Meeting NIS2 requirements can be complex regardless of organizational size, especially the requirements around managing third-party risks and incident response. In this article, we go over what NIS2 requires, how to avoid penalties, and how to leverage the requirements to support business growth and operations.
The NIS2 Directive represents another new requirement in an increasingly strict cybersecurity regulatory ecosystem. The law, which came into force in January of 2023, specifically impacts organizations operating in the European Union (EU). Businesses that provide essential or important services must meet the obligations or face regulatory scrutiny.
What Is NIS2?
NIS2 is the EU's updated cybersecurity Directive, expanding on the scope of the original NIS Directive to cover more sectors and introduce even stricter security, risk management, and reporting requirements. If your business provides services in the EU ranging from transportation, banking, healthcare, manufacturing, food production, and more, you are likely required to comply.
The Directive applies to industries including technology, finance, healthcare, energy, and transportation, as well as many digital service providers. Broadly, it requires organizations to implement risk management measures, report significant incidents within 24 hours, and effectively manage third-party risks.
Non-compliance can result in fines of up to €10 million or 2% of global annual turnover, whichever is higher. Compliance impacts not only your regulatory standing but also your contracts, customer trust, and business continuity. Building a compliance strategy early will help avoid last-minute disruptions and potential penalties.
Who Must Comply With NIS2 Requirements?
NIS2 applies to organizations classified as essential or important entities across a variety of sectors. The Directive expands largely on the scope of the original NIS Directive, covering a broader range of industries and lowering the threshold for organizations that must comply.
Essential entities include large organizations in critical sectors where cybersecurity failures could have widespread and serious impacts, such as:
- Energy - Electricity suppliers, gas providers, oil companies, and district heating operators.
- Transport - Airlines, rail operators, shipping companies, and logistics providers.
- Banking - Credit institutions and financial market infrastructure providers.
- Healthcare - Hospitals, clinics, and pharmaceutical manufacturers.
- Drinking Water & Wastewater - Water supply and treatment facilities.
- Digital Infrastructure - Cloud services providers, data center operators, and domain name system (DNS) service providers.
Important entities are medium and large businesses in sectors that are critical but do not require the same level of regulatory scrutiny. These include:
- Manufacturing - Producers of medical devices and electrical equipment.
- Food Production - Businesses that manufacture food and beverages.
- Postal and Courier Services.
- Waste Management Companies.
- Digital Service Providers - Online search engines, marketplaces, and social networking platforms.
- Managed Security Service Providers (MSSPs) - Businesses providing cybersecurity services to other organizations.
It's important to note that both essential and important entities are generally defined as medium or large enterprises, meaning they have at least 50 employees or an annual turnover of €10 million or more. Smaller organizations, however, may still fall under NIS2 if they are critical to a supply chain or if they operate in a high-risk sector.
NIS2 Requirements: What You Need To Plan For
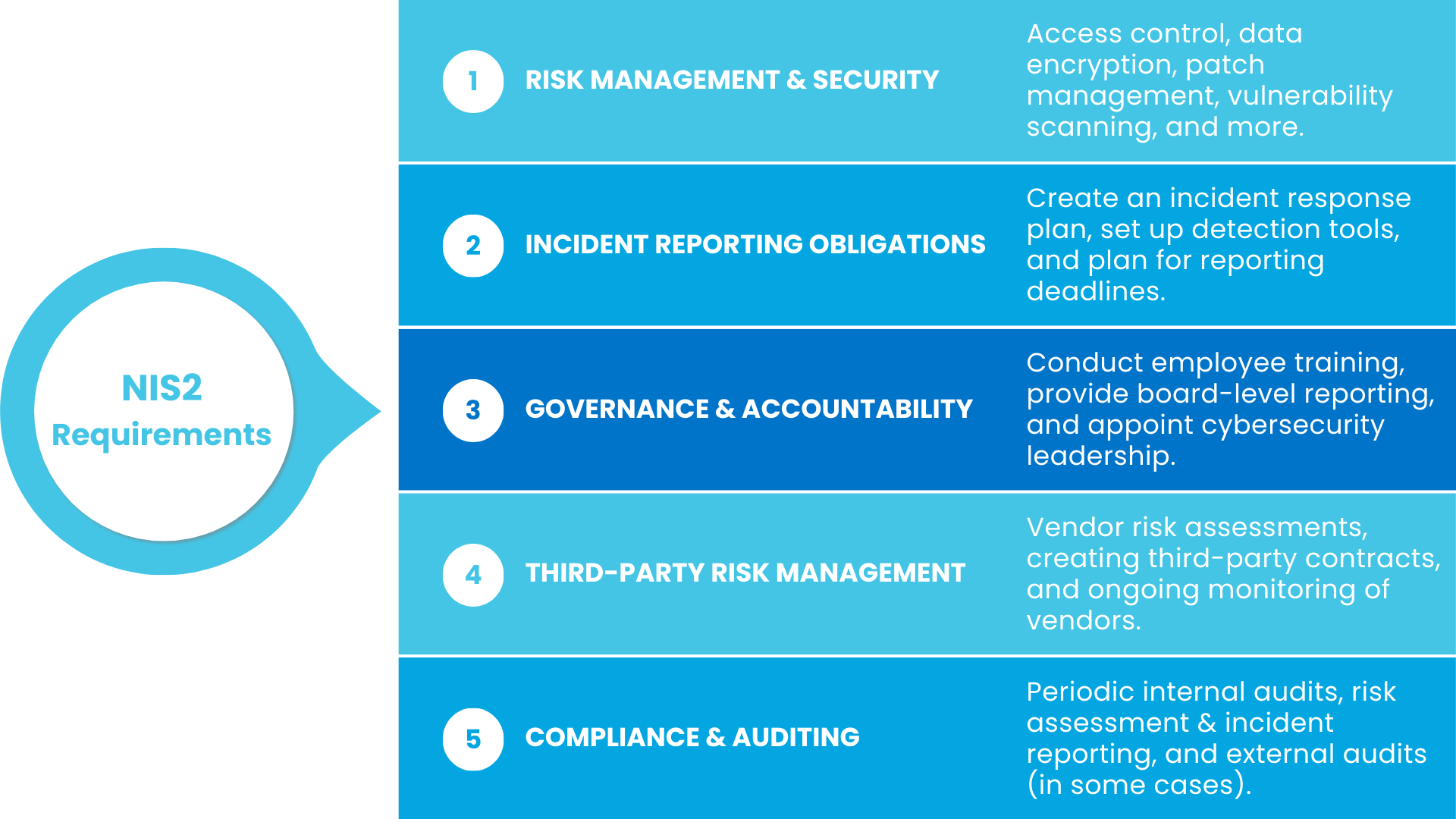
NIS2 entails a range of security and operational requirements, with a particular emphasis on minimizing cybersecurity risks. Below is an explanation of the 5 overarching requirements and what implementing them may look like for your organization.
1. Risk Management & Security Measures
