A SOC 2 readiness assessment is an important first step if your organization is thinking about obtaining SOC 2 compliance. Think of the readiness assessment as a health check for your security practices - it's meant to help you get everything you need completed before the formal audit.
In this FAQ, we'll tackle some of the most common questions we hear about SOC 2 readiness assessments - why you might need one, what it costs, how long it takes, who should be involved, and more. This will give you a clear picture of what to expect and help you understand what your organization needs before undergoing an external audit.

What Is A SOC 2 Readiness Assessment?
A SOC 2 readiness assessment is a pre-audit process that helps organizations prepare for their official SOC 2 audit. It identifies gaps in your current security controls and SOC 2 policies and procedures compared to where you need to be.
The first step is to select an external consultant. Your consultant will conduct a thorough review of your existing security controls (security measures, documentation, operational procedures, and more) to identify areas where you may not be meeting SOC 2 standards.
The assessment entails several key benefits, allowing you to:
- Have a third-party opinion of your SOC 2 audit preparedness
- Pinpoint gaps and weaknesses in your existing controls
- Obtain ideas on how to strengthen your processes and procedures
Testing your current controls and finding areas where remediation is needed is important to do in preparation for your audit.
How Much Does A SOC 2 Readiness Assessment Cost?
The cost of a SOC 2 readiness assessment can vary. The following factors impact cost: Organization size, the complexity of your IT infrastructure, the consultant you work with, the Trust Services Criteria you selected, the use of project management or GRC tools, and other factors that vary from consultant to consultant.
Readiness assessment estimates start at around $7,000 - $15,000. For a small startup with a straightforward infrastructure, costs typically start at the lower end. For larger organizations or for those with complex systems, costs can increase significantly, potentially reaching tens of thousands of dollars.
Some firms offer fixed-price packages that bundle the SOC 2 readiness assessment into the overall cost of obtaining SOC 2 compliance. Others charge based on the time and resources required to complete the assessment. Obtaining detailed quotes from multiple providers can help you understand the potential costs for your organization.
How Long Does A SOC 2 Readiness Assessment Take?
The timeframe to complete a SOC 2 readiness assessment varies. For large organizations or for those with more complex IT environments, it can take anywhere from 1-4 weeks. For smaller organizations with less complex environments, it can take as little time as several days to a week.
During this period, key activities include evaluating your existing security controls, identifying any deficiencies, and creating a plan to address those gaps. Another factor that impacts the time frame is how quickly your organization can make changes and remediate gaps.
Who Should Be Involved From Your Team?
A SOC 2 readiness assessment requires involvement from several key members of your team. These typically include:
1. IT and Security Personnel, as they have the best understanding of your technical infrastructure and current security measures.
2. Compliance Officers (If Applicable): Whomever at your organization is responsible for ensuring adherence to regulatory and industry standards should be involved.
3. Operations Managers: Personnel who oversee the processes and controls related to daily business activities can help make sure daily operations adapt to and are impacted as little as possible by any new security measures.
4. HR Personnel can provide information on employee onboarding, training, and access controls.
5. Executive Leadership: Executives are responsible for allocating resources and ensuring changes to the organization's security posture are communicated down the line. (Note: An emphasis on the role of executive leadership and governance in cybersecurity is increasingly being seen across other cybersecurity standards, including under the recently added NIST governance function).
Involving all of these specialized roles allows you to speed things up and facilitates an effective assessment. Using compliance automation software can also help fast-track the process by providing a centralized location where all involved parties can access and track pertinent information.
Does Your Organization Need a SOC 2 Readiness Assessment?
Whether your organization needs a SOC 2 readiness assessment depends on your circumstances and goals. It's particularly useful if you're new to SOC 2 or if you have not previously undergone a SOC 2 audit. It serves to make the entire SOC 2 process easier, as assessments are highly tailored to your organization's unique needs.
Not every company should follow everything under the SOC 2 standard. Choosing the right Trust Services Criteria is an important step in your journey. A readiness assessment allows you to identify the security controls and practices that you actually need to implement.
Can You Fail A SOC 2 Readiness Assessment?
No, you cannot technically "fail" a SOC 2 readiness assessment. The assessment is a preparatory step that identifies gaps and recommends improvements before your formal audit. It serves as a diagnostic tool to help you understand which areas need to be addressed to meet SOC 2 requirements.
What Happens If Gaps Are Found During The Assessment?
If gaps are found it means your organization has some work to do before pursuing the official audit. That's the purpose of the readiness assessment: to highlight and correct issues in advance.
The controls you may need to remediate depend on which Trust Services Criteria you selected. For example, if you selected the Security Trust Services Criteria and are not currently conducting measures like regular phishing training for employees, you may need to implement stronger controls to protect against unauthorized access and disclosure of data.

Who Performs A SOC 2 Readiness Assessment?
The assessment is typically performed by experienced third-party firms that specialize in compliance and security audits. This includes:
1. Certified Public Accountants (CPAs) with IT specializations have the expertise needed to understand both the technical and compliance aspects of SOC 2.
2. IT Consulting Firms that focus on cybersecurity and compliance, and are experienced in assessing and improving IT controls.
3. Managed Security Service Providers (MSSPs) offer a range of security services and can conduct readiness assessments as part of their broader security offerings.
These options all provide an external expert perspective, enabling you to identify gaps and act on expert recommendations to effectively meet SOC 2 requirements.
What Are The Most Frequently Found Gaps In SOC 2 Readiness Assessments?
At Rhymetec, we have worked with hundreds of companies on their SOC 2 readiness. Some of the most common gaps we see companies have include the following:
1. Access Controls: We often see gaps related to inadequate controls over user access to systems and data. This includes weak password policies, lack of multi-factor authentication, and improper user permissions.
2. Security Monitoring: Many organizations lack up-to-par monitoring based on SOC 2 guidelines if this is an area they haven't previously paid much attention to. Under SOC 2 requirements, systems and networks should be monitored for suspicious activities or unauthorized access.
3. Data Protection: There is often room for improvement in areas like data encryption. Our security experts have helped many organizations improve their data backup and recovery procedures in preparation for their audit.
4. Vendor Management: A lot of organizations don't realize how much oversight of their third-party vendors and service providers is required under SOC 2. We help organizations identify any gaps in due diligence, contract management, and vendor review & risk assessments.
5. Incident Response: Organizations often need to create a documented incident response policy and accompanying procedures. At Rhymetec, we craft detailed incident response plans tailored to our clients’ individual industries and needs.

Addressing these common gaps is not only critical for achieving SOC 2 compliance, but also for better protecting your organization's (and end users') data and systems.
Interested in reading more on SOC 2? Check out additional content on our blog:
- SOC 2 Compliance Checklist
- SOC 2 Type 1 vs Type 2: Which Do You Need?
- Rhymetec's Complete SOC 2 Compliance Guide
About Rhymetec
Rhymetec was founded in 2015 as a Penetration Testing company. We offer a range of penetration testing services to include:
- Mobile Application Penetration Testing
- Web Application Penetration Testing
- External Network Penetration Testing
- API Penetration Testing
After seeing a gap for broader security support in the market, Rhymetec grew to offer managed compliance services for frameworks like SOC 2, ISO 27001, GDPR, CCPA, HIPAA, HITRUST, NIST and more. Since then, we have served hundreds of SaaS businesses globally in all their cybersecurity, compliance, and data privacy needs. We're industry leaders in cloud security, and our custom services align with the specific needs of your business. If you want to learn more about how our team can help your business with your security needs, contact our team for more information.
Companies often find that SOC 2 compliance acts as a business enabler, unblocking sales and allowing them to break into new marketplaces.
However, obstacles like resource constraints and a lack of in-house expertise make crossing the finish line with compliance a challenge, especially for small and mid-sized businesses.
Achieving compliance with standards like SOC 2 can seem like a daunting task. In our latest webinar, Rhymetec CISO Metin Kortak spoke to Craig Saldanha from Insight Assurance about how to simplify SOC 2 compliance and navigate the 5 SOC 2 Trust Services Criteria:

