The attack surface has changed. Organizations rely on dozens of cloud apps, APIs, and third-party integrations, and attackers are already using AI to find and exploit weaknesses at machine speed. Demand for penetration tests is at an all-time high. This means pentesters need to arm themselves with new ways to get the job done to keep pace with AI attacks.
That’s why Rhymetec is partnering with XBOW, the world’s leading autonomous pentesting platform. Together, we bring clients a new standard of security:
- AI-powered and fully autonomous: XBOW deploys hundreds of specialized agents in parallel working side by side with human penetration testers.
- On demand: Run tests as often as you need, integrated directly into your development cycle.
- Surgically precise: Every vulnerability XBOW discovers comes with a full proof of concept for exploitation, eliminating false positives.
“The threat landscape isn’t static. Attackers are already leveraging automation, and defenders must respond in kind. By partnering with XBOW, we can now give our clients the speed of autonomous testing with the human guidance and compliance expertise they trust Rhymetec for.” — Justin Rende, CEO, Rhymetec
“The rise of AI-powered offense demands that defenders move much faster, while also increasing the depth of their analysis. The solution is to automate all routine work with XBOW's autonomous AI hacker, so human experts can focus on the deep security design questions. This way, the human security team gains super powers, being able to move with unprecedented speed and depth. We're delighted to partner with the team of experts at Rhymetec, perfectly complementing XBOW to deliver a complete security solution.” — Oege de Moor, CEO, XBOW
What to Expect
According to Verizon’s 2025 Data Breach Investigations Report, it still takes a median of five weeks for known flaws to be remediated, and nearly half of critical edge-device vulnerabilities remain unpatched. This lag time is untenable when adversaries are exploiting at AI speed.
With Rhymetec and XBOW, organizations gain the ability to:
- Continuously validate security posture across web apps, APIs, and third-party integrations.
- Accelerate compliance readiness by feeding validated findings directly into Rhymetec’s compliance services.
- Scale offensive testing affordably with on-demand automation, reserving human experts for complex, business-logic vulnerabilities.
For Startups and Growth-Stage Companies
For early-stage teams, every security decision feels like a trade-off between speed, cost, and credibility. With this partnership, startups no longer have to choose.
- Accelerated Security Reviews: XBOW completes penetration tests in hours, helping founders meet buyer and investor security expectations without waiting weeks.
- Built-In Compliance Readiness: Validated findings flow directly into Rhymetec’s compliance services, reducing audit stress and building customer trust from day one.
- Enterprise-Grade Security at Startup Speed: On-demand AI-driven testing delivers enterprise-level assurance at a fraction of the cost, giving startups security maturity without slowing growth.
For Mid-Market and Enterprise Organizations
As organizations scale, so does the complexity of their attack surface — more applications, more integrations, and more pressure to deliver secure products without slowing down. Traditional testing simply can’t cover it all.
With XBOW and Rhymetec, security leaders get:
- Expanded Coverage Across Applications: Autonomous agents extend testing across web apps and APIs, including the third-party integrations that are often overlooked.
- Human Expertise Where It Counts: Automated testing handles the routine, giving Rhymetec’s security experts more time to focus on complex business-logic vulnerabilities.
- Ongoing Validation: Findings arrive pre-validated with exploit proof, and fixes can be retested on demand — ensuring vulnerabilities are truly closed, not just logged.
A Smarter Way Forward
Our combined approach blends autonomous agents that never tire with human experts who bring judgment, context, and compliance guidance. The result: faster closure of common vulnerabilities, stronger defenses against subtle flaws, and the confidence that your security program can keep pace with modern development velocity.
[video width="1920" height="1080" mp4="https://rhymetec.com/wp-content/uploads/2025/09/XBOW_Clip.mp4%22][/video]
Your attack surface has changed. Your pentesting strategy should too.
👉 Contact Rhymetec to learn how AI-powered penetration testing with XBOW can strengthen your security program and accelerate compliance.
XBOW is an AI-powered penetration testing platform that scales offensive security in hours. Delivering human-level security testing at machine speed, XBOW helps organizations discover vulnerabilities before attackers can exploit them. Ranked as #1 on the HackerOne leaderboard in the U.S., XBOW was founded by the creators of GitHub Copilot and GitHub Advanced Security, and is backed by Sequoia and Altimeter.
Rhymetec is the trusted partner of over 1,500 organizations globally in all of their cybersecurity and compliance needs. Founded in NYC in 2015, Rhymetec delivers information security programs that are effective, compliant, and built to scale with your business. Our fully in-house team of dedicated vCISOs and seasoned penetration testers manages every phase of your cybersecurity and compliance journey, enabling you to focus on what matters most — growing your business.
The attack surface has changed. Organizations rely on dozens of cloud apps, APIs, and third-party integrations, and attackers are already using AI to find and exploit weaknesses at machine speed. Demand for penetration tests is at an all-time high. This means pentesters need to arm themselves with new ways to get the job done to keep pace with AI attacks.
That’s why Rhymetec is partnering with XBOW, the world’s leading autonomous pentesting platform. Together, we bring clients a new standard of security:
- AI-powered and fully autonomous: XBOW deploys hundreds of specialized agents in parallel working side by side with human penetration testers.
- On demand: Run tests as often as you need, integrated directly into your development cycle.
- Surgically precise: Every vulnerability XBOW discovers comes with a full proof of concept for exploitation, eliminating false positives.
“The threat landscape isn’t static. Attackers are already leveraging automation, and defenders must respond in kind. By partnering with XBOW, we can now give our clients the speed of autonomous testing with the human guidance and compliance expertise they trust Rhymetec for.” — Justin Rende, CEO, Rhymetec
“The rise of AI-powered offense demands that defenders move much faster, while also increasing the depth of their analysis. The solution is to automate all routine work with XBOW’s autonomous AI hacker, so human experts can focus on the deep security design questions. This way, the human security team gains super powers, being able to move with unprecedented speed and depth. We’re delighted to partner with the team of experts at Rhymetec, perfectly complementing XBOW to deliver a complete security solution.” — Oege de Moor, CEO, XBOW
What to Expect
According to Verizon’s 2025 Data Breach Investigations Report, it still takes a median of five weeks for known flaws to be remediated, and nearly half of critical edge-device vulnerabilities remain unpatched. This lag time is untenable when adversaries are exploiting at AI speed.
With Rhymetec and XBOW, organizations gain the ability to:
- Continuously validate security posture across web apps, APIs, and third-party integrations.
- Accelerate compliance readiness by feeding validated findings directly into Rhymetec’s compliance services.
- Scale offensive testing affordably with on-demand automation, reserving human experts for complex, business-logic vulnerabilities.
For Startups and Growth-Stage Companies
For early-stage teams, every security decision feels like a trade-off between speed, cost, and credibility. With this partnership, startups no longer have to choose.
- Accelerated Security Reviews: XBOW completes penetration tests in hours, helping founders meet buyer and investor security expectations without waiting weeks.
- Built-In Compliance Readiness: Validated findings flow directly into Rhymetec’s compliance services, reducing audit stress and building customer trust from day one.
- Enterprise-Grade Security at Startup Speed: On-demand AI-driven testing delivers enterprise-level assurance at a fraction of the cost, giving startups security maturity without slowing growth.
For Mid-Market and Enterprise Organizations
As organizations scale, so does the complexity of their attack surface — more applications, more integrations, and more pressure to deliver secure products without slowing down. Traditional testing simply can’t cover it all.
With XBOW and Rhymetec, security leaders get:
- Expanded Coverage Across Applications: Autonomous agents extend testing across web apps and APIs, including the third-party integrations that are often overlooked.
- Human Expertise Where It Counts: Automated testing handles the routine, giving Rhymetec’s security experts more time to focus on complex business-logic vulnerabilities.
- Ongoing Validation: Findings arrive pre-validated with exploit proof, and fixes can be retested on demand — ensuring vulnerabilities are truly closed, not just logged.
A Smarter Way Forward
Our combined approach blends autonomous agents that never tire with human experts who bring judgment, context, and compliance guidance. The result: faster closure of common vulnerabilities, stronger defenses against subtle flaws, and the confidence that your security program can keep pace with modern development velocity.
Your attack surface has changed. Your pentesting strategy should too.
👉 Contact Rhymetec to learn how AI-powered penetration testing with XBOW can strengthen your security program and accelerate compliance.
XBOW is an AI-powered penetration testing platform that scales offensive security in hours. Delivering human-level security testing at machine speed, XBOW helps organizations discover vulnerabilities before attackers can exploit them. Ranked as #1 on the HackerOne leaderboard in the U.S., XBOW was founded by the creators of GitHub Copilot and GitHub Advanced Security, and is backed by Sequoia and Altimeter.
Rhymetec is the trusted partner of over 1,500 organizations globally in all of their cybersecurity and compliance needs. Founded in NYC in 2015, Rhymetec delivers information security programs that are effective, compliant, and built to scale with your business. Our fully in-house team of dedicated vCISOs and seasoned penetration testers manages every phase of your cybersecurity and compliance journey, enabling you to focus on what matters most — growing your business.
Justifying the return on cybersecurity investments can be hard. Some things are relatively easy, especially with the help of tools like compliance automation platforms. You have to comply with legal requirements and customer demands to see your SOC 2 report, but what about security that goes beyond regulatory requirements?
In a business full of competing interests, managers asking for new hires, and the marketing team wanting to spend additional money, security often falls by the wayside - but it shouldn't.
That's one of the reasons at Rhymetec we love checking out Verizon's annual Data Breach Investigation Report (DBIR). Verizon's DBIR shows exactly why companies need to move beyond compliance and implement proactive controls.
Regulators are often years behind the latest trends in the industry - companies that just focus on compliance often fail to implement safeguards and controls that could save their business millions of dollars in lost business, fines, and legal fees.
So, what are the big takeaways from this year's DBIR? Well, there are quite a few:
Generative AI, Compliance, and Accidental Leaks
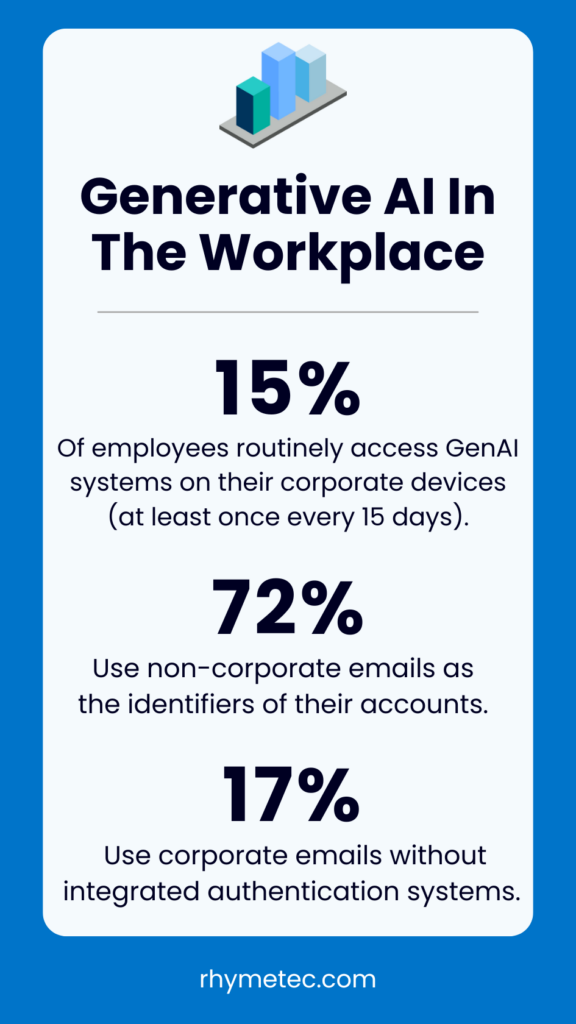
You almost certainly have employees at your company feeding data into AI models that you don't know about. One of the findings that should be the most alarming to information security leaders is that, according to the DBIR:
"15% of employees were routinely accessing GenAI systems on their corporate devices (at least once every 15 days). Even more concerning, a large number of those were either using non-corporate emails as the identifiers of their accounts (72%) or were using their corporate emails without integrated authentication systems in place (17%), most likely suggesting use outside of corporate policy."
Many organizations pick one or two AI vendors and work with those, and accept a certain degree of risk. However, employees signing up directly for generative AI applications can pose severe risks, particularly to organizations that deal with highly sensitive intellectual property, regulated data such as health records, or even national security and classified data.
For example, imagine an employee at a defense contractor decides to use DeepSeek to analyze CUI (controlled unclassified information) that a contractor sends them. They likely unknowingly just sent that data directly to China.
Getting a handle on "shadow SaaS", and particularly which AI applications employees may be sending sensitive data, is likely to be one of the most important issues vexing information security teams in the next five years.
Third-Party Risk Remains Highly Relevant in The 2025 Verizon Data Breach Report
Another key finding in the 2025 DBIR that security professionals should be paying close attention to is the dramatic increase in third-party involvement in breaches. According to Verizon's analysis, third-party involvement in breaches doubled from 15% to 30% in just one year. This isn't merely a statistical blip - it represents a fundamental shift in how attackers are approaching your organization's security perimeter.
As in all things in life, there are tradeoffs. As organizations increasingly adopt convenient SaaS solutions to solve various business challenges, in many cases, they unwittingly dramatically expand their attack surface (sometimes even the business doesn't know what their attack surface is, such as with shadow generative AI use).
The report specifically highlights how several high-profile breaches in services like Change Healthcare, CDK Global, and Blue Yonder exposed sensitive data and created substantial business interruption events across entire industries:
Healthcare providers couldn't process claims, auto dealerships lost access to their systems, and retailers and food services companies found themselves unable to manage inventory. When your critical business functions rely on third-party SaaS providers, their security posture becomes your operational vulnerability.
While compliance frameworks like SOC 2 have recognized third-party risk for years, the real-world impact is growing faster than many organizations' vendor management programs can adapt.
This data should serve as a wake-up call: Today's interconnected business ecosystem requires a much more proactive approach to vendor security assessment, continuous monitoring, and contingency planning. Organizations that fail to evolve beyond "check the box" vendor management will increasingly find themselves dealing with the consequences of their partners' security failures.
Malware Is Fueling Identity-Based Attacks
On page 54 of the report is perhaps one of the most interesting insights of the 2025 DBIR. In a section titled "Infostealers Galore", Verizon discusses one of the most prominent threats to organizations today - infostealer malware.
Infostealers are a type of malware that infects a victim's computer and siphons all of the passwords and session cookies the victim has saved on their browser, sessions for applications such as Discord, crypto wallet keys, autofill data, and basically any other sensitive or valuable lightweight data from the device. This data is then sent back to the threat actor's infrastructure, where individual victims' information is sold as an "infostealer log" containing one victim's data.