NIS2 requires organizations to take a proactive approach to mitigate cybersecurity risks.
Security measures across areas, including network security, data protection, and system integrity, are required. Here's what this may look like in practice for your organization, particularly if you are a SaaS company:
- Implementing Access Control Measures: Access control measures such as multi-factor authentication (MFA) for all employees and users accessing your platform are required under NIS2. MFA means both a password and app-based token or another second form of verification are needed to log in.
- Enabling Data Encryption Measures: Encrypt sensitive customer data both at rest and in transit. For NIS2, this includes encrypting databases and using TLS (Transport Layer Security) for all data exchanged between clients and your platform.
- Creating A Patch Management Program: Regularly update software and systems to fix vulnerabilities. Additionally, you'll need to implement an automated patching system that ensures no critical updates are missed.
- Conducting Regular Vulnerability Scanning: This requirement entails using automated tools to regularly scan your applications and infrastructure for vulnerabilities. For instance, using tools like Nessus can identify weaknesses.
2. Incident Reporting Obligations
NIS2 mandates relatively quick reporting of cybersecurity incidents in the event they occur. As an example, if you were to experience a breach where an attacker gained access to customer data, you would be required to notify relevant authorities and affected clients within the prescribed timeframe and provide updates on the breach as it is resolved.
In practice, setting up the incident reporting process from beginning to end will likely entail the following for your organization:
- Creating An Incident Response Plan: Internal incident response policies that outline the exact steps to take when a breach occurs, designate a response team, and describe how you will identify the root causes of the breach are required.
- Setting Up Incident Detection Tools: Set up monitoring systems like SIEM (Security Information and Event Management) to detect unusual activity in real-time. Tools like Splunk or Datalog track suspicious logins or data exfiltration are commonly used for this purpose.
- Making A Plan To Follow Compliance with Reporting Deadlines: Lastly, know what your process would be for reporting incidents in a timely fashion to the appropriate authorities and your affected clients.
3. Governance & Accountability
An increasing emphasis on governance is being seen across historically gold standard cybersecurity frameworks such as the NIST Cybersecurity Framework (NIST CSF) with the addition of the NIST governance function. This shift is being seen in recent laws as well, including in the case of NIS2.
In practice, this means that cybersecurity should not be a function of just IT, but a function of corporate governance and should stem from there. Senior management is responsible for making sure that the organization meets NIS2's cybersecurity requirements and that sufficient resources are allocated. Leadership must:
- Appoint Cybersecurity Leadership: Appoint a Chief Information Security Officer (CISO) or designate a cybersecurity lead who will be accountable for ensuring the organization meets NIS2's requirements.
- Ensure Employee Training is Conducted: Employees, particularly those who handle sensitive data, need to be trained in cybersecurity practices and incident reporting procedures. This often takes the form of having mandatory, recurring cybersecurity awareness sessions, phishing training for employees, and/or tabletop exercises.
- Receive Board-Level Reporting: Senior management should regularly receive reports on cybersecurity risks and incidents, and be involved in decision-making processes related to cybersecurity investment. This can take the form of discussing the current cybersecurity posture and resource allocation at quarterly board meetings, for example.