Check out the recording to watch their discussion. A bit about the speakers:
Metin Kortak started his career in IT security and then joined Rhymetec to build data privacy and managed compliance as a service offerings. Rhymetec started as a penetration testing firm in 2015, and under Metin's leadership, we've expanded to do all things security and compliance, with a focus on working with startups.
Craig Saldanha from Insight Assurance has nearly 10 years of audit experience. He's an expert in GRC and third-party/vendor risk management. In his current role at Insight Assurance, he leads and manages SOC 2, PCI, & vCISO service lines.
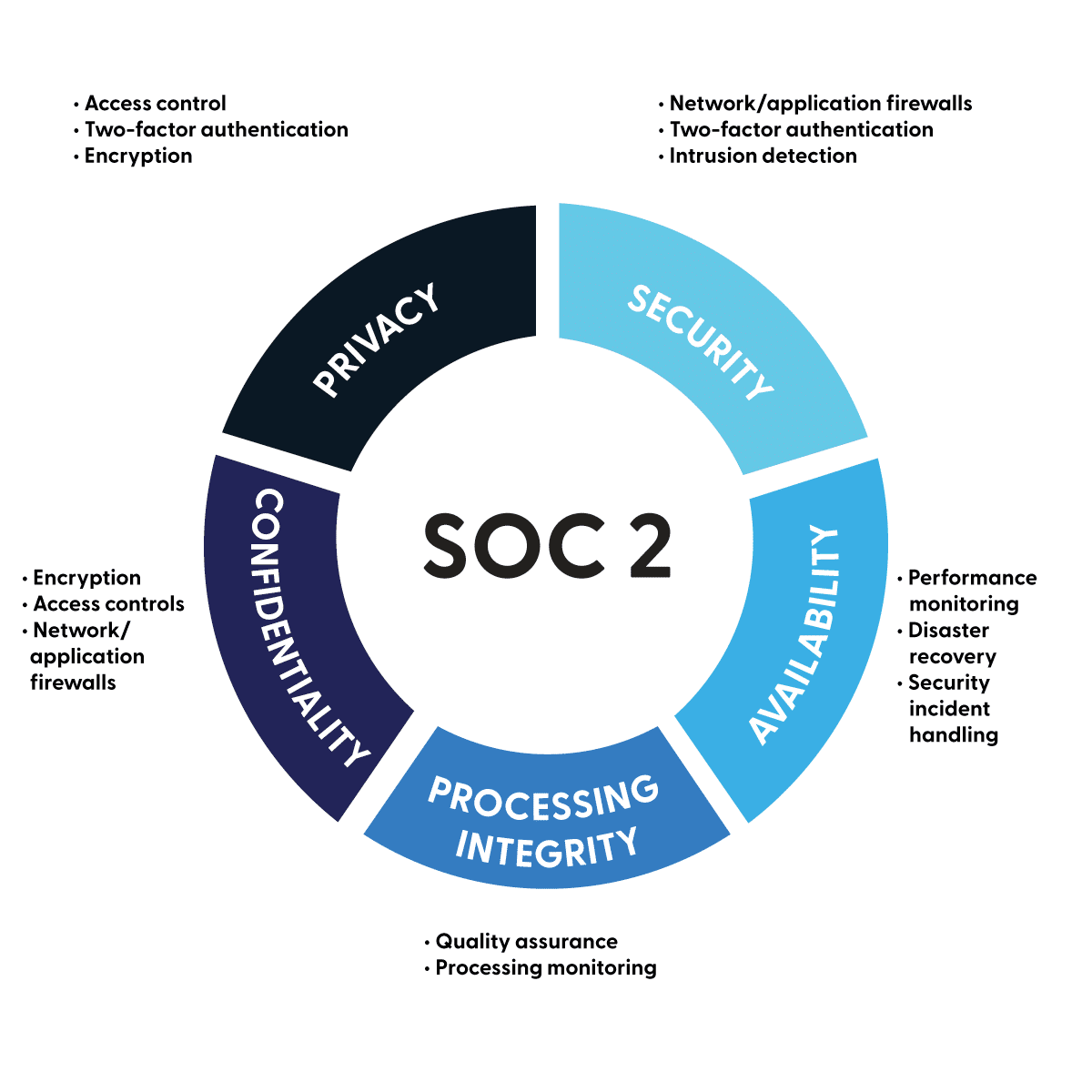
What Are The 5 Trust Services Criteria for SOC 2?
The SOC 2 Trust Services Criteria are used to evaluate an organization's controls related to data management. The 5 criteria are:
- Security (the protection of data against unauthorized access).
- Availability (the system's operational uptime and accessibility).
- Processing Integrity (ensuring that system processing is complete, valid, and accurate).
- Confidentiality (protection of sensitive information from unauthorized disclosure).
- Privacy (focuses on the collection, use, and retention of personal information).
"Security is the most common one that we see at Rhymetec," Metin noted.
The entire SOC 2 set of controls is over 150 controls. About 70% of that is likely going to be controls related to the security Trust Services Criteria. When customers are pursuing a SOC 2 assessment, security Trust Services Criteria are usually selected by default and included in every report.
The remaining 4 have fewer available controls to select. Some of them are more challenging to implement, which is one reason some companies just select the security criteria.
When it comes to which criteria to select, there are two main things to consider:
- What your requirements from your client base are
- What you value in your information security program
At Rhymetec, "We usually look at what our customers need, what is most important to them, and what their customer requirements are. A lot of organizations pursue SOC 2 because their clients are requiring them to have it, or they would like to pursue a larger client that has stricter requirements to start working with them," said Metin.
It also depends on what you value as a company. If you really value the availability of customer data and are concerned about privacy, you'd also want to select those criteria. Lastly, it also depends on factors like the type of data you handle and requirements specific to your industry.
At Rhymetec, we sometimes see customers pursuing all 5 Trust Services Criteria:
What Is SOC 2 and Why Are The SOC 2 Trust Services Criteria Important?
SOC 2 is a security and compliance standard created by the AICPA.
The primary purpose of SOC 2 is to ensure that third-party companies, SaaS providers, and other organizations protect their client information in a secure manner. SOC 2 compliance demonstrates your commitment to security and builds trust with your clients and stakeholders.
There are two types of SOC 2 audits: Type 1 and Type 2.
"Type 1 is a point-in-time audit and takes a much shorter time to complete with our customers at Rhymetec," Metin explained in our webinar. "We can usually get them compliant within about three months, and in some cases even less if they have already implemented some security controls."
For SOC 2 Type 2 (the more commonly sought type), companies are audited over a period of time.
Observation windows start at a minimum of three to six months, with some auditors requiring a 12-month period. Metin noted that, "...it makes the audit definitely more challenging, as companies are audited over the course of the observation window. If you missed an SLA (service-level agreement), or if an employee was onboarded incorrectly, that may cause some issues with your audit reports."
Getting expert input from the beginning of your SOC 2 journey can avoid these pitfalls, and enable you to choose the right criteria for your business.
From an MSSP (Managed Security Services Provider) perspective, Metin typically finds that there is a lack of understanding about the SOC 2 Trust Services Criteria in particular:
"When customers start working with us, we usually need to explain to them what the 5 Trust Services Criteria are and which ones they should select for their business. It's a very critical decision-making process."
So, let's jump right into what the Trust Services Criteria are, how to select the right ones for your business, and more:
Industry-Specific Examples for Each SOC 2 Trust Services Criteria
Let's take a closer look at each individual Trust Services Criteria:
1. Security
Regardless of your industry or what type of company you are, the security Trust Services Criteria is a mandatory component of the SOC 2 Report. It's required for all SOC 2 engagements and forms the baseline on which other criteria are then built.
For the next 4 criteria, we will provide examples of the types of companies that may opt to select each one:
2. Availability
Criteria around the availability of data apply to companies like online realtors and e-commerce platforms that rely on continuous uptime to support their customer transactions.
Telecom companies that provide communication services and need to maintain uninterrupted network availability would also want to explore availability criteria under SOC 2. Lastly, utilities and other critical infrastructure providers that need to ensure constant availability for operational purposes may opt for this set of criteria.
3. Processing Integrity
This applies to investment firms, accounting firms, and financial service providers that manage financial transactions and require accurate processing of data. Manufacturers that rely on automated processes for production and distribution would also want to consider the integrity selection criteria.
4. Confidentiality
"Law firms and legal service providers that handle sensitive client information would want to consider confidentiality," said Craig. So would consulting firms that deal with proprietary business strategies and government organizations that handle classified or sensitive information.
5. Privacy
Last but not least, privacy is often selected by schools, universities, and online education platforms to protect the personal data of students and staff. Likewise, online retailers that collect customer information for marketing purposes and healthcare organizations often opt for privacy criteria.
It's important to note that companies must roll out SOC 2 compliance across all locations and business units. Some adjusting may be needed if you operate across multiple regions to reflect nuances like local regulations and cultural differences. But in general, controls under the selected Trust Services Criteria should be consistently implemented.
Who And What Should Be In Scope?
The scope refers to the specific boundaries and focus areas that an audit will cover concerning the SOC 2 Trust Services Criteria.
By paying close attention to scope from the beginning, you can help reduce the scope and get through your audit easier. Here is what auditors will look for of who will be in scope, according to Craig:
"Any users that are critical to the delivery or the service that we are auditing should be in scope. In addition to anyone with access to sensitive data, customer data, or production data."
This could include your core team members across IT security, compliance, HR, finance, and operations, as well as consultants or contractors.
As for systems in scope (the what), it depends on 1) which systems impact your customers, and 2) which systems contain customer information.
"When we go through a SOC 2 Type 2 audit with a client, the auditors are looking into the production systems, production networks, and other production devices that actually impact customers. Staging environments or test environments that do not impact customer systems are not monitored or even audited," Metin explained.
If you have a SaaS product or other technical systems in place, you should think about what is actually in production and what impacts your customers. This also applies to any third-party vendors you work with.
If a vendor does not impact your customers in any way and does not process sensitive information, it will likely be assigned as low-risk and won't be subject to the same scrutiny as high-risk vendors (like your hosting provider or your email provider).
What Tools and Advice Should Companies Consider To Help Streamline Compliance?
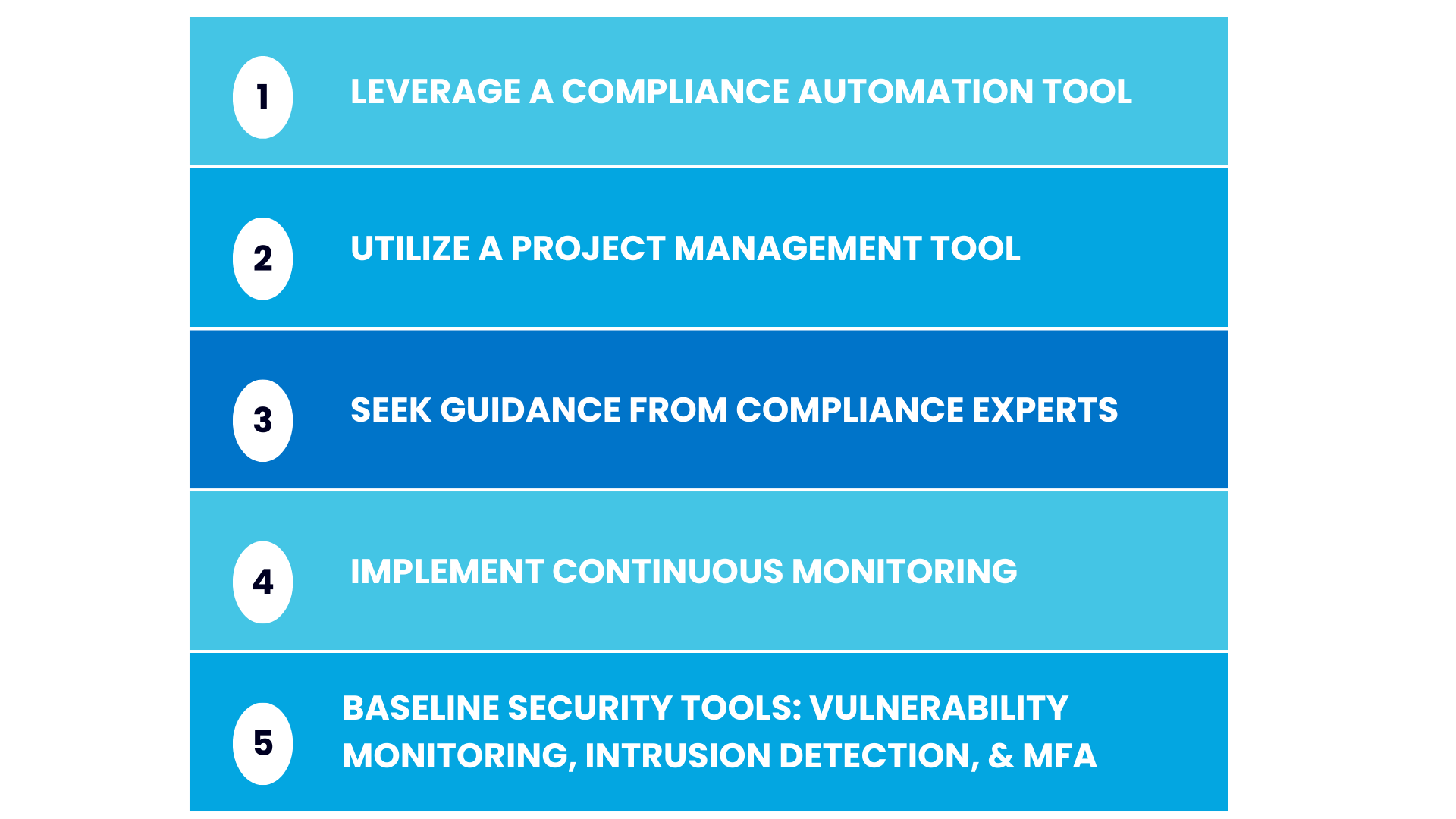
"First off, consider using compliance automation tools," suggested Craig. "We see clients save time to focus on their business by leveraging compliance automation tools in the market."
Spreadsheets don't cut it anymore. Compliance automation tools speed things up for everyone and are favored by auditors.
Having a solid project management tool is also very important.
There is a lot of work involved in SOC 2 compliance and there are typically 10 - 15 stakeholders who need to follow these controls and track them to completion. With a project management tool, you can add certain tasks (such as your penetration tests, access reviews, and risk assessments), assign them to the right personnel, and track them to completion.
Craig also suggested seeking guidance from compliance experts. Choosing the right vCISO and the right auditing partner for your business is critical, as is investing in internal training to ensure everyone understands their roles in your compliance journey.
Next, implementing continuous monitoring for compliance maintenance is extremely important. Any instances of non-compliance should be quickly rectified. Be sure to keep thorough documentation for your audit for any areas that fall out of compliance and how you addressed them.
There are some additional baseline security tools you will need to have, depending on which controls you select. These include vulnerability monitoring tools, intrusion detection systems, and a system to enable multifactor authentication.
5 Ways To Streamline Compliance
Concluding Thoughts: How Rhymetec Aligns SOC 2 Trust Services Criteria With Businesses' Operations & Goals
At Rhymetec, we enable businesses to align SOC 2 controls with their operations and goals to protect data, build customer trust, and meet regulatory requirements in their industry.
SOC 2 compliance shows that you take security seriously and mitigates risks. As demonstrated in our case studies with businesses like Kizen and Modicum, companies also find that having their SOC 2 report unblocks sales and opens up new market opportunities.
At Rhymetec, we see compliance and security as business enablers. We've helped over 600 companies establish scalable security solutions and get compliant in record time. Our custom solutions are specifically tailored to each organization we work with so their cybersecurity grows with their business and goals.
Explore our transparent pricingand schedule a time to chat with our team to learn more.
Interested in reading more? Check out additional content on our blog.
ISO 42001 sets the stage for responsibly managing AI systems within organizations. Taken together, ISO 42001 controls and policies represent the first international AI management system standard. With the proliferation of AI across many industries showing no signs of slowing down, guidance is sorely needed to address potential security, societal, environmental, and other risks posed by the use of AI.
Security concerns around AI are top of mind for many organizations at the moment. Recently, companies like Samsung have gone as far as banning the internal use of generative AI tools after a data leak with ChatGPT. Meanwhile, consumers are becoming increasingly concerned about how companies utilizing AI systems handle their data.
ISO 42001 aims to provide clarity around how organizations can responsibly use AI. Adherence to ISO 42001 controls sends a strong signal that an organization takes the security component of AI seriously. It is the most comprehensive attempt to date to provide clear requirements for implementing and continually managing the use of artificial intelligence. In this article, we go over what it is, who it applies to, and what businesses need to do to implement it.
Who Does ISO 42001 Apply To?
ISO 42001 is a voluntary standard. There are no legal obligations to adhere to it. However, it becomes a must-have for many organizations once their prospects and clients start asking for evidence and reassurance that their data is being safely handled by systems using AI.
Given the wave of media hype around AI, and the rapid improvement of the technology itself, many organizations have started to ask serious questions about the potential risks.
The standard applies to any organization developing or providing products or services that utilize AI systems. Based on official guidelines, ISO/IEC 42001 is for:
"Organizations of any size involved in developing, providing, or using AI-based products or services. It is applicable across all industries and relevant for public sector agencies as well as companies or non-profits."
The implementation of ISO 42001 controls, as well as the responsibilities within the management of AI systems, can vary depending on the individual organization.
What Do Businesses Need To Do To Implement ISO 42001 Controls?
The standard is quite robust but can be summarized into three main action items that organizations must complete in order to implement it. There is a clear focus on risk assessment, the role of governance, and compliance as a continuous process rather than a "check the box" item for businesses. The focus on these trends is reflected across the standard's three main components:
1. Create An AI Management System
A key component of ISO/IEC 42001 is the concept of an Artificial Intelligence Management System (AIMS). An AI management system is a documented system an organization uses to establish and enforce policies that manage assets using AI.
The AI management system also establishes objectives related to the use of AI and creates processes to achieve them. The goal is to have a set strategy for responsibly managing AI that is applied across the organization and aligns with overall business goals.
At a high level, the AI Management System should:
- Align with organizational objectives.
- Define and manage both risks and opportunities associated with AI.
- Oversee the implementation of controls to address AI security risks.
- Manage third-party vendors and partners involved in the development and/or ongoing use of AI systems.
In conjunction with the creation and documentation of an AI Management System, organizations must also conduct an impact analysis (determining the broader potential security and societal impact of AI systems, as well as the impact on business goals), establish clear policies on the use of AI, and implement controls to ensure data is responsibly handled in AI systems.
Lastly, the standard emphasizes the importance of continuous monitoring and improvement of the AI management system.
2. Conduct An Impact Analysis
There is a clear focus on the importance of assessing the societal impacts of AI systems. One of the core controls requires organizations to assess and document the potential impacts of their AI systems in the following areas:
- Environment sustainability (including the impacts on natural resources and greenhouse gas emissions);
- Economic (including access to financial services, employment opportunities, taxes, trade and commerce);
- Government (including legislative processes, misinformation for political gain, national security and criminal justice systems);
- Health and safety (including access to healthcare, medical diagnosis and treatment, and potential physical and psychological harms);
- Norms, traditions, culture and values (including misinformation that leads to biases or harms to individuals or groups of individuals, or both, and societies).
ISO 42001 controls require an AI risk assessment, along with an AI system impact assessment, to be conducted and continuously evaluated. This means that organizations must not only continuously monitor the impact of AI as risks change but must also evaluate the efficacy of their systems intended to mitigate that risk.
3. Implement and Continuously Improve ISO 42001 Controls
There are many areas where controls can be adjusted according to the organization's industry and needs.
Here is a summary of the standard's additional controls and overall implementation guidance:
Establish Roles & Responsibilities, and Document AI Policies: Organizations must establish and document clear policies around AI that are aligned with overall objectives and demonstrate a commitment to continuous improvement. Leadership must communicate the importance of AI management across the organization and share resources with employees. The roles and responsibilities related to the AI management system should be made clear, as well as how the AI management system requirements fit into business processes and goals. AI design choices, including machine learning methods, must also be documented.
Address Risks and Opportunities: Identifying potential risks and establishing a plan to address them is a critical step. This involves conducting an AI risk assessment and then selecting appropriate risk treatment options, implementing controls, and producing a statement of the applicability of controls. Objectives related to the use of AI, as well as a plan to achieve them, must be established and continuously reassessed.
Provide Organization-Wide Resources and Support: Create and distribute resources necessary for the AI management system and its ongoing improvement. Ensure that employees involved in AI-related activities receive appropriate training and education and that employees are aware of their roles within the AI policies.
Evaluate Performance: This involves ongoing monitoring, analysis, and evaluation of the performance of the AI management system. This can take the form of internal audits, intended to ensure conformity to AI management system requirements across the organization. Reviews of the AI management system must be conducted at planned intervals throughout the year.
Continual Improvement and Corrective Action: This last piece highlights the increasing importance being placed on continuous compliance rather than a "check the box" mentality. This is a shift we are seeing across the board for other requirements and standards, such as in the latest version of NIST CSF with the addition of the NIST Governance function.
In the context of ISO 42001, this means that organizations must continually improve their AI management system and take corrective action to make changes as needed.

