is locked.
Note: If your organization is preparing for a major compliance audit, working with clients that demand high levels of security, or going through rapid growth, a penetration test is highly recommended!
If you incorporate penetration into your regular security checks, you'll get a clear picture of how well you're protected and will be able to tackle weaknesses before they become costly problems down the line. Getting a test done annually or after major changes to your systems helps you stay ahead of emerging threats.
Rhymetec offers a variety of penetration testing services, including:
Choosing The Right Partner for Your Audit
Not all auditors are created equal, so it's important to select a partner who's not only experienced but also a good fit for your company's size, structure, and industry. You need someone who understands both your industry and the specific compliance requirements you're facing.
Audit Partner Factors To Consider
First, check out their track record. Have they worked with startups or SMBs before? It's one thing to know the rules, but another to understand the unique challenges small to midsized companies and startups face regarding security and compliance.
Ask about their previous clients and whether they've helped similar businesses successfully meet their compliance goals. Request to see case studies from their prior engagements with companies with similar profiles as yours.
Another factor to consider is how hands-on you want your audit partner to be. Some partners take a more hands-on approach by choosing to work with select MSSPs to help you improve your security along the way, while others are more focused on just performing the audit and reporting findings.
Audit Report "Red Flags" To Look Out For
A thorough audit report gives you a roadmap for improving your security with clear steps, while a deficient one can leave you with more questions than answers.
Plus, 69% of organizations report that the quality of compliance reports is extremely important. Your clients and stakeholders will want to see evidence of a thorough, high-quality audit.
So, how do you tell the difference between a thorough audit report and a deficient one?
1. First, look at how the findings are communicated:
A high-quality audit report won't just tell you that there's an issue - it will explain where the problem is, why it matters, and how it could impact your business. Look for specifics, like which systems or processes failed, how attackers could exploit weaknesses, and what steps to take next. If your report is filled with vague statements or broad recommendations without context specific to your organization, that's a sign it's not as thorough as it should be.
2. A high-quality report will also show you how issues across different areas are connected:
If weak access controls, for example, show up in multiple places - whether in your cloud setup, employee accounts, or vendor portals - a good report will explain how these issues are linked. A deficient report might mention them individually without showing the bigger picture.
3. Findings on your documentation is another area where a thorough report stands out from a deficient one:
A high-quality report points out exactly where your policies or training records are lacking and provides actionable steps to fix them. If your report glosses over missing documentation or doesn't dig into whether your policies match actual practices, you're likely looking at a surface-level, boilerplate review rather than a meaningful and tailored audit.
4. Finally, a quality report doesn't simply list issues but will categorize them based on their severity and urgency:
This helps guide you on which areas to focus on first. A deficient report may give you a laundry list of issues but won't help you understand which ones pose the most immediate threat.
In short, a thorough audit report provides clarity, context, and a plan. A deficient one leaves you guessing and unsure of how to proceed and may not hold up under scrutiny from your customers and stakeholders.
How Working With An MSSP Simplifies Cybersecurity Audits
Partnering with a Managed Security Services Provider (MSSP) can take a lot of stress out of cybersecurity audits. An MSSP handles much of the ongoing work for you, so when it's time for your audit, you're not rushing to get everything in order.
With continuous monitoring, regular updates, and fully managed compliance services, an MSSP ensures that your security posture stays audit-ready all year round. For example, if your business needs to meet standards like PCI DSS or ISO 27001, an MSSP can keep your policies and security controls aligned with the latest requirements and make sure you're up-to-date on your recurring audits.
Working with an experienced MSSP is the best way to minimize the risk of non-compliance and saves your internal team from having to devote time to it themselves. When you work with an MSSP, you're essentially outsourcing the complex, technical aspects of security to a team that specializes in it, freeing up your business to focus on growth while staying secure and compliant.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.