4. Third-Party Risk Management
NIS2 puts the obligation on businesses to manage risks posed by their third-party vendors, especially if those vendors provide business-critical services or have access to sensitive data. A third-party risk management program entails the following elements:
- Vendor Risk Assessments: A vendor risk assessment evaluates the security and compliance practices of third-party providers. This is especially important for vendors that provide services such as cloud hosting, payment processing, or customer support. These vendors and others need to be able to show they meet NIS2's security standards.
- Third-Party Contracts: Contracts with vendors need to define their security obligations (requiring them to comply with certain security standards, report incidents within specific timeframes, and/or undergo audits of their security practices). Your contract for your cloud provider, for example, should outline measures they need to have in place, such as strong access controls and encryption.
- Ongoing Monitoring: Continuously monitoring your vendors. For instance, regularly review their security certifications, check they are staying compliant with relevant laws or frameworks, or conduct periodic assessments.
5. Compliance & Auditing
NIS2 requires maintaining evidence of your cybersecurity practices, with measures such as:
- Internal Audits: Periodic internal audits of security practices to ensure compliance maintenance with NIS2. Internal audits service to verify that measures like encryption and access control are functioning as intended.
- Risk Assessment & Incident Reports Documentation: Keeping up-to-date records of risk assessments, incident reports, and audits helps meet NIS2's governance and accountability requirements.
- External Audits: In some cases, if an organization falls within the essential or important entity categories and is subject to supervisory measures by national authorities, it may be required to undergo an external audit. Some jurisdictions may also require routine external audits for critical infrastructure or high-risk organizations.
NIS2 Requirements: 5 High-Level Requirements
Meeting NIS2's requirements will involve a combination of technical measures, governance practices, and ongoing actions such as continuous monitoring. For organizations like SaaS startups, implementing these requirements ensures you are in compliance with the law and are well-equipped to build a secure platform that protects user data and reduces business risks.
How NIS2 Affects Third-Party Relationships
NIS2 expands security obligations to include third-party vendors and service providers, requiring businesses to manage risks introduced by their supply chain. Practically, this means you must verify that your vendors (including cloud services providers and software vendors) meet security standards and comply with contractual requirements.
With NIS2, due diligence with your vendors' cybersecurity practices is especially important as organizations covered by NIS2 are responsible for security incidents linked to their third parties.
A common way to verify your vendors' security is by requesting to see evidence of their compliance with cybersecurity frameworks and laws relevant to your industry and location. Security questionnaires, audits, and contractual clauses can also be used to clarify your vendors' security practices. However you choose to accomplish this, third-party relationships need to be documented as part of your overall risk management efforts.
Vendor agreements need to set clear security expectations, incident reporting obligations, and liability terms. Due diligence and ongoing monitoring can help identify risks before they lead to regulatory penalties or operational disruptions.
How Do NIS2 Requirements Compare To Other Cybersecurity Regulations In Terms Of Third-Party Risk?
NIS2 places an even stronger emphasis on third-party risk management compared to many other cybersecurity regulations.
Here's how it compares to a few major frameworks:
NIS2 vs. NIS1
The focus on third-party risks is, in fac,t the most substantial change between NIS2 vs. NIS1. NIS1 focused more on internal security measures without expansive supply chain obligations. NIS2, however, expands on the original NIS Directive by explicitly requiring organizations to assess and manage third-party risks.
NIS2 vs. GDPR
GDPR compliance requires third-party risk management in terms of data protection and requires organizations to have contracts with processors handling personal data. NIS2 goes a step further and requires security risk assessments, continuous monitoring, and contractual obligations for security, even for vendors that don't process personal data.
NIS2 vs. ISO 27001
ISO 27001 includes third-party risk management as part of an overall information security management system (ISMS). However, compliance is voluntary. NIS2, meanwhile, mandates risk management practices for third parties and includes enforcement actions for non-compliance.
NIS2 vs. DORA
The Digital Operational Resilience Act (DORA), which applies to financial services organizations, actually has stricter third-party risk requirements than NIS2. DORA requires direct regulatory oversight of critical third-party providers. NIS2 requires strong vendor risk management, but an important distinction is that it does not impose direct regulatory supervision on suppliers.
Where To Start
After you understand whether your organization is in scope and what gaps exist in your current security program, the next step is to develop a compliance plan and begin implementation (see the section above on NIS2 Requirements for what you'll need to plan for).
A popular option for many organizations nowadays is to work with a virtual Chief Information Security Officer (vCISO) at this stage. A vCISO helps translate NIS2 requirements into a plan specifically made for your business. They provide the expertise needed to interpret requirements, assess your risks, and build a compliance roadmap, all without incurring the cost of a full-time security executive or having to build out an in-house team.
Compliance automation tools, which automate risk assessments, track your security controls, and generate documentation, can also vastly simplify the process. Our vCISOs at Rhymetec leverage compliance automation tools on behalf of our clients while also completing all of the manual security work needed to meet requirements.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We've worked with over 700 companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
Interested in reading more? Check out more content on our blog.