In Conclusion: What ISO 42001 and The AI Management System Mean For Businesses
Organizations that adhere to ISO 42001 gain several key benefits. First and foremost, they gain the benefit of responsible use of AI and the peace of mind knowing they can provide evidence of that to any partners, prospects, or other business stakeholders.
As is often the case with other voluntary standards (such as SOC 2), organizations often find that their deals cycle becomes shorter, as prospects' questions around security are proactively answered and they no longer need to fill out lengthy security questionnaires.
Secondly, organizations gain the benefit of reputation management. Given the focus on mitigating environmental, societal, and economic damage, adherence to ISO 42001 controls serves as a signal that organizations care about their role in these issues and have taken steps to invest in the responsible use of AI. This can have the effect of improving their reputation as reliable, responsible, and trustworthy.
Lastly, there is an enormous benefit in terms of AI governance. ISO 42001 controls map onto laws and regulations around the use of artificial intelligence, allowing organizations to align the use of AI with laws relevant to their industry and location. As one of the first frameworks to directly address AI, ISO 42001 will serve as a baseline for future standards and laws.
Organizations can take a proactive approach by complying with ISO 42001. This saves time and money down the line when other frameworks and laws catch up.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business.
If your organization is interested in exploring compliance with AI standards, we now offer ISO/IEC 42001 certification readiness and maintenance services and are happy to answer any questions you may have.
About The Author: Metin Kortak, CISO
Metin Kortak is the Chief Information Security Officer at Rhymetec. Metin began his career working in IT security and gained extensive knowledge of compliance and data privacy frameworks such as SOC 2, ISO 27001, PCI, FedRAMP, NIST 800-53, GDPR, CCPA, HITRUST and HIPAA. He joined Rhymetec to build data privacy and compliance as a service offering.
Under Metin’s leadership, these offerings have grown to more than 200 customers, positioning the company as a leading SaaS security service provider in the industry.
Interested in reading more? Check out additional content on our blog:
- Maximize Your Use of Compliance Automation Platforms
- 7 Factors To Consider Before Implementing AI in Your SaaS Company
- Phishing Training For Employees: 5 Steps To Success
How are resource-savvy businesses fast-tracking and maintaining cybersecurity compliance in 2024?
Many companies are now using an innovative and complete solution that combines automation with hands-on, expert security services. Compliance automation platforms provide an invaluable tool that works in sync with manual tasks to achieve compliance in the fastest timeframe possible, helping you effectively prepare for your audit.
Our team of security experts at Rhymetec is extremely experienced with this process. We have helped hundreds of companies build strong infosec programs and meet compliance requirements while reaping the full benefits of an automation tool. For more information on how we can help with all of your security and compliance automation needs, contact our team today:
The Benefits of Compliance Automation
Compliance automation is an innovative tool companies use to establish and scale their information security (infosec) programs. The platform serves as a single source of truth for everything related to compliance, allowing companies to have sharp visibility into these areas and pinpoint exactly what they need to do.
Many companies elect to use an automation tool because they are astutely thinking ahead about their audits and what they can do to make the process easier. After all, what makes life easier for your auditor will ultimately make your life easier as well.
No auditor likes receiving headache-inducing 50-page Excel spreadsheets that they have to figure out how to navigate for every new engagement. Instead, auditors appreciate having a single place where companies can easily collect all relevant documentation laid out in a clear format. Compliance automation platforms provide exactly this.
They streamline the process in many areas, accomplishing the following tasks:
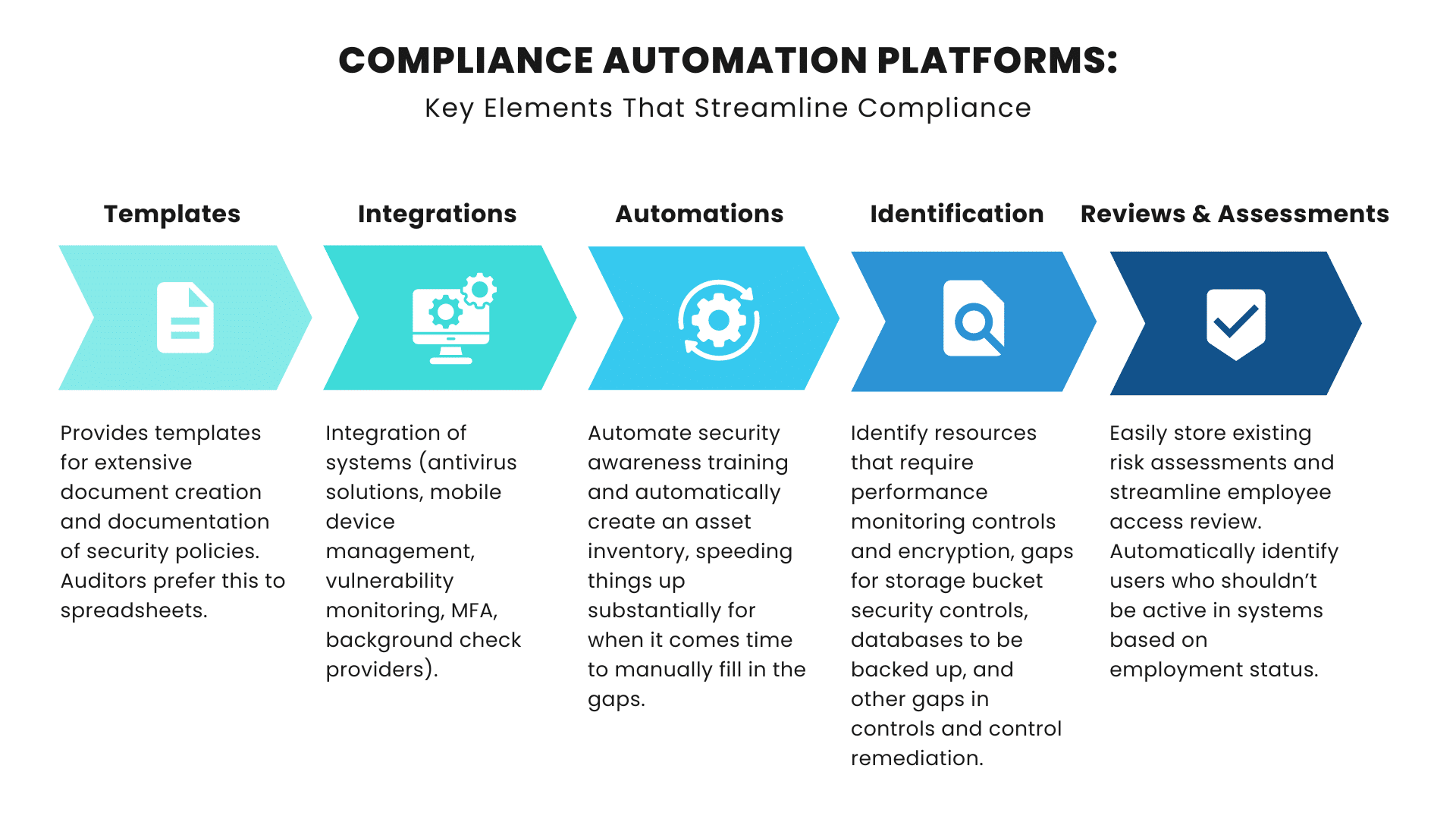
Policy Templates:
Compliance automation platforms provide robust templates for extensive document creation and documentation of security policies.
Integrations Provided By Compliance Automation:
A key advantage of using an automation platform is the level of integrations it provides. Platforms provide integrations in the following areas (and more) in order to streamline compliance:
- Background check providers to notify clients if background checks are missing for any employees.
- Vulnerability monitoring solutions to create test failures based on vulnerabilities and source code tools for identification of testing failures.
- Relevant client systems to identify systems without MFA.
- Mobile Device Management and antivirus solutions to identify gaps in compliance.
Human Resource (HR) Security Solutions:
Automation platforms can automate security awareness training for organizations. This is an important advantage, as many frameworks require security awareness training. Employee access reviews can also be conducted by identifying users who shouldn't be active in systems based on their employment status. This is made possible by collecting user access information through integrations with other systems.
Frameworks like SOC 2 require periodic performance reviews for employees. These platforms provide a centralized place for evidence collection of performance reviews.
Asset Inventory:
The automatic creation of an asset inventory using available integrations is a key benefit, speeding things up substantially for when it comes time to manually fill in the gaps.
Identification Through Compliance Automation:
Compliance automation platforms automatically identify control items in the following areas:
- Resources that require performance monitoring controls.
- Resources that require encryption in transit.
- Resources with gaps for storage bucket security controls.
- Databases that are not backed up.
- Gaps in controls and control remediation.
Risk Management:
Compliance automation platforms store existing risk assessments conducted by the customer or security professional. Additionally, they provides 3rd party supplier management by storing existing risk assessments for all vendors, and their security reports.
Security Questionnaire Fulfillment:
Lastly, they offer automated security questionnaire fulfillment, removing a large amount of the burden of filling out long questionnaires.
The automation and integrations provided by compliance automation platforms speed up an array of complex processes that would otherwise take substantially longer. However, a security and compliance professional is still needed to ensure your team is doing the manual tasks of meeting your desired compliance goals; drafting policies, setting up company-specific security awareness training, conducting risk assessments, and much more.
Pinpointing The Controls You Need and That Align With Auditor Expectations
Don't have a security or compliance professional in-house? Or unsure where to start?
This is where an outsourced team of security professionals can come in to carry out a wide range of manual components necessary to get businesses across the finish line for compliance. Rhymetec's team provides the customization needed to make security and compliance efforts specific to your unique infrastructure every step of the way.
For example, one of the best parts of SOC 2 is the level of flexibility it provides for the controls, allowing companies the ability to tailor it to fit their needs. A compliance automation platform used in tandem with the customized services from an expert security team enables companies to speed things up while also ensuring they implement only the controls that make sense for their business and will align with what the auditor will expect to see.