As you can imagine, there is a trove of high value information for threat actors to leverage within this data to include session cookies which can be used to hijack active sessions to facilitiate account takeover attacks for major web applications and e-commerce companies, crypto wallet keys which can allow the threat actor to steal currency, and even credit card data from autofills which can facilitate fraud.
However, this malware can also grab corporate emails and passwords for SaaS applications, VPN's, corporate bank accounts, and other critical information. Verizon estimates that 30% of the tens of millions of logs out there come from devices that are corporate-owned, an absolutely astounding figure.
A discerning observer might ask an obvious question: Does the prevalence of corporate credentials, session cookies, and information available in the stealer log ecosystem enable ransomware groups and other similar threat actors?
Well, Verizon has the answer there, too.
"By examining some of the victims posted to the ransomware extortion sites, we found that 54% of the victims had their domains show up in at least one infostealer log or in marketplace postings, and 40% of those logs contained corporate email addresses." - Verizon Data Breach Report 2025, page 57.
This type of analysis is critical, as threat actors are continuously evolving their tactics, techniques, and procedures in response to improvements in organizational cybersecurity. Oftentimes, threat actors will use whatever is easiest, and active sets of corporate credentials and session cookies floating around in the criminal ether is indeed a pretty easy way to get access to some high-value systems.
Ransomware Is On the Rise, Sort Of
Speaking of ransomware, many organizations make the mistake of believing that they are too small for ransomware groups and threat actors to target.
However, this belief couldn't be further from the truth. One of the most interesting and relevant findings from the DBIR was the data around ransomware attacks in 2024. While attacks continue to rise, victim behavior and attacker strategies are evolving in notable ways.
Ransomware incidents jumped dramatically, showing a 37% increase from last year. These attacks now represent 44% of all data breaches analyzed - up from 32% in the previous report. Nobody expected ransomware to go away, but this data shows that even the notable law enforcement takedowns of Lockbit, Black Cat, and other high-profile ransomware groups has at best dented this highly financially lucrative criminal operation.
However, it's worth digging in a bit on the ransomware piece of the report because the increase in ransomware as a proportion of all attacks doesn't tell the whole story. The reports section on ransom payments shows a potential silver lining:
Both the frequency and size of ransom payments are decreasing. The median ransom payment dropped to $115,000 in 2024, down from $150,000 in 2023. More significantly, 64% of victims now refuse to pay ransoms altogether - a substantial increase from 50% just two years ago.
While the report doesn't directly make the connection, organizations improving backup and recovery combined with defensive measures may be fueling another trend - the increased targeting of small and midsize businesses by ransomware operators.
Perhaps the most alarming finding is how severely ransomware affects smaller organizations. While ransomware appears in 39% of breaches at large enterprises, it's present at a staggering 88% of breaches at SMBs.
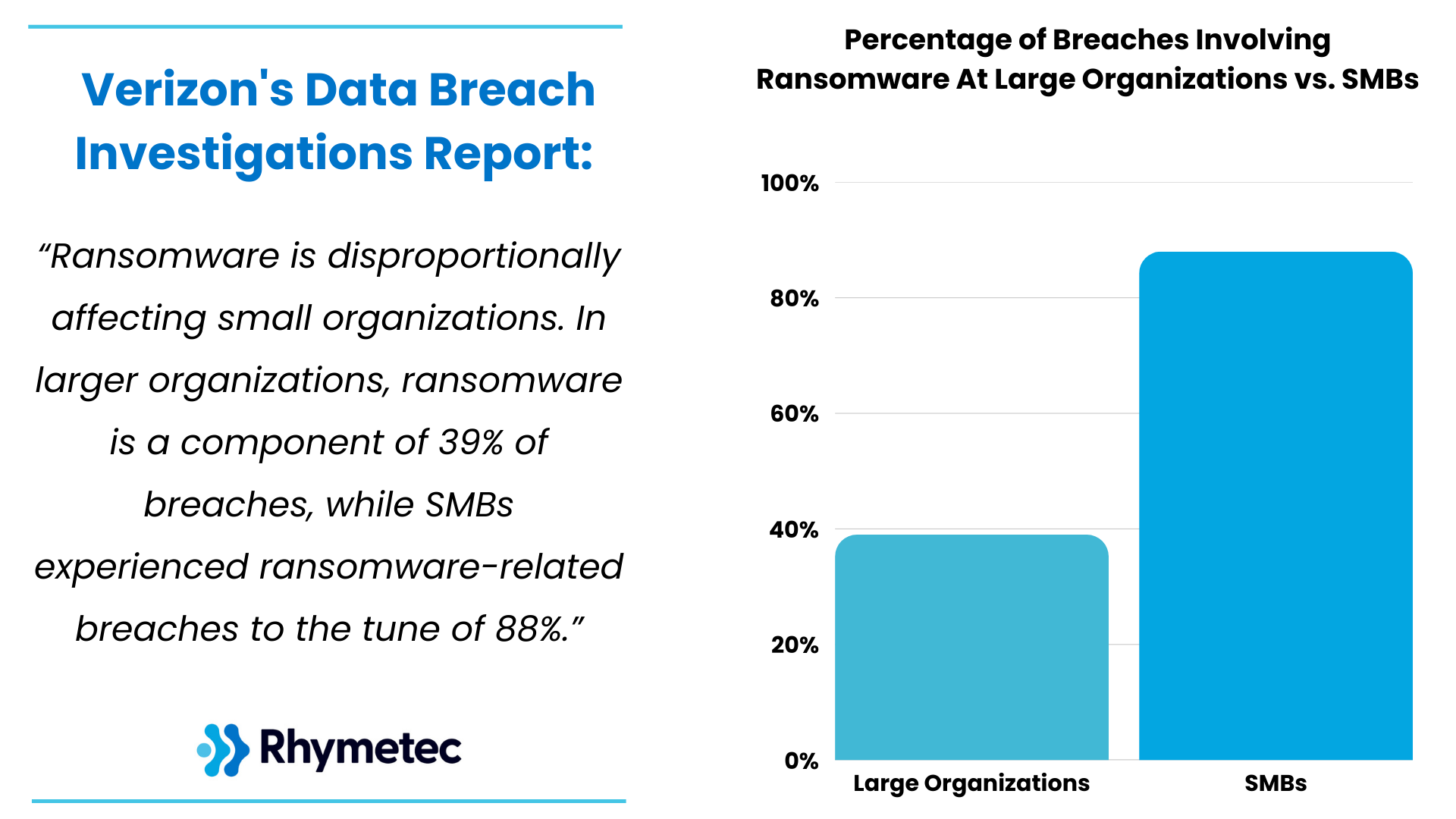
This disparity likely reflects the resource gap in cybersecurity preparedness. Smaller organizations typically have less robust backup solutions, fewer security controls, and limited incident response capabilities, making them both easier targets and more likely to suffer catastrophic impacts.
Concluding Thoughts: The Verizon Data Breach Report 2025
The 2025 Verizon Data Breach Report paints a clear picture of an evolving threat landscape that demands more than just a checkbox approach to security. Compliance frameworks like SOC 2 and ISO 27001 provide a valuable foundation, but going beyond them is essential for organizations to protect themselves from sophisticated ransomware groups and other threat actors.
The data tells a compelling story: Third-party risks have doubled, credential theft via infostealers is directly fueling ransomware attacks, and shadow AI usage presents entirely new vectors for data loss. These threats are often moving faster than regulatory and best practice frameworks can adapt.
At Rhymetec, we recommend that organizations build their compliance foundation with targeted security investments that address these emerging threats:
- Implement continuous monitoring for external threats.
- Develop comprehensive controls for third-party risk management that go beyond questionnaires.
- Establish clear policies and technical controls for AI platform usage.
- Prioritize edge device security given their increased targeting by threat actors.
- Develop security strategies that account for the human element, which remains involved in 60% of breaches.
The most successful organizations will be those that view compliance as the starting point, not the destination, of their security journey. And most importantly, those who stay educated on how the threat landscape is shifting over time.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We've worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
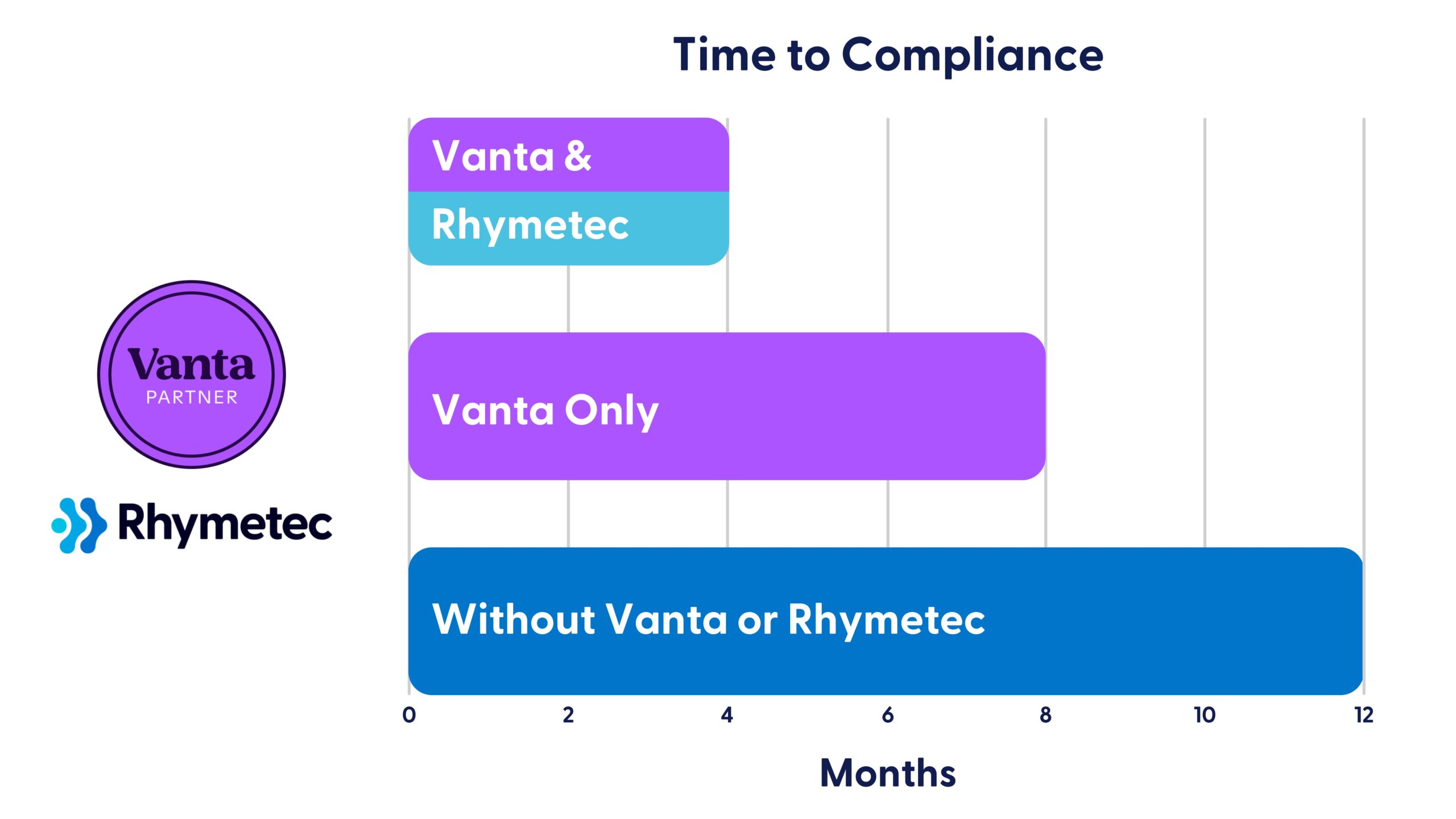
So, you're considering SOC 2 or ISO 27001 for the first time - and realizing just how much time and expertise it takes to actually get there. That's where Vanta (and Rhymetec!) comes in:
Vanta automates 90% of compliance monitoring through integrations with 300+ systems, real-time control insights, and automated evidence collection—enhancing your visibility into your security posture. Rhymetec handles the hands-on readiness tasks for you. The combination of Vanta with our tailored services delivers a faster, more manageable path to audit success.
Our team of experts at Rhymetec, by leveraging Vanta for you, accelerates every step of your compliance journey from the initial scoping phase to auditor handoff. We've helped over 1,000 organizations efficiently meet their security and compliance goals with this method. Here's how Vanta works in conjunction with our services, and how the platform can benefit you immediately, especially if you are early on in the process of compliance:
Vanta Automates Compliance Workflows
Vanta automates the visibility into tasks required to build a compliance program. One of the main value adds of Vanta is that it will handle the repetitive work for you and give you back your time to focus on what really matters - growing your business. Here's how it works, particularly for organizations early in their compliance journey:
Using Vanta circumvents the need to even get started on tedious manual spreadsheets and checklists. Instead, Vanta enables organizations to jump right in and leverage its capabilities, including system integrations and automated collection of evidence.
For instance, a startup pursuing SOC 2 may need to prove that it restricts employee access to production systems, monitors for security incidents, and keeps its asset inventory up-to-date and in line with SOC 2 requirements. Vanta connects to systems including AWS, GitHub, Google Workspace, and Okta to automatically accomplish the following:
- Display passing controls.
- Simplify policy management.
- Collect the evidence needed for an audit.
It also includes pre-built policy templates for every framework, so teams can work from a baseline and avoid having to write everything from scratch. Leadership is able to track compliance status in real time and improve visibility tied to audit preparation for employees—resulting in efficiency and reduced time to compliance.
Who Uses Vanta And Why
Vanta is primarily used by fast-growing, cloud-native organizations that are seeking to meet relevant security and data privacy requirements in the most efficient way possible. Often, these organizations are trying to avoid dedicating excessive internal resources to manual compliance work. However, we’ve seen companies from all sizes—startup to enterprise—with varying environments—such as multi-cloud and hybrid—utilize Vanta to streamline their compliance efforts.
Some of the main reasons companies opt to use Vanta are to help them:
- Reduce their audit timelines.
- Improve visibility into their security posture.
- Lower the overall cost of compliance.
Vanta connects to the tools you use via API, the cloud infrastructure you're set up in, and your internal systems to give you a complete view of your security and compliance.
This eliminates the need for fragmented spreadsheets and manual checklists, providing leadership more control over compliance progress and unburdening technical teams that are already stretched thin.
Another core value add is that Vanta enables a single source of truth for audit readiness, helping leaders and your sales team demonstrate you're where you need to be in terms of security and compliance to auditors, customers, your partners, and other stakeholders.
What Does Vanta Do? Vanta Supports Continuous Compliance
It's important to know going into your compliance journey that compliance doesn’t stop after one audit.
Frameworks like SOC 2, ISO 27001, and HIPAA require ongoing evidence of control effectiveness, which means you need continuous monitoring rather than only point-in-time documentation.
Vanta is built precisely to support this model. It runs in the background, constantly monitoring your infrastructure and systems for changes that could impact compliance. It will flag any issues in real time, such as expired access, unapproved software, or missing security training. The platform centralizes the evidence you'll need to show controls are operating continuously.
This approach replaces manual check-ins and periodic reviews with continuous visibility. Combined with Rhymetec's guidance and remediation support, clients stay audit-ready year-round without having to rebuild compliance work from scratch each cycle.
