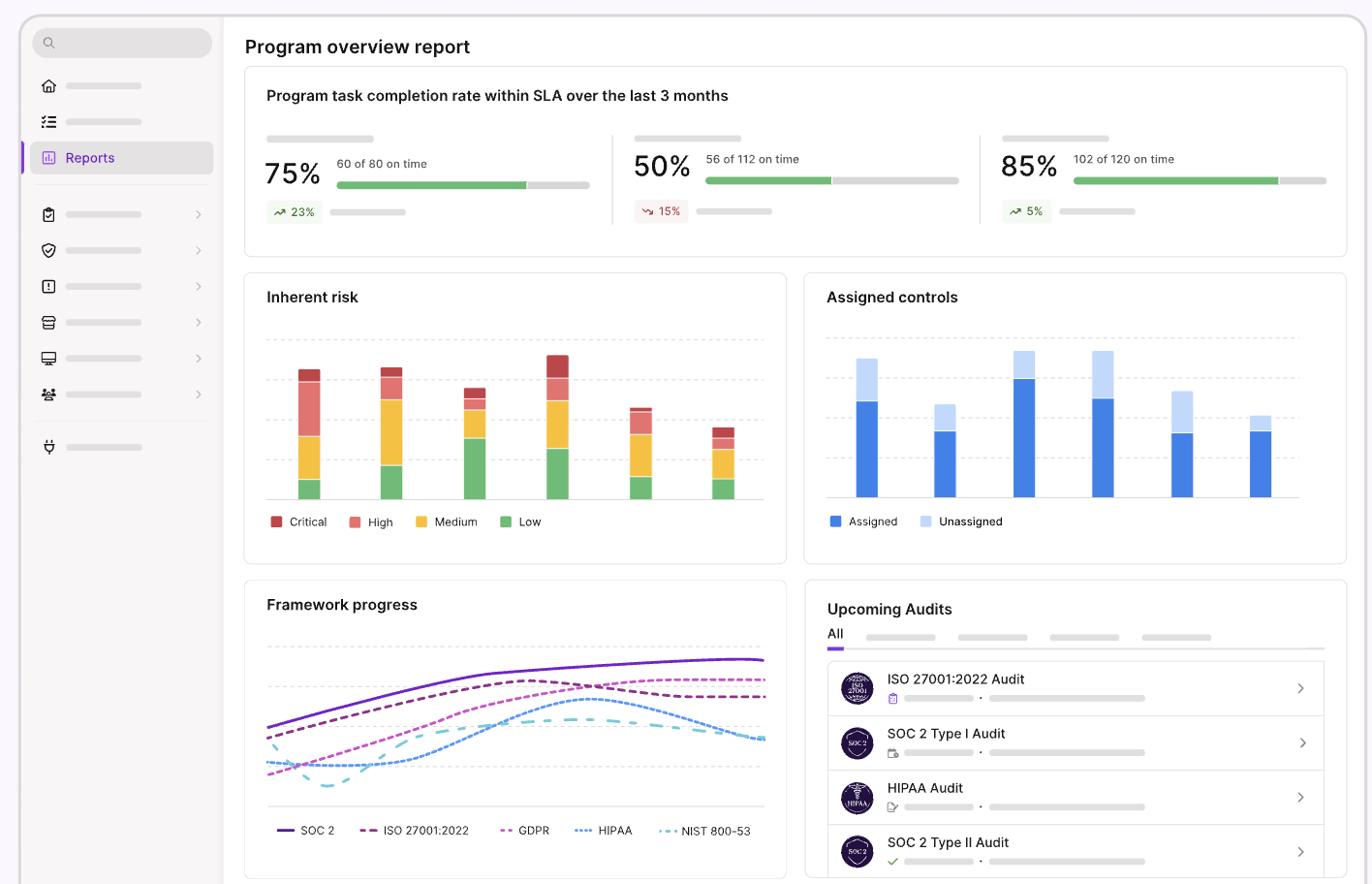
So, you're considering SOC 2 or ISO 27001 for the first time - and realizing just how much time and expertise it takes to actually get there. That's where Vanta (and Rhymetec!) comes in:
Vanta automates 90% of compliance monitoring through integrations with 300+ systems, real-time control insights, and automated evidence collection—enhancing your visibility into your security posture. Rhymetec handles the hands-on readiness tasks for you. The combination of Vanta with our tailored services delivers a faster, more manageable path to audit success.
Our team of experts at Rhymetec, by leveraging Vanta for you, accelerates every step of your compliance journey from the initial scoping phase to auditor handoff. We've helped over 1,000 organizations efficiently meet their security and compliance goals with this method. Here's how Vanta works in conjunction with our services, and how the platform can benefit you immediately, especially if you are early on in the process of compliance:
Vanta Automates Compliance Workflows
Vanta automates the visibility into tasks required to build a compliance program. One of the main value adds of Vanta is that it will handle the repetitive work for you and give you back your time to focus on what really matters - growing your business. Here's how it works, particularly for organizations early in their compliance journey:
Using Vanta circumvents the need to even get started on tedious manual spreadsheets and checklists. Instead, Vanta enables organizations to jump right in and leverage its capabilities, including system integrations and automated collection of evidence.
For instance, a startup pursuing SOC 2 may need to prove that it restricts employee access to production systems, monitors for security incidents, and keeps its asset inventory up-to-date and in line with SOC 2 requirements. Vanta connects to systems including AWS, GitHub, Google Workspace, and Okta to automatically accomplish the following:
- Display passing controls.
- Simplify policy management.
- Collect the evidence needed for an audit.
It also includes pre-built policy templates for every framework, so teams can work from a baseline and avoid having to write everything from scratch. Leadership is able to track compliance status in real time and improve visibility tied to audit preparation for employees—resulting in efficiency and reduced time to compliance.
Who Uses Vanta And Why
Vanta is primarily used by fast-growing, cloud-native organizations that are seeking to meet relevant security and data privacy requirements in the most efficient way possible. Often, these organizations are trying to avoid dedicating excessive internal resources to manual compliance work. However, we’ve seen companies from all sizes—startup to enterprise—with varying environments—such as multi-cloud and hybrid—utilize Vanta to streamline their compliance efforts.
Some of the main reasons companies opt to use Vanta are to help them:
- Reduce their audit timelines.
- Improve visibility into their security posture.
- Lower the overall cost of compliance.
Vanta connects to the tools you use via API, the cloud infrastructure you're set up in, and your internal systems to give you a complete view of your security and compliance.
This eliminates the need for fragmented spreadsheets and manual checklists, providing leadership more control over compliance progress and unburdening technical teams that are already stretched thin.
Another core value add is that Vanta enables a single source of truth for audit readiness, helping leaders and your sales team demonstrate you're where you need to be in terms of security and compliance to auditors, customers, your partners, and other stakeholders.
What Does Vanta Do? Vanta Supports Continuous Compliance
It's important to know going into your compliance journey that compliance doesn’t stop after one audit.
Frameworks like SOC 2, ISO 27001, and HIPAA require ongoing evidence of control effectiveness, which means you need continuous monitoring rather than only point-in-time documentation.
Vanta is built precisely to support this model. It runs in the background, constantly monitoring your infrastructure and systems for changes that could impact compliance. It will flag any issues in real time, such as expired access, unapproved software, or missing security training. The platform centralizes the evidence you'll need to show controls are operating continuously.
This approach replaces manual check-ins and periodic reviews with continuous visibility. Combined with Rhymetec's guidance and remediation support, clients stay audit-ready year-round without having to rebuild compliance work from scratch each cycle.
Vanta Streamlines The Work of Cybersecurity & Compliance Experts
Vanta automates the visibility into tasks (While Rhymetec can support the completion of them) that are most likely to slow down compliance teams, allowing the experts to focus on higher-impact and more specific work. Tasks like collecting screenshots, tracking evidence, and managing spreadsheets shift to automated processes within the platform.
For Rhymetec's team, the platform provides a centralized source of truth and allows us to spend more time analyzing results and guiding clients through control implementation. Our team uses Vanta in every step of the compliance automation process on your behalf. By handling repetitive tasks and bringing issues to our attention automatically, Vanta allows us to carry out a more efficient process to compliance readiness for your organization.
How Rhymetec Leverages Vanta To Deliver Compliance - Fast
Rhymetec leverages Vanta as a core part of our compliance delivery model.
Our approach combines all of the benefits of automation with hands-on cybersecurity expertise to shorten the path to audit readiness. Our team configures Vanta for your systems and selected framework. We work hard to eliminate common setup delays and create alignment between compliance goals and actual business operations.
Once deployed, Vanta automatically monitors your cloud infrastructure and systems for compliance-related activities. But automation alone doesn’t get you audit-ready. That’s where Rhymetec comes in. After the initial setup, our team steps in to:
- Interpret and prioritize Vanta’s findings based on your unique business needs
- Remediate flagged issues with hands-on support — not just advice
- Tackle all remaining manual components like policy creation, access reviews, evidence collection, and control implementation
The combination of automated and manual work keeps the momentum going and gets clients through readiness assessments and audits on a much faster timeframe. By managing both Vanta and the 'hands-on' components of compliance readiness work on your behalf, we’re able to accelerate every phase of the compliance process.
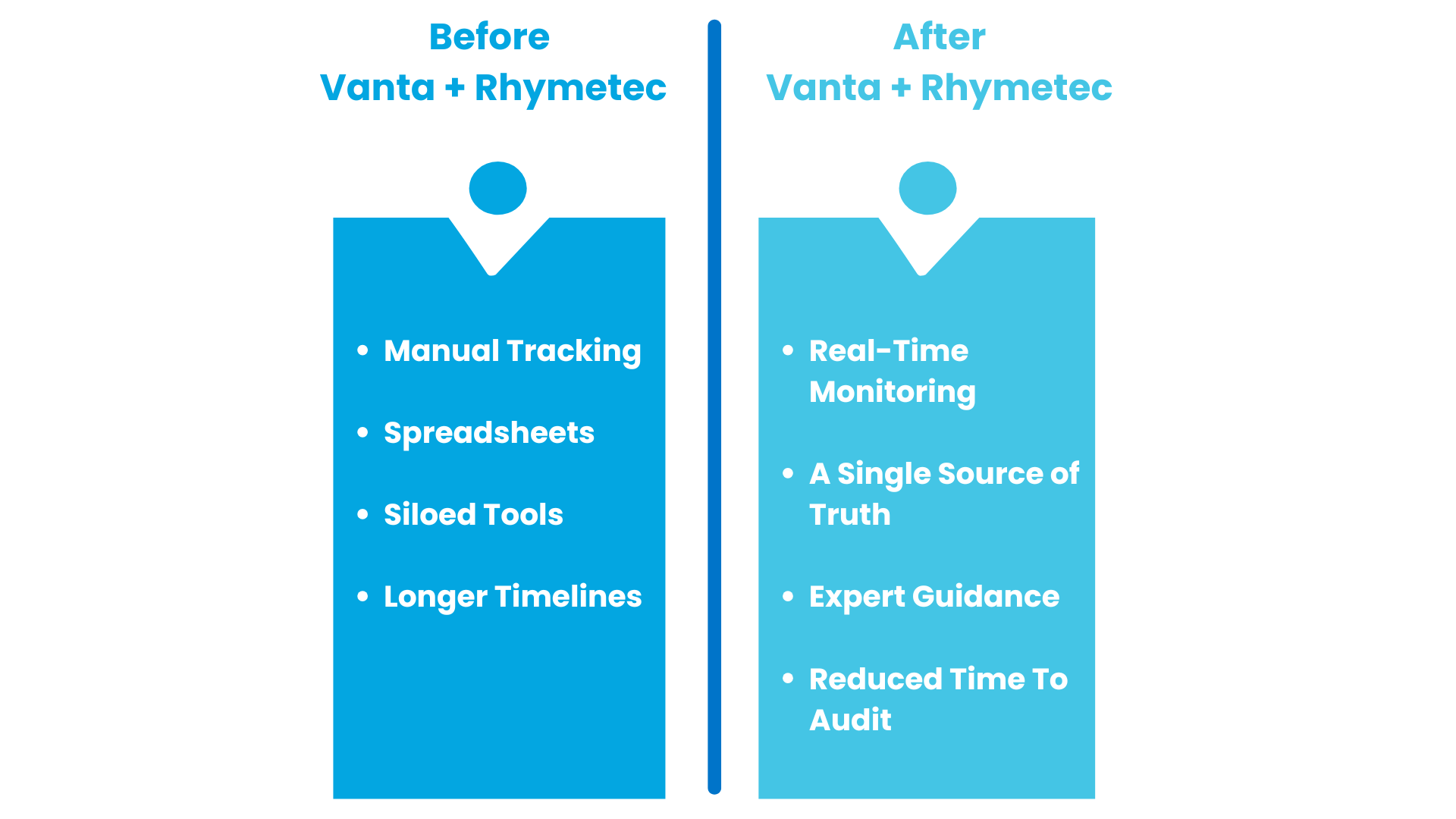
Why Pairing Vanta and Rhymetec Delivers Better Outcomes
Most frameworks require an array of expert judgment, manual implementation of certain controls, and a level of preparation that automation can't complete 100% of on its own.
Rhymetec fills that gap by managing the manual work and aligning Vanta specifically to your environment. We interpret control requirements, resolve flagged issues, write custom policies, manage communication with auditors on your behalf, and more.
By using Vanta for compliance automation - and Rhymetec filling in the gaps for you when needed - clients move faster and meet their compliance goals with less internal burden. Together, we consistently generate strong audit readiness and stronger security programs.
Accessing Vanta Through Rhymetec
Rhymetec is proud to offer Vanta (in conjunction with our Vanta compliance services) directly to clients who haven't yet selected a compliance automation platform.
Particularly in the case of clients early in their compliance journey, this vastly simplifies the buying process by providing both the technology and the services needed to meet requirements in one engagement. We give clients access to a world-class platform without requiring them to manage separate vendor relationships or navigate pricing and setup alone.
Our team at Rhymetec handles everything from the initial deployment and setup in Vanta to ongoing administration of the platform on your behalf. This allows you to adopt automation earlier, which will accelerate your compliance timelines and help you avoid missteps that a self-directed rollout could entail. Contact our team to learn more:
SOC 2 policies are formal guidelines that organizations implement to comply with SOC 2, which sets forth measures to securely manage customer data based on five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy.
These policies and procedures outline how an organization secures data, controls access, responds to incidents, and maintains compliance through regular audits and risk assessments. Effective SOC 2 compliance not only aids in risk mitigation but also serves as a business enabler, allowing you to be more confident in the efficacy of your information security program and sell to a broader array of prospects.
In this article, we will review specific examples of SOC 2 policies and provide tips from the experts on how to write them for your organization.
If you have more specific questions, please feel free to contact our team:
How Do I Write SOC 2 Policies and Procedures?
Some good news first: SOC 2 doesn't provide specific policy or timeline guidelines in many areas. Organizations have a lot of leeway to select and tailor policies internally and set their own timelines.
This can be both a pro and a con, however. Due to the flexibility of SOC 2, there's actually a risk of doing too much. Policies often don't need to be overly stringent. It's about what works for the business, and policies should be created with that in mind.