The specialization provided by a security team allows businesses to avoid overly onerous control implementation that may not be necessary in their compliance journey.
The Manual Components of Compliance: Humans Still In The Loop
Compliance requirements and voluntary standards mandate an array of hands-on security support that only a team of qualified professionals with years of experience across different subdisciplines in cybersecurity can perform. To achieve and maintain compliance, organizations need a team of experts in GRC, penetration testing & vulnerability management, cloud security, network security, incident response, and more.
Compliance automation platforms provide a great way to manage the process and continually identify areas that need attention, speeding up the time it takes to get started and complete manual tasks. Meanwhile, the customization provided by working with Rhymetec's team ensures alignment between the controls and auditors' checklists. It enables clients to show evidence of completion of controls that cannot be automated, including penetration testing, internal audits, and tabletop exercises.
The Initial Phase: Getting Set Up
In the initial phase of the engagement, Rhymetec's security team gets the client set up in the compliance automation platform by manually accomplishing the following tasks:
- Initial Set Up In The Platform: Rhymetec manually adds the client's information to the compliance automation platform. Additionally, employees, users, and all other relevant information depending on the individual client's needs are added to the platform.
- Integration of Relevant Systems: Next, the team integrates relevant systems with the automation platform and configures settings to get items including security awareness training and onboarding setup.
- Project Planning: Rhymetec's team meets with the client to determine the infrastructure details and create a system description. The security team works closely with the client at this phase to gain a deep understanding of their individual needs and to identify the exact controls they need to adhere to under the chosen framework(s).
Compliance isn't one-size-fits-all.
Organizations can have vastly different needs depending on factors like their industry, geography, company size, the third parties they work with, the types of data they handle, and more. Without an experienced security and compliance team to examine these factors, there's a risk of not doing enough or even doing too much.
Filling In The Gaps
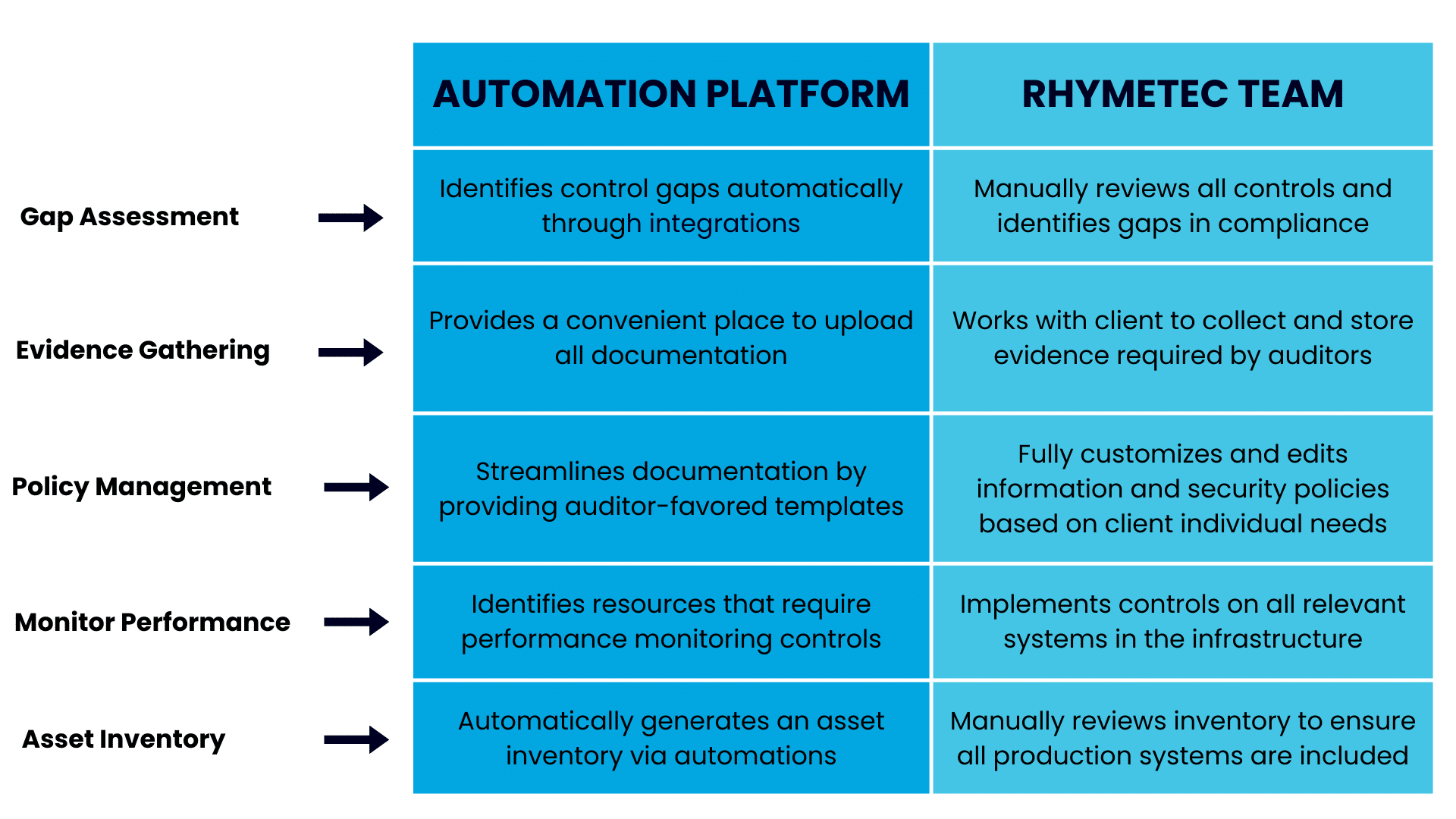
Using the information provided by the platform as a baseline, Rhymetec's team goes from there to fill in the gaps based on each client's individual needs. This stage involves:
- Gap Assessment: Rhymetec manually reviews all controls and identifies gaps in compliance for the client.
- Evidence Gathering: The security team works with the client and other stakeholders to collect and store evidence required by auditors, using the compliance automation platform as a convenient place to upload all documentation.
- Policy Management: Using templates provided by the compliance automation platform as a baseline, Rhymetec fully customizes and edits information security policies based on individual client needs.
- Performance monitoring controls: Based on the resources identified by the compliance automation platform, Rhymetec implements controls on infrastructure systems such as databases, servers, and buckets. This helps the client gain visibility into their infrastructure.
- Asset inventory: Using the asset inventory created by the automation platform, Rhymetec manually reviews the inventory and ensures all production systems are included in it.
These action items work hand-in-hand with the compliance automation platform in the following ways:
Completion of Manual Security Tasks
Thanks to the features of the compliance automation platform, many items are able to be easily identified as needed for the client on an ongoing basis. This substantially cuts down time, enabling the security team to fill in the manual pieces as soon as they are identified.
However, not every task has elements that can be automated. The fully manual tasks needed to meet controls under many cybersecurity regulations and frameworks include the following:
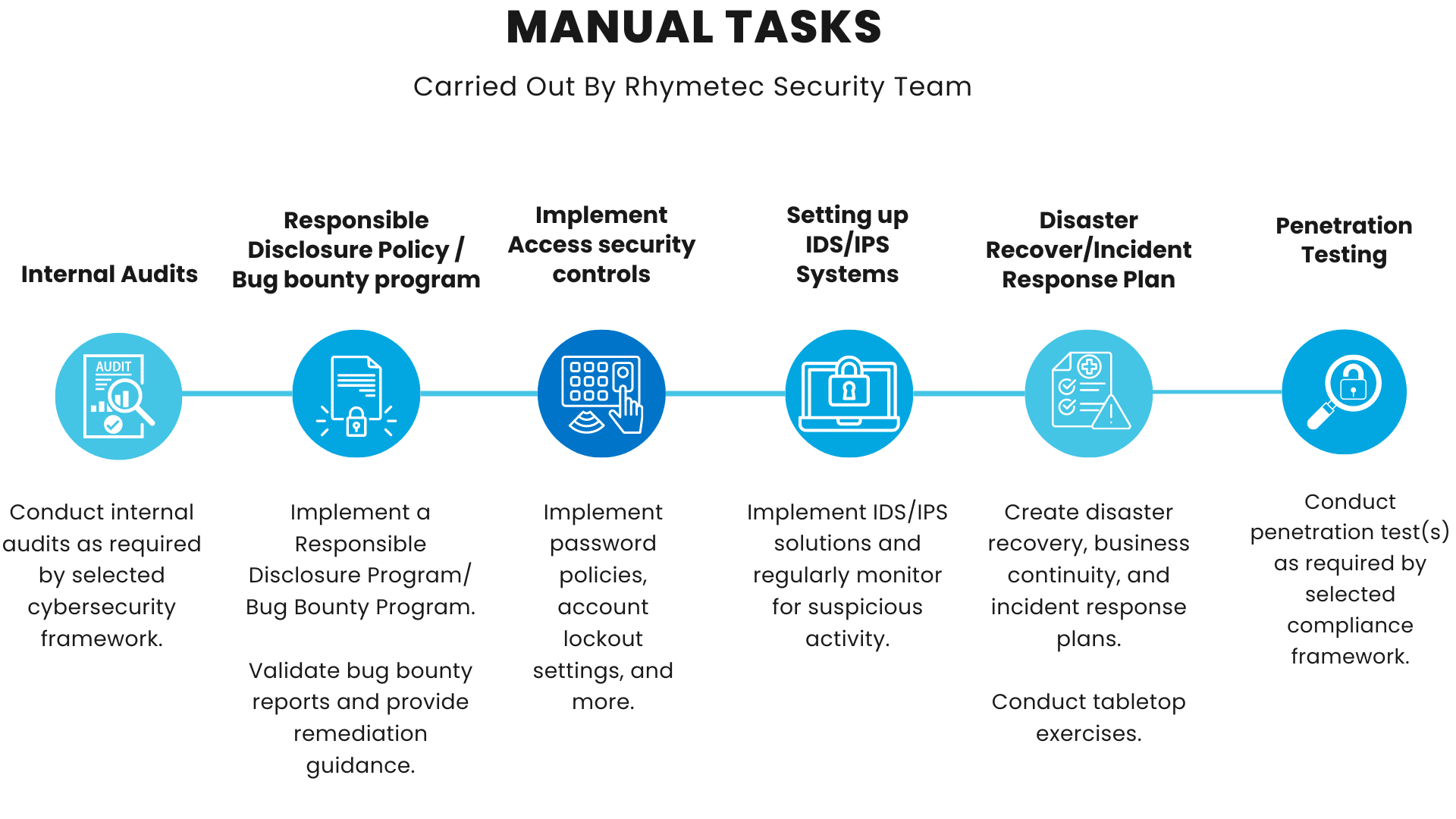
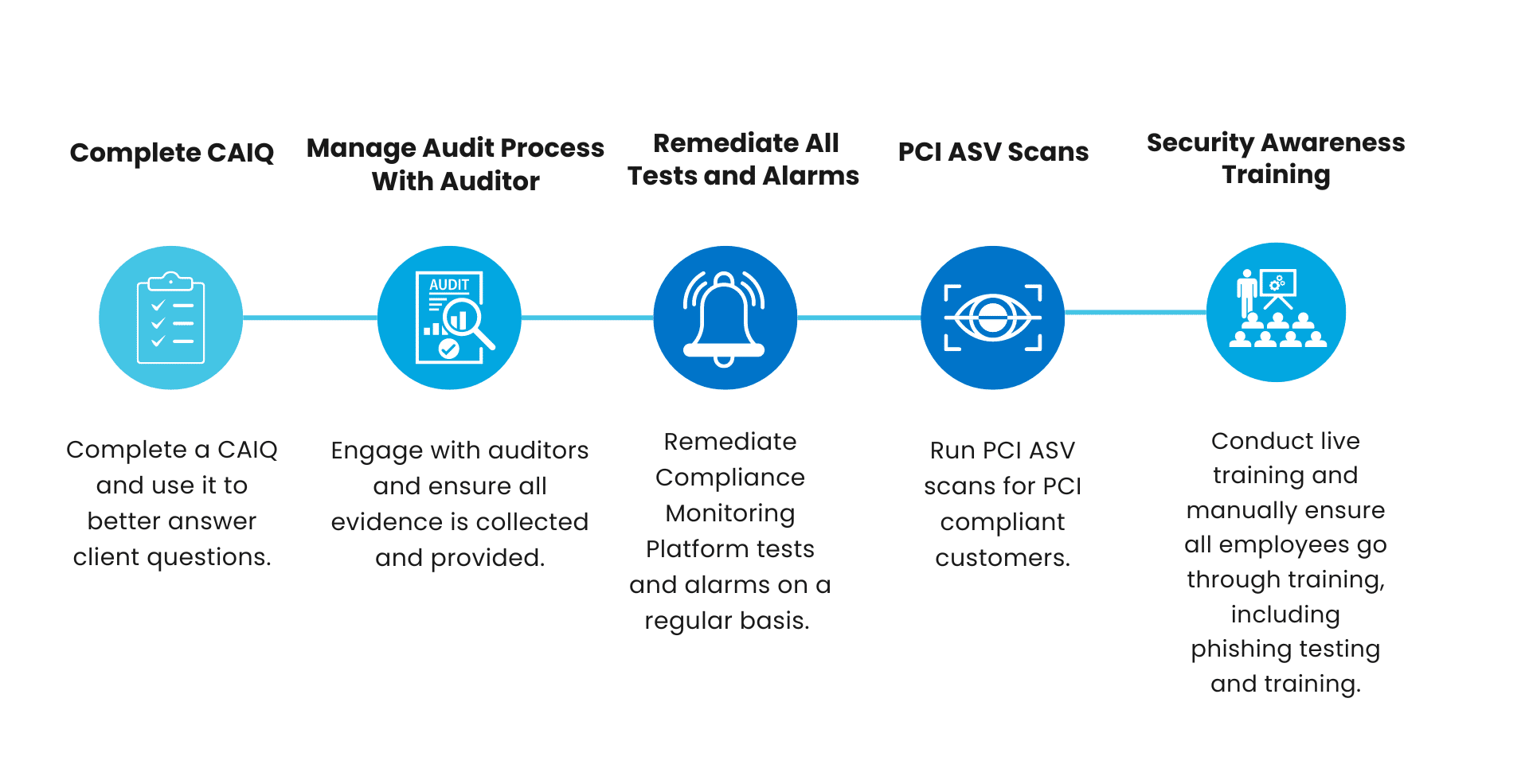
The above action items needed for compliance, such as penetration testing and tabletop exercises, cannot be automated. Items such as incident response plans also must be manually completed in order to be tailored to each individual company, their risk profile, and their industry.
The compliance automation platform comes back into play in the next phase, streamlining the completion of all additional security controls.
Fulfillment Of Additional Critical Security Controls: Manual Solutions Working With Compliance Automation
Rhymetec creates and implements the additional cybersecurity controls required by the compliance framework selected by the client. The compliance automation platform, meanwhile, plays a key role in this step for each control through system integrations and identification of areas for improvement.
Here's how the two solutions work in sync to streamline the implementation of critical security controls needed across many different frameworks, laws, and regulations:
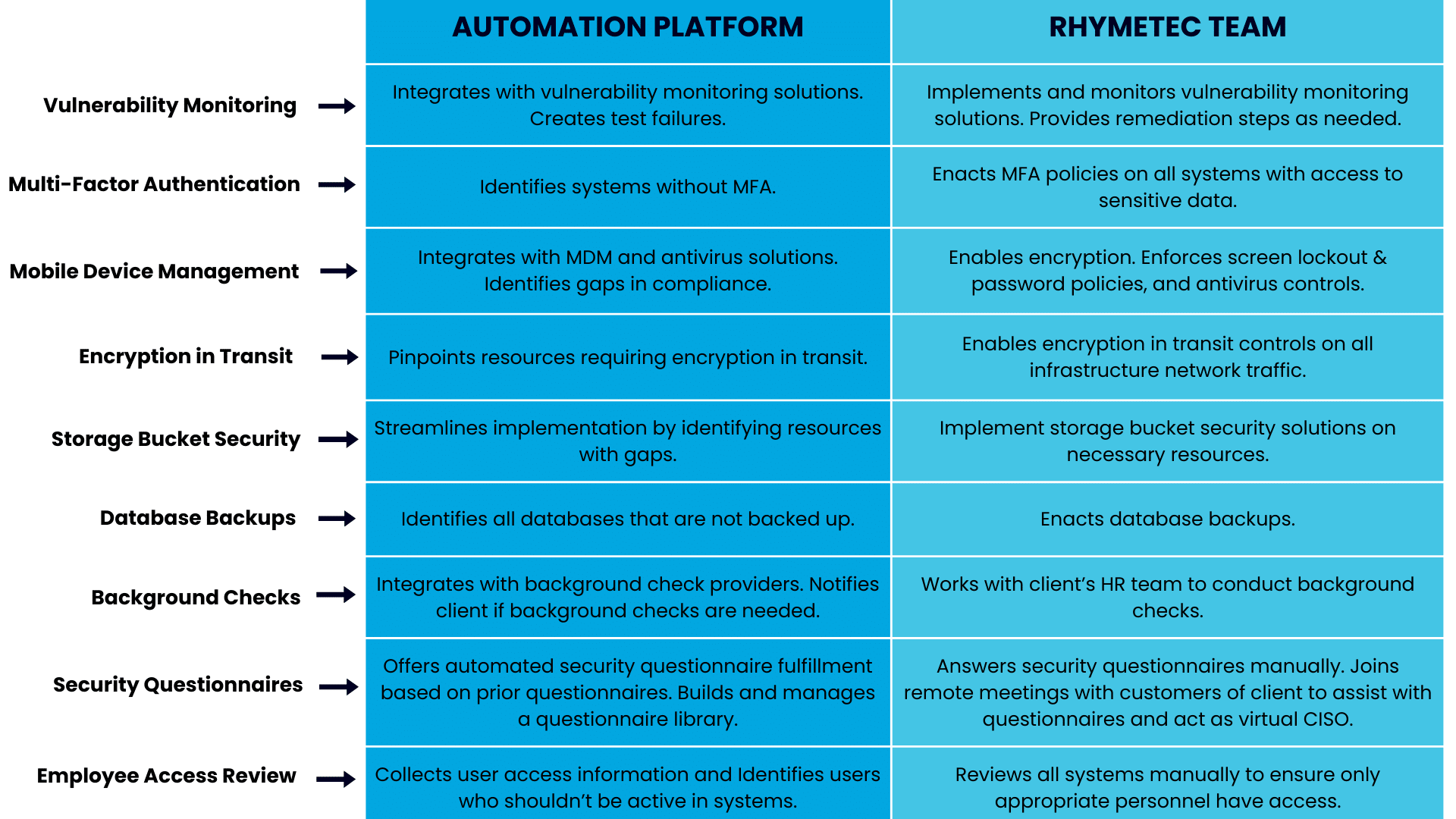
The platform serves as a foundation for the tasks performed by Rhymetec's security team, enabling them to jump right in and start the hands-on work.
As an example, almost every cybersecurity standard nowadays requires organizations to implement multi-factor authentication, as it is one of the best measures companies can take to protect themselves. The compliance automation platform is able to identify systems in a client's infrastructure without MFA. The security team takes it from there to enable MFA policies on all critical systems.
Final Audit Preparation, Conducting The Audit, & After The Audit
In preparation for the audit, Rhymetec ensures all necessary documentation is organized and accessible. For frameworks like ISO 27001, Rhymetec will conduct an internal audit to identify and address any non-conformities in preparation for the external audit. During the official audit, Rhymetec works closely with auditors to ensure all evidence is collected and provided.
For standards like SOC 2 that clients will be audited on annually, and to maintain a continuous strong posture of security, Rhymetec completes the following items on an ongoing basis: Annual vendor risk assessments, regularly updating risk assessments to reflect new risks, regularly reviewing firewall rules for customers to ensure they stay compliant with policies, and running continuous assessments like PCI compliance scans for PCI-compliant customers.
Don't forget, for some stakeholders compliance isn't always enough. Security questionnaires are a secondary tool that prospects use to evaluate your security against their own standards. Utilizing compliance automation can help you streamline this process. Using Rhymetec's team of experts can help you get into the weeds around more robust or complex questionnaires and even represent your business on security-related discussions.
In Conclusion: How Compliance Automation and Manual Security Services Provide A Full Portfolio Solution For The Modern Business
Compliance is not a sprint right before an audit.
It requires an ongoing solution that streamlines the process by automating the pieces that can be automated and leveraging a team of experts to fill in the gaps and carry out the manual tasks. Through a combination of automation and manual security services, organizations can maintain a posture of continuous compliance, ensuring that requirements are always being met and evidence of these standards can be accessed easily.
When used together, a compliance automation platform and the level of customization provided by an experienced security team fast-tracks compliance while avoiding a one-size-fits-all approach. Every company has its own controls that need to be implemented, as well as a unique risk profile. For effective compliance maintenance, modern businesses need an automation platform plus a team of security experts to carry out and maintain these requirements.
With Rhymetec, the manual components are accomplished by a security team with more than a century of cumulative experience across a diverse array of cybersecurity disciplines. Rhymetec leverages this experience to tailor compliance to fit organizations' individual needs and to maximize the efficiency of control implementation. Meanwhile, the compliance automation platform speeds things up every step of the way, provides a single source of truth for the client, and serves as an auditor-favored platform with all documentation presented in a clear format.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while also balancing security with budget.
We enable our clients to outsource the complexity of security and focus on what really matters – their business. If you are interested in our services, or if you simply have questions about security, you can contact our team for more information.
Interested in reading more? Check out our other blogs:
- Managed Compliance: An Updated Approach For The Cyber Regulatory World
- Security Policies For Small Businesses: 5 Tips For Effective Communication
- Cybersecurity for Startups: A Rhymetec Guide for 2024
The array of compliance requirements being propagated by both government and private sector entities is dizzying. The European Union's NIS2 regulations, the recent SEC data breach notification rule, and the ever-impending requirements under the U.S. DoD's CMMC are all examples of an expanding regulatory framework meant to bolster corporate information security practices and protect consumer data.
Building a comprehensive information security program that maps technical and process controls to existing and pending regulations has never been more critical, but companies still struggle.
Compliance is complex. Small companies often lack the full-time subject matter experts required to translate technical jargon into risk reduction and compliance controls. Large organizations, meanwhile, struggle with massive IT infrastructures and huge amounts of data.
This article dives deep into the world of information security compliance. First, we'll examine why governments and private industry groups are expanding requirements. We'll then spotlight a few upcoming requirements. Finally, we will review a way that organizations, both large and small, can stay current with compliance - an approach Rhymetec dubs "managed compliance" or "compliance management."
Managed Compliance: Why Is The Regulatory Landscape Shifting?
Before we dive into how the landscape is shifting, let's start with a more basic question - why is it shifting?
The simple answer is that the cyber threat landscape is becoming increasingly dire at the same time as geopolitical tension is increasing around the world.
Ransomware continues to plague both large enterprises and small organizations, and ransomware groups are resorting to increasingly high-stakes gambits in order to elicit payments.
These aggressive tactics were on full display in February of 2024 with the attack on Change Healthcare, which allegedly compromised terabytes of personal health data belonging to millions of consumers. The ransomware group Black Cat not only encrypted files but also threatened to publicize the information if payment was not made, resulting in an eye-popping twenty-two million dollar ransom.