Vanta Streamlines The Work of Cybersecurity & Compliance Experts
Vanta automates the visibility into tasks (While Rhymetec can support the completion of them) that are most likely to slow down compliance teams, allowing the experts to focus on higher-impact and more specific work. Tasks like collecting screenshots, tracking evidence, and managing spreadsheets shift to automated processes within the platform.
For Rhymetec's team, the platform provides a centralized source of truth and allows us to spend more time analyzing results and guiding clients through control implementation. Our team uses Vanta in every step of the compliance automation process on your behalf. By handling repetitive tasks and bringing issues to our attention automatically, Vanta allows us to carry out a more efficient process to compliance readiness for your organization.
How Rhymetec Leverages Vanta To Deliver Compliance - Fast
Rhymetec leverages Vanta as a core part of our compliance delivery model.
Our approach combines all of the benefits of automation with hands-on cybersecurity expertise to shorten the path to audit readiness. Our team configures Vanta for your systems and selected framework. We work hard to eliminate common setup delays and create alignment between compliance goals and actual business operations.
Once deployed, Vanta automatically monitors your cloud infrastructure and systems for compliance-related activities. But automation alone doesn’t get you audit-ready. That’s where Rhymetec comes in. After the initial setup, our team steps in to:
- Interpret and prioritize Vanta’s findings based on your unique business needs
- Remediate flagged issues with hands-on support — not just advice
- Tackle all remaining manual components like policy creation, access reviews, evidence collection, and control implementation
The combination of automated and manual work keeps the momentum going and gets clients through readiness assessments and audits on a much faster timeframe. By managing both Vanta and the 'hands-on' components of compliance readiness work on your behalf, we’re able to accelerate every phase of the compliance process.
Why Pairing Vanta and Rhymetec Delivers Better Outcomes
Most frameworks require an array of expert judgment, manual implementation of certain controls, and a level of preparation that automation can't complete 100% of on its own.
Rhymetec fills that gap by managing the manual work and aligning Vanta specifically to your environment. We interpret control requirements, resolve flagged issues, write custom policies, manage communication with auditors on your behalf, and more.
By using Vanta for compliance automation - and Rhymetec filling in the gaps for you when needed - clients move faster and meet their compliance goals with less internal burden. Together, we consistently generate strong audit readiness and stronger security programs.
Accessing Vanta Through Rhymetec
Rhymetec is proud to offer Vanta (in conjunction with our Vanta compliance services) directly to clients who haven't yet selected a compliance automation platform.
Particularly in the case of clients early in their compliance journey, this vastly simplifies the buying process by providing both the technology and the services needed to meet requirements in one engagement. We give clients access to a world-class platform without requiring them to manage separate vendor relationships or navigate pricing and setup alone.
Our team at Rhymetec handles everything from the initial deployment and setup in Vanta to ongoing administration of the platform on your behalf. This allows you to adopt automation earlier, which will accelerate your compliance timelines and help you avoid missteps that a self-directed rollout could entail. Contact our team to learn more:
As an industry leader in cybersecurity and compliance, Rhymetec is proud to partner with Vanta to deliver a complete solution for modern businesses. As Vanta's 1st MSP partner, together, we fast-track compliance, strengthen your security posture, and reduce the time and effort needed to meet regulatory requirements.
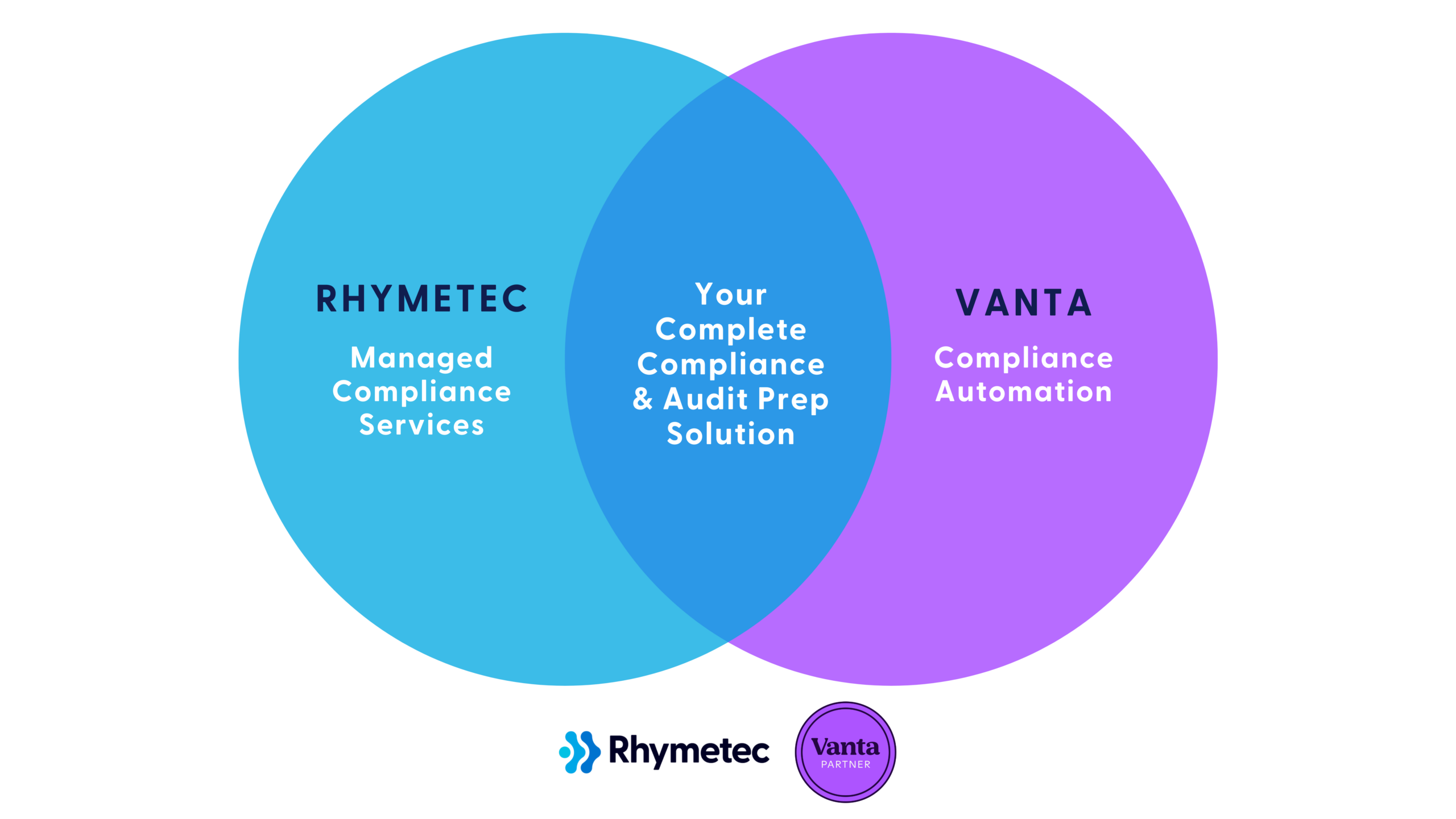
The Rhymetec + Vanta Advantage
Our team at Rhymetec leverages Vanta to transform compliance from a complex challenge into a strategic advantage for your business. Over the last decade, we've helped over 1,000 companies around the world meet their security and compliance goals.
With our joint services, you can:
1. Alleviate The Pressures of Audit Preparation
Vanta was built with auditors and the audit process top-of-mind. Rhymetec will ensure you have all the documents and evidence necessary for the audit itself, and manage the audit process using Vanta as a source of truth.
2. Access Continuous Security and Compliance Monitoring and Support
Vanta's automation capabilities help achieve ongoing compliance maintenance and management, while Rhymetec's vCISO services address ongoing security efforts and questionnaires, aiding new phases of growth.
3. Streamline Control Implementation With Vanta Compliance Services
Rhymetec implements controls required by the compliance framework selected by the client. Vanta plays a key role in this process for each control through system integrations and identification of areas for improvement.
Together, we provide a simplified approach to security and the compliance automation process. We work together to provide an automated and comprehensive solution, saving significant time and resources for you.
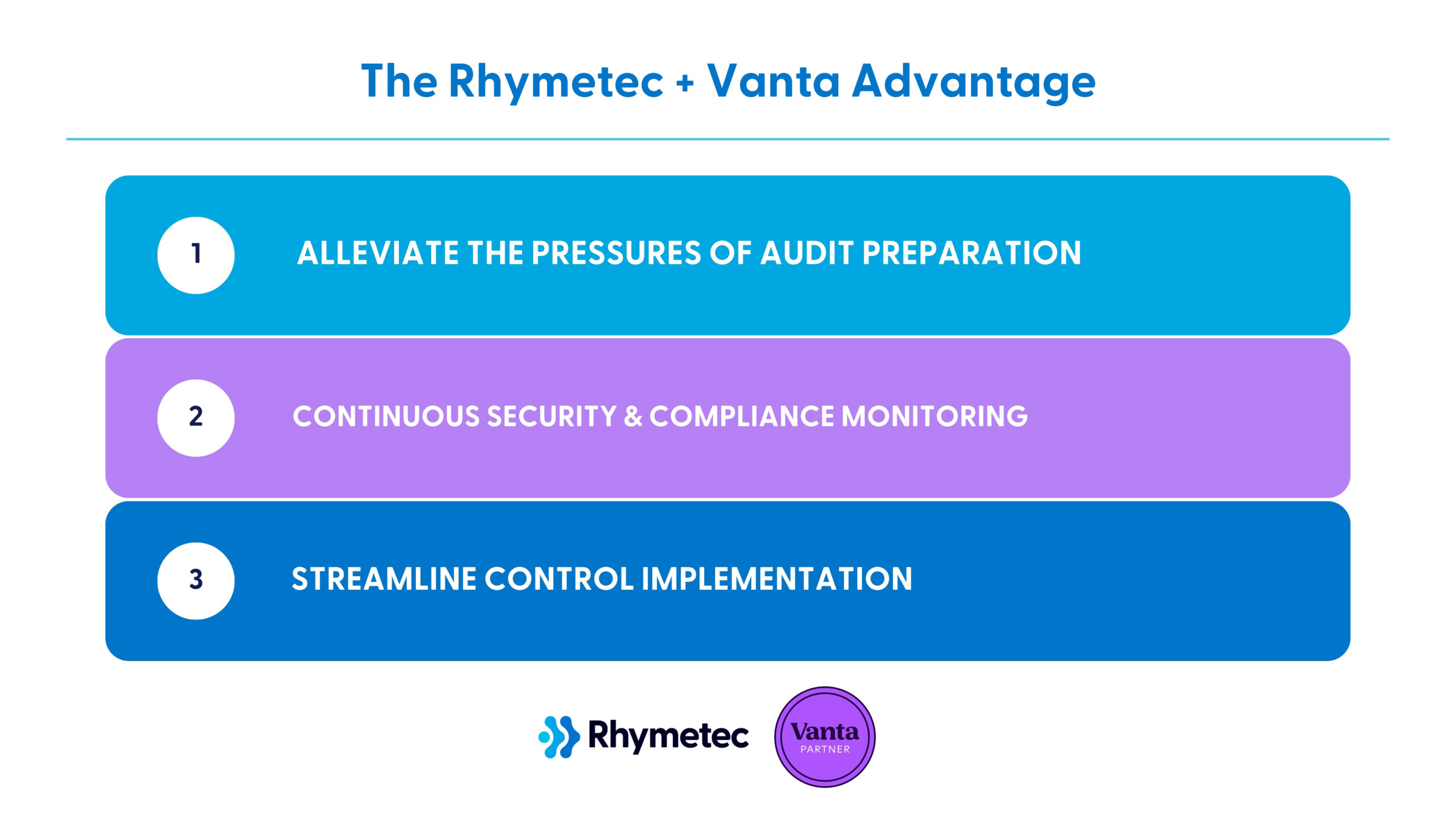
Our Vanta Compliance Services
Vanta Implementation and Deployment
Vanta automates 90% of compliance tasks through integrations with 300+ systems, real-time control monitoring, and automated evidence collection.
The Rhymetec team configures and deploys the platform on your behalf, integrating it with your infrastructure to maximize automation capabilities. We connect relevant systems, set up automated workflows, and customize policies to fit your organization and the selected compliance framework.
With Vanta deployment carried out by our experts, your team avoids the complexity of configuring integrations. From day one, we ensure accurate and reliable compliance monitoring and allow you to dramatically reduce the burden on your internal resources.
Compliance Framework Support From Start To Finish
Vanta provides pre-built controls for 20+ frameworks, including SOC 2, ISO 27001, HIPAA, and GDPR. It automates scoping and document management and provides a foundation for policy creation. The Rhymetec team aligns these automated capabilities with your business needs and your selected compliance framework, performing the tasks required for full compliance such as internal audits, tabletop exercises, and evidence preparation.
Managing compliance without a dedicated team can lead to missed controls or even doing too much and implementing unnecessary requirements. By handling the full compliance process, we eliminate uncertainty, accelerate your audit readiness, and ensure your documentation fully meets auditor expectations.
Continuous Optimization and Compliance Maintenace
Vanta's continuous monitoring identifies failing controls, missing security measures, and real-time compliance risks. Automated notifications provide alerts to potential issues, and remediation workflows drive fast resolution.
Our team at Rhymetec oversees these alerts, interprets risk impacts, and executes the manual corrections on your behalf so you can maintain compliance.
Ongoing compliance management is resource-intensive. Without expert oversight, organizations risk falling out of compliance between audits. With our team handling continuous monitoring and remediation, your organization stays audit-ready, reduces compliance drift, and proactively addresses any security gaps.
Penetration Testing To Meet Audit and Regulatory Requirements
Many voluntary frameworks as well as legal requirements require penetration testing.
SOC 2, PCI DSS, ISO 27001, CMMC, and HIPAA all include requirements to regularly test network and application security. Regulations such as GDPR and CCPA also encourage proactive security measures to identify vulnerabilities before a security incident can occur, and penetration testing can be used to fulfill these requirements.
Rhymetec started as a penetration testing company in 2015, and we offer the highest quality penetration tests to meet your organization's compliance obligations while enhancing its security posture. We provide detailed reports of the findings, along with remediation recommendations, helping your organization address security gaps before an audit.
We offer a range of penetration testing services to fit your security and compliance needs, including mobile application penetration testing and web application penetration testing.
Strategic Security Guidance
Vanta's AI-driven features streamline core compliance areas to include risk management, access reviews, vendor security assessments, and security questionnaires. The platform accelerates compliance workflows, while expert guidance from Rhymetec's team enables you to interpret findings, implement security best practices, and customize controls based on your unique risk profile and risk appetite.
Security and compliance strategies must be tailored to business needs. Without in-house expertise, it can be difficult to implement effective controls. With Rhymetec's team providing ongoing guidance, while leveraging Vanta's cutting-edge integrations and capabilities, you gain a compliance program that meets regulatory requirements while reducing risk to your organization and maintaining operational efficiency.
Why Rhymetec?
Transparency:
We believe our clients deserve complete clarity about what they're getting, how we work, and the results they can expect. Whether it's our methodologies, testing scope, or the tools we use, we provide detailed insights at every step.
Autonomous:
As a self-funded company, we have the freedom to make client-focused decisions quickly and flexibly. This independence allows us to adapt our services to meet your unique needs and help our partners win in competitive scenarios. Our autonomy ensures every decision prioritizes your success.