For instance, you could have a policy to remediate critical vulnerabilities within x # of days. SOC 2 doesn't have guidelines around that timeline, which gives organizations the ability to set rules that align with realistic business operations. Compared to other standards, SOC 2 offers a greater degree of flexibility in drafting your policies and procedures.
In our latest webinar, Rhymetec CISO Metin Kortak spoke to Craig Saldanha from auditing firm Insight Assurance about how organizations can streamline SOC 2 compliance and navigate the 5 SOC 2 Trust Services Criteria.
"An area of weakness we often see is the termination SLAs," noted Craig when asked which SOC 2 measures organizations are most commonly weak on when getting audited. "Sometimes organizations just write these policies too stringently."
So, how should my policies look, and how can we prevent them from being overly onerous?
As suggested by the experts themselves in our webinar, here is a 6-step process to build out SOC 2 policies that work for your business:
How To Make SOC 2 Policies Work For Your Business
1. Choose and familiarize yourself with which Trust Services Criteria (TSC) your business is going to be doing.
Apart from the Security criteria, which is mandatory for every SOC 2 audit, you can choose which of the 5 TSCs to include in your SOC 2 audit.
Start by understanding the requirements under each one, and select the criteria that are most relevant to your business operations and compliance goals. A company offering cloud services may include Availability and Confidentiality in addition to Security to show that their service is not only secure but also reliable and protects sensitive information.
Risk assessments should also drive your selection of TSCs. If you have customers who are concerned about a product or service up-time, this may drive the inclusion of Availability as customers want some assurance around your uptime and availability. If the organization has identified a risk around data classification and retention, that may prompt Confidentiality to be included.
2. Identify your organization's needs through an assessment of current processes and systems to pinpoint where policies are needed.
This gap analysis should identify areas where you are falling short of SOC 2 requirements.
Using compliance automation tools at this stage can streamline the gap analysis process. These tools show real-time insights into where your current processes deviate from SOC 2 requirements and provide a centralized place to track everything.
3. Collaborate with stakeholders from IT, security, legal, and HR.
Gather input and ensure buy-in across the organization. Organize workshops with key stakeholders to discuss the findings of the gap analysis in Step 2, and gather their insights on remediation.
4. Develop clear SOC 2 policies & procedures.
Create detailed documents that outline the controls your organization will implement. Policies should be written in clear, concise language that is accessible to all employees.
If you work in tech, it may seem evident to you what the policy means when it says:
"Multi-factor authentication must be enforced for all user accounts accessing the corporate network, using a combination of at least two forms of authentication, such as a password and a time-based one-time password (TOTP) generated by an authenticator app."
But this is probably unclear to most employees. It's better to make a policy like the following (and show employees exactly how to use MFA as part of their training):
"All employees must use two steps to log into the company's network, such as a password and a code from a phone app."
5. Provide training on policies and ensure that employees understand their role in the compliance environment.
Use a variety of training methods such as workshops, e-learning modules, and hands-on exercises. Don't just tell people what to do. Show them why it matters and they'll be more likely to remember.
6. Conduct internal audits and update your SOC 2 policies as needed to reflect changes in regulations, emerging threats, and your environment.
A regular schedule of internal audits to assess compliance with policies and identify areas for improvement enables you to remain compliant with SOC 2 over time.
Next, let's go over some of the most common SOC 2 policies and procedures to give you an idea of what these policies may actually look like:

What Are Some Examples of SOC 2 Policies and Procedures?
The examples below are common policies organizations use to meet the requirements of SOC 2:
Access Control Policies
Access control policies specify the procedures for granting, modifying, and revoking access to the organization's systems and data. Your policy may say something like:
All user access to the company's internal systems must be based on the principle of least privilege and approved by the department. Employees must submit an access request form that includes the systems and applications required, the justification for access, and the duration for which access is needed. Approved requests are to be forwarded to the IT security team. Access reviews are conducted quarterly to ensure that only authorized personnel have access to sensitive systems and that any changes are logged and reviewed.
Incident Response Policies
An incident response policy outlines the steps to take when a security incident occurs. Procedures include the identification and reporting of incidents, the assignment of incident response team members, and the classification of incidents based on severity. At a high level, your incident response policy could look something like the following:
Employees must report any suspected security incidents to the security team immediately using the incident reporting form. The incident response team assesses the reported incident to determine its severity and impact within one hour. For high-severity incidents, the team isolates affected systems to prevent further damage by disconnecting impacted systems from the network and changing access credentials.
Measures are enacted to mitigate the impact, such as patching vulnerabilities or restoring from backups. Within two weeks of resolving the incident, a post-incident review will document lessons learned and update the plan as needed.
Data Encryption Policy
This policy mandates the encryption of data at rest and in transit and specifies the encryption standards to be used. Policies should require the use of encryption keys, regular rotation of keys, and secure key storage solutions:
Sensitive data stored on company servers must be encrypted using AES-256 encryption. The encryption keys must be stored in a hardware security module managed by the IT security team. All data transmitted over the company network (including emails, file transfers, and API communications) must be encrypted using TLS 1.2 or higher.
Encryption keys must be rotated every 90 days, and the security team must document rotations. Quarterly audits should be done to verify that encryption mechanisms are working. Areas for remediation must be documented and addressed within 5 business days.
Change Management SOC 2 Policies
This policy governs how changes to IT systems and applications are managed to minimize disruption while maintaining security. Procedures typically include the following:
All changes to IT systems and applications must follow defined change management procedures: All change requests must include a detailed description of the change, expected impact, rollback procedures, and testing plans. IT managers and security personnel approve or reject requests during weekly meetings.
The changes are implemented in maintenance windows to minimize disruption to business operations. Change implementation must be logged, and a post-implementation review is to be carried out within one week.
Vendor Management SOC 2 Policies
Vendor management is an extremely critical area under SOC 2 policies.
These policies outline how third-party vendors are evaluated and monitored to make sure they meet security requirements. This involves a vendor risk assessment process, requiring vendors to provide SOC 2 reports or equivalent evidence of their security program. As an example:
Before engaging with a new vendor, a risk assessment using the Vendor Risk Assessment Questionnaire must be completed. The strength of the vendor's security program should be assessed by reviewing their responses to the questionnaire as well as their SOC 2 report or equivalent certification. Contractual obligations are to include specific security requirements, such as the obligation to notify the company of any data breaches within 24 hours and compliance with industry standards.
Annual reviews (including requesting updated security certifications) are to be conducted to assess vendors' security practices. Any deviations from agreed-upon practices must be documented and corrected within 30 days. If a vendor fails to meet requirements, a termination procedure is to be carried out that ensures a smooth transition and protects company data during the process.

Which SOC 2 Policies And Procedures Are Companies Most Commonly Weak On When Getting Audited?
"I think a lot of companies forget to include the fraud component within their risk assessment, which is part of the criteria within SOC 2," Craig Saldanha from auditing firm Insight Assurance noted in our SOC 2 webinar.
" Sometimes organizations just write these policies too stringently," Craig noted, mentioning termination SLAs as an area where he sees this happen frequently:
For example, their policy will require fully offboarding employees within 8 hours with all system access removed. There's no hard requirement that states you have to do it within 8 hours! You should draft your SOC 2 policies to cover all necessary areas while also considering what realistically works for the business.
The next component organizations are commonly weak on is vulnerability SLAs. "We see this as being an area of concern as well," said Craig. "A lot of people can't remediate those adequately because of resource or budgetary constraints. It's important to document this with business justifications."
There are many vulnerabilities on a daily basis, and being able to resolve all of them on time and create proper risk assessments around them is vital. Vulnerability remediation is a common challenge that can lead to exceptions.
What Is The Biggest Pain Point In Obtaining A SOC 2 Report?
"Number one would be understanding the requirements and identifying gaps," said Craig in our webinar. "It can feel like a scavenger hunt sometimes." Guidance from experts at the very beginning of your journey can be extremely helpful in developing a clear roadmap.
Ongoing maintenance is another one of the biggest pain points:
"A lot of customers don't understand that there is ongoing maintenance involved, and they actually need to allocate resources if they want to remain compliant over time," pointed out Rhymetec CISO Metin Kortak.
An example of an ongoing control is having employees undergo security awareness training (including regular phishing training for employees). This isn't something you do once during the observation and then stop. It has to be done on an ongoing basis.
Lastly, getting through the actual audit can be a challenge if you aren't adequately prepared. Finding a strong audit firm with solid communication can make all the difference.
About Rhymetec
Rhymetec was founded in 2015 as a Penetration Testing company. Since then, we have served hundreds of SaaS businesses globally in all their cybersecurity, compliance, and data privacy needs. We're industry leaders in cloud security, and our custom services align with the specific needs of your business. If you want to learn more about how our team can help your business with your security needs, contact our team for more information.
Check out our case studies to learn how our security team fast-tracked companies like Kizen and Solvvy to SOC 2 compliance and enabled them to shorten their sales cycle, increase trust with customers, and expand into new marketplaces.
Interested in reading more? Check out additional content on our blog:
- Cybersecurity for SMBs: 10 Key Measures and Statistics
- Security Questionnaire From A Customer? What To Expect and How To Answer
- The Misconception of Cost In Building An Information Security Program
A SOC 2 readiness assessment is an important first step if your organization is thinking about obtaining SOC 2 compliance. Think of the readiness assessment as a health check for your security practices - it's meant to help you get everything you need completed before the formal audit.
In this FAQ, we'll tackle some of the most common questions we hear about SOC 2 readiness assessments - why you might need one, what it costs, how long it takes, who should be involved, and more. This will give you a clear picture of what to expect and help you understand what your organization needs before undergoing an external audit.

What Is A SOC 2 Readiness Assessment?
A SOC 2 readiness assessment is a pre-audit process that helps organizations prepare for their official SOC 2 audit. It identifies gaps in your current security controls and SOC 2 policies and procedures compared to where you need to be.
The first step is to select an external consultant. Your consultant will conduct a thorough review of your existing security controls (security measures, documentation, operational procedures, and more) to identify areas where you may not be meeting SOC 2 standards.
The assessment entails several key benefits, allowing you to:
- Have a third-party opinion of your SOC 2 audit preparedness
- Pinpoint gaps and weaknesses in your existing controls
- Obtain ideas on how to strengthen your processes and procedures
Testing your current controls and finding areas where remediation is needed is important to do in preparation for your audit.
How Much Does A SOC 2 Readiness Assessment Cost?
The cost of a SOC 2 readiness assessment can vary. The following factors impact cost: Organization size, the complexity of your IT infrastructure, the consultant you work with, the Trust Services Criteria you selected, the use of project management or GRC tools, and other factors that vary from consultant to consultant.
Readiness assessment estimates start at around $7,000 - $15,000. For a small startup with a straightforward infrastructure, costs typically start at the lower end. For larger organizations or for those with complex systems, costs can increase significantly, potentially reaching tens of thousands of dollars.
Some firms offer fixed-price packages that bundle the SOC 2 readiness assessment into the overall cost of obtaining SOC 2 compliance. Others charge based on the time and resources required to complete the assessment. Obtaining detailed quotes from multiple providers can help you understand the potential costs for your organization.
How Long Does A SOC 2 Readiness Assessment Take?
The timeframe to complete a SOC 2 readiness assessment varies. For large organizations or for those with more complex IT environments, it can take anywhere from 1-4 weeks. For smaller organizations with less complex environments, it can take as little time as several days to a week.
During this period, key activities include evaluating your existing security controls, identifying any deficiencies, and creating a plan to address those gaps. Another factor that impacts the time frame is how quickly your organization can make changes and remediate gaps.
Who Should Be Involved From Your Team?
A SOC 2 readiness assessment requires involvement from several key members of your team. These typically include:
1. IT and Security Personnel, as they have the best understanding of your technical infrastructure and current security measures.
2. Compliance Officers (If Applicable): Whomever at your organization is responsible for ensuring adherence to regulatory and industry standards should be involved.
3. Operations Managers: Personnel who oversee the processes and controls related to daily business activities can help make sure daily operations adapt to and are impacted as little as possible by any new security measures.
4. HR Personnel can provide information on employee onboarding, training, and access controls.
5. Executive Leadership: Executives are responsible for allocating resources and ensuring changes to the organization's security posture are communicated down the line. (Note: An emphasis on the role of executive leadership and governance in cybersecurity is increasingly being seen across other cybersecurity standards, including under the recently added NIST governance function).
Involving all of these specialized roles allows you to speed things up and facilitates an effective assessment. Using compliance automation software can also help fast-track the process by providing a centralized location where all involved parties can access and track pertinent information.
Does Your Organization Need a SOC 2 Readiness Assessment?
Whether your organization needs a SOC 2 readiness assessment depends on your circumstances and goals. It's particularly useful if you're new to SOC 2 or if you have not previously undergone a SOC 2 audit. It serves to make the entire SOC 2 process easier, as assessments are highly tailored to your organization's unique needs.
Not every company should follow everything under the SOC 2 standard. Choosing the right Trust Services Criteria is an important step in your journey. A readiness assessment allows you to identify the security controls and practices that you actually need to implement.
Can You Fail A SOC 2 Readiness Assessment?
No, you cannot technically "fail" a SOC 2 readiness assessment. The assessment is a preparatory step that identifies gaps and recommends improvements before your formal audit. It serves as a diagnostic tool to help you understand which areas need to be addressed to meet SOC 2 requirements.
What Happens If Gaps Are Found During The Assessment?
If gaps are found it means your organization has some work to do before pursuing the official audit. That's the purpose of the readiness assessment: to highlight and correct issues in advance.
The controls you may need to remediate depend on which Trust Services Criteria you selected. For example, if you selected the Security Trust Services Criteria and are not currently conducting measures like regular phishing training for employees, you may need to implement stronger controls to protect against unauthorized access and disclosure of data.

Who Performs A SOC 2 Readiness Assessment?
The assessment is typically performed by experienced third-party firms that specialize in compliance and security audits. This includes:
1. Certified Public Accountants (CPAs) with IT specializations have the expertise needed to understand both the technical and compliance aspects of SOC 2.
2. IT Consulting Firms that focus on cybersecurity and compliance, and are experienced in assessing and improving IT controls.
3. Managed Security Service Providers (MSSPs) offer a range of security services and can conduct readiness assessments as part of their broader security offerings.
These options all provide an external expert perspective, enabling you to identify gaps and act on expert recommendations to effectively meet SOC 2 requirements.
What Are The Most Frequently Found Gaps In SOC 2 Readiness Assessments?
At Rhymetec, we have worked with hundreds of companies on their SOC 2 readiness. Some of the most common gaps we see companies have include the following:
1. Access Controls: We often see gaps related to inadequate controls over user access to systems and data. This includes weak password policies, lack of multi-factor authentication, and improper user permissions.
2. Security Monitoring: Many organizations lack up-to-par monitoring based on SOC 2 guidelines if this is an area they haven't previously paid much attention to. Under SOC 2 requirements, systems and networks should be monitored for suspicious activities or unauthorized access.
3. Data Protection: There is often room for improvement in areas like data encryption. Our security experts have helped many organizations improve their data backup and recovery procedures in preparation for their audit.
4. Vendor Management: A lot of organizations don't realize how much oversight of their third-party vendors and service providers is required under SOC 2. We help organizations identify any gaps in due diligence, contract management, and vendor review & risk assessments.
5. Incident Response: Organizations often need to create a documented incident response policy and accompanying procedures. At Rhymetec, we craft detailed incident response plans tailored to our clients’ individual industries and needs.