Secondly, geopolitical tensions between the United States and Russia continue to remain at a post-Cold War low point. The risk of Russian, Iranian, and Chinese cyber-espionage against the U.S. technology and critical infrastructure sectors continues to remain acute, with both CISA and the U.S. FBI publishing repeated warnings that they have evidence of ongoing campaigns.
Finally, the cybercrime ecosystem itself is expanding rapidly, and the cybercrime market is booming: The global cost of cybercrime is projected to increase 15% year over year, reaching an annual $10.5 trillion USD by 2025. Market economics incentivizes threat actors to target both consumers and businesses as it pays, particularly in countries and economies with relatively weak rule of law and low median earnings.
Governments around the world, but particularly in Western Europe and the United States, are responding to these challenges with an increasing array of regulations, warnings, and executive decrees designed to incentivize companies to improve their security posture and reduce risk.
Pending Regulations & Examples of Managed Compliance in a Rapidly Changing World
There are many regulations one could cover in this article.
To illustrate our point we will focus on two salient requirements that are particularly telling of where things are moving: The EU's NIS2 Directive and the SEC data breach notification requirement. We will also talk about recent updates to frameworks like ISO that address new risks to organizations posed by Artificial Intelligence.
The NIS2 Directive and The EU
NIS2 is an EU-wide compliance requirement that will require many EU businesses to meet increasingly stringent information security requirements. Version 2 builds on an original framework that was specifically targeted to improve the security of a narrow band of critical infrastructure companies within the European Union. NIS2 expands on both the scope and scale of NIS, mandating requirements for what will likely be the majority of EU businesses.
EU regulations work by creating a comprehensive framework at the EU level, which is then written into each EU member's legal code by a certain date. As it stands, many organizations will be required to implement NIS2 by the fall of 2024, specifically ones that provide necessary services to the EU member states, regardless of location.
Some key changes in NIS2 include:
Executive teams and boards of directors become directly liable for compliance violations under the update. Organizations that fall under the regulation are required to implement many specific technical safeguards and are required to report serious incidents to their national Cyber Security Incident Response Teams (CSIRT). Covered organizations are also required to carefully evaluate their supply chains for risks that could result in substantial disruption.
NIS2 is novel in several respects, particularly by making boards of directors and corporate executives directly liable for non-compliance. We've seen a similar move to raise cyber risk to the board level in the United States, with the recent propagation of the voluntary framework NIST CSF V2.0 with the addition of the NIST governance function.
SEC Data Breach Notification Rule
The United States currently lacks a strong national cybersecurity regulation such as NIS2. However, various states and federal entities continue to add additional requirements. In 2023 the U.S. Securities and Exchange Commission published a data breach notification rule, requiring covered financial entities to publicly report a substantially adverse event within 24 hours. While this may seem relatively minor, this extends reporting requirements to thousands of publicly traded financial institutions.
The new SEC rule is illustrative of the U.S. patchwork approach to security compliance. Unlike the EU, which is adopting sweeping pan-national legislation, the U.S. instead operates under an array of state, federal, and administrative information security requirements. This can create enormous complexity for both startups and large enterprises as there are questions of jurisdiction, legal language, and mapping complex controls to a variety of requirements.
ISO 42001 and The AI Management System
The AI boom isn't showing any signs of slowing down. Organizations all over the world are increasingly incorporating the use of AI into their operations and systems. While AI may represent exciting opportunities, a cautious approach that keeps in mind security risks is necessary, particularly as AI is increasingly incorporated into many SaaS companies.
Before implementing AI, security experts recommend that organizations consider the following factors: The projected impact on products, transparency and customer trust, contractual obligations and customer agreements, how AI processes data, and, above all - data privacy and security concerns.
Enter ISO 42001.
ISO 42001 is the first international standard for the use of Artificial Intelligence. It provides comprehensive guidance for organizations on how to establish and manage systems using AI. Similar to the updated NIST CSF framework and NIS 2 in the EU, there appears to be a stronger focus on governance in ISO 42001.
Certification with the standard includes incorporating a defensible systems management strategy specifically for AI. Under controls that address leadership, top management must show how the AIMS (AI Management System) is being used across the organization and how it aligns with the overall direction and goals of the organization.
It's important to note here that this part of the standard emphasizes continuous improvement. To stay compliant, organizations must provide ongoing evidence that their AIMS is not only continually working as intended but that they are continually improving it to align with new uses of their systems.
Overall, ISO 42001 illustrates yet another shift in the direction of two areas:
1 ) The increasing importance of governance.
2) The sharper focus on continuous compliance rather than a "check the box" mentality of compliance.
Three Benefits of Managed Compliance
At Rhymetec, our vCISO services take the approach of continuous managed compliance.
That is, we don't treat requirements as a fixed-in-time prescriptive list that's checked off once it's done. Instead, we work with our customers to continuously demonstrate affirmative compliance across multiple frameworks and requirements.
We fully manage your legal and voluntary compliance for you in a way that is guaranteed to continuously fine-tune your security posture, be defendable to auditors, and scale with your growing business. We take a multi-step process that includes:
1. Understanding Which Compliance Requirements Apply
It can be remarkably complex for small organizations (and sometimes large ones!) to even begin to understand which compliance requirements they are legally obligated to meet. For example, a large financial institution operating out of New York State may be obligated to meet cybersecurity requirements under:
- NYDFS Cybersecurity Regulation
- The EU's General Data Protection Regulation (GDPR)
- The U.S. Gramm-Leach-Bliley Act (GLBA)
- The Payment Card Industry Data Security Standard (PCI DSS)
- SOC 2 (As required by customers)
- ISO 27001 (As required by customers)
Rhymetec works continuously with our clients to examine their current business and which existing requirements may apply to them while also keeping an eye on developing requirements in order to help our customers proactively meet legal obligations.
2. Implementing Controls Effectively: Doing Just The Right Amount
One of the benefits of working with a Managed Security Services Provider to implement a managed compliance program is that we leverage more than a century of cumulative experience across a diverse range of cybersecurity disciplines. We bring this experience to bear for clients in order to maximize the efficiency of control implementation. We only implement the controls that make sense for our clients.
Fortunately for our clients (and their bank accounts!), in many cases, one security control can meet requirements under multiple frameworks and regulations. For example, the control "employee training" can be tailored to meet requirements under both SOC 2 and HIPAA.
When architected properly, an information security program should be able to meet a large number of requirements with a small number of controls. Effective compliance programs serve as business enablers, allowing the business to work in confidence that they have substantially reduced breach risk and are meeting relevant regulatory requirements.