Team Credentials:
Our team boasts a broad range of industry-recognized certifications, including Burp Suite Certified Practitioner, ISC2 CISSP, EC-Council CHFI, CPENT, Offensive Security: OSE3 OSED OSEP OSWA OSWE OSCP, and CompTIA Security+, PECB Internal Auditor Certifications, and more.
Market Maturity:
Rhymetec was founded in 2015. Our specialized expertise ensures a deeper understanding of your business's unique challenges, providing the most impactful security insights. Don't settle for less experienced competitors when it comes to protecting your business or meeting the needs for compliance requirements.
Frameworks Supported by Rhymetec's Vanta Compliance Services
Achieve compliance faster and with greater confidence with Vanta's automation and Rhymetec's hands-on security expertise. Together, we streamline control implementation and tackle every step of the compliance process for you. We fully manage the following frameworks (and more) on your behalf, from start to finish, getting you over the finish line with your audit in the fastest time frame possible:
SOC 2 With Vanta & Rhymetec
Vanta automates control monitoring, policy management, and evidence collection for SOC 2, reducing the time required to prepare for an audit. As SOC 2 allows flexibility in control implementation (which requires interpretation to align with your business operations), the Rhymetec team ensures that automated controls are properly scoped, fills in gaps with manual tasks like risk assessments and penetration testing, and guides your team through audit readiness.
ISO 27001 With Vanta & Rhymetec
Vanta accelerates ISO 27001 certification by automating risk assessments, system inventory, and document management, including the Statement of Applicability. ISO 27001 also requires internal audits and ongoing security improvements. Our team at Rhymetec handles these manual components and others, develops custom policies, and aligns your Information Security Management System (ISMS) to your business risks.
GDPR
Vanta supports GDPR compliance through automated access reviews, vendor risk assessments, and security monitoring. GDPR compliance also entails implementing legal and operational processes, such as data mapping, incident response planning, Data Protection Impact Assessments, and more. At Rhymetec, our vCISOs carry out these actions and ensure that all of your privacy policies, manual risk assessments, and data processing agreements are in full alignment with GDPR requirements.
HIPAA
Vanta automates HIPAA compliance by monitoring technical safeguards, conducting access control reviews, and managing security policies. For the aspects of HIPAA compliance that require administrative safeguards, such as employee training, documented risk management procedures, and business associate agreements, the Rhymetec team bridges the gap by filling in or fine-tuning these items. For example, we implement customized employee training and advise you on regulatory expectations. Leveraging Vanta and our services provides a complete approach to HIPAA compliance.
PCI DSS
Vanta identifies security gaps related to PCI DSS controls, while the Rhymetec team fills pieces such as penetration testing, network segmentation, and quarterly scanning. Our experts ensure that all PCI DSS requirements are met, manages security assessments, and handles auditor interactions for you. By combining Vanta's automation with our technical security expertise, you meet the requirements in the fastest timeframe possible and maintain continuous compliance over time.
CMMC
Vanta helps streamline CMMC compliance by automating areas such as security control monitoring and access review. While working to meet the extensive CMMC requirements under risk management, ongoing assessments, and security controls, a dedicated team of security and compliance experts can greatly reduce the complexity for your organization. While leveraging Vanta, Rhymetec’s team ensures that all necessary security measures (including incident response planning tailored to your organization, system security plans, and third-party risk management) are correctly implemented.
Additional Frameworks Supported By Rhymetec and Vanta
Beyond the frameworks listed above, Vanta and Rhymetec support a range of other compliance frameworks. These include ISO/IEC 42001 for AI risk management, DORA for financial sector resilience, HITRUST CSF for healthcare security, NIST AI RMF for AI governance, The California Consumer Privacy Act (CCPA), and various other global and industry-specific standards.
For any framework(s) you select, using Vanta in conjunction with Rhymetec's guidance streamlines certification, strengthens your security operations, and sets you up for successful long-term compliance.
Ready to Simplify Your Vanta Compliance Journey?
Don't let compliance barriers slow down your growth.
Our experts are ready to transform security from a roadblock to a competitive advantage. We leverage the most cutting-edge tools like Vanta on your behalf and remove the work entirely off your plate so you can get back to what really matters - running your business. Contact us today to learn more.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We've worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
Interested in reading more? Check out more content on our blog.
Businesses often rely on a network of vendors to support their operations, yet many don’t realize this reliance comes with significant cybersecurity risks. Because of this, strengthening vendor risk management isn't just a necessity; it's a critical component of maintaining customer trust and safeguarding sensitive information. Here's how businesses can strengthen their vendor risk management practices and stay ahead of potential threats:
Start With Due Diligence
Before onboarding a vendor, conduct a thorough evaluation of their security practices. This means more than simply reviewing their policies or taking their word for it. Begin by requesting detailed information about their cybersecurity measures, including network security, data protection protocols, and any certifications or attestation reports they hold (e.g., ISO 27001 or SOC 2 compliance).
Next, conduct interviews with their team, ask for case studies and request references from other clients. A vendor's security posture should be robust and transparent, and any hesitance or vagueness in providing this information should be considered a red flag.
Implement Ongoing Monitoring And Review Processes
Onboarding a vendor with strong security practices is just the beginning. Cybersecurity isn’t static, and your approach to vendor management shouldn't be either. Define a process for ongoing monitoring of your vendors' security postures. This could involve quarterly reviews, where you reassess vendors' network security, business continuity plans, and any incidents of data breaches.
Regular reviews help verify that vendors maintain the standards agreed upon at the start of your partnership. After all, a vendor's security measures might lapse or become outdated over time, posing a risk to your business. You can identify and address potential issues by staying proactive and conducting regular assessments before they escalate.
Strengthen Communication And Transparency
Transparency is key in vendor relationships, especially when it comes to cybersecurity. Establish clear communication channels and expectations from the start. Your vendors should be aware that you expect to be informed of any security incidents or changes in their operations that could impact their ability to safeguard your data.
You may also want to consider asking your vendors if they have a trust center or public page that outlines their controls and practices, reporting on their security status in real time. This kind of transparency builds trust and allows you to address potential risks swiftly.
Leverage Technology For Continuous Monitoring
As the number of vendors you work with increases, so does the complexity of managing them. To stay ahead, you can invest in technology solutions that help automate the monitoring process. Tools that continuously track vendor performance, security updates, and compliance status can provide real-time insights, enabling you to act quickly if a risk is identified.
These tools can also help you maintain an up-to-date inventory of your vendors, track the flow of data between your company and its vendors, and identify any potential vulnerabilities. In the cybersecurity landscape, where threats evolve rapidly, leveraging technology can provide a significant advantage in staying ahead of potential risks.
Tailor Your Approach Based On Vendor Risk Levels
Not all vendors pose the same level of risk to your organization, so a one-size-fits-all approach to vendor management can be inefficient and ineffective. Instead, classify your vendors based on their access to your sensitive data and the potential impact on your business if their security were to be compromised.
More stringent monitoring and controls should be in place for high-risk vendors, such as those with access to critical systems or sensitive customer information. This might include more frequent reviews, higher standards for cybersecurity measures, and more detailed contractual obligations. A less intensive approach may be sufficient for lower-risk vendors, but they should still be subject to regular reviews to ensure they meet your security expectations.
Cultivate A Culture Of Security Within Your Organization
Strengthening vendor risk management starts with a culture of security within your own organization. Your team should understand the importance of cybersecurity and be trained to identify potential risks when interacting with vendors. Encourage your employees to follow best practices, like verifying the legitimacy of vendor claims and reporting any suspicious behavior.
Develop A Vendor Incident Response Plan
Incidents can still occur no matter how robust your vendor management process is. As such, it’s crucial to have a vendor incident response plan outlining the steps your company will take if a vendor's security is compromised. This plan should include clear communication protocols, roles and responsibilities, and a process for mitigating the impact of a security breach.
By planning for the worst, you can respond quickly and effectively to minimize the damage to your business and your clients. A well-prepared incident response plan can also help to reassure your clients that you are committed to protecting their data, even in the face of unexpected challenges.
In Closing
Strengthening vendor risk management is not a one-time task, but an ongoing commitment. By implementing comprehensive due diligence, ongoing monitoring, clear communication, and leveraging technology, businesses can significantly reduce their exposure to cybersecurity risks. Prioritizing cybersecurity and ethics in vendor management protects your business and builds the trust essential for long-term success in the digital era.
You can read the original article posted in Fast Company by Rhymetec CEO, Justin Rende.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We've worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
Interested in reading more? Check out more content on our blog.
The future of cybersecurity remains a constant concern for security professionals and organizational leaders. Even if the organization is protected now, what new threats and events could derail the organization in a few days, weeks, or months? After all, the rapid advancement of technology also means a rapid advancement of vulnerabilities.
There is no crystal ball to forecast the future; however, organizations can make informed predictions about cybersecurity in the coming year. There are several trends that will likely shape the cyberlandscape in 2025, and organizations looking to stay ahead of the curve should prepare accordingly.
More Sophisticated Ransomware
Since up to 20% of all breaches are ransomware attacks, this security challenge has been a prevalent risk for over a decade, and its threat potential stands to become even greater in the near future. There are now more than 150 ransomware families, showing that this attack vector is proliferating and increasing in sophistication.
Moreover, artificial intelligence (AI) is fueling this growth, making ransomware increasingly complex and more difficult to detect—which also means it is more dangerous. Previously, malware scanners had proven quite effective in detecting ransomware, but their effectiveness is decreasing as technology evolves.
What can organizations do about this? First, they must rethink how they detect ransomware. Organizations may need to augment their existing tools and bring in newer, AI-fueled systems to identify and thwart more sophisticated threats. Second, invest in employee training, specifically around phishing attacks, as these are still the primary vehicle for ransomware deployment.
To this end, the most effective training involves providing phishing simulations and phishing material to educate employees on how to spot the phish in the future. The next step is to wait for an employee to fall for a phishing email and/or input their credentials into a phishing website (and they will). At that point, they should be given immediate security awareness guidance on what phishing is and how to avoid phishing attempts in the future. Responding at the moment they fell prey to the attempt is key to raising awareness and preventing similar scenarios in the future.
More Security Needed for the Cloud
According to G2, 85% of organizations will be “cloud first” by 2025. While this is exciting news for our digital-centric society, the downside is that cloud adoption has moved faster than cloud security measures have.
With many organizations moving to remote or hybrid environments, employees have gone from using IT-configured devices on the office premises to using remote devices nearly anywhere and everywhere. This, naturally, makes the organizations with a remote and/or hybrid workforce must focus on implementing robust cloud security frameworks. Two examples include Zero Trust Architecture, which assumes no user or device is trusted by default, and Cloud Security Posture Management (CSPM), which consists of continuously monitoring cloud infrastructure to identify and remediate security risk and misconfigurations. Employee education and clear policies about cloud usage are as crucial as ever, along with implementing tools meant for cloud environments.
AI Continues to Change Cybersecurity
Cybercriminals use AI technology to create more elaborate hacking tools, while cybersecurity professionals rely on it to develop better threat detection systems and predict future attacks. The debate over whether AI has helped or hurt cybersecurity efforts continues, but its impact is undeniable. In truth, it has become even more of a complex issue because both sides of the equation are embracing it. As 2025 approaches, both protectors and attackers will continue to turn to AI to outsmart one another.
Outside of the threat and defense landscape, AI governance also plays a critical role. While the International Organization for Standardization (ISO) and International Electrotechnical Commission (IEC), ISO/IEC 42001:2023 Information technology — Artificial intelligence — Management system standard represents progress in establishing governance and responsible management of AI systems, it alone is insufficient. Organizations must implement additional safeguards and strategies to protect their AI operations fully.
The organizations that will fare the best will implement AI-enhanced security tools, such as AI-powered threat detection, automated compliance monitoring, and/or behavioral analytics. Staying on top of regulatory developments and compliance is also of critical importance.
Cyberwarfare in Upcoming Elections
In the digital environment, cyberwarfare has become the new norm in elections, with hackers attempting to manipulate outcomes and spread misinformation. Given the high-profile elections regularly occurring around the world, cybercriminals are expected to target political campaigns and critical infrastructure.
As is usually the case, an ounce of prevention is worth a pound of cure. Organizations and governments alike should plan for a spike in attacks leading up to important elections, taking the time now to proactively secure crucial systems and implement plans to combat misinformation campaigns.
Retain and Attract Cybersecurity Experts
Half of cybersecurity professionals expect that they will burnout in the next 12 months due to the stress and pressures of their jobs. Professionals in the field suffer from burnout after facing unprecedented pressure and being held accountable for breaches. Given the already existing talent gap, this is nothing short of a crisis.
To retain their seasoned cybersecurity specialists, organizations must avoid personally blaming chief information security officers (CISOs) for cyberattacks. Even though the individuals in this role oversee the organization's security measures, and are the most visible in this department, they should not be personally held responsible for breaches. This often happens due to a lack of understanding of cybersecurity, and the natural human desire to find someone or something to blame for a problem. But these situations are usually highly complex and the only outcome from pinning an attack on a CISO is that they will be more likely to burn out and/or leave the organization.
Along the same lines, an organization's security team is the backbone of the enterprise and should be supported well, especially those in high-stress roles. As such, organizations should provide mechanisms to support and appreciate security teams, ensuring scheduled breaks, and distributing employee workload. This should be done while also recognizing their achievements. Organizations can enhance their security teams' effectiveness by investing in robust security measures, even when the return on investment is not immediately apparent. This commitment demonstrates a dedication to setting everyone up for success by equipping both the organization and its security department with the best tools available.
Last, reconsider how to educate and certify cybersecurity experts. For example, the Certified Information Systems Security Professional (CISSP) certification is still often used but is based on technology from the early 2000s. Instead, certifications should be relevant to today’s cybersecurity landscape, and the industry needs to reflect this. For instance, certifications from CompTIA, the Criminal Justice Information Services (CJIS) certification from the United States Federal Bureau of Investigation (FBI), and the Certified Ethical Hacker (CEH) are all highly respected and applicable today.
Looking Ahead
In 2025, organizations can look forward to many technological advancements. But these advancements will come with more ransomware, AI on both the attacker and defender sides of security, cyberwarfare, employee shortages, and more. As such, organizations must be vigilant and more proactive than ever in investing in security measures and putting safeguards first.
About The Author: Justin Rende, CEO
Justin Rende is the founder and CEO of Rhymetec, a cybersecurity firm providing cybersecurity, compliance, and data privacy needs to SaaS companies. With more than 20 years of experience in cybersecurity, Rende has focused exclusively on developing the most innovative and customizable cybersecurity solutions for modern SaaS-based companies.
You can read the original article posted in ISACA by Rhymetec CEO, Justin Rende.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We've worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
Interested in reading more? Check out more content on our blog.
To kick off the New Year, we've compiled 25 cybersecurity memes for 2025! Sharing these memes can help lighten the mood in the often stressful world of cybersecurity and reinforce important security concepts.
Check out our ultimate list of the best cybersecurity and compliance memes:
1. Cybersecurity Memes: The Small Business Dilemma

The hard truth is that cybersecurity is important regardless of organization size! In fact, small businesses are actually more likely to be targeted, precisely because they are small. Small businesses also need security policies, incident response plans, and much, much more.
2. The Regular Updating Scroll of Truth

We've all been there. It never feels like the right time to update, does it? It's so tempting to click "Remind me tomorrow" every day. But regular updates are one of the most basic and important things to do for security. However tempting it may be to keep putting it off:
3. Software Updates Cannot Be Ignored!

Regular updating enables known vulnerabilities to be patched. If vulnerabilities are not addressed, threat actors can exploit them. Plus, besides the obvious security benefits, updates also improve the performance and functionality of the applications you use every day. And that leads us to…
4. Don't Be This Surprised Pikachu

Failing to update software is like leaving the door wide open for cybercriminals. Known exploits can target unpatched systems, making you an easy target. Don't be this Pikachu - get proactive with your cybersecurity!
5. The Neverending Questionnaire
What better topic for cybersecurity memes than the infamous security questionnaire? We (or our GRC teams) have all been here:

6. The Friday Afternoon Security Questionnaire
Friday afternoons are for winding down, not being bombarded with a security questionnaire. Pro tip: Keep your documentation organized, and future-you will thank you!
7. When You Realize You Can Stop Filling Out So Many Security Questionnaires

That's right - the actual reason to get a SOC 2 report is to avoid filling out security questionnaires! (Just kidding, though, security also matters…)
8. Password Cybersecurity Memes

If you think this is an exaggeration, think again! Here are the top 10 passwords used in the United States:
- 123456
- 123456789
- 12345678
- password
- qwerty123
- qwerty1
- 111111
- 12345
- secret
- 123123
The top 200 feature a wide range of other variations of the word "password."
9. Hacker, or Bob From Accounting?

When logs show unusual activity, at first glance, it can seem like a toss-up: malicious actor or user error? Whether it's Bob from accounting or something more sinister, analyzing these events is critical.
10. And Definitely Don't Do This:

You could have the strongest password in the world, but if you use it across multiple accounts, it doesn't matter!
If just one site is compromised, attackers can easily gain access to your other accounts. Unique passwords create additional layers of security and make it harder for cybercriminals to exploit a single point of entry.
11. When You Put Your Cat's Name In Your Password

When your password is "Fluffy123"...Remember that your pet's name isn't as secure as you think. Use strong, unique passwords and leave Fluffy out of it.
12. Cybersecurity Memes: Penetration Testing

Penetration testing isn't just a checkbox for compliance. It should be conducted on a regular basis to identify vulnerabilities before attackers can exploit them. Don't wait for a breach to find out what's exposed! When shopping for pen testing vendors, look for teams that employ local talent and don't outsource their services.
13. Penetration Testing or Just a Vulnerability Scan?

Some vendors claim to offer "penetration testing" when, in reality, what they are really doing is vulnerability scanning. Make sure to know the differences between penetration testing vs. vulnerability scanning, so you know your pen testing vendor is doing what they say they are!
14. The Layers of Security: Defense in Depth

Good security means implementing many layers of defense. An example of defense-in-depth is access control on top of things like your firewall and intrusion detection to keep your assets safe. This is a standard security philosophy and strategy.
15. Rickrolling: The OG Phishing Simulation

If you learned how to not trust any links by being chronically online during your childhood, you're not alone. Rickrolling really did teach an entire generation to stop blindly clicking links. It didn't come with a training manual, but it worked. Can your phishing training say the same?
16. When Your Team Passes The Phishing Test Like Pros

Okay, maybe it was all the rickrolling they've encountered.
Or maybe it was your training program! Either way, it's a big win for security awareness. Phishing attacks are one of the most common threats, and getting your team to spot them is incredibly important.
As phishing attacks become even more sophisticated with the advent of AI, investing in phishing training for employees is something every single organization should be doing as a basic security measure nowadays.
17. A False Dichotomy? Compliance vs. Cybersecurity

Compliance: checking the boxes to get compliant ASAP.
Cybersecurity: so, so much more.
Ahh, the security vs. compliance debate. The challenge is balancing both. Compliance might make auditors happy, but it doesn't always mean your systems are actually secure. True security goes beyond frameworks.
But why not do both?
18. Compliance Cybersecurity Memes

Startups - we get it. There's a lot on your plate. However, not prioritizing compliance for startups is a risky move. Compliance builds trust with customers and sets your business up for long-term success. Bluey gets it.
19. Regulations…Just When You Think You're Safe

Just when you think you've finally caught up with the latest compliance regulations….new changes are announced. It's a never-ending cycle. Stay ready, because the compliance game never stops.
20. SOC 2: When They Say Everything's Fine

When the team says they have everything under control for SOC 2, but you know nothing is ever as simple as it seems.
SOC 2 is no joke and is quite a process. Don't assume it's going to be easy, and don't wait until the last minute to find out if you're missing key pieces. Make sure everything really is under control before your audit by conducting a gap assessment or working with a seasoned MSSP (Managed Security Services Provider) to help you be prepared.
21. What Do You Mean It's Quarterly?

Like many other legal and voluntary standards, there are ongoing action items to stay compliant with PCI DSS. Don't ever assume compliance is over once you have all the boxes checked off one time. Most frameworks involve ongoing items.
And that leads us to:
22. When Your Compliance Approach Is "Check The Box"
Don't let this be your compliance program!
SOC 2, ISO 27001, PCI DSS, GDPR, HIPAA, and more all require organizations to monitor vendor compliance on an ongoing basis to remain compliant. This is a critical part of risk management, especially as organizations increasingly rely on third-party services.
23. Imagine: This Could Be You

When that moment hits, and you realize you're officially certified - all the hard work and investments finally paid off. Time to celebrate, but don't forget - security is a journey, not a destination.
24. It's Been 84 Years….

When you try to get compliant without using a compliance automation tool, it can feel like it takes decades…Compliance automation tools seriously speed things up.
25. Lastly…Maybe All You Need Is a vCISO (Even If She Doesn't Even Go Here)

Many startups and SMBs outsource cybersecurity and compliance to a vCISO. The CISO as a service option can be a much more sustainable, scalable, and cost-effective option than building out an entire security team in-house.
At Rhymetec, our vCISOs integrate with your team and act as a part of your organization to help you meet your goals and turn security and compliance into business enablers.
Beyond Cybersecurity Memes - About Rhymetec
We hope these cybersecurity memes for 2025 brightened your day!
At Rhymetec, our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
Interested in reading more? Check out more content on our blog.
In this blog, we'll go over frequently asked questions about conducting a cybersecurity tabletop exercise, including how it works, why it's important for startups and SMBs, which voluntary and legal compliance requirements you need one for, and more.
What Is a Cybersecurity Tabletop Exercise?
You're sitting in a meeting with your leadership team, the IT lead, and a couple of personnel from operations. Someone kicks things off by saying, "Alright, here's the situation: You've just received an email from a threat actor claiming they've gained access to our production environment. They've encrypted customer data and are demanding a $50,000 ransom in the 48 hours. What do we do first?".
That's a cybersecurity tabletop exercise in action. A tabletop exercise allows your team to practice handling a cybersecurity incident without the actual crisis. Your team works through a realistic scenario step by step, discussing who's responsible for what and how decisions will be made. During the exercise, gaps in your existing plan and questions you need to answer going forward will likely surface:
Who decides if the ransom should be paid? What happens if legal or PR resources are tied up? Is your team ready to handle questions from customers or regulators?
These are the types of issues that otherwise may not come up unless you are in the middle of a real incident, but a tabletop exercise allows you to address them before they actually happen.

These exercises enable you to see how your team will react when/if you experience a real threat, based on your specific situation: Maybe your team has a strong technical foundation but hasn't worked out all the details for responding to an attack. Or maybe you're growing quickly, and roles like security and IT are spread across multiple people who wear a lot of hats.
Regardless of your situation, tabletop exercises strengthen your security posture by giving you a chance to run through various scenarios, fine-tune how to respond, and stress-test your existing processes.
They also need to be conducted to meet many voluntary and legal requirements. For this reason, they're especially critical for organizations seeking to land bigger clients or meet compliance requirements like SOC 2 or ISO 27001.
Why Do Startups and SMBs Need Tabletop Exercises?
Let's say your startup just landed a major client. Part of the contract includes a requirement to prove you can handle a security incident without putting their data at risk (or, they simply ask to see your SOC 2 report).
You've got your security policies written up, but when it comes to how your team would respond to a real incident, you need to make sure everyone is on the same page and that you have documented proof of your processes.
Enter the tabletop exercise.
Startups and SMBs often operate with lean teams, where people juggle multiple responsibilities. In a crisis, this reality can often cause confusion over who does what and how to make decisions. A cybersecurity tabletop exercise allows you to clarify responsibilities and builds confidence in your ability to respond to incidents.
Besides disrupting your daily business operations and creating downtime, an incident like ransomware or a data breach can harm the trust of your customers and hurt your ability to grow. Knowing how you'll respond greatly reduces that risk and helps minimize the fallout.
Compliance is another factor. Frameworks like SOC 2 require you to put your incident response policies and plan to the test, and tabletop exercises are an easy way to meet that requirement. Tabletop exercises are just as critical for startups and SMBs as they are for large enterprises.
For startups looking to scale, being able to demonstrate that you've done this makes a big difference when building trust with investors, partners, and customers.
Cybersecurity Tabletop Exercises and Compliance: SOC 2 and More
Under the SOC 2 Trust Services Criteria, tabletop exercises meet the incident response testing requirement of the security criteria (which is not amongst the optional criteria under SOC 2!). Criteria CC7.1 and CC7.2 require organizations to test out an incident response plan. Auditors will therefore ask to see evidence that you've actually put your plans to the test and don't simply have them written down as policies.
ISO 27001, often seen as the baseline for global security standards, also calls for incident response testing. Annex A.16.1.5 requires the periodic testing of information security incident response plans. Tabletop exercises are the simplest, most effective, and industry-standard way to satisfy this requirement.
PCI DSS Version 4.0, which applies to organizations that handle payment card data, also includes a specific requirement for incident response testing. Noncompliance with PCI DSS can lead to fines and additional transaction fees. Requirement 12.10.2 states that companies must "test incident response procedures at least annually". Again, tabletop exercises are the most straightforward and widely accepted way to meet this requirement.
For privacy regulations like GDPR and the California Consumer Privacy Act (CCPA), there are various stipulations around the importance of having processes in place to be ready in the event of a security incident.
For instance, GDPR's Article 32 emphasizes the need for "…a process for regularly testing, assessing and evaluating the effectiveness of technical and organisational measures for ensuring the security of the processing." While tabletop exercises aren't explicitly named, CCPA has similar expectations for businesses handling sensitive consumer information.
Putting your response to a security incident into practice through a tabletop exercise allows you to prove to auditors that you can meet these requirements.
Enterprise clients in particular will want reassurance that you can handle incidents without putting their data at risk. Many enterprise contracts (which can be used as either an alternative or an add-on to compliance by some organizations) also include requirements for incident response testing. This can be especially important if your organization handles sensitive data or will be integrating with an enterprise client's systems.
3 Ways MSSPs Support Tabletop Exercises for Organizations
Organizations often choose to work with a Managed Security Services Provider (MSSP) in order to guide them through tabletop exercises. Here are three ways MSSPs offer valuable support through this process while ensuring you meet compliance requirements:
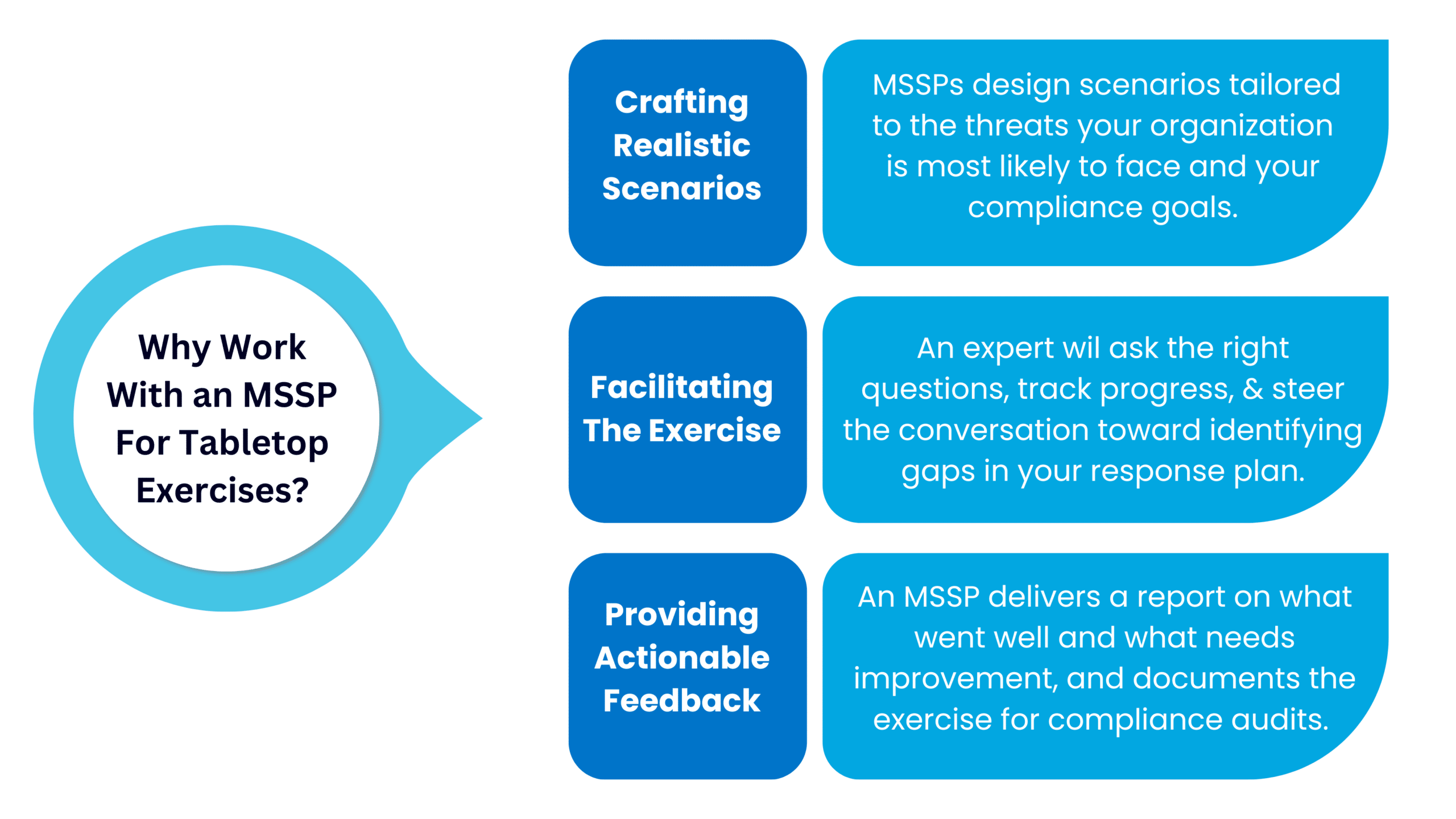
1. Crafting Realistic Scenarios For Your Cybersecurity Tabletop Exercise
Creating a scenario that makes sense for your business is critical. MSSPs can design scenarios tailored to the threats your organization is most likely to face and your compliance goals.
For example, if your company handles customer payment data and you are trying to obtain PCI DSS compliance, the exercise may focus on a ransomware attack targeting your payment processing systems. If you're in SaaS, it could take the form of a simulated compromise of user accounts.
2. Facilitating the Exercise
To conduct tabletop exercises, you need a neutral facilitator to guide the discussion and keep the team on track. A security expert (such as a Virtual CISO, vCISO) at an MSSP can take on this role, asking the right questions, tracking progress, and steering the conversation toward identifying gaps in your response plan.
Working with an outside expert allows your team to engage in the exercise without worrying about having to run it themselves. They bring an outsider's point of view, which can enable you to gain insight into areas your internal team may overlook.
3. Providing Actionable Feedback
After the exercise, an MSSP delivers a report on what went well and what needs improvement. They can help you prioritize updates to your incident response plan and recommend additional security measures based on gaps uncovered during the exercise. They can also document the exercise for compliance audits.
Working with an MSSP provides access to expertise, allows you to strengthen your response capabilities without pulling your internal team away from their day-to-day work, and provides deliverables you can use to demonstrate your security posture to auditors and customers.
Getting Started: Partnering With Experts
Cybersecurity tabletop exercises can be used to meet a vast range of both legal and voluntary requirements, and having conducted them builds trust with your clients and prospects. They provide both the evidence auditors need and the confidence customers expect.
However, startups and smaller organizations may lack the resources or internal expertise needed to effectively run cybersecurity tabletop exercises. An external expert, such as a vCISO, solves this issue and provides specialized knowledge. At Rhymetec, our vCISOs have walked dozens of organizations through their tabletop exercises and provided reports that fulfill compliance requirements.
Check out details on our vCISO services to get started today if you are interested in conducting exercises for your organization.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We've worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
About the Author
Metin Kortak has been the Chief Information Security Officer at Rhymetec since 2017. He began his career working in IT security and gained extensive knowledge of compliance and data privacy frameworks such as SOC, ISO 27001, PCI, FEDRAMP, NIST 800-53, GDPR, CCPA, HITRUST and HIPAA. Metin joined Rhymetec to build data privacy and compliance as a service offering. Under his leadership, these offerings have grown to more than 700 customers, and the company is now a leading SaaS security service provider in the industry.
Interested in reading more? Check out more content on our blog.
With data breaches and cyber threats seemingly making headlines every day, the importance of ethics in cybersecurity cannot be overstated. As businesses increasingly rely on digital solutions to manage sensitive information, trust becomes the cornerstone of successful relationships between companies and their clients.
But what happens when unethical practices enter the arena? Let’s take a deeper look at the role of ethics in cybersecurity and how businesses can build and maintain trust in a digital era.
The Ethics Of Outsourcing
One of the most pressing moral debates in cybersecurity today is about the outsourcing of services, often to overseas vendors. Many companies, driven by cost-cutting measures, turn to platforms like Fiverr or Upwork to handle critical aspects of their cybersecurity needs. But while outsourcing itself isn’t inherently unethical, the lack of transparency and control over who has access to sensitive data in these particular cases raises significant concerns.
When a company outsources its cybersecurity services without informing its clients, it risks violating their trust. Clients believe their data is being handled securely and locally, only to discover it has been outsourced to unknown entities worldwide. This practice not only undermines the trust of clients but also poses a significant security risk. After all, how can a company guarantee the security of its data if it doesn’t even know who is handling it?
Due Diligence: The Foundation Of Trust
This is another critical aspect of ethics in cybersecurity. Bringing on vendors without thoroughly vetting them or understanding who they, in turn, might outsource the work to exposes companies to major risks. Trusting a vendor based on their word or a polished presentation is not enough. Businesses must conduct thorough research to ensure their vendors have robust security measures in place and are transparent about their operations.
At my company, for instance, we conduct quarterly reviews of all our vendors to assess their security posture. This isn’t just a one-time check but a continual process of monitoring and evaluation. We look at key factors such as network security, business continuity, and any past breaches to determine whether a vendor remains a trustworthy partner. By doing so, we ensure our vendors uphold the same high standards of ethics and security that we promise to our clients.
Identifying Red Flags
Make sure you know who you’re working with and accept their claims with a healthy dose of skepticism. For example, if a vendor claims to have thousands of clients but only has a handful of employees on LinkedIn, consider it a red flag. Such a discrepancy suggests the company might be outsourcing work to unknown third parties, potentially compromising client data. If this isn’t the case, then it might suggest they’re lying about the number of clients they have, which is still another glaring red flag.
As a business, it’s essential to do your due diligence when hiring vendors or full-time employees in the cybersecurity space. This means looking beyond surface-level claims and digging deeper into their background, certifications, and past performance. Asking for referrals, checking their LinkedIn profiles, and verifying their claims are all part of this process. It’s about ensuring the people you’re entrusting with your data are both technically competent and ethically sound.
Transparency: The Hallmark Of Ethical Cybersecurity
Once you’ve established a strong foundation of ethics within your cybersecurity practices, the next step is to communicate this to the marketplace. Marketing your ethical standards is not just about showcasing security badges on your website. It’s about demonstrating an ongoing commitment to maintaining and improving your security posture.
For instance, some companies might claim to be SOC 2 compliant and proudly display this on their websites. However, if they are not undergoing an annual SOC 2 audit through an AICPA-accredited firm, their security posture might not be as robust as they suggest.
At my company, we emphasize the importance of continuous monitoring and evaluation. We encourage clients to take advantage of our partner solutions that offer a real-time view of their security posture. This way, they can see we’re not just resting on past achievements but are actively working to maintain the highest security standards, too.
Transparency is a key component of building trust in cybersecurity. Companies that are open about their security practices and publicize their security posture are typically more trustworthy. This doesn’t mean revealing every detail of your security measures but rather being upfront about your processes, controls, and commitment to ethical practices.
Ethics As A Competitive Advantage
Ethics can be a powerful differentiator in the highly competitive field of cybersecurity. Companies prioritizing ethical practices, from vendor management to operations, are better positioned to build and maintain client trust. As digital threats evolve, so must our commitment to ethical cybersecurity practices. By doing so, we can not only protect our clients’ data but also uphold the trust that is essential to our industry’s success.
You can read the original article posted in Fast Company by Rhymetec CEO, Justin Rende.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.
Interested in reading more? Check out more content on our blog.
Regular cybersecurity audits are the best way to ensure your business continuously meets security and compliance requirements while reaping the business benefits of investing in security. This post will go over the different types of audits, their benefits for your organization, how to prepare, and common findings to be aware of.
For many fast-growing startups and SMBs, cybersecurity might not feel like a top priority. But with increasingly complex data regulations, rising threats, and growing client expectations, security can no longer be an afterthought, regardless of company size or industry.
The good news is that organizations that invest in improving their security posture and undergo regular cybersecurity audits start to see a wide range of benefits, especially once they have evidence they've successfully completed their audit through a certification or a report:
Barriers are removed in their deal flows, the time spent on filling out onerous security questionnaires is eliminated, and they can get back to what really matters - moving their business forward.
Why Cybersecurity Audits Matter For Your Organization
A cybersecurity audit is a thorough review of an organization's security posture, assessing the adequacy of protections in place to defend against cyber threats and meet regulatory requirements. You can think of an audit as a health check for your security practices, allowing you to identify potential vulnerabilities before they can lead to an actual security incident.
Audit findings provide valuable insight into how secure your organization is and how well you are meeting any relevant requirements. Knowing how well your security practices measure up against industry standards allows you to pinpoint where improvements need to be made, and make only the changes you actually need.
Cybersecurity audits identify vulnerabilities and show where your security measures align with or diverge from relevant frameworks like ISO 27001, SOC 2, and HIPAA. After an audit, as you enact necessary changes to address the audit's findings, you'll reduce the risk of regulatory penalties, reputational damage, and security incidents. Decision-makers can use the results of an audit to prioritize security improvements and guide their compliance efforts.
When clients, investors, regulators, or other stakeholders expect evidence of your security controls, having third-party verification of the strength of your security posture is important. It shows that you've addressed security requirements upfront, creates confidence in your security approach, and helps meet stakeholder expectations.

Types of Cybersecurity Audits Every Startup Should Be Aware Of
Startups should know about a few different types of cybersecurity audits:
Internal audits are when your own team or an outside consultant examines your security setup. The goal is to conduct a gap assessment and find any areas for improvement to help better prepare you for future external audits. For example, an ISO internal audit provides a way to spot weaknesses early and adjust them before your official audit for frameworks like ISO 27001 and ISO 42001.
External audits bring in a third-party auditing firm to confirm that your organization is following specific security standards such as ISO 27001, PCI DSS, SOC 2, HIPAA, and more. Passing an external audit is vital if you're trying to land bigger clients or want to enter highly regulated industries.
Penetration testing mimics real-world attacks on your systems to find potential vulnerabilities. Penetration tests give you an idea of how strong your defenses really are under pressure, and the findings help prepare you to avoid real threats:
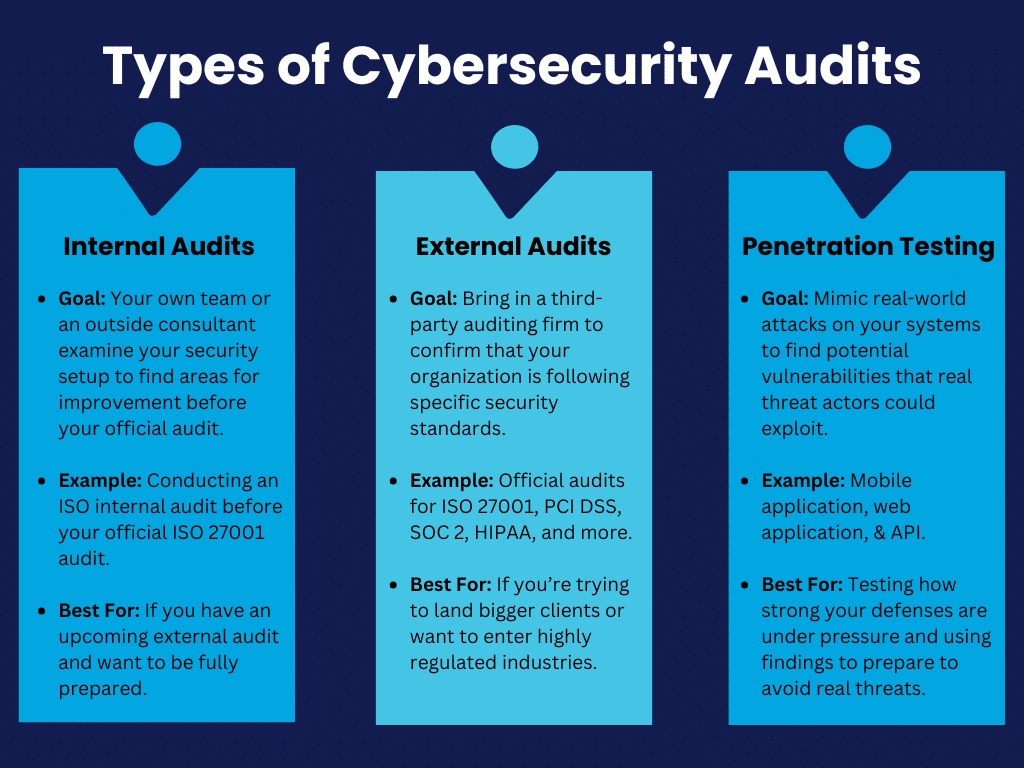
How to Prepare For a Cybersecurity Audit
To prepare for an audit, the first step is to take a close look at your existing policies and procedures: Are they actually being followed?
It's common for companies to write policies that look great on paper but fall short in practice. You'll want to make sure everyone on your team knows their roles, especially around access controls, data handling, and your organization's incident response policies.
Don't neglect the tech side. Run vulnerability scans, review your logging and monitoring, and make sure your backups are up to date. Auditors will likely examine these areas regardless of which type of audit you undergo. Lastly, keep your documentation extremely organized. Auditors appreciate easily accessible and well-organized documentation. Having it ready can be the difference between a smooth audit and a chaotic scramble.
Bonus Tip: A compliance automation tool can come in extremely handy at this stage, as it allows a single place to upload and keep track of all of your documentation. Your auditor will appreciate being able to easily access everything in one place!
Preparing ahead of time as much as possible puts you in control of the process rather than reacting to questions or findings that may come up. Providers like Rhymetec offer internal audits and gap assessment services that are conducted before your audit, leading to fewer surprises during your official audit.
Common Findings in Cybersecurity Audits (And How To Address Them)
Cybersecurity audits often reveal a few common recurring issues that many startups and SMBs face:
One of the most common findings across a variety of different types of audits is weak access controls. Cybersecurity audits frequently find gaps in access control requirements, meaning that too many people have unnecessary access to sensitive data or systems.
The fix here is straightforward:
- Review who has access to what.
- Limit permissions to those who need it.
- Implement multi-factor authentication to add a last additional layer of security to make it harder for unauthorized users to gain access.
Another issue that often comes up is missing or outdated documentation. Auditors will expect to see things like security policies, incident response plans, and training records. If you can't provide these documents or if they're outdated, that's a red flag.
To address this issue, you should:
- Create clear, up-to-date policies that reflect what's actually happening at your organization.
- Make documentation a regular part of your operations, so you're not scrambling to pull everything together before an audit.
- Consider using compliance automation software to organize all of your documentation for auditors in one place.
Another common area where audits also tend to find vulnerabilities is in systems that haven't been patched or updated.
Leaving old software as is is like leaving your door unlocked. You should be regularly updating and patching systems to close off potential entry points for attackers. Simply setting up automated reminders or systems to handle updates can be extremely helpful.
Third-party risk management is another area that is often overlooked by organizations and comes up in audit findings. For PCI DSS audits, for example, this is one of the most common challenges our experts at Rhymetec see that organizations encounter. For many frameworks, you need to make sure your third-party vendors are also compliant.

Finally, many audits reveal a lack of proper employee training. As noted by our experts in Rhymetec's Cybersecurity Awareness Month Tips, your people are often the first line of defense. If they're not aware of basic security practices or don't follow steps to adhere to them on a daily basis, it's a problem.
Ongoing security awareness training and phishing training for employees help everyone in your company recognize and avoid common vectors of attack like phishing attempts.
If possible, address these common issues ahead of time for a smoother audit process.
Cybersecurity Audits and Penetration Testing
Penetration testing is the best way to understand how well your defenses would stand up to real-world attacks.
While not every audit requires a pen test, it's often necessary for audits tied to specific compliance frameworks like PCI DSS and certain SOC 2 reports. These audits don't just ask if you've set up your security controls - they want tangible proof that your system can actually withstand an attack.
Penetration testing is recommended when you need more than a surface-level review of your security and need to go beyond checking boxes to meet compliance requirements; experts simulate actual cyberattacks to try to break through your defenses. Think of it as having someone attempt to lockpick your door, rather than just checking if your door is locked.
Note: If your organization is preparing for a major compliance audit, working with clients that demand high levels of security, or going through rapid growth, a penetration test is highly recommended!
If you incorporate penetration into your regular security checks, you'll get a clear picture of how well you're protected and will be able to tackle weaknesses before they become costly problems down the line. Getting a test done annually or after major changes to your systems helps you stay ahead of emerging threats.
Rhymetec offers a variety of penetration testing services, including:
- Mobile application penetration testing
- API penetration tests
- Web application penetration testing
- External network penetration tests
Choosing The Right Partner for Your Audit
Not all auditors are created equal, so it's important to select a partner who's not only experienced but also a good fit for your company's size, structure, and industry. You need someone who understands both your industry and the specific compliance requirements you're facing.
Audit Partner Factors To Consider
First, check out their track record. Have they worked with startups or SMBs before? It's one thing to know the rules, but another to understand the unique challenges small to midsized companies and startups face regarding security and compliance.
Ask about their previous clients and whether they've helped similar businesses successfully meet their compliance goals. Request to see case studies from their prior engagements with companies with similar profiles as yours.
Another factor to consider is how hands-on you want your audit partner to be. Some partners take a more hands-on approach by choosing to work with select MSSPs to help you improve your security along the way, while others are more focused on just performing the audit and reporting findings.

Audit Report "Red Flags" To Look Out For
A thorough audit report gives you a roadmap for improving your security with clear steps, while a deficient one can leave you with more questions than answers.
Plus, 69% of organizations report that the quality of compliance reports is extremely important. Your clients and stakeholders will want to see evidence of a thorough, high-quality audit.
So, how do you tell the difference between a thorough audit report and a deficient one?
1. First, look at how the findings are communicated:
A high-quality audit report won't just tell you that there's an issue - it will explain where the problem is, why it matters, and how it could impact your business. Look for specifics, like which systems or processes failed, how attackers could exploit weaknesses, and what steps to take next. If your report is filled with vague statements or broad recommendations without context specific to your organization, that's a sign it's not as thorough as it should be.
2. A high-quality report will also show you how issues across different areas are connected:
If weak access controls, for example, show up in multiple places - whether in your cloud setup, employee accounts, or vendor portals - a good report will explain how these issues are linked. A deficient report might mention them individually without showing the bigger picture.
3. Findings on your documentation is another area where a thorough report stands out from a deficient one:
A high-quality report points out exactly where your policies or training records are lacking and provides actionable steps to fix them. If your report glosses over missing documentation or doesn't dig into whether your policies match actual practices, you're likely looking at a surface-level, boilerplate review rather than a meaningful and tailored audit.
4. Finally, a quality report doesn't simply list issues but will categorize them based on their severity and urgency:
This helps guide you on which areas to focus on first. A deficient report may give you a laundry list of issues but won't help you understand which ones pose the most immediate threat.
In short, a thorough audit report provides clarity, context, and a plan. A deficient one leaves you guessing and unsure of how to proceed and may not hold up under scrutiny from your customers and stakeholders.
How Working With An MSSP Simplifies Cybersecurity Audits
Partnering with a Managed Security Services Provider (MSSP) can take a lot of stress out of cybersecurity audits. An MSSP handles much of the ongoing work for you, so when it's time for your audit, you're not rushing to get everything in order.
With continuous monitoring, regular updates, and fully managed compliance services, an MSSP ensures that your security posture stays audit-ready all year round. For example, if your business needs to meet standards like PCI DSS or ISO 27001, an MSSP can keep your policies and security controls aligned with the latest requirements and make sure you're up-to-date on your recurring audits.
Working with an experienced MSSP is the best way to minimize the risk of non-compliance and saves your internal team from having to devote time to it themselves. When you work with an MSSP, you're essentially outsourcing the complex, technical aspects of security to a team that specializes in it, freeing up your business to focus on growth while staying secure and compliant.
About Rhymetec
Our mission is to make cutting-edge cybersecurity available to SaaS companies and startups. We’ve worked with hundreds of companies to provide practical security solutions tailored to their needs, enabling them to be secure and compliant while balancing security with budget. We enable our clients to outsource the complexity of security and focus on what really matters – their business. Contact us today to get started.