Addressing these common gaps is not only critical for achieving SOC 2 compliance, but also for better protecting your organization's (and end users') data and systems.
Interested in reading more on SOC 2? Check out additional content on our blog:
- SOC 2 Compliance Checklist
- SOC 2 Type 1 vs Type 2: Which Do You Need?
- Rhymetec's Complete SOC 2 Compliance Guide
About Rhymetec
Rhymetec was founded in 2015 as a Penetration Testing company. We offer a range of penetration testing services to include:
- Mobile Application Penetration Testing
- Web Application Penetration Testing
- External Network Penetration Testing
- API Penetration Testing
After seeing a gap for broader security support in the market, Rhymetec grew to offer managed compliance services for frameworks like SOC 2, ISO 27001, GDPR, CCPA, HIPAA, HITRUST, NIST and more. Since then, we have served hundreds of SaaS businesses globally in all their cybersecurity, compliance, and data privacy needs. We're industry leaders in cloud security, and our custom services align with the specific needs of your business. If you want to learn more about how our team can help your business with your security needs, contact our team for more information.
Companies often find that SOC 2 compliance acts as a business enabler, unblocking sales and allowing them to break into new marketplaces.
However, obstacles like resource constraints and a lack of in-house expertise make crossing the finish line with compliance a challenge, especially for small and mid-sized businesses.
Achieving compliance with standards like SOC 2 can seem like a daunting task. In our latest webinar, Rhymetec CISO Metin Kortak spoke to Craig Saldanha from Insight Assurance about how to simplify SOC 2 compliance and navigate the 5 SOC 2 Trust Services Criteria:

Check out the recording to watch their discussion. A bit about the speakers:
Metin Kortak started his career in IT security and then joined Rhymetec to build data privacy and managed compliance as a service offerings. Rhymetec started as a penetration testing firm in 2015, and under Metin's leadership, we've expanded to do all things security and compliance, with a focus on working with startups.
Craig Saldanha from Insight Assurance has nearly 10 years of audit experience. He's an expert in GRC and third-party/vendor risk management. In his current role at Insight Assurance, he leads and manages SOC 2, PCI, & vCISO service lines.
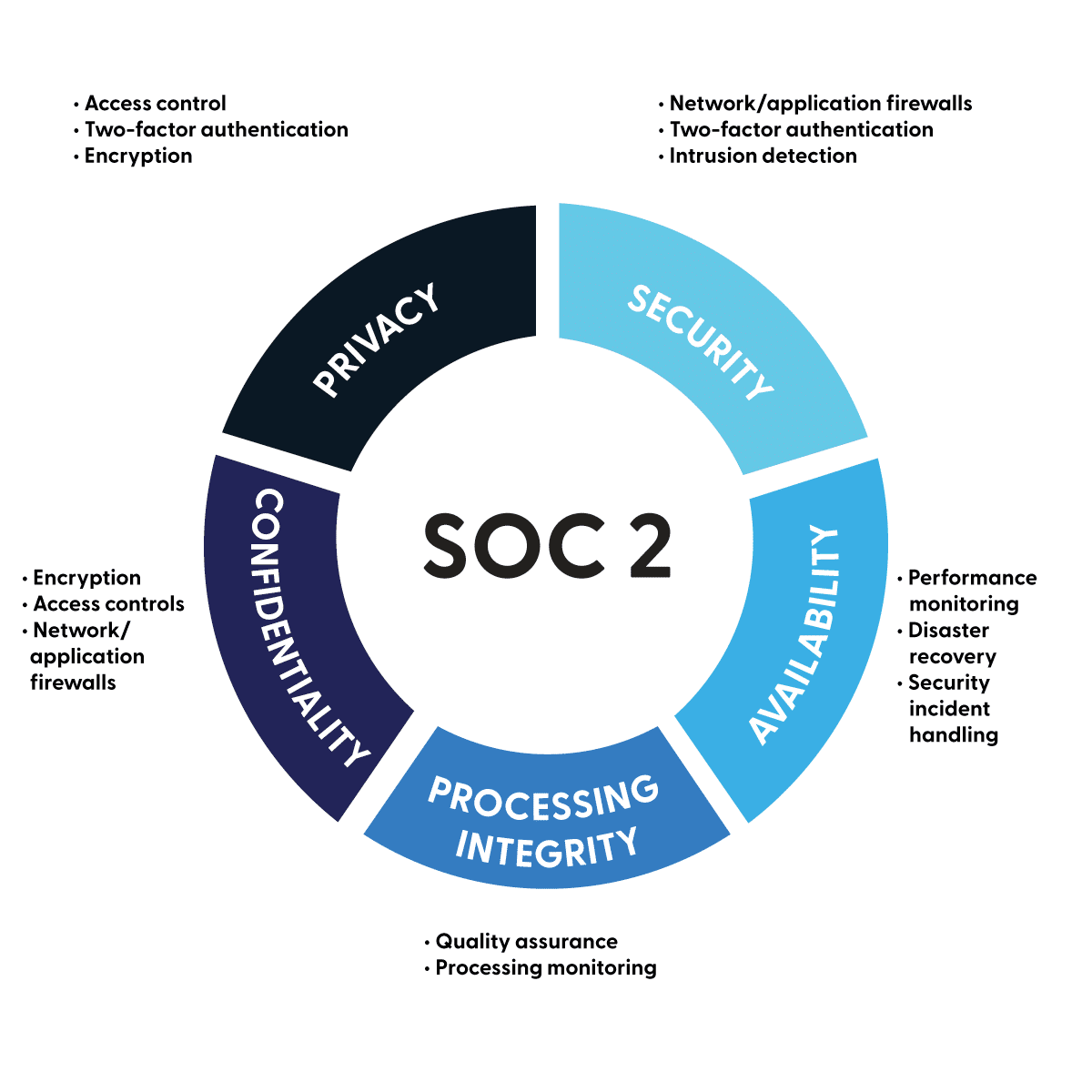
What Are The 5 Trust Services Criteria for SOC 2?
The SOC 2 Trust Services Criteria are used to evaluate an organization's controls related to data management. The 5 criteria are:
- Security (the protection of data against unauthorized access).
- Availability (the system's operational uptime and accessibility).
- Processing Integrity (ensuring that system processing is complete, valid, and accurate).
- Confidentiality (protection of sensitive information from unauthorized disclosure).
- Privacy (focuses on the collection, use, and retention of personal information).
"Security is the most common one that we see at Rhymetec," Metin noted.
The entire SOC 2 set of controls is over 150 controls. About 70% of that is likely going to be controls related to the security Trust Services Criteria. When customers are pursuing a SOC 2 assessment, security Trust Services Criteria are usually selected by default and included in every report.
The remaining 4 have fewer available controls to select. Some of them are more challenging to implement, which is one reason some companies just select the security criteria.
When it comes to which criteria to select, there are two main things to consider:
- What your requirements from your client base are
- What you value in your information security program
At Rhymetec, "We usually look at what our customers need, what is most important to them, and what their customer requirements are. A lot of organizations pursue SOC 2 because their clients are requiring them to have it, or they would like to pursue a larger client that has stricter requirements to start working with them," said Metin.
It also depends on what you value as a company. If you really value the availability of customer data and are concerned about privacy, you'd also want to select those criteria. Lastly, it also depends on factors like the type of data you handle and requirements specific to your industry.
At Rhymetec, we sometimes see customers pursuing all 5 Trust Services Criteria:
What Is SOC 2 and Why Are The SOC 2 Trust Services Criteria Important?
SOC 2 is a security and compliance standard created by the AICPA.
The primary purpose of SOC 2 is to ensure that third-party companies, SaaS providers, and other organizations protect their client information in a secure manner. SOC 2 compliance demonstrates your commitment to security and builds trust with your clients and stakeholders.
There are two types of SOC 2 audits: Type 1 and Type 2.
"Type 1 is a point-in-time audit and takes a much shorter time to complete with our customers at Rhymetec," Metin explained in our webinar. "We can usually get them compliant within about three months, and in some cases even less if they have already implemented some security controls."
For SOC 2 Type 2 (the more commonly sought type), companies are audited over a period of time.
Observation windows start at a minimum of three to six months, with some auditors requiring a 12-month period. Metin noted that, "...it makes the audit definitely more challenging, as companies are audited over the course of the observation window. If you missed an SLA (service-level agreement), or if an employee was onboarded incorrectly, that may cause some issues with your audit reports."
Getting expert input from the beginning of your SOC 2 journey can avoid these pitfalls, and enable you to choose the right criteria for your business.
From an MSSP (Managed Security Services Provider) perspective, Metin typically finds that there is a lack of understanding about the SOC 2 Trust Services Criteria in particular:
"When customers start working with us, we usually need to explain to them what the 5 Trust Services Criteria are and which ones they should select for their business. It's a very critical decision-making process."
So, let's jump right into what the Trust Services Criteria are, how to select the right ones for your business, and more:
Industry-Specific Examples for Each SOC 2 Trust Services Criteria
Let's take a closer look at each individual Trust Services Criteria:
1. Security
Regardless of your industry or what type of company you are, the security Trust Services Criteria is a mandatory component of the SOC 2 Report. It's required for all SOC 2 engagements and forms the baseline on which other criteria are then built.
For the next 4 criteria, we will provide examples of the types of companies that may opt to select each one:
2. Availability
Criteria around the availability of data apply to companies like online realtors and e-commerce platforms that rely on continuous uptime to support their customer transactions.
Telecom companies that provide communication services and need to maintain uninterrupted network availability would also want to explore availability criteria under SOC 2. Lastly, utilities and other critical infrastructure providers that need to ensure constant availability for operational purposes may opt for this set of criteria.
3. Processing Integrity
This applies to investment firms, accounting firms, and financial service providers that manage financial transactions and require accurate processing of data. Manufacturers that rely on automated processes for production and distribution would also want to consider the integrity selection criteria.
4. Confidentiality
"Law firms and legal service providers that handle sensitive client information would want to consider confidentiality," said Craig. So would consulting firms that deal with proprietary business strategies and government organizations that handle classified or sensitive information.
5. Privacy
Last but not least, privacy is often selected by schools, universities, and online education platforms to protect the personal data of students and staff. Likewise, online retailers that collect customer information for marketing purposes and healthcare organizations often opt for privacy criteria.
It's important to note that companies must roll out SOC 2 compliance across all locations and business units. Some adjusting may be needed if you operate across multiple regions to reflect nuances like local regulations and cultural differences. But in general, controls under the selected Trust Services Criteria should be consistently implemented.
Who And What Should Be In Scope?
The scope refers to the specific boundaries and focus areas that an audit will cover concerning the SOC 2 Trust Services Criteria.
By paying close attention to scope from the beginning, you can help reduce the scope and get through your audit easier. Here is what auditors will look for of who will be in scope, according to Craig:
"Any users that are critical to the delivery or the service that we are auditing should be in scope. In addition to anyone with access to sensitive data, customer data, or production data."
This could include your core team members across IT security, compliance, HR, finance, and operations, as well as consultants or contractors.
As for systems in scope (the what), it depends on 1) which systems impact your customers, and 2) which systems contain customer information.
"When we go through a SOC 2 Type 2 audit with a client, the auditors are looking into the production systems, production networks, and other production devices that actually impact customers. Staging environments or test environments that do not impact customer systems are not monitored or even audited," Metin explained.
If you have a SaaS product or other technical systems in place, you should think about what is actually in production and what impacts your customers. This also applies to any third-party vendors you work with.
If a vendor does not impact your customers in any way and does not process sensitive information, it will likely be assigned as low-risk and won't be subject to the same scrutiny as high-risk vendors (like your hosting provider or your email provider).
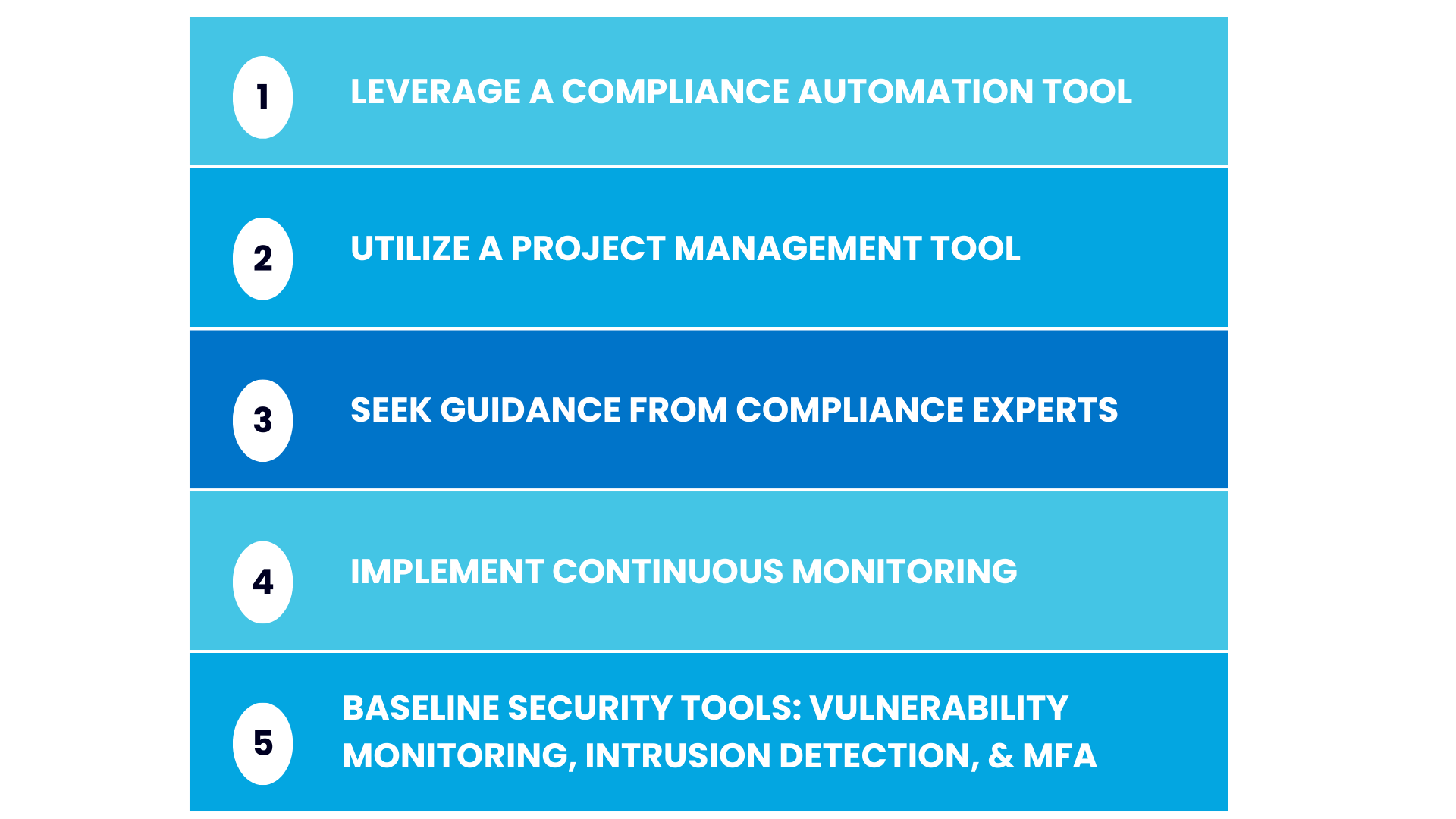
What Tools and Advice Should Companies Consider To Help Streamline Compliance?
"First off, consider using compliance automation tools," suggested Craig. "We see clients save time to focus on their business by leveraging compliance automation tools in the market."
Spreadsheets don't cut it anymore. Compliance automation tools speed things up for everyone and are favored by auditors.
Having a solid project management tool is also very important.
There is a lot of work involved in SOC 2 compliance and there are typically 10 - 15 stakeholders who need to follow these controls and track them to completion. With a project management tool, you can add certain tasks (such as your penetration tests, access reviews, and risk assessments), assign them to the right personnel, and track them to completion.
Craig also suggested seeking guidance from compliance experts. Choosing the right vCISO and the right auditing partner for your business is critical, as is investing in internal training to ensure everyone understands their roles in your compliance journey.
Next, implementing continuous monitoring for compliance maintenance is extremely important. Any instances of non-compliance should be quickly rectified. Be sure to keep thorough documentation for your audit for any areas that fall out of compliance and how you addressed them.
There are some additional baseline security tools you will need to have, depending on which controls you select. These include vulnerability monitoring tools, intrusion detection systems, and a system to enable multifactor authentication.
5 Ways To Streamline Compliance
Concluding Thoughts: How Rhymetec Aligns SOC 2 Trust Services Criteria With Businesses' Operations & Goals
At Rhymetec, we enable businesses to align SOC 2 controls with their operations and goals to protect data, build customer trust, and meet regulatory requirements in their industry.
SOC 2 compliance shows that you take security seriously and mitigates risks. As demonstrated in our case studies with businesses like Kizen and Modicum, companies also find that having their SOC 2 report unblocks sales and opens up new market opportunities.
At Rhymetec, we see compliance and security as business enablers. We've helped over 600 companies establish scalable security solutions and get compliant in record time. Our custom solutions are specifically tailored to each organization we work with so their cybersecurity grows with their business and goals.
Explore our transparent pricingand schedule a time to chat with our team to learn more.
Interested in reading more? Check out additional content on our blog.
How are resource-savvy businesses fast-tracking and maintaining cybersecurity compliance in 2024?
Many companies are now using an innovative and complete solution that combines automation with hands-on, expert security services. Compliance automation platforms provide an invaluable tool that works in sync with manual tasks to achieve compliance in the fastest timeframe possible, helping you effectively prepare for your audit.
Our team of security experts at Rhymetec is extremely experienced with this process. We have helped hundreds of companies build strong infosec programs and meet compliance requirements while reaping the full benefits of an automation tool. For more information on how we can help with all of your security and compliance automation needs, contact our team today:
The Benefits of Compliance Automation
Compliance automation is an innovative tool companies use to establish and scale their information security (infosec) programs. The platform serves as a single source of truth for everything related to compliance, allowing companies to have sharp visibility into these areas and pinpoint exactly what they need to do.
Many companies elect to use an automation tool because they are astutely thinking ahead about their audits and what they can do to make the process easier. After all, what makes life easier for your auditor will ultimately make your life easier as well.
No auditor likes receiving headache-inducing 50-page Excel spreadsheets that they have to figure out how to navigate for every new engagement. Instead, auditors appreciate having a single place where companies can easily collect all relevant documentation laid out in a clear format. Compliance automation platforms provide exactly this.
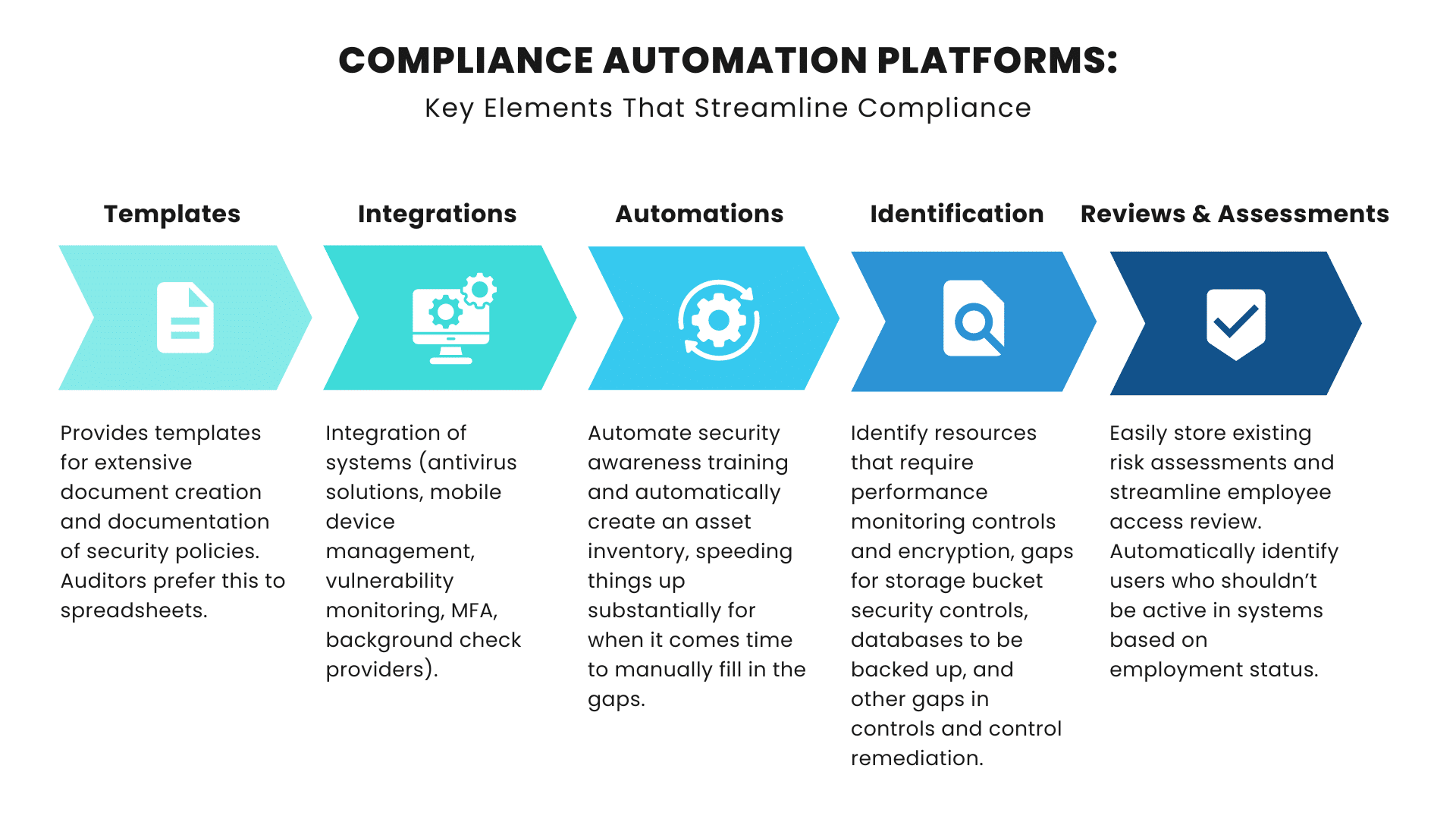
They streamline the process in many areas, accomplishing the following tasks:
Policy Templates:
Compliance automation platforms provide robust templates for extensive document creation and documentation of security policies.
Integrations Provided By Compliance Automation:
A key advantage of using an automation platform is the level of integrations it provides. Platforms provide integrations in the following areas (and more) in order to streamline compliance:
- Background check providers to notify clients if background checks are missing for any employees.
- Vulnerability monitoring solutions to create test failures based on vulnerabilities and source code tools for identification of testing failures.
- Relevant client systems to identify systems without MFA.
- Mobile Device Management and antivirus solutions to identify gaps in compliance.
Human Resource (HR) Security Solutions:
Automation platforms can automate security awareness training for organizations. This is an important advantage, as many frameworks require security awareness training. Employee access reviews can also be conducted by identifying users who shouldn't be active in systems based on their employment status. This is made possible by collecting user access information through integrations with other systems.
Frameworks like SOC 2 require periodic performance reviews for employees. These platforms provide a centralized place for evidence collection of performance reviews.
Asset Inventory:
The automatic creation of an asset inventory using available integrations is a key benefit, speeding things up substantially for when it comes time to manually fill in the gaps.
Identification Through Compliance Automation:
Compliance automation platforms automatically identify control items in the following areas:
- Resources that require performance monitoring controls.
- Resources that require encryption in transit.
- Resources with gaps for storage bucket security controls.
- Databases that are not backed up.
- Gaps in controls and control remediation.
Risk Management:
Compliance automation platforms store existing risk assessments conducted by the customer or security professional. Additionally, they provides 3rd party supplier management by storing existing risk assessments for all vendors, and their security reports.
Security Questionnaire Fulfillment:
Lastly, they offer automated security questionnaire fulfillment, removing a large amount of the burden of filling out long questionnaires.
The automation and integrations provided by compliance automation platforms speed up an array of complex processes that would otherwise take substantially longer. However, a security and compliance professional is still needed to ensure your team is doing the manual tasks of meeting your desired compliance goals; drafting policies, setting up company-specific security awareness training, conducting risk assessments, and much more.
Pinpointing The Controls You Need and That Align With Auditor Expectations
Don't have a security or compliance professional in-house? Or unsure where to start?
This is where an outsourced team of security professionals can come in to carry out a wide range of manual components necessary to get businesses across the finish line for compliance. Rhymetec's team provides the customization needed to make security and compliance efforts specific to your unique infrastructure every step of the way.
For example, one of the best parts of SOC 2 is the level of flexibility it provides for the controls, allowing companies the ability to tailor it to fit their needs. A compliance automation platform used in tandem with the customized services from an expert security team enables companies to speed things up while also ensuring they implement only the controls that make sense for their business and will align with what the auditor will expect to see.