Bonus Tip For Startups:
As your organization matures, you will likely be asked to meet an increasing number of both legal and voluntary requirements such as SOC 2, NIS2, GDPR, CCPA, FedRAMP, and others. Rhymetec works to understand our client's business so that we can advise you to be as efficient as possible when implementing compliance frameworks the first time, resulting in cost savings down the road.
For example, if you know you will be selling to the federal government in 2025, we can architect your program to begin meeting and documenting FedRAMP requirements early.
3. Continuous Review
Security is not a fixed point in time activity.
A well-managed compliance program should involve continuous review of the organization's security controls to ensure they are being effectively met and that processes are properly implemented. Many organizations that attempt to meet compliance themselves follow a similar pattern:
- An organizational leader is tasked with meeting a common compliance requirement or framework, often SOC 2 or ISO 27001 (more often than not because a prospect has asked for it).
- They spend several weeks building documentation, paperwork, and processes to demonstrate compliance.
- They implement many required technical controls.
- But, by the time the auditor comes, many of the processes have been discarded in favor of efficiency and many of the technical controls have lapsed, resulting in a poor showing on the compliance audit.
At Rhymetec, we take the opposite approach:
Controls are only as effective as their implementation and processes are only as good as the adherence to them is. We work with our clients to ensure that security policies aren't just documents that sit on a shelf collecting dust but are core business documents that form the basis for how the organization does business.
Knowing you've outsourced the complexity of all of this and have a team continuously taking care of your legal and voluntary requirements provides peace of mind. That's one of the key benefits of managed compliance that companies report.
Rhymetec's Method for Accelerating and Managing Compliance
Our team has worked with hundreds of clients across different industries. We are equipped with the expertise to conduct a thorough gap analysis at the beginning of the engagement to identify areas of improvement. Our team works with you to craft a roadmap tailored to your individual security needs and the compliance requirements relevant to your industry.
We leverage the latest technology, such as compliance automation tools, to streamline documentation of your security policies, collect evidence for audits, and more. We offer expert phishing testing services, internal audits, and penetration testing services (including mobile application penetration testing and web application penetration testing) that are guaranteed to meet security controls.
Finally, our team of experts continuously reviews and updates existing controls, evaluates your information security program throughout phases of growth, and stays up to date with the latest changes in the industry or with compliance standards to help you prevent gaps in compliance—providing an effective compliance maintenance program.
About the Author: Justin Rende, CEO
Justin Rende has been providing comprehensive and customizable technology solutions around the globe since 2001. In 2015 he founded Rhymetec with the mission to reduce the complexities of cloud security and make cutting-edge cybersecurity services available to SaaS-based startups. Under Justin’s leadership, Rhymetec has redesigned infosec and data privacy compliance management programs for the modern SaaS-based company and established itself as a leader in cloud security services.
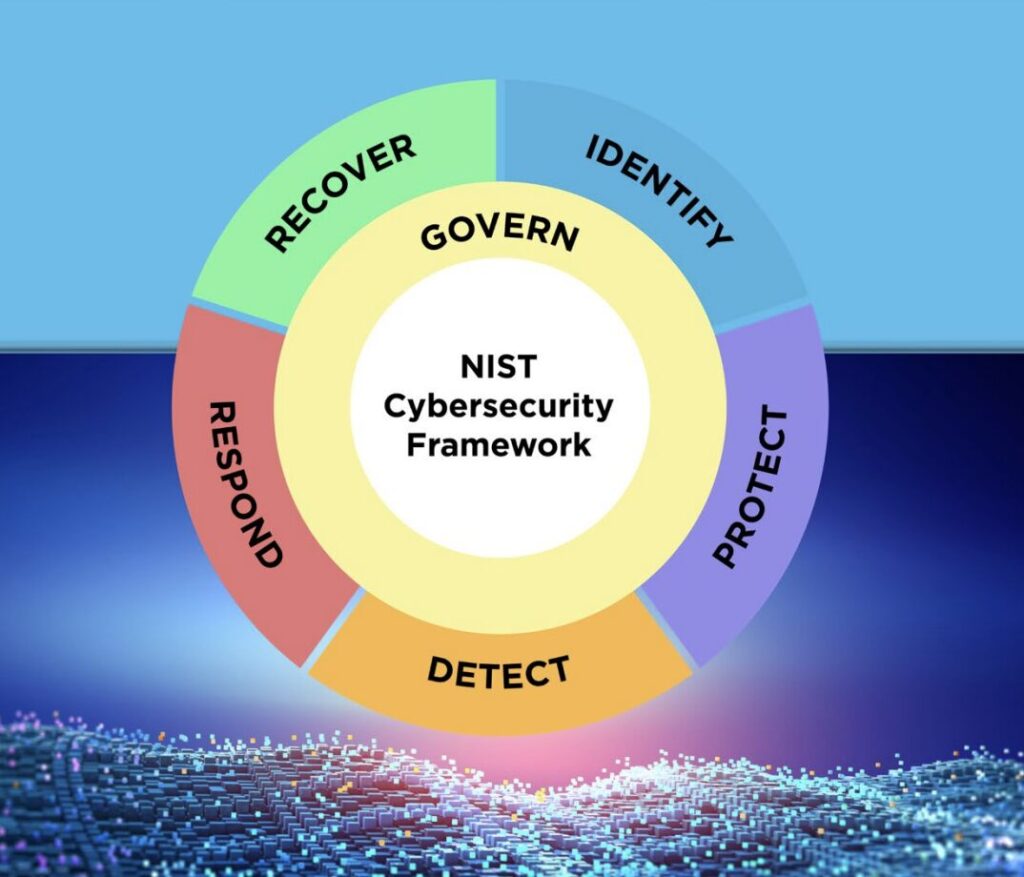
There were many major releases in 2024. The hit new TV series FX Shogun, Dune Part 2, Taylor Swift's Eras Tour on Disney+, and most importantly, the new NIST Cybersecurity Framework Version 2.0 with the addition of the NIST Governance Function.
Thrilled yet? Well, you should be. The National Institute of Standards and Technology regularly releases technical guidance documents and frameworks for both the public and private sectors to use as best practices guides.
The original NIST Cybersecurity Framework (NIST CSF) serves as the basis for tens of thousands of cybersecurity programs around the world and directly inspires many other compliance frameworks and requirements.
By meeting NIST, organizations automatically cover many controls in other requirements that overlap with NIST. It's widely considered the gold standard of robust cybersecurity across many industries.
This article will explore NIST CSF V2.0, what's changed, and what's likely to change going forward.
If you have more specific questions on what these changes may mean for your organization, please feel free to contact our team for support:
What Is The NIST Cybersecurity Framework?
NIST CSF was originally intended as a cybersecurity framework for critical infrastructure companies.
Some key facts about NIST CSF V1.0:
- The original NIST CSF was released in 2014
- NIST CSF was developed in collaboration with industry and government stakeholders
- Provided a high-level framework for cybersecurity risk management
- Consisted of five core functions: Identify, Protect, Detect, Respond, and Recover
- Each core function is broken down into subcategories and controls
- NIST CSF is voluntary, but it is widely used by organizations of all sizes
- NIST CSF was updated on a regular basis to reflect changes in the cybersecurity landscape
In addition, many regulations (particularly those in the United States) directly drew on controls originally formulated in the NIST Cybersecurity Framework.
NIST CSF is split into five modules reflecting elements of the cybersecurity lifecycle, including:
Identify:
- Get visibility into the network environment, including asset categorization.
- Create continuous monitoring for new assets being brought back online or added to the network.
Protect:
- Implement robust security protocols across the organization to include IDS/IPS, firewalls, EDR systems, and anti-virus
- Create and maintain a regular patching program to reduce exploitable vulnerabilities.
- Utilize strong authentication (such as multi-factor authentication) to reduce the risk of unauthorized access.
Detect:
- Use security monitoring tools to get visibility into suspicious activity such as unauthorized access attempts.
- Set up a notifications and alerts system to inform your security team in a timely manner of potential incidents and threats.
Respond:
- Have a well-documented incident response plan that describes the procedures for responding to security incidents.
- Be able to contain security incidents to minimize their impact and mitigate further damage.
Recover:
- Ensure a comprehensive backup and recovery program is in place to protect critical assets and restore data in the event of a security incident or natural disaster.
- Test back up and recovery programs regularly and update as needed.
NIST CSF V2.0: What's In It?
NIST CSF version two carries on many of the fundamental themes found in the original NIST CSF. However, a new element has been added: NIST Governance.
Source: NIST Drafts Major Update To Its Widely Used Cybersecurity Framework.
Note the clear emphasis of the guidance under this new function:
Governance
- Executives take on an active role in organizational risk management and collaborate on how potential cybersecurity gaps across the organization may impact broader objectives.
- Regularly hold dialogue among executives about risk management strategies, roles, and policies.
- Establish security goals tailored to the industry and organization at the executive level.
- Document and communicate security policies and expectations down the line to managers and individuals.
- Encourage collaboration at the executive level and across the organization about risk management strategies, including cybersecurity supply chain risk.
- Ensure cybersecurity risk management is explicitly rolled into overall Enterprise Risk Management (ERM).
In short, the updated CSF is intended to help executives communicate better about cybersecurity, with the goal of ensuring robust security through every level of the organization:
"The CSF helps organizations translate their terminology for cybersecurity and cybersecurity risk management into general risk management language that executives will understand."
The features of the new version also help enforce that the CSF applies to small organizations as well as large ones, and can be easily tailored to fit their needs.
A New Addition: NIST Governance and What It Means For Businesses Going Forward
It's important to remember, that compared to many functions of a business, cybersecurity in its current state is still extremely young.
Cybersecurity began as a sub-discipline of Information Technology.
In the 2010s, business leaders, particularly in industries with a heavy reliance on information technology, increasingly came to see cybersecurity as a standalone field - one that needed adequate resources and provisioning to succeed.
The NIST Governance section is an effort to add concreteness to cybersecurity as a board-level conversation in its own right and not just an offshoot of information technology. NIST states:
"The CSF's governance component emphasizes that cybersecurity is a major source of enterprise risk that senior leaders should consider alongside others such as finance and reputation."
It's worth pausing for a moment and reflecting on what a significant statement this is.
NIST is advising companies to consider cybersecurity as significant of a risk as running out of money or having their reputation destroyed (note that bad cyber practices can cause both of these things).
The new NIST governance function includes six key aspects:
- Organizational Context (GV.OC)
- Risk Management Strategy (GV.RM)
- Roles, Responsibilities, and Authorities (GV.RR)
- Policy (GV.PO)
- Oversight (GV.OV)
- Cybersecurity Supply Chain Risk Management (GV.SC)
The introduction of Cybersecurity Supply Chain Risk Management (C-SCRM) under governance is another critical addition.
Software supply chain attacks have become increasingly common in recent years, such as the 2020 SolarWinds breach and the 2023 MOVEit vulnerability, famously exploited by the CL0P ransomware group.
Rhymetec's Take: The business impact of investing in cybersecurity is exceptionally high. The threat landscape has continued to increase in risk, and organizations are increasingly expecting third-party suppliers to not only meet compliance but also demonstrate security that goes past it. NIST CSF's Governance change is an excellent addition that reflects the growing importance of security for modern businesses.
The Expanded Scope: NIST Governance
NIST CSF V1.0 was focused specifically on critical infrastructure. While this did not stop organizations all over the world from using it as a basis, it did create a sense that it might be overkill for some businesses.
NIST CSF V2.0 has remedied this flaw and makes it clear that the CSF can be tailored to fit any business regardless of size or maturity.
Rhymetec's Take: In this case NIST is catching up to where many organizations already are. NIST has long and widely been used as the basis for cybersecurity programs, but it is a positive development for them to acknowledge and expand the use case.
Additional Resources for Implementation and The NIST Governance Section
One of the most profound and significant changes has been the additional material NIST is publishing to help organizations build their security programs based on the cybersecurity framework.
NIST is publishing several appendix documents, including:
Implementation Guidance for CSF V2.0
The implementation guidance is an extremely valuable addition to the CSF.
Many organizations, particularly those that don't yet have dedicated cybersecurity staff, may struggle to understand what the cybersecurity framework is actually asking of them. The addition of remediation guidance provides an enormous amount of additional clarity.
For example, let's take a control found in the new governance section:
GV.SC-06: Planning and due diligence are performed to reduce risks before entering into formal supplier or other third-party relationships.
For seasoned governance risk and compliance professionals, this may seem straightforward.
But for an organization without GRC staff that is just beginning to think about third-party due diligence, how can this be implemented?
Fortunately, the Implementation Guidance provides real-life, concrete examples for businesses to better understand how to do a practical implementation of a security control. For GV.SC-06, NIST provides 4 implementation examples:
- Ex1: Perform thorough due diligence on prospective suppliers that is consistent with procurement planning and commensurate with the level of risk, criticality, and complexity of each supplier relationship.
- Ex2: Assess the suitability of the technology and cybersecurity capabilities and the risk management practices of prospective suppliers.
- Ex3: Conduct supplier risk assessments against business and applicable cybersecurity requirements, including lower-tier suppliers and the supply chain for critical suppliers.
- Ex4: Assess the authenticity, integrity, and security of critical products prior to acquisition and use.
For many organizations, implementation examples will undoubtedly be key to help clarify the request being made of them by the guidance. Note how each example has slightly different wording: compliance isn't a one-size-fits-all project.
Many compliance requirements leave room for organizations to implement the security control in a way that will optimally benefit their organization.
Working with a vCISO can help by leveraging decades of experience in tailoring security controls to your company's unique risk profile, maximizing your return on investment while also ensuring that your organization meets the technical and intended definition of the control.
For instance, example 4 only has the organization assessing critical suppliers, whereas example 1 has the organization tiering their suppliers and level of due diligence. If an organization is just beginning their C-SCRM program, they may not have the sophistication or resources (or need!) to fully vet every single supplier based on a tiered approach.
While the company matures, only assessing mission-critical suppliers can be an excellent addition to a security program, and it is far better than doing nothing.
Rhymetec's Take: Implementation guidance should substantially help bridge the gap, particularly with small or immature organizations to effectively implement NIST CSF 2.0's guidance. Note that simply claiming you are meeting a control will not pass an auditor's scrutiny. You need to have a documented process for meeting the control, appropriate technology, and evidence that your policy is acted upon.
NIST CSF 2.0 Reference Tool
Another addition with NIST CSF 2.0 is a new reference tool that can be used to identify requirements and export data quickly.
Rather than reading a massive PDF, the new reference tool makes it simple to rapidly identify controls or subsets of controls within NIST and export that section or subset either in machine or human-readable format.
Users are able to filter based on the control family and whether the control is focused on first or third parties and then export the data into JSON or Excel. The reference tool also includes the aforementioned implementation guidance, significantly simplifying the process of understanding and complying with controls.
This makes it considerably more user friendly and allows easy exporting of data.
The reference tool could be helpful for many organizations, but particularly for large or complex organizations that may have many different individuals and functions responsible for implementing the second version of NIST CSF to include updates in alignment with the NIST Governance element.
NIST CSF 2.0 Quick Start Guides
The last major addition to NIST CSF 2.0 we will cover is quick start guides, designed to help organizations get started on implementing controls from NIST Governance and other functions based on their unique circumstances and risk posture.
Quick start guides are segmented into:
- Organizational Profiles: According to NIST, an organizational profile "...describes an organization's current and/or target cybersecurity posture in terms of cybersecurity outcomes from the Cybersecurity Framework (CSF) Core."
- Community Profiles: These are designed to help specific industries and sectors implement the CSF based on their unique risk profile. According to NIST, "A Community Profile can be thought of as guidance for a specific community that is organized around the common taxonomy of the CSF."
- Small Business Resources: The small business section of the quick start guide is focused on providing actionable, easy-to-implement steps that small businesses can use to begin implementing CSF V2.0 controls.
- Cyber Supply Chain Risk Management (C-SCRM): C-SCRM is a growing concern for organizations of all sizes that continues to be highlighted by major supply chain breaches. The C-SCRM quick start guide provides specific guidance on how you can use the CSF to establish your C-SCRM program.
- Enterprise Risk Management: The Enterprise Risk Management quick start guide helps organizations better understand the implementation of NIST CSF 2.0, particularly NIST Governance, in a complex and multifaceted enterprise context.
- Tiers: NIST CSF 2.0 tiers "...can be applied to CSF Organizational Profiles to characterize the rigor of an organization's cybersecurity risk governance and management outcomes. This can help provide context on how an organization views cybersecurity risks and the processes in place to manage those risks."
Concluding Thoughts On NIST Governance and NIST CSF 2.0
NIST CSF 2.0 represents a huge step from the original NIST.
There has clearly been a focus on making it easier to conceptualize, understand, and implement CSF controls in a way that will reduce organizational risk for businesses.
The NIST governance section is a critical addition that helps solidify the case that cybersecurity and cyber risk management are no longer a function of the IT department, but a function that requires whole-business buy-in from the board of directors down to individual department heads.
Contact our team at Rhymetec for more information:
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while also balancing security with budget. We offer a full suite of security services including mobile application penetration testing services, phishing testing services, PCI compliance scanning, and more.
Our team has extensive experience helping organizations implement a variety of security frameworks and compliance requirements, including NIST CSF, SOC 2, HIPAA, GDPR, and many more.
We enable our clients to outsource the complexity of security and focus on what really matters – their business. If you are interested in our services, or if you simply have questions about security, you can contact our team for more information.
About The Author: Metin Kortak, CISO
Metin Kortak is the Chief Information Security Officer at Rhymetec. Metin began his career working in IT security and gained extensive knowledge of compliance and data privacy frameworks such as SOC 2, ISO 27001, PCI, FedRAMP, NIST 800-53, GDPR, CCPA, HITRUST and HIPAA. He joined Rhymetec to build data privacy and compliance as a service offering. Under Metin’s leadership, these offerings have grown to more than 200 customers, positioning the company as a leading SaaS security service provider in the industry.
So, you've just been handed a security questionnaire by a potential customer, and you're not sure where to start.
What is access control? What should you answer when asked if you utilize strong authentication across all applications with sensitive data?
This Rhymetec guide will not only help you answer these questions but will also provide suggestions that you can use to strengthen your security posture and work with potential customers more confidently, with less risk of non-compliance or a data breach.
What Is A Security Questionnaire?
Security questionnaires are used by your potential customers to assess their third-party vendors and suppliers. Numerous major third-party incidents have occurred in recent years, and threat actors are increasingly attempting "supply chain attacks" - cyberattacks that target a critical element of a particular supply chain and then attempt to move laterally into other parts of the supply chain.
For example, the identity and access management platform Okta recently suffered from numerous compromises that threat actors attempted to use to gain access to Okta's customers' data. All of this was a long way of saying companies with mature cybersecurity programs care about supply chain attacks - a lot.
Enter the security questionnaire.
Security questionnaires are required by some compliance requirements such as HIPAA, GLBA, and PCI DSS. In addition, understanding who you're doing business with, what their security controls are, and what types of data you will be sharing with them is important from a simple risk mitigation perspective.
Security Questionnaire Example Questions
So, what exactly do security questionnaires typically ask?
It can vary a lot, but here are some common types of questions:
- Does your organization employ strong authentication measures such as multi-factor authentication for all corporate applications that hold customer data?
- Does your organization offboard employees within 8 hours of the termination of employment?
- Does your organization conduct routine penetration testing to identify vulnerabilities in your environment?
- Does your organization have documented incident response plans and processes?
- Does your organization routinely train users regarding information security and risk?
Depending on the potential customer you are working with, questions may be very in-depth or very cursory. In many cases, your customers may tier their security questionnaires; a company that stores data about tennis shoe manufacturing needs far less scrutiny than a company storing Protected Health Information (PHI).
Security Questionnaires and Compliance
Security questionnaires aren't only driven by risk requirements. They are also driven by specific legal compliance requirements that your customers fall under. We will provide two examples of major compliance regulations that directly touch on vendor security.
In both of these, notice that nowhere is it mandated that you must send a security questionnaire. Instead, both require that organizations assess their vendors. The security questionnaire is the form that this assessment takes.
The HIPAA Security Rule
The Health Insurance Portability and Accountability Act Security Rule (HIPAA): HIPAA applies to healthcare organizations and other organizations that handle Protected Health Information (PHI).
Under HIPAA, any organization handling PHI that is considered a "covered entity" is required to comply with the HIPAA Security Rule, a specific set of information security standards. In addition, "business associates" of covered entities are also required to meet all requirements in the security rule:
- 164.308 Administrative safeguards. (A) Risk analysis (Required). Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity or business associate.
The U.S. Department of Health and Human Services also publishes guidance on how to conduct the risk analysis required by section 164.308.
The Bottom Line: If your organization gets a security questionnaire from a healthcare organization and you will be handing PHI, take it extremely seriously. You may be considered a HIPAA business associate and be required to comply with the HIPAA Security Rule. An experienced vCISO can help guide you on how to answer questions and implement missing security controls.
The Gramm-Leach Bliley Act and The Security Questionnaire
The GLBA applies to financial services organizations. Part of the regulation requires organizations to meet certain information security requirements. eCFR Part 16, § 314.4 spells out specifically what financial institutions need to do in order to maintain compliance regarding third-party suppliers:
- Taking reasonable steps to select and retain service providers that are capable of maintaining appropriate safeguards for the customer information at issue;
- Requiring your service providers by contract to implement and maintain such safeguards; and
- Periodically assessing your service providers based on the risk they present and the continued adequacy of their safeguards.
The Bottom Line: If you are getting a security questionnaire from a financial services organization, they are likely trying to meet their legal requirements under GLBA. The organization likely isn't measuring you against a specific standard where all requirements must be met to do work with your organization. If you don't meet every control in the risk questionnaire, consider having a conversation with the customer about which ones they find totally necessary to work with a vendor, and identify a plan to meet those on a set time scale.
How Do You Answer a Security Questionnaire?
Answers to security questionnaires from customers should be honest, straightforward, and complete.
For example, to answer the following question:
- Does your organization routinely train users regarding information security and risk?
You might reply:
- Users are trained on a monthly basis on information security best practices using the security awareness training platform KnowBe4. In addition, regular simulated phishing campaigns are conducted against employees. If an employee fails a phishing test additional training is mandated.
Notice this answer gives a specific example of not only that the activity is being carried out but how the activity is being carried out (KnowBe4).
It also goes into detail about how often the phishing test takes place, and even provides additional evidence of a serious security posture by describing an interrelated simulated exercise.
However, don't go overboard with information. If your customer is asking a question about training, you don't need to tell them about your amazing vulnerability management practice. Instead, answering questions with additional detail on related policies, procedures, or technology can help make the customer's job easier.
The most important thing to do is never lie.
If there are certain questions that your potential customer has asked that you don't want to disclose, have a frank and honest discussion about what information you can provide, what you can't, and why. Lying on vendor risk questionnaires can put your organization in potential legal jeopardy, both civilly and criminally.
Should I Get Outside Help in Answering a Security Questionnaire?
Many organizations turn to managed security services organizations for help in answering security questionnaires.
Why choose a managed security services company to help you?
There are a few different reasons.
First, cybersecurity can be extremely complex! Answering vendor risk questionnaires isn't always a straightforward exercise. Does your routine security assessment performed by a third party satisfy the definition of a penetration test? Does annual user training meet the question, "Do you regularly engage in security awareness training?"
These types of details matter but aren't always immediately apparent to those answering a security questionnaire.
Secondly, the "why" of a security questionnaire matters. Mistakenly answering a question on a security questionnaire from a customer who is simply doing their due diligence can be damaging. But mistakenly answering a question for an organization assessing your HIPAA compliance under the business associates rule can be fraught with legal peril.
An experienced vCISO can help navigate these waters and ensure that answers are correct and backed with evidence.
Finally, answering security questionnaires doesn't have to be hard! There's no reason that you should be spending weeks fretting over whether your security awareness training program is up to snuff.
Engaging a managed security services company can help you rapidly respond to security questionnaires, unclogging your sales pipeline and turning security compliance into a selling strength.
SOC 2 and The Security Questionnaire
Fortunately, there may be a way that you don't need to answer every security questionnaire that comes your way.
Enter the SOC 2 Report.
SOC 2 is a voluntary framework that organizations can meet and be audited against on an annual basis. By meeting requirements under SOC 2 Type 2 and undergoing an annual audit, you can have a specific report outlining your security controls to provide to prospective customers, dramatically simplifying the process.
SOC 2 isn't just a way to get out of doing security questionnaires, though.
Organizations are increasingly choosing their vendors based on good security practices and continuous compliance. Using a vendor like Rhymetec to help you meet SOC 2 can expedite your sales process, build trust with potential customers, and enable you to engage prospects who want to see evidence of your security before doing business.
The Bottom Line
Many organizations use security questionnaires as a way to screen potential vendors for unacceptable security risks. This is becoming increasingly common, as companies wish to strengthen their third-party risk management in light of recent breaches due to vendors and suppliers.
Hopefully, this guide helped clarify how to answer questions on security questionnaires and how to turn risk assessments into a business enabler rather than a cost center.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We've worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while also balancing security with budget.
We enable our clients to outsource the complexity of security and focus on what really matters - their business. If you are interested in our services, or if you simply have questions about security, you can contact our team for more information.
About The Author: Metin Kortak, CISO
Metin Kortak is the Chief Information Security Officer at Rhymetec. Metin began his career working in IT security and gained extensive knowledge of compliance and data privacy frameworks such as SOC 2, ISO 27001, PCI, FedRAMP, NIST 800-53, GDPR, CCPA, HITRUST and HIPAA. He joined Rhymetec to build data privacy and compliance as a service offering. Under Metin's leadership, these offerings have grown to more than 200 customers, positioning the company as a leading SaaS security service provider in the industry.
Interested in reading more? Check out our blog.
Ask any security professional what the biggest risk to organizations is, and nine times out of ten you'll get the same answer - people.
What security professionals know from experience is further confirmed by security research. Verizon's 2025 Data Breach Investigations Report puts the percentage of breaches that involved human error as high as 60%. Despite the best intentions, even the most diligent employees are susceptible to falling for social engineering tactics like phishing emails.
The onus is on company leadership to not only establish clear security policies for their business but to effectively communicate these policies to employees.
You could have the best, most meticulously documented security policies in the world, but they won't be able to help if they aren't communicated to the people who handle your assets daily. In 2025, small businesses also face added scrutiny from enterprise customers and regulators, making strong policies not just a security measure but a business requirement.
Rhymetec's Senior Cybersecurity Analyst, Kyle Jones, discussed how to effectively communicate security policies with employees in the latest episode of SaaS District:

Rhymetec, a Managed Security Services Provider focused on cybersecurity, compliance, and data privacy, enables SaaS organizations to have in-house security expertise at a fraction of the cost. Security professionals like Kyle have firsthand experience behind the scenes of the information security programs at hundreds of companies.
Based on Kyle's experience, here are 5 tips he encourages businesses to use to communicate security policies with employees effectively:
1. The First Rule of Security Policies for Small Businesses: Know Your Audience
"The first thing I would suggest is know your audience. Know who you're communicating to,” suggested Kyle when asked how to communicate security policies in a startup environment of rapid growth. "If you're a CEO, a CTO, someone that's going to roll out policies - the first thing you want to focus on is knowing your audience. If you're a marketing agency, you don't want to draft heavily technical policies for your employees, because the communication is going to fail."
When tailoring and communicating policies to your organization, you want the policies to become ingrained as practice, not just documents that sit on a shelf (or in a file on your Google Drive that nobody looks at twice!).
The first step to effectively accomplishing this is to know your audience and make sure you remember to tailor your language to everyone in your audience.
If you work in tech, it may seem evident to you what the policy means when it says:
"All corporate devices must utilize full-disk encryption using the AES-XTS data encryption algorithm in compliance with the NIST Advanced Encryption Standard".
But this likely means nothing to your company's lawyer or accountant. Instead, simplify the language and foster clear communication. If the policy is going to apply to a non-technical audience it's far better to create a policy like:
"All corporate laptops and desktops must enable full-disk encryption in their device's settings."
Creating effective policies and procedures requires remembering that many users may not be security or even IT knowledgeable. This is becoming even more important as many small businesses are adopting AI tools and cloud platforms in 2025. Policies must account for a non-technical audience using technologies that carry significant risk if misunderstood.
2. Make Sure Your Small Business Security Policies Are Drafted by a Subject Matter Expert
Kyle emphasized the importance of working with a subject matter expert who understands the regulatory requirements in your industry as well as the voluntary security standards your customers may want you to have.
Having a subject matter expert develop your policies, especially in the early stages, allows you to align your policies with industry standards and with what you want to achieve as your company grows. Businesses that bake security in from the get-go establish a solid foundation, saving money and headaches in the long term.
Many organizations see security policies as "another GRC checklist item". This couldn't be further from the truth. Security policies are a core part of your business, and working towards adherence is critical.
However, even before building buy-in, you need to make sure your security policies are rock solid.
Here are a few questions you should ask in reference to the organization or individual drafting your policies:
- Are they basing their security policies on a risk assessment specific to your organization?
Organizations have dramatically different risk profiles based on industry or sector. For example, a software as a service company has numerous risks related to cloud hosting, data segmentation, and cloud identity and access management. These risks are not shared by a typical accounting firm. Policies should be tailored to your specific organization and can't be written in a vacuum.
- Does the person or organization have a strong working knowledge of how policies are implemented in practice?
Policies are only as useful as their implementation (and you will be audited based on both!). There should be a strong plan for operationalizing any policies that have been drafted on behalf of your business. This is where working with an outside expert like a Managed Security Services Provider, particularly for startups who may not have the resources to build out large in-house security teams, can come into play as a resource.

Ensuring The Companies of the Future Are Secure
To Kyle, one of the most important challenges of his work is making sure companies have solid security practices in place and that they are secure from the ground up:
"At Rhymetec, we're working with startups. A lot of them are early-stage startups…A lot of the companies that I work with and manage the security program for are the future. They have very powerful technologies and very innovative products".
The companies he works with are forward-thinking and looking to grow quickly. Establishing solid security policies for small businesses is critical before they expand into new marketplaces or internationally, before they go public, or before they are acquired.
Subject matter experts like the team at Rhymetec take the job of security entirely off their plate so they can focus on core tasks and grow their business.
3. Emphasize Security Policies Throughout the Year
There's nothing worse than policies that haven't been adopted.
Identify opportunities throughout the year where you can emphasize security policies for your small business in a proactive and exciting way.
"Something else I think that all organizations can do more of is emphasizing the importance of the policies. The policies are not an annual thing we review and send out to employees, and it's done. We want to find different ways to emphasize the policies," Kyle pointed out.
Have a company all hands?
This can be a great opportunity to discuss security policies, their implementation, and overall best practices. Include policy provisions in your security awareness and training courses, and aim to connect policies with outcomes.
When employees ask questions about anything security or IT-related, that can be a great opportunity to reference the policies and see what they say. When Kyle talks to the companies he manages security programs for, he uses their questions as an opportunity to bring up the policies and emphasize their importance.
It can be difficult for employees to conceptualize why security policies are necessary as they can often seem divorced from outcomes.
Walking the company (at a high level) through how a ransomware attack happens, or how threat actors launch business email compromise campaigns can be informative and help solidify the importance of adhering to policy language. The point is not to fearmonger, but to provide information that helps employees mentally link the policies to the reasons behind them.
People are more likely to adhere to something if they understand it.
In other words, don't just tell people what to do - show them why it matters.

4. Have a Training Program Built Around the Policy Language
Staff awareness training is an excellent opportunity to reinforce and build on your policies.
You want to ensure that your training program directly reflects language from your policies. For example, if you have a policy around full disk encryption (to use an earlier example), reinforcing this and providing a how-to guide in your training provides an excellent opportunity for reinforcement.
As another example, if you have a policy of reporting any suspicious emails as phishing for the security team to look at, reinforce this with training! Small businesses now often rely on a myriad of cloud collaboration tools, APIs, and AI assistants. Your training must be updated to reflect this reality and directly reference related policies, such as how to securely handle shared data or what information can be input into AI systems.
It's hard for employees to remember technical minutia and playbooks, so constantly reinforcing and iterating on your organization's security posture and policies is critical.
5. Update and Review Policies Regularly
Risk to your organization changes.
Both the regulatory and threat landscapes are in constant flux. Policies should not only be updated regularly but should be continuously reviewed and adjusted based on new information.
For example, the advent of large language models such as OpenAI's GPT-4 and Google's Gemini should force organizations to reimagine their policies:
- Are employees allowed to use these applications at work?
- What types of data can be shared with them?
- Do our policies reflect current regulatory language about algorithm decision-making?
These are important questions to answer. At Rhymetec we recommend conducting regular policy reviews. Working with a vCISO can dramatically simplify this process as they will be in tune with regulatory and threat landscape changes that could impact your business.
In summary, here are the 5 expert-approved tips discussed in this article to effectively communicate security policies to employees:

Security Policies for Small Businesses: The Bottom Line
Small businesses need security policies that work for them. They need policies that are tailored, based on real risks the business faces, and that meet a range of complex compliance requirements.
When done right, reinforced, and iterated on, policies form the backbone of a security program and enable organizations to do business with confidence and precision.
Hopefully, this article helped solidify how to draft and implement policies effectively. At Rhymetec, we believe that security and compliance are continuous processes that need to evolve and improve over time. We work directly with clients to build policies and security programs that meet regulatory requirements, scale with their growing organization, and enable business outcomes.
If you have more specific questions on crafting security policies for your business, please feel free to contact our team:
FAQs: Security Policies For Small Businesses
Why are security policies so important for small businesses?
Because most breaches stem from human error, strong policies protect against mistakes and provide much-needed guidance to employees. They also demonstrate accountability to customers, auditors, and regulators.
How often should small businesses update their security policies?
At least annually — but ideally every 6 months or whenever major changes occur in technology, staff, or regulations. In 2025, rapid changes in AI and data privacy laws mean reviews are needed more frequently.
Who should write or review a company’s security policies?
A subject matter expert with compliance and technical knowledge. Many SMBs rely on vCISO services or MSSPs like Rhymetec to ensure policies are tailored to industry risks and compliance frameworks.
How can small businesses make policies easier for employees to follow?
Keep language clear and non-technical, integrate policies into training, and connect them to real-world examples like phishing or ransomware incidents. Policies that are simple to understand are more likely to be followed.
Do security policies help with compliance certifications?
Yes. Well-documented policies form the backbone of compliance efforts for frameworks like SOC 2, ISO 27001, HIPAA, GDPR, and CMMC. They are often the first thing auditors request when evaluating a company’s security posture. As part of Rhymetec's Vanta Compliance Services, we can leverage cutting-edge compliance automation technologies like Vanta to accelerate this process for you. We enable our clients to maximize their use of compliance automation platforms like Vanta and Drata.
About Rhymetec
Rhymetec was founded in 2015 as a Penetration Testing company. Since then, we have served hundreds of SaaS businesses globally in all their cybersecurity, compliance, and data privacy needs. We're industry leaders in cloud security, and our custom services align with the specific needs of your business.

About Kyle Jones: Information Security Manager at Rhymetec
Kyle Jones is a Senior Cybersecurity Analyst at Rhymetec. Kyle is an experienced cybersecurity and compliance professional who excels at aligning SaaS cloud architecture with industry standards and regulations. If you have any questions about security, you can get in touch with Kyle on LinkedIn or contact our team at Rhymetec.
Partnering with a Managed Security Services Provider (MSSP) is an elegant solution for many companies for two main reasons:
- MSSPs provide specialized experience at scale, enabling organizations to access expert security services without having to build in-house security teams.
- Companies of all sizes are increasingly recognizing that good security is good business.
Cybersecurity and information technology risks continue to shift more rapidly than ever. Organizations of all sizes are coming under increasing regulatory scrutiny both in the United States and the European Union, with new requirements such as the U.S. SEC Data Breach rule and the EU's NIS2 Directive, as well as upcoming regulations like the Digital Operational Resilience Act (DORA) requirements in Europe and CMMC 2.0 in the U.S. defense sector.
In 2025, enterprise buyers are also raising the bar with stricter vendor due diligence and security questionnaire requirements. At the same time, a vast cybercrime underground continues to flourish, amplifying the ever-present threats of ransomware attacks, data breaches, and insider threats.
But even beyond these well-known risks, having a solid information security foundation is just good business. It inspires confidence with partners, vendors, customers, and employees. Even more than that, it enables organizations to scale effectively without the omnipresent threat of ransomware attacks, data breaches, and compliance violations.
Good security is good business.
What is a Managed Security Services Provider?
Managed Security Services Providers (MSSPs) provide outsourced cybersecurity and consulting services to businesses of all sizes, providing an elegant and simple solution for organizations to reduce the risk of both regulatory noncompliance and experiencing a threat actor attack. Common services provided include incident response, endpoint protection, threat intelligence, patch management, risk management, security questionnaire fulfillment, compliance management, and much more.
MSSPs centralize decades of security experience across different functions and organizations into a single entity, enabling small businesses to leverage security know-how and experience usually reserved for the world's largest and most sophisticated corporations.
Why Organizations Are Turning to MSSPs in 2025
Business drivers in 2025 include:
Expansion into regulated markets (e.g., finance, healthcare, SaaS)
Scaling globally, especially into Europe under NIS2 and DORA
Meeting stricter third-party vendor risk assessments from enterprise buyers
Preparing for CMMC 2.0 certification in the U.S. defense sector
This is why MSSPs like Rhymetec, now serving over 1,000 clients worldwide, are seeing increased demand from SaaS companies, startups, and enterprises alike.
Indeed, MSSPs help organizations work through a variety of complex technical and regulatory challenges, including:
Compliance Frameworks and Regulatory Requirements
Compliance requirements continue to proliferate adding additional regulatory impetus for organizations to improve their cybersecurity.
That's one of the reasons why Managed Security Services Providers with extensive experience helping organizations meet a range of frameworks (such as SOC 2, ISO 27001, PCI DSS, FedRAMP, GDPR, and others) are increasingly seen as the best route to go to meet requirements. In 2025, new frameworks like ISO 42001 (AI Management Systems) are also becoming relevant for companies building or deploying AI, and the EU AI Act is introducing additional oversight.
Many organizations see regulatory requirements as purely a cost. However, collaborating with the right MSSP company can help transform these requirements into a net benefit that can be applied across the organization.