The specialization provided by a security team allows businesses to avoid overly onerous control implementation that may not be necessary in their compliance journey.
The Manual Components of Compliance: Humans Still In The Loop
Compliance requirements and voluntary standards mandate an array of hands-on security support that only a team of qualified professionals with years of experience across different subdisciplines in cybersecurity can perform. To achieve and maintain compliance, organizations need a team of experts in GRC, penetration testing & vulnerability management, cloud security, network security, incident response, and more.
Compliance automation platforms provide a great way to manage the process and continually identify areas that need attention, speeding up the time it takes to get started and complete manual tasks. Meanwhile, the customization provided by working with Rhymetec's team ensures alignment between the controls and auditors' checklists. It enables clients to show evidence of completion of controls that cannot be automated, including penetration testing, internal audits, and tabletop exercises.
The Initial Phase: Getting Set Up
In the initial phase of the engagement, Rhymetec's security team gets the client set up in the compliance automation platform by manually accomplishing the following tasks:
- Initial Set Up In The Platform: Rhymetec manually adds the client's information to the compliance automation platform. Additionally, employees, users, and all other relevant information depending on the individual client's needs are added to the platform.
- Integration of Relevant Systems: Next, the team integrates relevant systems with the automation platform and configures settings to get items including security awareness training and onboarding setup.
- Project Planning: Rhymetec's team meets with the client to determine the infrastructure details and create a system description. The security team works closely with the client at this phase to gain a deep understanding of their individual needs and to identify the exact controls they need to adhere to under the chosen framework(s).
Compliance isn't one-size-fits-all.
Organizations can have vastly different needs depending on factors like their industry, geography, company size, the third parties they work with, the types of data they handle, and more. Without an experienced security and compliance team to examine these factors, there's a risk of not doing enough or even doing too much.
Filling In The Gaps
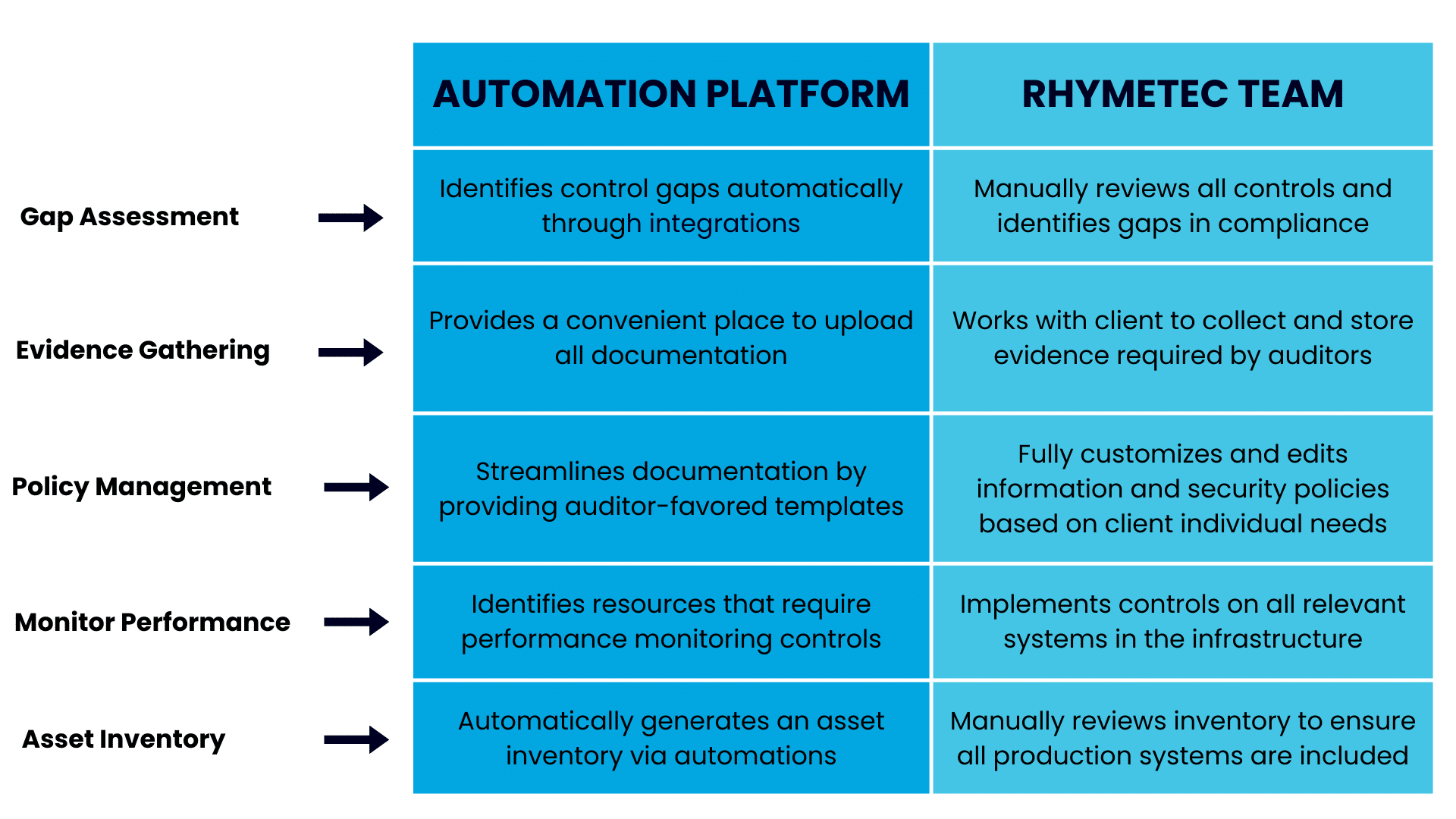
Using the information provided by the platform as a baseline, Rhymetec's team goes from there to fill in the gaps based on each client's individual needs. This stage involves:
- Gap Assessment: Rhymetec manually reviews all controls and identifies gaps in compliance for the client.
- Evidence Gathering: The security team works with the client and other stakeholders to collect and store evidence required by auditors, using the compliance automation platform as a convenient place to upload all documentation.
- Policy Management: Using templates provided by the compliance automation platform as a baseline, Rhymetec fully customizes and edits information security policies based on individual client needs.
- Performance monitoring controls: Based on the resources identified by the compliance automation platform, Rhymetec implements controls on infrastructure systems such as databases, servers, and buckets. This helps the client gain visibility into their infrastructure.
- Asset inventory: Using the asset inventory created by the automation platform, Rhymetec manually reviews the inventory and ensures all production systems are included in it.
These action items work hand-in-hand with the compliance automation platform in the following ways:
Completion of Manual Security Tasks
Thanks to the features of the compliance automation platform, many items are able to be easily identified as needed for the client on an ongoing basis. This substantially cuts down time, enabling the security team to fill in the manual pieces as soon as they are identified.
However, not every task has elements that can be automated. The fully manual tasks needed to meet controls under many cybersecurity regulations and frameworks include the following:
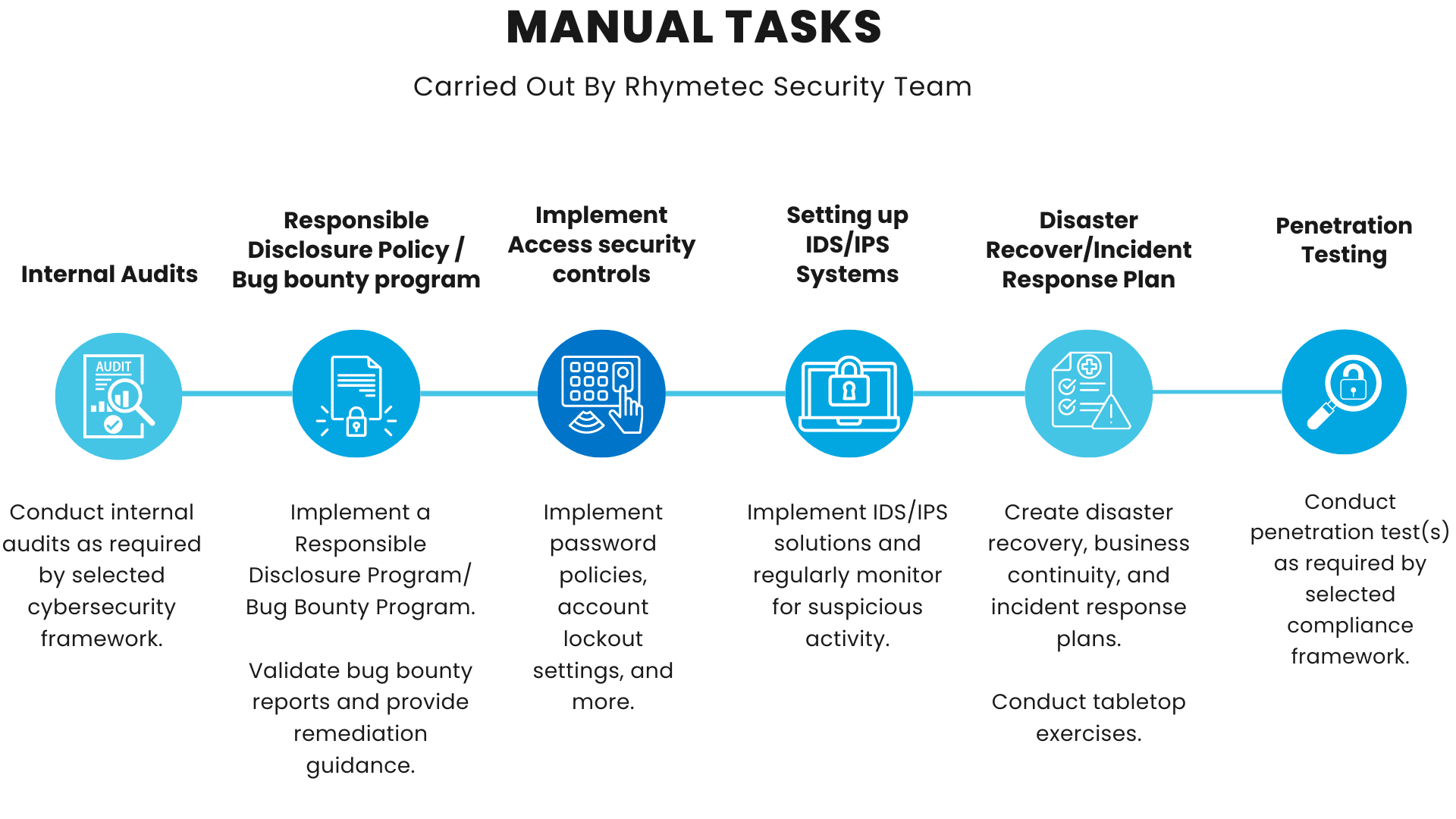
The above action items needed for compliance, such as penetration testing and tabletop exercises, cannot be automated. Items such as incident response plans also must be manually completed in order to be tailored to each individual company, their risk profile, and their industry.
The compliance automation platform comes back into play in the next phase, streamlining the completion of all additional security controls.
Fulfillment Of Additional Critical Security Controls: Manual Solutions Working With Compliance Automation
Rhymetec creates and implements the additional cybersecurity controls required by the compliance framework selected by the client. The compliance automation platform, meanwhile, plays a key role in this step for each control through system integrations and identification of areas for improvement.
Here's how the two solutions work in sync to streamline the implementation of critical security controls needed across many different frameworks, laws, and regulations:
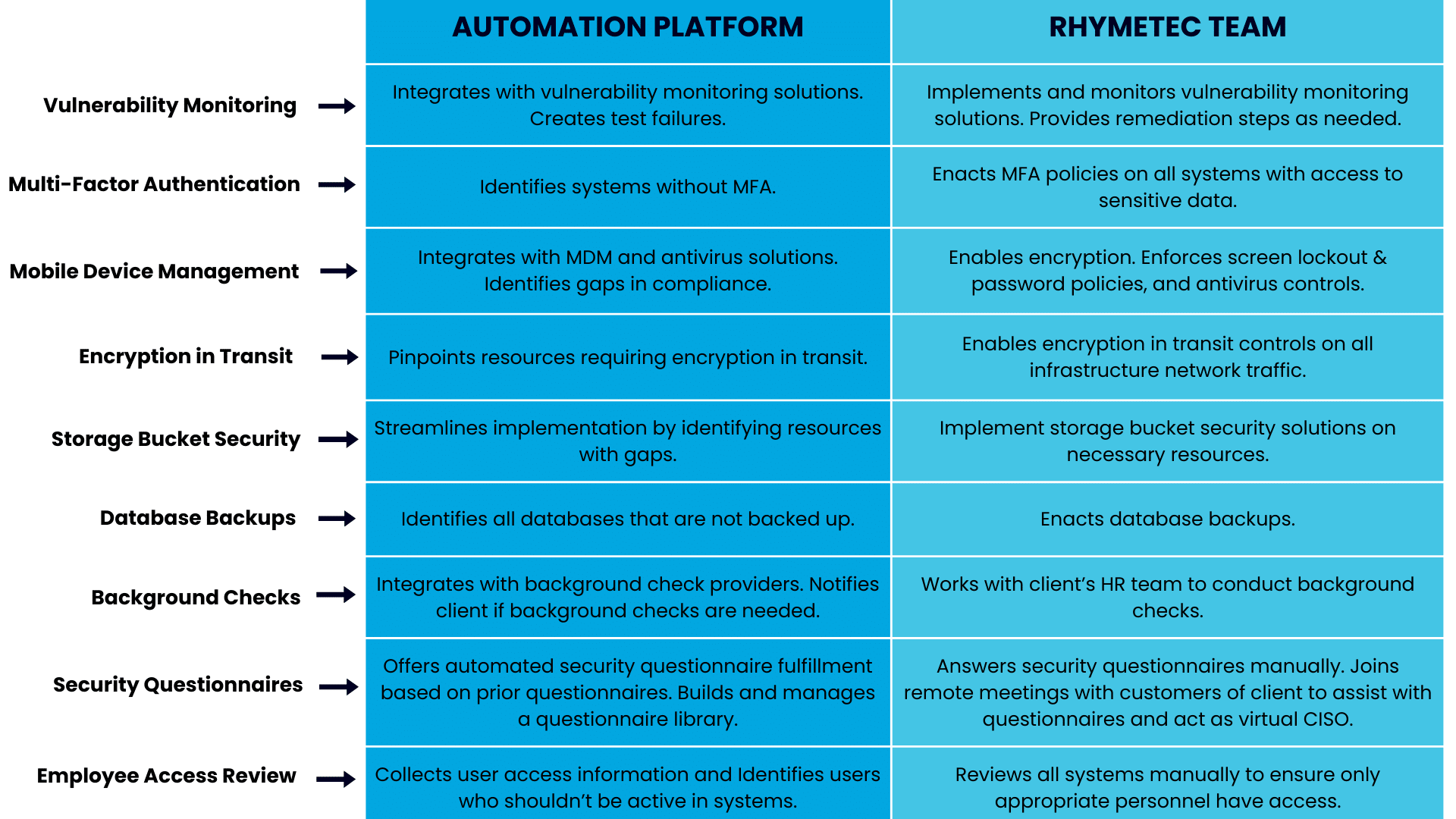
The platform serves as a foundation for the tasks performed by Rhymetec's security team, enabling them to jump right in and start the hands-on work.
As an example, almost every cybersecurity standard nowadays requires organizations to implement multi-factor authentication, as it is one of the best measures companies can take to protect themselves. The compliance automation platform is able to identify systems in a client's infrastructure without MFA. The security team takes it from there to enable MFA policies on all critical systems.
Final Audit Preparation, Conducting The Audit, & After The Audit
In preparation for the audit, Rhymetec ensures all necessary documentation is organized and accessible. For frameworks like ISO 27001, Rhymetec will conduct an internal audit to identify and address any non-conformities in preparation for the external audit. During the official audit, Rhymetec works closely with auditors to ensure all evidence is collected and provided.
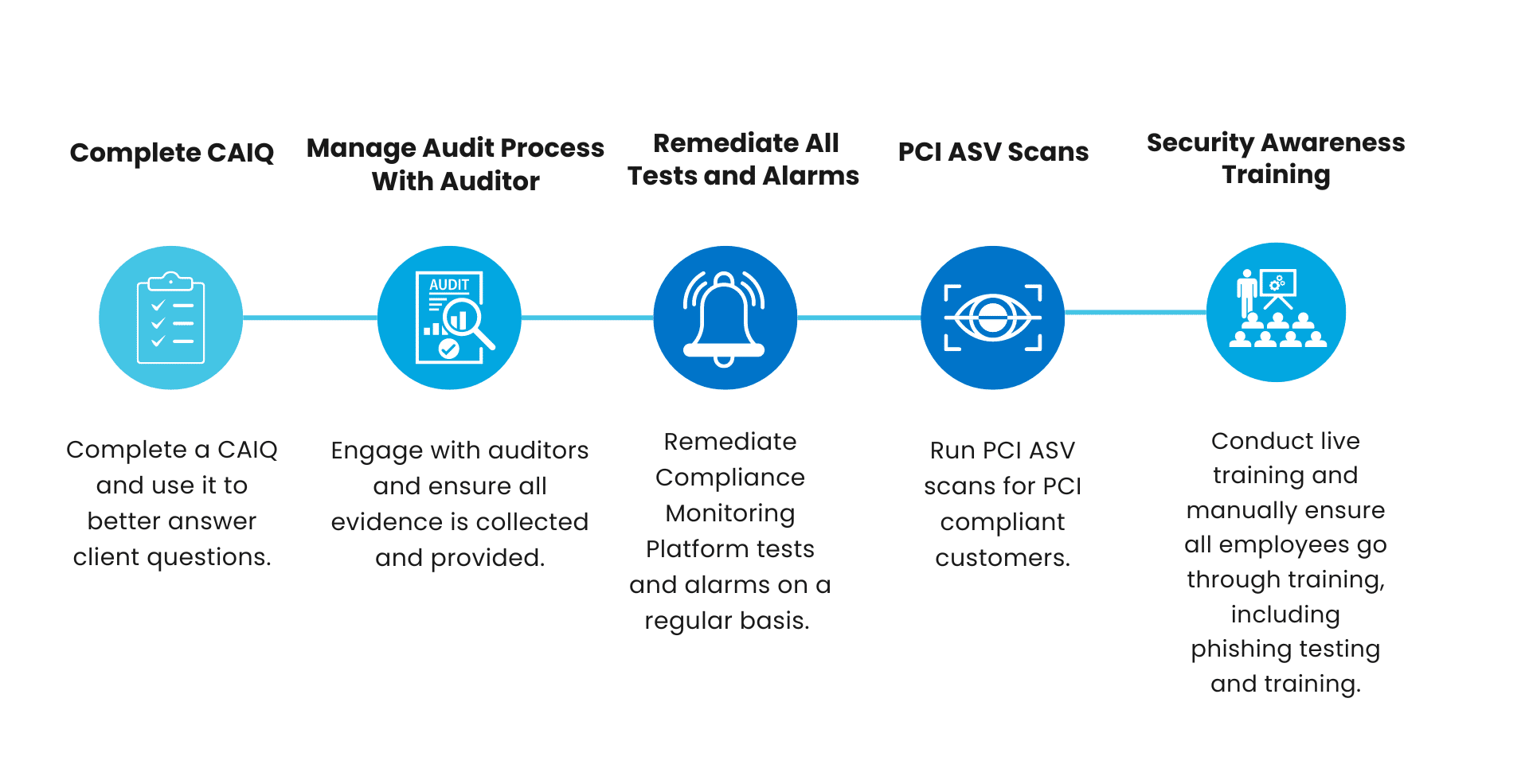
For standards like SOC 2 that clients will be audited on annually, and to maintain a continuous strong posture of security, Rhymetec completes the following items on an ongoing basis: Annual vendor risk assessments, regularly updating risk assessments to reflect new risks, regularly reviewing firewall rules for customers to ensure they stay compliant with policies, and running continuous assessments like PCI compliance scans for PCI-compliant customers.
Don't forget, for some stakeholders compliance isn't always enough. Security questionnaires are a secondary tool that prospects use to evaluate your security against their own standards. Utilizing compliance automation can help you streamline this process. Using Rhymetec's team of experts can help you get into the weeds around more robust or complex questionnaires and even represent your business on security-related discussions.
In Conclusion: How Compliance Automation and Manual Security Services Provide A Full Portfolio Solution For The Modern Business
Compliance is not a sprint right before an audit.
It requires an ongoing solution that streamlines the process by automating the pieces that can be automated and leveraging a team of experts to fill in the gaps and carry out the manual tasks. Through a combination of automation and manual security services, organizations can maintain a posture of continuous compliance, ensuring that requirements are always being met and evidence of these standards can be accessed easily.
When used together, a compliance automation platform and the level of customization provided by an experienced security team fast-tracks compliance while avoiding a one-size-fits-all approach. Every company has its own controls that need to be implemented, as well as a unique risk profile. For effective compliance maintenance, modern businesses need an automation platform plus a team of security experts to carry out and maintain these requirements.
With Rhymetec, the manual components are accomplished by a security team with more than a century of cumulative experience across a diverse array of cybersecurity disciplines. Rhymetec leverages this experience to tailor compliance to fit organizations' individual needs and to maximize the efficiency of control implementation. Meanwhile, the compliance automation platform speeds things up every step of the way, provides a single source of truth for the client, and serves as an auditor-favored platform with all documentation presented in a clear format.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while also balancing security with budget.
We enable our clients to outsource the complexity of security and focus on what really matters – their business. If you are interested in our services, or if you simply have questions about security, you can contact our team for more information.
Interested in reading more? Check out our other blogs:
- Managed Compliance: An Updated Approach For The Cyber Regulatory World
- Security Policies For Small Businesses: 5 Tips For Effective Communication
- Cybersecurity for Startups: A Rhymetec Guide for 2024
So, you've just been handed a security questionnaire by a potential customer, and you're not sure where to start.
What is access control? What should you answer when asked if you utilize strong authentication across all applications with sensitive data?
This Rhymetec guide will not only help you answer these questions but will also provide suggestions that you can use to strengthen your security posture and work with potential customers more confidently, with less risk of non-compliance or a data breach.
What Is A Security Questionnaire?
Security questionnaires are used by your potential customers to assess their third-party vendors and suppliers. Numerous major third-party incidents have occurred in recent years, and threat actors are increasingly attempting "supply chain attacks" - cyberattacks that target a critical element of a particular supply chain and then attempt to move laterally into other parts of the supply chain.
For example, the identity and access management platform Okta recently suffered from numerous compromises that threat actors attempted to use to gain access to Okta's customers' data. All of this was a long way of saying companies with mature cybersecurity programs care about supply chain attacks - a lot.
Enter the security questionnaire.
Security questionnaires are required by some compliance requirements such as HIPAA, GLBA, and PCI DSS. In addition, understanding who you're doing business with, what their security controls are, and what types of data you will be sharing with them is important from a simple risk mitigation perspective.
Security Questionnaire Example Questions
So, what exactly do security questionnaires typically ask?
It can vary a lot, but here are some common types of questions:
- Does your organization employ strong authentication measures such as multi-factor authentication for all corporate applications that hold customer data?
- Does your organization offboard employees within 8 hours of the termination of employment?
- Does your organization conduct routine penetration testing to identify vulnerabilities in your environment?
- Does your organization have documented incident response plans and processes?
- Does your organization routinely train users regarding information security and risk?
Depending on the potential customer you are working with, questions may be very in-depth or very cursory. In many cases, your customers may tier their security questionnaires; a company that stores data about tennis shoe manufacturing needs far less scrutiny than a company storing Protected Health Information (PHI).
Security Questionnaires and Compliance
Security questionnaires aren't only driven by risk requirements. They are also driven by specific legal compliance requirements that your customers fall under. We will provide two examples of major compliance regulations that directly touch on vendor security.
In both of these, notice that nowhere is it mandated that you must send a security questionnaire. Instead, both require that organizations assess their vendors. The security questionnaire is the form that this assessment takes.
The HIPAA Security Rule
The Health Insurance Portability and Accountability Act Security Rule (HIPAA): HIPAA applies to healthcare organizations and other organizations that handle Protected Health Information (PHI).
Under HIPAA, any organization handling PHI that is considered a "covered entity" is required to comply with the HIPAA Security Rule, a specific set of information security standards. In addition, "business associates" of covered entities are also required to meet all requirements in the security rule:
- 164.308 Administrative safeguards. (A) Risk analysis (Required). Conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by the covered entity or business associate.
The U.S. Department of Health and Human Services also publishes guidance on how to conduct the risk analysis required by section 164.308.
The Bottom Line: If your organization gets a security questionnaire from a healthcare organization and you will be handing PHI, take it extremely seriously. You may be considered a HIPAA business associate and be required to comply with the HIPAA Security Rule. An experienced vCISO can help guide you on how to answer questions and implement missing security controls.
The Gramm-Leach Bliley Act and The Security Questionnaire
The GLBA applies to financial services organizations. Part of the regulation requires organizations to meet certain information security requirements. eCFR Part 16, § 314.4 spells out specifically what financial institutions need to do in order to maintain compliance regarding third-party suppliers:
- Taking reasonable steps to select and retain service providers that are capable of maintaining appropriate safeguards for the customer information at issue;
- Requiring your service providers by contract to implement and maintain such safeguards; and
- Periodically assessing your service providers based on the risk they present and the continued adequacy of their safeguards.
The Bottom Line: If you are getting a security questionnaire from a financial services organization, they are likely trying to meet their legal requirements under GLBA. The organization likely isn't measuring you against a specific standard where all requirements must be met to do work with your organization. If you don't meet every control in the risk questionnaire, consider having a conversation with the customer about which ones they find totally necessary to work with a vendor, and identify a plan to meet those on a set time scale.
How Do You Answer a Security Questionnaire?
Answers to security questionnaires from customers should be honest, straightforward, and complete.
For example, to answer the following question:
- Does your organization routinely train users regarding information security and risk?
You might reply:
- Users are trained on a monthly basis on information security best practices using the security awareness training platform KnowBe4. In addition, regular simulated phishing campaigns are conducted against employees. If an employee fails a phishing test additional training is mandated.
Notice this answer gives a specific example of not only that the activity is being carried out but how the activity is being carried out (KnowBe4).
It also goes into detail about how often the phishing test takes place, and even provides additional evidence of a serious security posture by describing an interrelated simulated exercise.
However, don't go overboard with information. If your customer is asking a question about training, you don't need to tell them about your amazing vulnerability management practice. Instead, answering questions with additional detail on related policies, procedures, or technology can help make the customer's job easier.
The most important thing to do is never lie.
If there are certain questions that your potential customer has asked that you don't want to disclose, have a frank and honest discussion about what information you can provide, what you can't, and why. Lying on vendor risk questionnaires can put your organization in potential legal jeopardy, both civilly and criminally.
Should I Get Outside Help in Answering a Security Questionnaire?
Many organizations turn to managed security services organizations for help in answering security questionnaires.
Why choose a managed security services company to help you?
There are a few different reasons.
First, cybersecurity can be extremely complex! Answering vendor risk questionnaires isn't always a straightforward exercise. Does your routine security assessment performed by a third party satisfy the definition of a penetration test? Does annual user training meet the question, "Do you regularly engage in security awareness training?"
These types of details matter but aren't always immediately apparent to those answering a security questionnaire.
Secondly, the "why" of a security questionnaire matters. Mistakenly answering a question on a security questionnaire from a customer who is simply doing their due diligence can be damaging. But mistakenly answering a question for an organization assessing your HIPAA compliance under the business associates rule can be fraught with legal peril.
An experienced vCISO can help navigate these waters and ensure that answers are correct and backed with evidence.
Finally, answering security questionnaires doesn't have to be hard! There's no reason that you should be spending weeks fretting over whether your security awareness training program is up to snuff.
Engaging a managed security services company can help you rapidly respond to security questionnaires, unclogging your sales pipeline and turning security compliance into a selling strength.
SOC 2 and The Security Questionnaire
Fortunately, there may be a way that you don't need to answer every security questionnaire that comes your way.
Enter the SOC 2 Report.
SOC 2 is a voluntary framework that organizations can meet and be audited against on an annual basis. By meeting requirements under SOC 2 Type 2 and undergoing an annual audit, you can have a specific report outlining your security controls to provide to prospective customers, dramatically simplifying the process.
SOC 2 isn't just a way to get out of doing security questionnaires, though.
Organizations are increasingly choosing their vendors based on good security practices and continuous compliance. Using a vendor like Rhymetec to help you meet SOC 2 can expedite your sales process, build trust with potential customers, and enable you to engage prospects who want to see evidence of your security before doing business.
The Bottom Line
Many organizations use security questionnaires as a way to screen potential vendors for unacceptable security risks. This is becoming increasingly common, as companies wish to strengthen their third-party risk management in light of recent breaches due to vendors and suppliers.
Hopefully, this guide helped clarify how to answer questions on security questionnaires and how to turn risk assessments into a business enabler rather than a cost center.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We've worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while also balancing security with budget.
We enable our clients to outsource the complexity of security and focus on what really matters - their business. If you are interested in our services, or if you simply have questions about security, you can contact our team for more information.
About The Author: Metin Kortak, CISO
Metin Kortak is the Chief Information Security Officer at Rhymetec. Metin began his career working in IT security and gained extensive knowledge of compliance and data privacy frameworks such as SOC 2, ISO 27001, PCI, FedRAMP, NIST 800-53, GDPR, CCPA, HITRUST and HIPAA. He joined Rhymetec to build data privacy and compliance as a service offering. Under Metin's leadership, these offerings have grown to more than 200 customers, positioning the company as a leading SaaS security service provider in the industry.
Interested in reading more? Check out our blog.
You might be wondering - Why would a threat actor bother targeting a startup? Don't they focus on larger companies?
In 2025, cybersecurity for startups is just as critical as it is for the world's largest organizations. You may be surprised to learn that small businesses nowadays are actually more frequent targets of cyberattacks than larger companies.
According to Verizon's 2023 Data Breach Investigations Report, there's a very clear reason for this:
Regardless of organizational size, companies are increasingly adopting similar services and infrastructure. This means that the attack surface of small organizations - all of the points from which a threat actor can access a system - looks more similar than ever to that of large companies.
When it comes to the attack surface of small versus large businesses, "...by now there is so little difference based on organizational size that we were hard-pressed to make any distinctions whatsoever." (Verizon, 2023).
While it's great that many business-accelerating tools are now equally accessible to small organizations, this democratization of technology has a dark side:
Organizations, from startups to Fortune 500, have increasingly similar risk profiles but do not have the same resources to prevent and respond to attacks.
From a threat actor's perspective, this makes smaller organizations ripe targets. In light of this, what can you do as a startup to improve your security, especially without breaking the bank?
This guide will discuss:
- Why is Cybersecurity for Startups Important?
- 5 Practical Things You Can Do Right Away
- Measures to Further Improve Your Security
- Balancing Security With Budget
- Frequently Asked Questions
- Accelerating Cybersecurity for Startups
Rhymetec was specifically founded with the mission to make cutting-edge security available to startups. We've worked with hundreds of companies to provide practical solutions that enable them to be as secure as possible while also balancing security with budget.
This guide will provide actionable solutions for cybersecurity for startups based on:
- Our experience working with hundreds of startups.
- Current trends in the industry in 2025.
Why is Cybersecurity for Startups Important?
Large companies have the resources to continuously sharpen their security measures and keep up with increasingly stringent compliance requirements. Meanwhile, smaller businesses without the same resources to devote to security are left behind.
Threat actors know this, and that's why an employee at a company with less than 100 employees receives 350% more social engineering attacks in their email than an employee at a large company.
And the smaller the business, the harder the attack hits: For over half of small companies, all it takes is one data breach to go out of business within 6 months.
What does this mean?
Startups need to invest in cybersecurity as much as large companies do, ideally from the onset. Fortunately, nowadays, there are affordable solutions for startups to access cybersecurity services and expertise historically reserved for large companies:
Instead of building out expensive in-house security teams, many startups turn to Virtual CISO Services as an alternative. Additionally, there are measures any startup can take right away to improve security, which we'll discuss in the section "5 Practical Things To Do Right Away".
But first, let's talk about the most common threats faced by startups in 2025. We'll keep these in mind when suggesting security measures you should consider.
Common Security Threats Faced by Startups in 2025
According to Verizon, 92% of tactics threat actors use against small businesses are either:
- Social engineering tactics, such as phishing emails.
- Basic web application attacks.
User credentials (like passwords) are the most frequently compromised type of data. This is because threat actors know this type of data is particularly vulnerable when hosted and processed by small organizations without strong security.
Even if you aren't at the stage where you want to explore building out a comprehensive security program, there are a few things you can do in the short term.
With the most common threats faced by startups in mind, here are 5 solutions that will mitigate a huge amount of risk right off the bat:
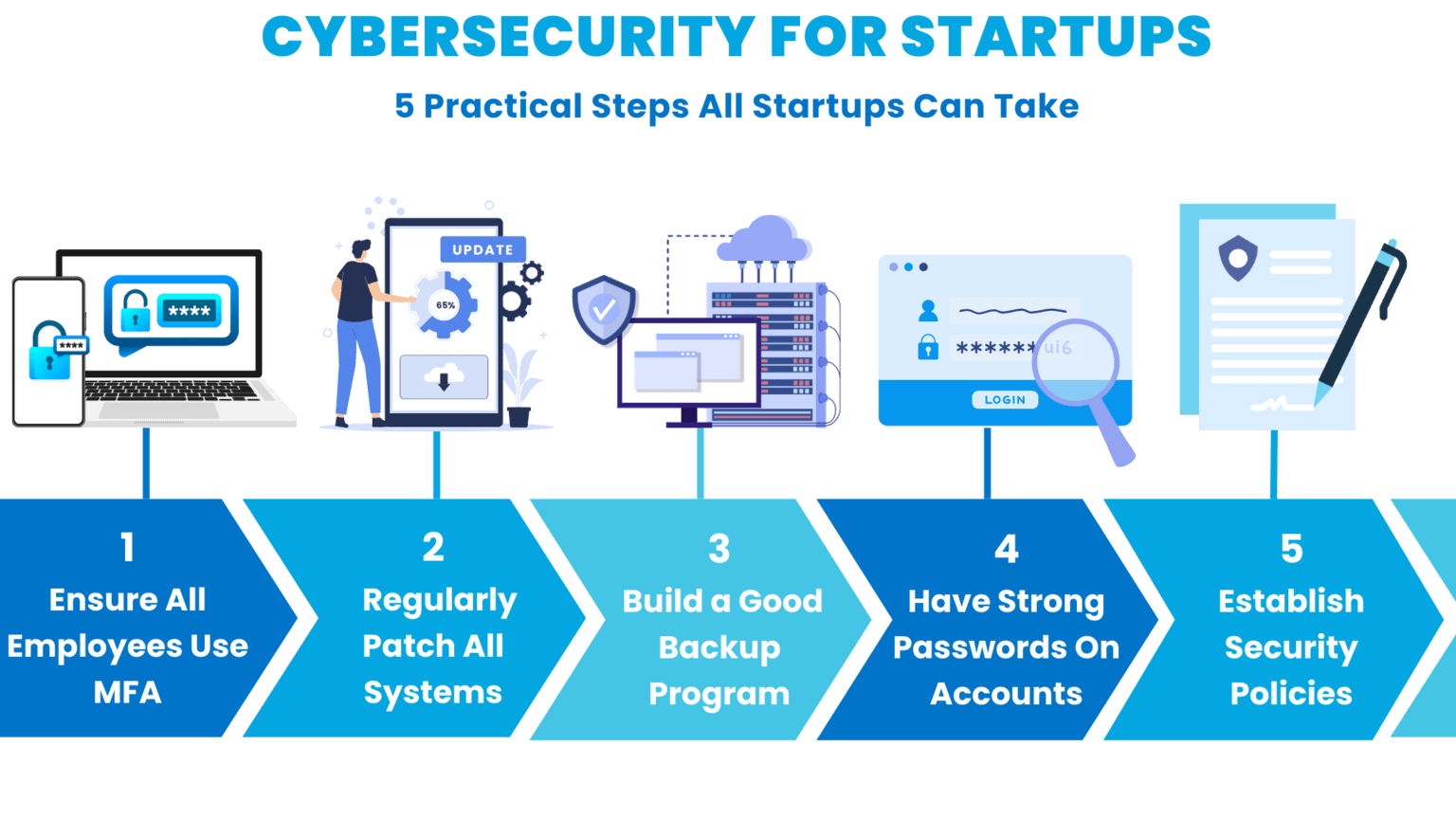
Cybersecurity for Startups: 5 Practical Things To Do Right Away
We get how much running a startup involves on a daily basis.
Even if you're crunched for time and resources, fortunately, there are a few 'quick win' measures you can take to improve your security immediately!
Some of these may seem basic. But you would be stunned how many people, even in high-level positions, are using passwords like "032564Oreo (user's birthday + their cat's name), or "newpassword2025!" (self-explanatory).
It's best to play it safe and operate from the assumption that most people simply don't practice good security hygiene. It's on company leadership to provide guidance and policies.
With this in mind, here are 5 measures you can take right away:
1. Ensure All Employees Use MFA At Your Startup
Multi-factor authentication (MFA) is critical to an effective security program.
Implementing MFA across all accounts, including cloud access, network access, and even SaaS access accounts, is the number one thing you can do to reduce the risk of a major incident or breach.

Without MFA, all a major breach takes is a single employee setting a weak password, which a threat actor then identifies through password spraying or traditional leaks.
Beyond simply setting up and requiring MFA, there are additional steps you should take in light of the current threat landscape in 2025. Unfortunately, threat actors have inventive ways around MFA nowadays.
To mitigate this risk, here are some important tips when setting up MFA controls:
- Understand where your customer data lives. Individual teams and employees may purchase new SaaS applications on their own authority and begin storing customer and other data in these systems. Without adequate controls and visibility, employees may be storing customer data in SaaS solutions without MFA that your IT and security teams are unaware of.
- Set short time-to-live (TLL) on session cookies where possible. Session cookies allow a user to reauthenticate without having to reenter a code for a set duration of time. If session cookies are stolen in the meantime, they can be used in a session replay attack to bypass codes. Setting time-to-live for cookies as shortly as possible does inconvenience users, but reduces the risk that if a threat actor steals cookies, they can be effectively used.
- When implementing MFA, it is strongly recommended to use authenticator applications rather than SMS-based authentication when possible. SMS-based authentication is susceptible through a practice known as "SIM Swapping," in which threat actors either social engineer or steal the means to swap SIM devices at the carrier level, allowing them to hijack a user's cellphone traffic.
2. Make Sure All Systems Are Patched
Many cyberattacks happen as a result of organizations not building a successful vulnerability management practice. Threat actors continuously scan for publicly facing IT assets with known vulnerabilities to identify potential targets to exploit.
A great example of this is the WannaCry ransomware attack in 2017. The exploit used by threat actors had actually been patched in Windows two months prior to the attack. Devices up-to-date on the latest security updates were not impacted by the attack. Meanwhile, devices that hadn't kept up with the latest patches were left vulnerable.
Vulnerability prioritization can be a pain. It isn't always clear when a vulnerability is critical versus when it can be delayed somewhat. Additionally, patches can be extremely disruptive to existing IT infrastructure. All of this makes effectively patching systems quite difficult. Here are a few tips:
- Prioritize vulnerabilities on publicly facing systems first: Threat actors regularly scan the internet looking for known exploitable vulnerabilities on publicly facing systems. An instance of this in 2025 includes the ConnectWise ScreenConnect vulnerability. Another recent example includes the MOVEit vulnerability.
- Prioritize actively exploited vulnerabilities: Not all vulnerabilities are equally high-risk. Vulnerabilities that are theoretical or haven't been known to be "actively exploited in the wild" are likely lower risk and can be deprioritized compared to those that threat actors are utilizing.
- Use a vulnerability management service like Shodan: Shodan can help identify publicly facing IT assets along with services running on them. This can dramatically expedite mapping your organization's attack surface and identifying services that may have exploitable vulnerabilities.
3. Build A Cybersecurity Program With an Extensive Backup and Recovery Program
It's no secret that ransomware groups often encrypt sensitive data belonging to organizations. But ransomware isn't the only reason you should have a strong backup and recovery program.
Natural disasters, unexpected outages, and threat actors can all compromise the confidentiality, integrity, and availability of data. This creates enormous risk.
Create not just a backup system for your startup, but a backup and recovery program that includes technology (either localized or cloud backups), processes (policies and procedures), and people responsible for ensuring it all works together.
Once you have a system that works, test it!
Tabletop exercises can be invaluable in testing real-world examples to make sure that your system works, everyone knows their role, and you can effectively respond to a crisis.
Bonus Tip: Be sure to back up your "less" critical systems.
Don't underestimate the dependencies between data and software applications. Even if your organization has multiple systems, don't isolate backup and recovery to "only" the most critical. It is often easy to overlook data dependencies between systems where one system going down can render another entirely nonfunctional.
4. Ensure All Employees Have A Strong Password

Many organizations make the mistake of believing that if they have strong two-factor authentication, they are adequately protected and don't need to worry too much about weak passwords. This couldn't be further from the truth.
If you have a weak, easily guessable password and two-factor authentication, you only really have single-factor authentication!
IBM's recent X-Force Report showed that identity-based attacks that involve leveraging valid user accounts are now the predominant way threat actors compromise environments. Compromising a single valid user account with administrative privileges can quickly escalate into a full-blown breach.
Multi-factor authentication means your organization has strong passwords and monitors password reuse. Here are a few tips to ensure employees are using good passwords:
- Create strong passwords with a length requirement, special characters, numbers, and letters.
- Use a credential monitoring service like haveibeenpwned to identify if a user's credentials have been compromised in a data breach. Rotate credentials immediately if this has happened.
- Talk extensively about password hygiene during regular security trainings. Emphasize not to reuse passwords across services. Walk users through how reusing passwords can result in the organization being compromised.
Bonus Tip: Use a password manager like 1Password.
Tools like 1Password automatically create strong passwords, which are then encrypted and stored so that only authorized users can access them.
This allows members of your team to share passwords without showing the actual password. Additionally, employees can access business-critical accounts across multiple devices without having to remember complex passwords.
If your startup has a remote workforce and employees are logging into their work accounts on multiple devices, a password manager is a must-have.
5. Establish A Written Security Policy
Establishing a written security policy is one of the most critical things you can do to create a strong cybersecurity baseline for your startup.
Rhymetec's Senior Cybersecurity Analyst, Kyle Jones, recently spoke about how to draft and communicate strong security policies. Here are a few tips he suggested:
- Know your audience. If the people who need to understand and adhere to your security policies aren't security knowledgeable, keep that in mind. Don't use overly technical language in your policies. Instead, tailor your language to your audience.
- Emphasize your policies continuously, and connect policies with the reasons behind them. People will be more likely to follow policies if the reason behind them is explained. Find opportunities, such as when an employee has an IT-related question, to reference the policies and see what they say.
- Make sure your policies reflect current trends. Your risk profile changes depending on what's going on in the world! For instance, the launching of large language models (LLMs) like Google's Gemini should make you rethink your policies.
Here are several critical questions about AI:
- Do you know if your employees are sharing data with any LLMs they may be using for work?
- Do you have an established policy around the use of this technology at your startup?
- What about updates to regulatory language around AI? Do your policies take that into account?
A great example of why these questions need to be visited can be seen in Samsung's 2023 data leak with Chat GPT - the company has since banned the internal use of generative AI tools.

Bonus Tip: Create a culture that prioritizes security and transparency.
Share resources and talk to your team regularly about the importance of security.
Don't fearmonger - you never want your employees to feel like they can't come to you if something happens. Make it clear that your door is open, and you want to know if they receive a suspicious email or if they notice unfamiliar software on their work device.
Cybersecurity for Startups: Measures To Further Improve
So, you've made sure your employees are using MFA and that nobody's password is their cat's name. You regularly update all of your systems, back up your data, and already have security policies in place.
Here are the next steps you should take:
1. Build A Formal Process to Assess The Security of Third-Party Vendors and Suppliers
Third-party risk management continues to grow in importance for organizations of all sizes.
We recommend building a full inventory of all third-party suppliers your organization uses and implementing a standard risk screening. Fortunately, modern standards make it easy to quickly screen to see if a potential third party takes information security seriously.
We recommend asking questions like:
- Does your organization have a SOC 2 Type 2 Report, or other third-party attestation on your information security program?
- Are you compliant with the HIPAA Security Rule, New York Department of Financial Services Cybersecurity Rule, or other formal legal requirements?
- Does your organization have documented security policies?
- Do you share customer data with third parties? If so, which ones?
2. Conduct Routine Pen Testing Engagements
Engage a third party (such as Rhymetec) to regularly put your security controls to the test.
Regular pen testing identifies gaps that potential attackers could exploit. Pen tests should be scoped to the specific risks that your organization faces. For example, Rhymetec can help with:
- Web application pen testing to identify vulnerabilities and misconfigurations in web apps.
- Mobile application penetration testing to identify vulnerabilities or exploits in mobile apps that could be exploited.
- Network penetration testing to identify ways that your organization's network could be exposed.
Pen testing is critical to meeting numerous security requirements. It also enables you to better answer questionnaires about your organization's security provided by potential customers.
3. Conduct Simulated Spear-Phishing Tests
Simulated phishing exercises represent another very significant opportunity to improve your security.
Running realistic simulated phishing tests can help condition employees to be wary of even realistic-looking emails purporting to offer them gift cards and sensitive information. Make sure emails look realistic and are targeted. Sending generic emails generated by a platform can come across as too obvious and fail to adequately test users.
Take an attacker's perspective - what might an attacker write without inside knowledge of users to get users to click links?
Bonus Tip: Have An Incident Response Plan In Place.
An incident response plan is a set of documented procedures to act on in the event of a security incident. For instance, do you know what steps to take in the event your startup experiences a ransomware attack?
To recall an earlier example, during the WannaCry ransomware attack in 2017, many victims paid the ransom to try to get their data back. Security professionals generally do not advise paying ransoms. The threat actors behind the WannaCry attack did not restore people's data even after they'd paid the ransom.
Having a documented incident response plan equips you with important know-how in the event you are to experience an attack or a data breach. This saves time, money, and headaches if an incident were to occur.
Balancing Security With Budget
Building good organizational security is critical. However the cost of protecting an asset shouldn't have to exceed the value of the asset.
Cybersecurity for startups needs to be balanced against ease of access, business processes, and the risks associated with the service, data, or application being secured.
At Rhymetec, we work with a lot of SaaS startups who need to build a security program typically because their customers require it and it's difficult to compete in the marketplace without one. These startups are working off a limited budget.
A good place to start to figure out how to balance security with budget is to think about the answers to the following two questions:
- What does your risk profile look like? Narrowing down the specific risks facing your organization helps prioritize where you need to spend your security dollars. For example, if you are located somewhere that's prone to earthquakes and your servers are stored there, that's a high risk. You would want to prioritize taking steps to remediate this.
- What's your risk appetite? Understand what your own risk tolerance is - If you have a low-risk appetite, you will want to commit to remediating any medium or high risks. Or, at the very least, look at how to reduce your risk from high to low in the areas of highest risk.
At Rhymetec, after we assess your risk profile and answer these questions, we get creative on the best way to proceed with building your information security program while keeping in mind budget constraints.
Frequently Asked Questions (FAQ) for Cybersecurity for Startups in 2025
Here are 5 questions we see frequently from startups in 2025. Knowing the answers to these questions - and implementing corresponding policies - is essential for robust cybersecurity for startups.
1. What are some commonly required or requested compliance frameworks for startups in 2025?
- SOC 2 is a voluntary standard often requested by customers to show you take security seriously and that their data will be in good hands if they share it with you.
- ISO 27001 is the leading international standard for information security.
- PCI DISS is necessary if your startup processes credit card payments.
- GDPR is required in 2025 if you handle the personal data of EU citizens.
- HIPAA privacy regulations require organizations dealing with healthcare data to follow procedures around the confidentiality and security of PHI (Protected Health Information).

2. How does the increasing shift to remote work impact cybersecurity for startups in 2025?
Cloud security is critical in the age of remote work.
Without proper controls, even daily activities like file sharing can result in sensitive information being shared with unauthorized users. Following best practices for cloud storage is essential in 2025, including:
- Make sure your employees have a strong separation between work and personal documents and devices.
- Invest in backing up your data to prevent the loss of important information and documents.
3. What should startups do from a security standpoint with all the AI hype?
AI amplifies existing threats, especially social engineering attacks. For example, AI can be used by threat actors to generate a larger number of personalized phishing emails.
This simply means that the best way to protect your business from AI-assisted threats is to strengthen your core security program. Staff awareness training to protect against social engineering attacks is especially important.
4. What are some best-of-breed tools startups can easily utilize in 2025?
As discussed earlier, the attack surface of small organizations is starting to increasingly resemble that of large organizations. What if you could monitor this, even down to the individual employee level?
Services like Picnic enable you to minimize the human attack surface of your startup and protect executives, contractors, and employees from social engineering attacks.
Nowadays, fortunately, there are tools that make security more accessible. Even if you have zero technical background, you can seamlessly integrate tools like Zip Security that provide enterprise-grade security and endpoint threat detection.
5. When is the right time to start looking into cybersecurity for startups?
The straightforward answer here is that if you're reading this, the right time is now.
Don't wait for the perfect time. The reality is that early-stage startups are unfortunately particularly vulnerable to cyberattacks, precisely because threat actors know they often lack even basic security practices.
Plus, it's always better to start building your security program early on so it can grow in alignment with your needs as your startup scales. Implementing a robust information security program after growth involves even more time, money, and resources to catch up.
How MSSPs Can Accelerate Cybersecurity for Startups in 2025
Hiring an external security team can substantially help organizations, especially in the early stages.
Virtual CISOs at organizations like Rhymetec have extensive experience balancing budgetary needs, usability, and security for start-up cybersecurity programs. It's not an easy balance, but leveraging an experienced partner can deliver huge amounts of specialized talent without the need to spend millions of dollars on an in-house security team.
Managed Security Services Providers like Rhymetec have dozens of professionals across security disciplines like cloud security, compliance, web application security, penetration testing, and others. They have the experience putting these skills to work for startups in a way that drives real security outcomes as you scale while also keeping your budget in mind.
To learn more about how our team can accelerate your security while keeping your budget in mind, contact us for more information.
About The Author: Metin Kortak, CISO
Metin Kortak is the Chief Information Security Officer at Rhymetec. Metin began his career working in IT security and gained extensive knowledge of compliance and data privacy frameworks such as SOC 2, ISO 27001, PCI, FedRAMP, NIST 800-53, GDPR, CCPA, HITRUST and HIPAA. He joined Rhymetec to build data privacy and compliance as a service offering. Under Metin's leadership, these offerings have grown to more than 200 customers, positioning the company as a leading SaaS security service provider in the industry.
If your company is exploring SOC 2 compliance, one of the first questions you may be wondering is—how long does it take to get SOC 2 compliance? The SOC 2 readiness and audit process can take anywhere from 3-12 months to complete. But with the support of a vCISO, service organizations can typically achieve SOC 2 compliance in half the time it would take them to navigate the process alone.
SOC 2 Readiness and Audit Timelines: How Long Does it Take to Get SOC 2 Compliance?
The SOC 2 compliance process generally takes between 3 to 12 months. This estimate includes the time it takes to prepare for an audit, undergo an audit, and receive a SOC 2 audit report. The timeline varies based on your team’s knowledge and expertise, available resources, the nature of your services, the size of your company, the auditor you choose to work with, and more.
SOC 2 Compliance Timeline: What to Expect & How Long A SOC 2 Audit Takes
Here’s what a SOC 2 compliance timeline looks like for clients that work with a Rhymetec vCISO versus those that choose to navigate the process alone. Remember: every organization is different, and yours will look a little different.
Phase 1: Prepare and Plan
During this phase, you’ll choose which type of SOC report you need (SOC 2 Type 1 vs Type 2), identify your compliance requirements, determine the trust services criteria to include in your SOC 2 report, assemble a team, allocate resources, and find an independent auditor.
Duration:
- With Rhymetec: 2 weeks.
- Without Rhymetec: 1-2 months.
Phase 2: Identify and Scope
This phase involves assessing your organization’s current readiness, benchmarking against all relevant SOC 2 Trust Services Criteria, SOC 2 training and employee education.
Duration:
- With Rhymetec: 2 to 3 weeks
- Without Rhymetec: 1 to 2 months
Phase 3: Assess and Implement
Now it’s time to conduct a risk assessment, implement controls, identify and address any outstanding issues, draft policies and procedures, implement monitoring, collect evidence, and ensure that your organization is ready to undergo a SOC 2 audit.
Duration:
- With Rhymetec: 1 to 3 months
- Without Rhymetec: 2 to 6 months
Phase 4: Prepare for Audit
Finally, you’ll need to complete a SOC 2 readiness assessment and address any final concerns before commencing a SOC 2 audit and receiving a SOC 2 report.
Duration:
- With Rhymetec: 4 to 6 weeks
- Without Rhymetec: 6 to 12 weeks
Phase 5: Official audit (2-6 weeks)
Your selected auditor will begin the official process of reviewing your company’s collected evidence and point-in-time snapshot.
How long does a SOC 2 audit take? From the kick-off of the audit to the SOC 2 report delivery, this process can take anywhere between 2-6 weeks. Factors that can impact your SOC 2 Audit timeline include:
- The scope of your audit
- Number of controls involved
- Evidence requests from your auditor
Once the evaluation is complete, your auditor will create and deliver your SOC 2 report. After the report is finalized, you can share it with vendors, partners, customers, and prospects.
How Rhymetec simplifies SOC 2 audits
The traditional SOC 2 process can take hundreds of hours to complete. Working with a Rhymetec vCISO removes the complexity and burden from SOC 2 compliance. Our team of cybersecurity experts has helped hundreds of SaaS and service-based organizations navigate the SOC 2 compliance process; we know what to look for, and we can guide you at every step of the way. How long it takes to get SOC 2 compliance varies, but our team has helped hundreds of companies cut down the amount of time needed substantially.
Not only do we consult you on how to achieve your SOC 2 goals, but provide the managed compliance services you need to get there. We like to say that we act on our own advice, so you can focus on other critical aspects of your business.
What a Rhymetec vCISO Can Do
Rhymetec’s team of cybersecurity experts acts as a member of your team and acts in the best interest of your company’s needs. With years of experience working among some of the most complex compliance regulations, we can provide you with strategic direction and hands-on support to simplify your SOC 2 readiness.
Tasks a vCISO can support in your compliance journey:
- Expert Audit and Compliance Guidance
- Security and Compliance Management
- Compliance Monitoring Software Deployment and Management
- InfoSec Policy and Procedure Development
- Human Resources Security Services
- Employee Access Management Services
- Vendor Management Services
- Incident Management and Response Services
- Security Questionnaire Fulfillment
- Security and Data Privacy Training Services
- Vulnerability Management and System Logging Services
- Risk Management Services
- Audit Management Services
- And More
Not only will a vCISO help you get ready for your audit and work with your auditor, but a Rhymetec vCISO can also support your post-audit maintenance goals to ensure ongoing compliance with SOC 2, and address stakeholder inquiries about security and compliance.
We give you the right level of vCISO support.
Whether your team needs high-level guidance from an experienced vCISO or hands-on support from our team of cybersecurity experts, Rhymetec can provide the level of support your organization needs to quickly achieve SOC 2 compliance.
To Learn More About Rhymetec's Services
Contact Our Team
What are SOC 2 compliance requirements, and do you really need SOC 2?
If you've been tasked with helping your organization become SOC 2 compliant, here’s everything you need to know about the process—what it is, why you need it, and how to prepare for an audit. If you have more specific questions, please feel free to contact our team:
What is SOC 2? A Beginner's Guide To SOC 2 Compliance Requirements
SOC 2 is a security compliance standard for service organizations. The purpose of SOC 2 compliance is to obtain proof that a company is storing and processing customer data in a secure manner. Also known as Service Organization Control Type 2, SOC 2 was developed by the American Institute of Certified Public Accountants (AICPA).
To achieve SOC 2 compliance, a company needs to undergo an audit to prove that it upholds high standards of data security based on five SOC 2 Trust Services Criteria: security, privacy, availability, confidentiality, and processing integrity.
Once completed, they receive a SOC 2 report. From there, audits should be conducted annually to assess ongoing adherence to SOC 2 compliance requirements and ensure compliance is maintained.
What is a SOC 2 Report?
A System and Organization Controls Report (aka SOC 2 report) is an attestation that your organization has the right security policies and procedures in place to manage and protect customer data properly.
A SOC 2 report indicates whether or not your organization’s security controls will operate as intended to mitigate risk and if they meet the specific Trust Services Criteria (TSC) identified by the scope of the audit.
There are two types of SOC 2 reports (SOC 2 Type 1 vs Type 2):
- Type 1: This report attests that an organization’s systems are properly designed at a specific point in time. The report describes the controls in use by an organization and confirms that the controls are properly designed and enforced.
- Type 2: This report includes everything that’s part of a Type 1 report, along with the attestation that the controls are operationally effective over a set period of time (usually 6-12 months).
Why Is Fulfilling SOC 2 Compliance Requirements Important?
Meeting SOC 2 compliance requirements is a business-enabler. It tells other companies that your organization maintains a high level of information security standards, which can help to win new business. Maintaining SOC 2 compliance also gives an organization the internal controls and procedures it needs to better protect customer data and prevent data breaches.
After all, clients and customers want to know that their information is safe and secure. SOC 2 is the security framework companies use to demonstrate their ability to protect customer data and tell the world that their security standards can be trusted.
Is SOC 2 Mandatory?
No, SOC 2 is not a requirement. SOC 2 is a voluntary compliance standard. However, many companies and customers consider SOC 2 compliance a prerequisite for the service providers and business partners they choose to work with. If this applies to your industry, you may lose business to your SOC 2-compliant competitors if you choose to forgo SOC 2 compliance.
Is SOC 2 a Certification?
No, SOC 2 is not a certification. It is an attestation that an organization meets industry-accepted security standards set out in the SOC 2 Trust Services Criteria.
How Much Does It Cost To Meet SOC 2 Compliance Requirements?
SOC 2 costs anywhere from $10,000 to $50,000. However, consider these figures a ballpark guide at best. The cost of fulfilling SOC 2 compliance requirements depends on the complexity of the project and a long list of other variables, including:
- The size of your company
- The nature of your services
- The complexity of the project
- The amount of resources you need
- The SOC 2 Trust Service Criteria you include in the audit
- …and more.
How Long Does SOC 2 Take?
Meeting all SOC 2 compliance requirements to obtain your report can take a mid-sized company anywhere from 3-12 months to complete. During this period, an organization will typically spend more time preparing for an audit than it will undergoing the actual SOC 2 audit phase. "How long does SOC 2 take" is a common question, but the answer varies:
Unfortunately, the time it takes to complete every item on an organization's SOC 2 checklist is difficult to project. Each company’s journey is different, and timelines are impacted by many variables.
With the support of a Rhymetec's vCISO service, organizations can typically achieve SOC 2 compliance in half the time it would take them to navigate the process alone.
What Are The SOC 2 Trust Service Criteria?
When an organization goes through a SOC 2 audit, it is assessed on its adherence to five Trust Service Criteria: Security, Availability, Processing Integrity, Confidentiality, and Privacy.
Security
Information and systems are protected against unauthorized access, unauthorized disclosure of information and damage to systems that could compromise the availability, integrity, confidentiality, and privacy of information or systems and affect the entity’s ability to meet its objectives.
Availability
Information and systems are available for operation and use to meet the entity’s objectives.
Processing integrity
System processing is complete, valid, accurate, timely and authorized to meet the entity’s objectives.
Confidentiality
Information designated as confidential is protected to meet the entity’s objectives.
Privacy
Personal information is collected, used, retained, disclosed and disposed of to meet the entity’s objectives.
Every organization needs to include Security in its SOC 2 report. From there, organizations can determine which of the other SOC 2 Trust Service Criteria it needs to include in its SOC 2 report.
Do You Need a SOC 2 Report?
Generally speaking, any organization providing a service for outsourcing the collection, processing, transmission, storing, organizing, maintenance, or disposal of customer information will benefit from a SOC 2 report.
But unless one of your existing or potential customers has proactively asked you to provide a SOC 2 report, you might be wondering if spending the time to meet SOC 2 compliance requirements is actually worthwhile.
If SOC 2 could help your organization win new business, then it’s usually a smart move to get a SOC 2 report before you need it—because the SOC 2 audit process can take months to complete.
For example, companies (usually service providers) that offer a B2B service or product and B2C organizations that handle sensitive customer information almost always need a SOC 2 report to work with other organizations.
What Are The Benefits of Meeting SOC 2 Compliance Requirements?
In addition to ensuring that your organization can effectively manage and protect customer data, a SOC 2 report can help in several ways.
Speed up the sales cycle
By eliminating security and compliance as a sales objection, SOC 2 can make it easier to quickly win new business and win the trust of larger, even enterprise companies.
Rhymetec can help you prepare a compliance package to support sales discussions.
Build customer confidence
Providing evidence your organization has met SOC 2 compliance requirements serves as a third-party seal of approval that your organization’s security controls are in place and effective. A SOC 2 report can help with customer retention and assure legal and risk departments that your service is secure.
Satisfy SOC 2 requests
Existing and potential partners may make a SOC 2 request from time to time. Having a valid SOC 2 report can help your team address these requests as soon as they are received.
Satisfy regulatory needs
Although SOC 2 itself is not a regulatory requirement, it does overlap with several regulation-based frameworks such as PCI DSS and HITRUST. Meeting SOC 2 compliance requirements can expedite enterprise compliance efforts as a whole.
Improve cybersecurity and compliance companywide
Undergoing the SOC 2 compliance process can create a framework for improving security practices and managing security risks across the company, which can help your organization avoid any surprises later on.
Create a framework for managing security risks across the company
SOC 2 can also build a strong security culture in your company’s operations. With defined cybersecurity, privacy, and compliance responsibilities and practices in place, security and compliance can become important, clearly defined processes for your entire team.
Gain a competitive advantage
Having SOC 2 compliance can also help you win deals against non-SOC 2 audited competition.
Accelerate investor, partner, and customer due diligence
Investors and other stakeholders often conduct due diligence before making business decisions. Having a SOC 2 audit report readily available can streamline the due diligence process, making it easier for stakeholders to assess the organization's security and compliance posture.
Increase staff productivity by reducing time spent on vendor questionnaires
SOC 2 reports are a valuable tool for organizations to demonstrate their commitment to security and compliance while reducing the administrative burden of responding to numerous security questionnaires. They provide a credible, standardized, and comprehensive assessment that can satisfy the security assurance needs of customers, partners, and stakeholders.
Fast Forward Your SOC 2 Journey
Our cybersecurity experts have helped hundreds of CTOs and decision-makers at SaaS companies work through the complex range of SOC 2 compliance requirements. When our clients first work with us, most of them tell a similar story: SOC 2 is a confusing, time-consuming process.
A Rhymetec vCISO can deliver the expertise, guidance, and support your team needs to prepare for and complete a SOC 2 audit, which means your team can stay focused on other important parts of your business.
To Learn More About Rhymetec's Services
SOC 2 Compliance Checklist:
How to Prepare for Your Audit
Although every company's SOC 2 journey is a little different, this SOC 2 compliance checklist breaks down the steps that most organizations will deal with as they prepare for an audit.
Our goal with this audit checklist is to give you a high-level overview of what you can expect during each stage of fulfilling the SOC 2 compliance requirements.
If you're planning to work your way through the SOC 2 process alone, grab a free copy of our SOC 2 Guide, which includes a detailed version of this SOC 2 checklist, time-saving best practices, and sample timelines.

What is a SOC 2 Checklist?
Preparing for a SOC 2 audit can usually be broken down into four phases. What are the phases and what do you need to do? How long does a SOC 2 audit take?
Here’s a high-level overview of what you can expect during each stage of the SOC 2 process:
SOC 2 Compliance Checklist - Phase 1: Prepare and Plan
Choose the right type of SOC 2 Report: Type 1 or Type 2
First, decide which type of SOC 2 report you need - SOC 2 Type 1 vs Type 2. The right audit report for your organization will depend on the requirements of the client or partner that has requested a SOC 2 audit report from your organization or what the standard is within the industry you serve.
If you need some help with this decision, get in touch with our team.
Determine the Trust Services Criteria for your SOC 2 report
SOC 2 compliance is based on five Trust Services Criteria. Every organization needs to comply with the first criteria (security). From there, your organization only needs to assess and document the other criteria that apply.
Assess which resources you’ll need
The resources you’ll need will depend on how closely your organization already aligns with SOC 2 security controls.
Get buy-in for the project
SOC 2 is a big project. Make sure your organization’s leadership teams understand the value of SOC 2 and are ready to provide the resources and budget you need to achieve SOC 2 compliance.
Assemble a team responsible for the project
Assemble a team responsible for the project. SOC 2 compliance typically requires input and representatives from IT, security, legal, and management. Your team should be expected to allocate a few hours weekly until you obtain your SOC 2 Type 2 report.
Create a SOC 2 project plan
Next, draft your SOC 2 project plan, outlining tasks, responsibilities, and deadlines.
Find and hire an auditor
You’ll also want to find a qualified SOC 2 auditor ASAP. Don’t wait until you’ve finished your SOC 2 preparations to complete this step. Finding a qualified auditing body early on allows you to communicate your control requirements and ensure that the auditor’s schedule can accommodate your organization’s timelines.
At Rhymetec, we connect clients to independent auditors during the initial stages of working together. However, if you’re working through SOC 2 yourself and you need to find an auditor, check out our list of vetted auditors registered with the American Institute of Certified Public Accountants (AICPA).

Phase 2: Identify and Scope
Assess your organization’s current readiness
Perform a gap assessment to determine which internal controls, processes, and practices your organization has already implemented and identify those you need to put into place.
Benchmark your organization against the Security Trust Services Criteria
Identify and implement any internal controls and procedures that you don’t yet meet (access controls, encryption, monitoring, and more) across several categories of security. Make sure to document control descriptions, policies, and procedures and assign ownership of security controls to specific team members.
Benchmark your organization against all other relevant Trust Services Criteria
Identify and implement each of the applicable controls in the other Trust Services Criteria that you identified in your initial framework, but that you have not yet implemented. Once controls are in place, begin mapping controls to the Trust Services Criteria.
Educate your employees about the upcoming SOC 2 audit and their roles in compliance
Ensure that your staff is aware of the SOC 2 requirements and their roles in compliance. It is recommended to provide training on compliance requirements and awareness programs to reinforce security best practices.
Phase 3: Assess and Implement
Conduct a risk assessment
One of the most critical pieces of your SOC 2 checklist should be conducting a robust risk assessment.
At a high level, a risk assessment in the context of SOC 2 readiness involves evaluating and documenting the potential risks to an organization's systems and data, specifically focusing on the Trust Services Criteria relevant to SOC 2 compliance. A risk assessment will help guide your control implementation efforts.
Implement controls
When implementing controls for SOC 2 compliance, it's crucial to document control testing results and promptly address any identified deficiencies through corrective actions.
Draft policies and procedures that adhere to SOC 2 standards
Your team will need to draft and manage a comprehensive set of information security policies, standards, and guidelines in accordance with business demands, compliance standards, and industry best practices.
Implement monitoring
Implement ongoing monitoring and review processes to continuously assess your controls and make necessary adjustments. You should regularly update your documentation to reflect changes and improvements.
Document compliance
Keep your documentation up to date and ensure it accurately reflects your organization's current practices and controls.
Collect evidence
Collect evidence that demonstrates compliance with the Trust Services Criteria. This evidence may include logs, reports, and records related to security incidents, access controls, change management, and more.
Ensure audit preparedness
Prepare for the SOC 2 audit by conducting a preliminary readiness assessment, ensuring the completeness and accuracy of control documentation, and providing necessary training to employees regarding their roles during the audit.
Phase 4: Prepare for Audit
Complete a SOC 2 readiness assessment
Share your control documentation with the auditor for their preliminary review and work with your auditor to determine if you have met the minimum standards to undergo a full compliance audit.
Address any final concerns
If your readiness assessment indicates that there are SOC 2 controls you need to address before your audit, complete these requirements.
Undergo a SOC 2 Audit
It’s time to work through a full audit with your chosen SOC 2 auditor. This may involve weeks or longer of working with your auditor to provide the documentation they need. When you complete your audit, the auditor will present you with your SOC 2 report to document and verify your compliance.

SOC 2 Checklist - Phase 5: Maintain Compliance Annually
Continuously monitor SOC 2 compliance and controls
Establish a system to monitor your compliance and identify any breaches of your compliance. These can occur during system updates and changes. Control monitoring should be done on a daily basis—if a control fails, immediate remediation will need to be put into place to avoid gaps in compliance.
Address any gaps immediately
Rather than waiting until your next audit, immediately address any gaps in your compliance that arise.
Conduct user onboarding awareness training
By integrating security awareness training into the user onboarding process, organizations can strengthen their security posture, reduce risks, and demonstrate their commitment to protecting sensitive information, all of which are essential for compliance.
Undergo an annual SOC 2 audit as the final step of your SOC 2 checklist
Last but not least for your SOC 2 checklist, it’s a good idea for service organizations to perform a SOC 2 audit on an annual or semi-annual basis.
Technically, your SOC 2 report does not expire. But companies will generally consider the information in a SOC 2 report to be outdated after 12 months because there’s no evidence that you’ve maintained your SOC 2 compliance without an annual or semi-annual audit.
Fulfill Your SOC 2 Checklist With Rhymetec
The process to become SOC 2 compliant can be confusing and resource-heavy at the best of times. If you hit a wall and need some help with SOC 2, book a chat with our team.
Rhymetec’s team of cybersecurity experts has helped hundreds of CTOs and SaaS organizations navigate the SOC 2 process. Our vCISO service provides the exact level of support your team needs to streamline the process and fulfill your SOC 2 checklist ASAP.
To Learn More About Rhymetec's Services
Contact Our Team