There's a reason that 75% of companies who achieve some level of continuous compliance view their compliance program as a business driver. Meeting regulatory and voluntary standards boosts your ability to serve more clients, unblock sales, and expand into additional markets.
And in 2025, CMMC 2.0 compliance is becoming a key requirement for U.S. defense contractors, making MSSP expertise essential for entry into that market.
Enterprise sales opportunities will want to see compliance with regulations relevant to their industry such as SOC 2, GDPR, HIPAA, and PCI before even considering an engagement. Working with an MSSP simplifies the process of achieving and maintaining compliance standards, ensuring you are able to break into new marketplaces as your company grows.
Penetration Testing
It's no secret that the threat landscape continues to drive higher levels of risk.
Increases in geopolitical tension, growth in cybercrime, and the rapidly evolving risk of ransomware attacks all directly increase risk to organizations. Penetration testing can directly reduce much of this risk.
Currently, another issue is that AI-powered attack tools and supply chain exploits are also creating new levels of exposure for SaaS companies. Through partnerships with leading platforms like XBOW, at Rhymetec, we now combine automation with human-led oversight to scale testing more effectively.
Similar to the importance of continuous compliance discussed above, when exploring how to select the right pen testing vendor, companies should consider the importance of continuous communication and a collaborative approach with the pen tester.
A good pen testing firm will work with you to scope the pen test to your organization's specific requirements and risks. For example, organizations that offer their data via API may benefit from API penetration testing while organizations with web applications may need pen testing specifically scoped to address common vulnerabilities in web applications.
A rigorous penetration test can identify flaws in your application or corporate security that an attacker could exploit. In addition, they can strengthen your compliance posture and reassure potential auditors that your organization takes security seriously.
An MSSP that offers pen testing as a service will collaborate with you to understand your business requirements and scope the pen test to vulnerabilities that threat actors are most likely to exploit based on your unique risk posture. For example, Rhymetec offers a variety of pen testing engagements, including web application, API, network, and mobile application pen testing.
Virtual CISO Services
Security isn't a one-time initiative. It's an evolving process that requires buy-in from individuals across the organization.
Virtual CISO (vCISO) services serve as the linchpin of a security program. A vCISO acts as your organization's security expert - enabling you to leverage executive security expertise without the need to employ a full-time CISO.
A vCISO can advise you on:
- When to make additional security investments
- Which security policies and procedures would most benefit your organization
- Emerging threats that may pose a risk to your business
- Maintaining robust security throughout complex engagements like cloud migrations
- Upcoming changes to compliance regulations that may need to be addressed
- Preparing you for compliance or data privacy audits
A good vCISO has an in-depth understanding of compliance requirements, coupled with the technical resources needed to implement security controls in the context of the threat landscape. Managed Security Services offering a vCISO service provide companies of all sizes access to this valuable combination of skills.
In addition, a vCISO enables you to maintain a posture of continuous compliance.
Working With A Managed Security Services Provider Encourages Continuous Compliance
At Rhymetec, we believe compliance shouldn't be a sprint right before an audit.
Organizations that make compliance core to their business can maintain a posture of constant compliance, reducing the stress and overhead associated with compliance while also ensuring that audit requirements are met.
A common misconception is that smaller businesses are exempt in some way from needing to meet requirements. However, requirements are generally stipulated across the board for most companies regardless of size.
Going beyond compliance frameworks, which represent a reasonable baseline but fall far from the finish line compared to an actual security program, vCISOs are able to implement additional security controls based on the unique risks an organization faces. Before building out or improving upon an existing security program, a vCISO will consider customer requirements and pinpoint specific laws and threats that apply to an organization and its vendors.
Opting for a vCISO service enables small and mid-size businesses to be certain they meet compliance standards while also leveraging their security dollars to reduce the risk of data breaches and ransomware attacks.
Let's expand on the main reasons why managed security services are an agile solution for smaller organizations:
Why Work With A Managed Security Services Provider? Specialized Experience At Scale.
The reason organizations choose to work with MSSPs is simple - specialized experience at scale. An average MSSP will often have experts on their team across many disciplines to include:
- Job Title (Salary range for an in-house full-time hire in 2025)
- CISO ($215,000 - $275,000 per year)
- Director of Security ($250,000 - $400,000 per year)
- Cloud Security Specialist ($110,000 - $150,000 per year)
- Application Security Specialist ($130,000 - $180,000 per year)
- Penetration Tester ($110,000 - $150,000 per year)
- Security Operations Analyst ($110,000 - $160,000 per year)
- Threat Intelligence Analyst ($80,000 - $140,000 per year)
- Governance, Risk and Compliance Specialist ($65,000 - $100,000 per year)
- Vulnerability Management Analyst ($100,000 - $165,000 per year)
Large enterprises spend millions of dollars on a security team with many highly specialized individuals across a range of disciplines. Small businesses need the same level of experience but not necessarily the same amount of work. Managed Security Services fill this gap perfectly.
Why Managed Security Services? It's Good Business.
Organizations are increasingly scrutinizing their vendors for security practices.
Suffering a major breach leaves a company scrambling to notify consumers, reassure investors, and manage employee fears. Proactively tackling cybersecurity, compliance, and data privacy by getting your SOC 2 Report (or other compliance audits), engaging in routine penetration testing, and utilizing vCISO services can serve as an amplifier across the rest of your business activities.
Having an MSSP as a continuous resource also simply provides peace of mind. When compliance frameworks are inevitably updated, when an auditor requests an evaluation of third-party risk, when you need things like phishing testing services to fulfill controls, or when you receive a security questionnaire from a customer - you'll know where to go for immediate and expert assistance.
Proactively providing SOC 2 Type 2 Reports to potential customers immediately makes your business stand out while also preventing the need for time-consuming security questionnaires. A vCISO service can help your organization identify and prepare for upcoming compliance regulations, saving costs and time in the long run.
Finally, working with an MSSP lets you leverage talent from across a variety of disciplines without the need to build large in-house teams.
Exploring Managed Security Services?
Rhymetec was founded in 2015 as a Penetration Testing company. Since then, we have served thousands of businesses globally in all their cybersecurity, compliance, and data privacy needs. We're industry leaders in cloud security, and our custom services align with the specific needs of your business. We help organizations achieve certifications like SOC 2, ISO 27001, HIPAA, and CMMC while preparing them for the evolving regulatory landscape in both the U.S. and Europe.
To learn more about our offerings and how a Managed Security Services Provider can be an accelerator for your business, contact our team for more information.
FAQs
Why choose managed security services instead of in-house security in 2025?
The demands of compliance and cybersecurity have outpaced what most in-house teams can manage. Managed security services provide access to expert resources, 24/7 monitoring, and full compliance management at a lower cost than building your own team. In 2025, when vendor due diligence and regulatory expectations are stricter than ever, MSSPs give businesses a faster and more reliable way to stay secure and audit-ready.
What is the cost difference between managed security services and hiring in-house?
Hiring a complete in-house security team can cost millions annually, with salaries for CISOs, penetration testers, and compliance specialists ranging from $80K to $275K each. Managed security services let you access the same breadth of expertise on a fractional basis. This approach delivers enterprise-grade protection and compliance readiness without the overhead of staffing a full team.
How do managed security services help with compliance like SOC 2 or CMMC 2.0?
MSSPs guide companies through the full compliance journey. We design policies, implement controls, maintain readiness, and support you through audits. Our team helps organizations meet frameworks such as SOC 2, ISO 27001, HIPAA, GDPR, FedRAMP, and CMMC 2.0. By outsourcing compliance management, businesses expand into new markets and shorten audit timelines, often achieving compliance in one-third of the expected time.
Can managed security services prepare businesses for AI regulations and new laws?
Yes. In 2025, MSSPs are helping organizations align with emerging frameworks like ISO 42001 (AI Management Systems - see our ISO 42001 Checklist for more info), EU AI Act compliance, and stricter privacy and disclosure requirements. By keeping you ahead of regulatory shifts, MSSPs make sure your business avoids gaps, reduces legal exposure, and can adopt AI securely while meeting compliance expectations.
How do managed security services reduce risk for growing businesses?
MSSPs combine continuous monitoring, penetration testing, vCISO leadership, and risk management to reduce the likelihood of breaches or compliance failures. This proactive approach protects your data and strengthens customer trust. For growing businesses, demonstrating strong security and continuous compliance can also shorten sales cycles by removing barriers during vendor assessments.

About the Author: Justin Rende, CEO
Justin Rende has been providing comprehensive and customizable technology solutions around the globe since 2001. In 2015 he founded Rhymetec with the mission to reduce the complexities of cloud security and make cutting-edge cybersecurity services available to SaaS-based startups. Under Justin's leadership, Rhymetec has redesigned infosec and data privacy compliance programs for the modern SaaS-based company and established itself as a leader in cloud security services.
Companies across every industry depend more and more on technology to run their businesses, store sensitive data, and carry out essential operations. With the rise in cybersecurity threats and tough technology regulations, organizations must have a robust security plan to meet IT compliance standards. However, since no two companies are the same, and every business has unique needs, a one-size-fits-all compliance plan is not enough to establish a compliant and effective information security program.
The Current Threat Landscape
Organizations using digital technology and cloud software face a complex threat landscape that grows increasingly sophisticated. Ransomware attacks, phishing attacks that attempt to trick people into sharing sensitive data, advanced persistent threats (APTs), and well-funded, determined attackers all target companies to steal intellectual property or disrupt operations.
Then there's the explosion in connected IoT devices, standing at 15.14 billion as of 2023, and the high risk of DDoS attacks. With individual cyber breaches costing upwards of US$4.35 million, failure of a one-size-fits-all solution can be dangerous and expensive.
Generic Compliance Plan Pitfalls
IT departments these days use many different architectures with various hardware, software, and network configurations. Because of these differences, it's difficult to create a single cybersecurity formula that works for all companies. Some of the pitfalls of trying to cut corners and save costs by implementing a generic plan include:
- Lack of customization: A one-size-fits-all approach doesn't consider the specific problems and needs of each company. What works for one organization may not be enough to address the weaknesses and particular requirements of the next. It's important to customize security measures to fit the unique characteristics of each company to effectively protect against cyber threats.
- Increased risk of breaches: When companies use a standardized compliance plan, it sets a basic level of security. However, this plan might not take into account the specific risks and security gaps that exist in each organization. Without customized security measures, a greater chance exists of experiencing data breaches or cyberattacks.
- Higher chance of vulnerabilities: Cybercriminals take advantage of vulnerabilities that are often not addressed in a generic security plan. In the past, we have seen the severe consequences of inadequate security measures. Well-known breaches caused by a lack of tailored security have resulted in large-scale data leaks, compromised customer information, and significant financial losses for companies.
To keep your data safe, protect against cyberattacks, build trust with customers, and combat the potential risks and consequences of non-compliance, you need a plan tailored for your organization.
The Cost of Corner-Cutting
Few young companies are equipped to handle and overcome the financial and business losses following an attack. The direct costs can be considerable, including legal proceedings, recovering lost data, and repairing damage to the company's reputation. Fines, penalties, and legal settlements can reach millions of dollars. Restoring compromised systems, conducting investigations, and enhancing security measures add to the expenses.
A cybersecurity incident can also seriously disrupt your company operations, resulting in downtime and lost productivity. Systems can become inaccessible, affecting critical tasks and leading to delays or disruptions in operations. Additionally, a breach damages the trust and loyalty of customers, which can cause the company to lose revenue and harm its reputation in the long run.
Advantages of a Human-Centric Approach
In many cybersecurity incidents, human error plays a significant role. According to Verizon's 2022 Data Breaches Investigations Report, 82% of data breaches involved a human element. From being victims of phishing scams to using weak passwords, employees accidentally create vulnerabilities that cyber attackers take advantage of. By adopting a human-centric approach, organizations (especially startups) can establish a strong defense and create a culture where everyone in the company values security. To achieve this, your company must:
1. Invest in education
A human-centric approach propels your organization to provide thorough training that creates a culture of cybersecurity awareness. Education empowers your employees to recognize and handle suspicious emails, avoid clicking on harmful links, and use safe practices when dealing with sensitive information.
2. Keep employees informed
When employees are kept informed about the latest threats and know how to protect company assets, they feel responsible for protecting the company's digital assets. By tailoring your training to address the specific risks employees face and keeping them up to date, your workers become the first line of defense against potential attacks.
3. Empower proactive defense
Companies that recognize a human focus is crucial for quality cybersecurity goals equips employees with the knowledge and skills to prevent cyber incidents proactively. This helps them to successfully reduce the number of threats unique to their industry or work environment.
Tailor Compliance Plans to Meet Organizational Needs
Customizing security and compliance to match your company's unique environment brings several benefits. It allows you to address the specific vulnerabilities and risks that apply to your operations. It lets you focus your resources on the most critical areas and ensures your security efforts are efficient and effective.
Customization also ensures that your security measures align with your company's goals, values, and compliance requirements, putting you in a stronger position to resist cyber threats. By considering factors like the types of data you handle, your IT infrastructure, and the skills of your workforce, you can develop a security approach that is targeted and relevant to your specific situation.
A human-centric compliance and cybersecurity program integrating technology and employee involvement gives you a holistic and robust defense against cyber threats.
You can read the original article posted in Forbes by Rhymetec CEO, Justin Rende.
Need custom cybersecurity and compliance solutions?
Hire a vCISO with years of experience in cloud security at a fraction of the cost of hiring a full-time CISO in-house. Rhymetec’s custom vCISO services adapt to your organization’s cybersecurity and compliance needs and scale as you grow over time. Providing executive-level security leadership, a dedicated Rhymetec vCISO can assess your organization’s cyber risk, develop an internal InfoSec Program, and assist in the compliance and security needs that align with your business.
Interested in reading more? Check out our blog: